Method and device for controlling permission
A technology of authority control and authority, applied in computer security devices, instruments, digital data authentication, etc., can solve the problems of tediousness, display data business, inability to provide protection for processes, complicated authority control, etc., to achieve simple authority control and extended application scope. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
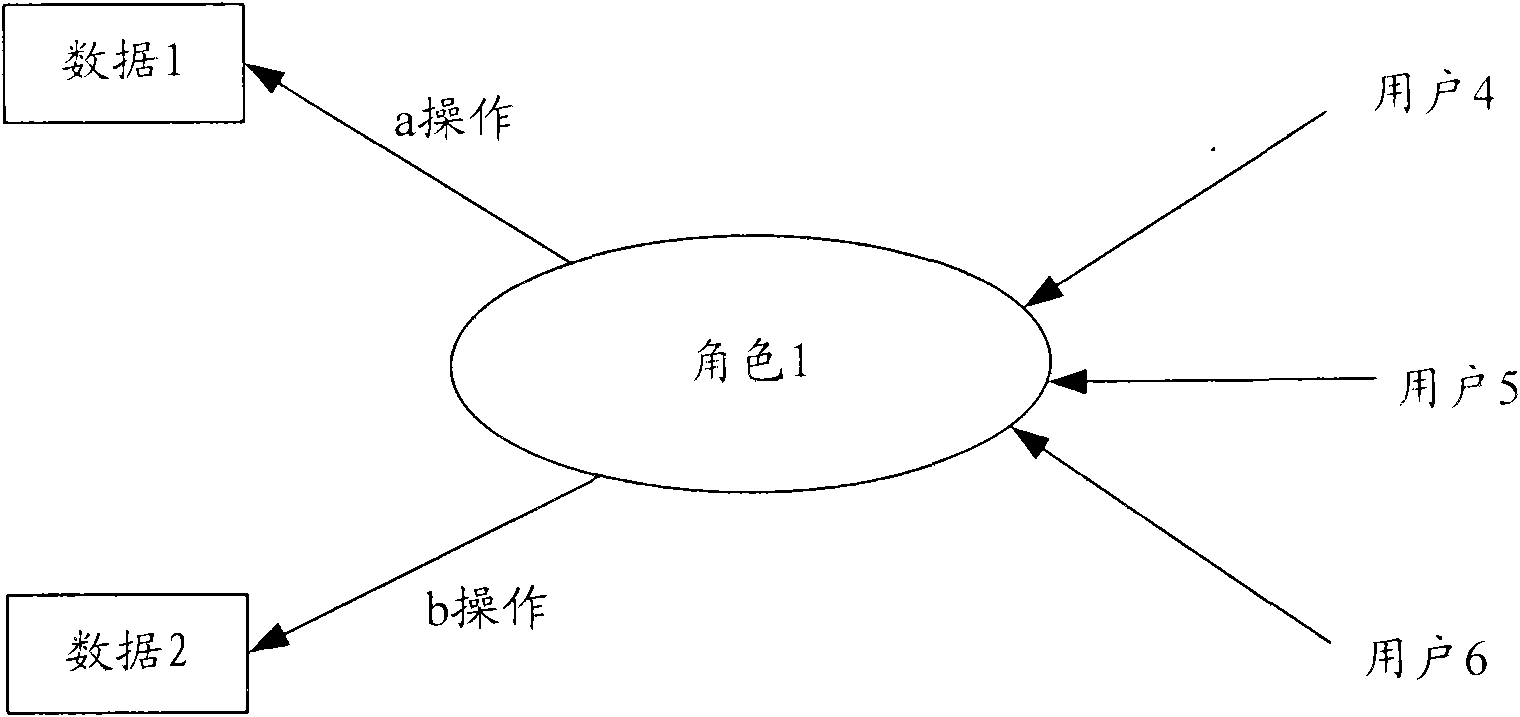
[0053] In this embodiment, only application permissions are assigned to roles, and no data constraints are set.
