Course selection system based on attribute passwords
A password and attribute technology, applied in the field of course selection system based on attribute password, can solve problems such as leakage, course data security, privacy, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
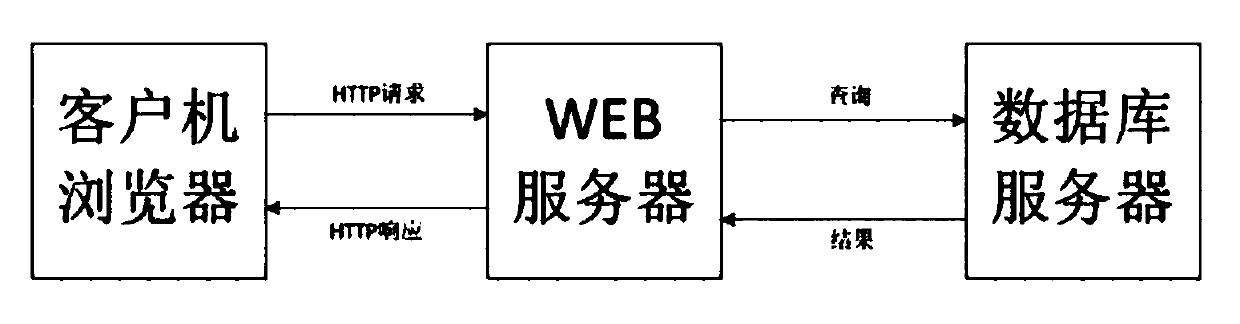
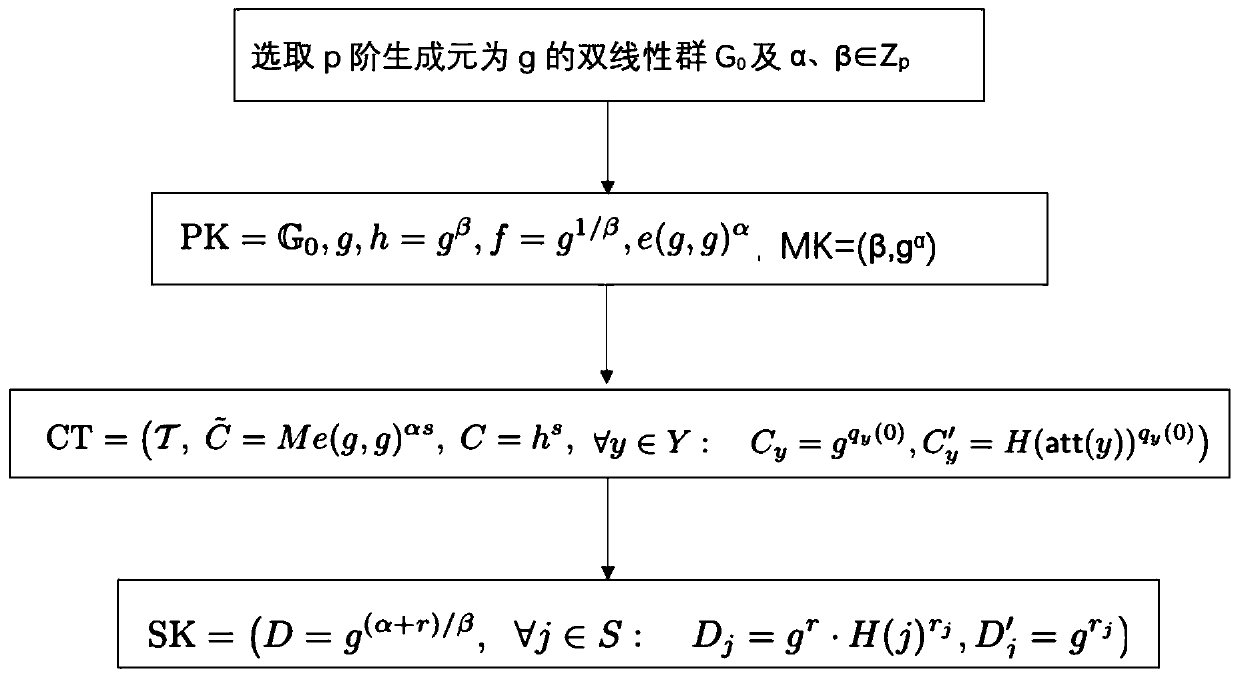
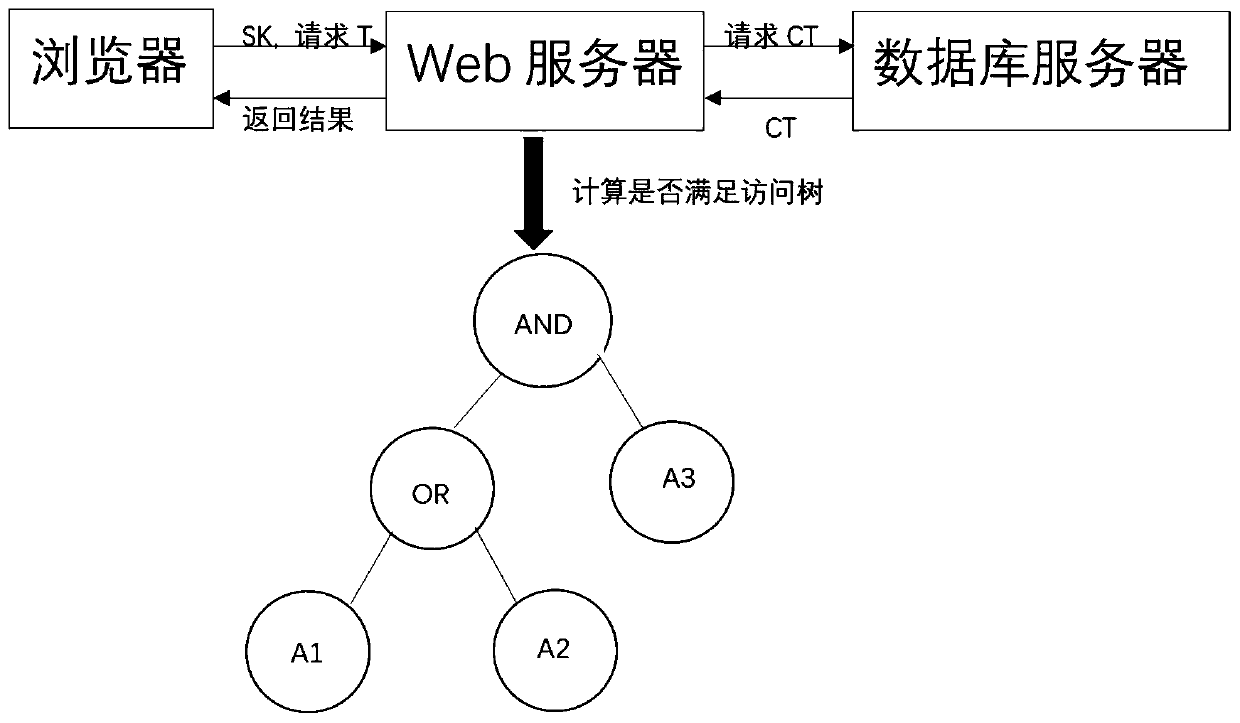
[0094] The course selection system solution proposed by the present invention is based on attribute cryptography technology, that is, using attribute cryptography's characteristics of security, low time cost, and low storage cost and the principle of asymmetric cryptography. The specific steps are:
[0095] (1) The system generates the public key PK, master key MK, and course selection authority key s according to the security parameters c And map the attribute set S; for example: "Computer College" attribute is mapped to 28 through hash function H; "Physics College" attribute is mapped to 29; "Student" attribute is mapped to 17 through hash function; "Teacher" attribute is mapped to H The H-mapping of the Greek function is 50; "2017 class" is 10; "2018 class" is 69; "2016 class" is 53; "cryptography laboratory" is 18.
[0096] (2) When adding new course information, use the public key to encrypt the non-public information M into CT according to the input permission restricti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com