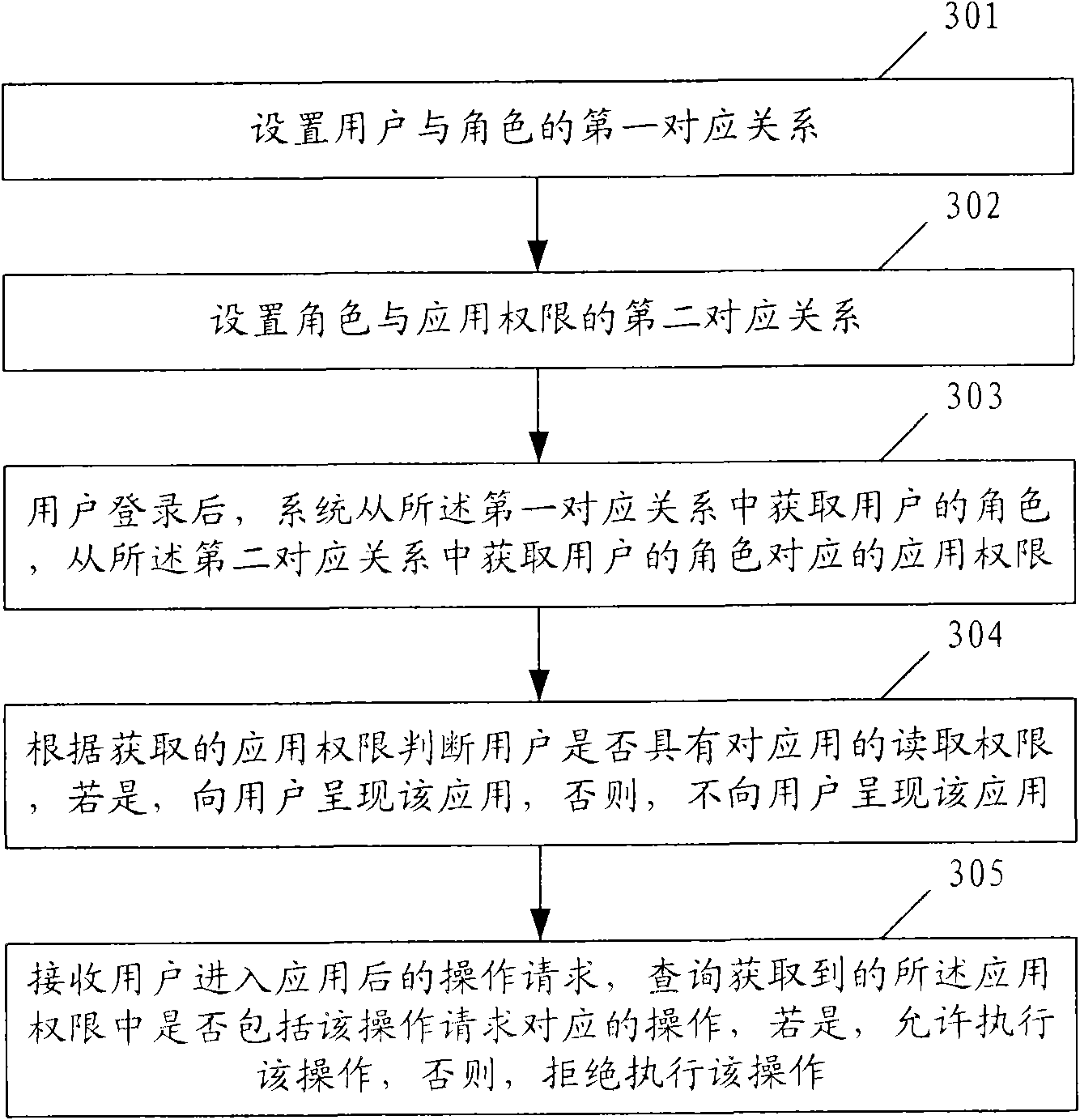
[0054] refer to image 3 , the authority control method of the embodiment of the present invention, comprises the following steps:
[0055] Step 301: Setting the first correspondence between users and roles;
[0056] Step 302: Setting the second corresponding relationship between roles and application permissions;
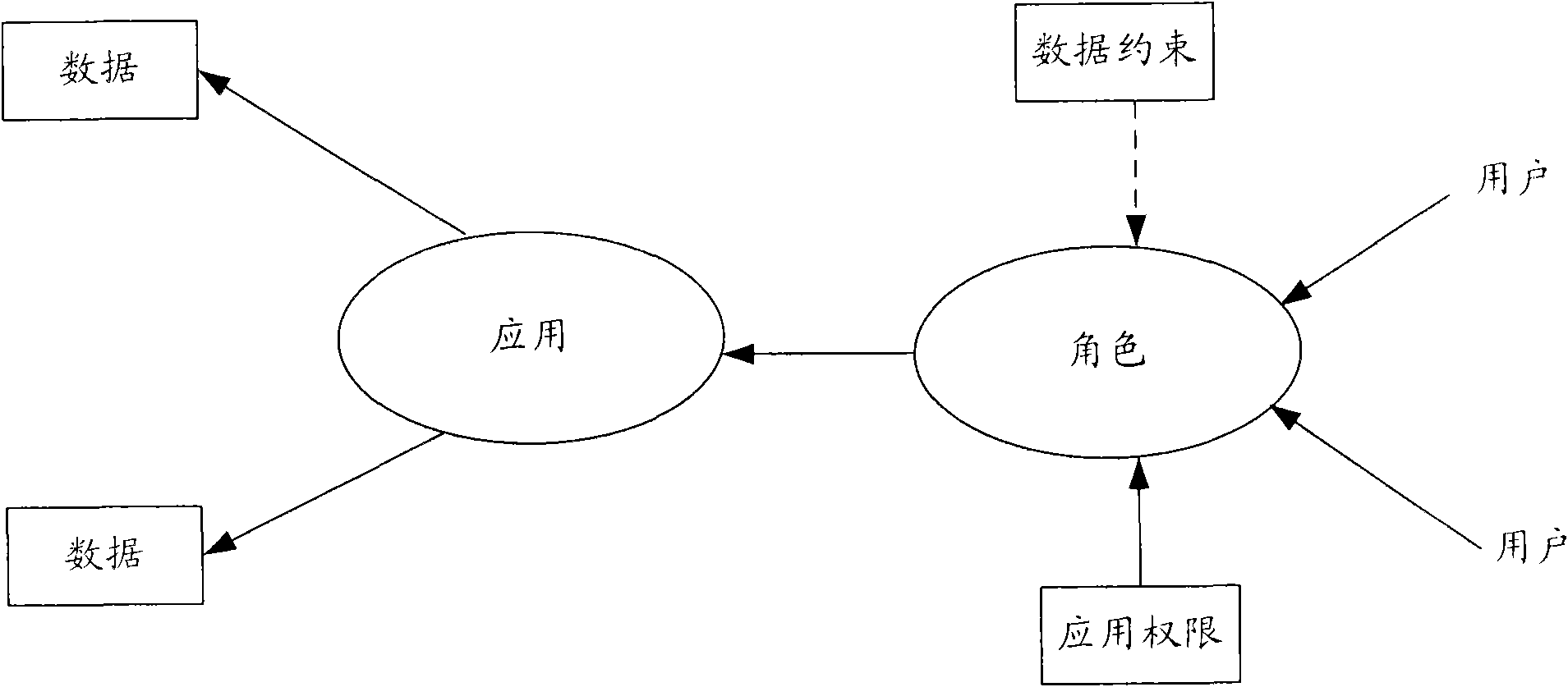
[0057]Application permissions correspond to the system functions and custom functions of the application, and are granted to user roles on the application object. The application permissions corresponding to the system functions of the application include: read (Read), add (Add), delete (Delete) and / or save (Save) permissions, and explain these types of permissions as follows:
[0058] Read: The application can be read. If the role does not have the Read permission for the application, the system will not present the application to the user, so the u...
example 1
[0063] Example 1: Send the corresponding data record to the mobile phone as a text message;
example 2
[0064] Example 2: Send the corresponding data records to the predetermined mailbox by email;
[0065] Example 3: Associate several database tables, generate and present statistical reports according to predetermined rules.
[0066] Step 303: After the user logs in, the system obtains the user's role from the first correspondence, and obtains the application authority corresponding to the user's role from the second correspondence;
[0067] Step 304: Determine whether the user has read permission for the application according to the obtained application permission, if so, present the application to the user, otherwise, do not present the application to the user;
[0068] After the application is presented to the user, the user can enter the application and issue corresponding operation requests; if the application is not applied to the user program, obviously the user cannot enter the application and cannot issue corresponding operation requests.
[0069] Step 305: Receive the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com