Safe USB flash disk and data active protection method thereof
A USB flash drive and security technology, applied in the direction of preventing unauthorized use of memory, etc., can solve the problem that USB flash drives cannot prevent unauthorized users from copying files without authorization, Trojan horses stealing USB flash drive data at will, so as to reduce use risks, enhance security, and protect physical security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
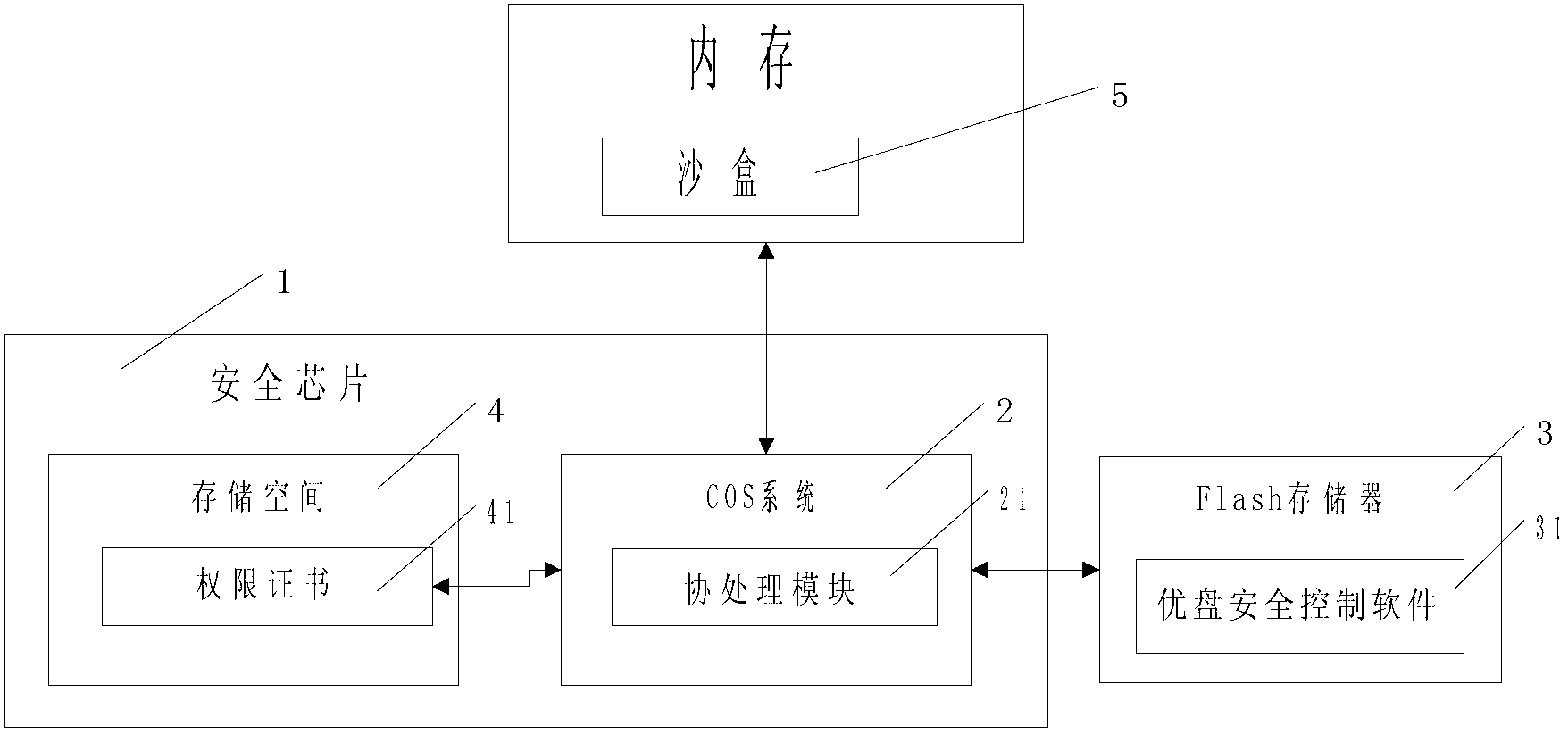
[0065] A. The administrator establishes the account number and password of the "Internet cafe" scenario user in the USB security control software, and sets its authority as "prevent file copying"; the security chip storage space stores the authority certificate of the "Internet cafe" scenario user;
[0066] B. The user connects the USB flash drive to the terminal in the Internet cafe, enters the account number and password of the "Internet cafe" scenario user, compares the USB flash drive with the authority certificate, and the match is qualified;
[0067] C. Click "Create New Document" on the USB flash drive;
[0068] D. The communication protocol module of the COS system compares the authority of the "Internet cafe" scenario user account in the USB security control software in the sandbox, and finds that creating new files is allowed;
[0069] E. A new document is created;
[0070] F. The computer Trojan attempts to copy the files on the USB flash drive;
[0071] G. The CO...
Embodiment 2
[0074] A. The bidder establishes the account number and password of the "bidding" scenario user in the USB security control software, and sets its authority as "prevent file copy, save, delete, modify, print; allow browsing", and the validity period of the certificate is 24 Hours; the storage space of the security chip stores the authority certificate of the "bidding" scenario user;
[0075] B. Send the USB flash drive and the account number and password of the "bidding" scenario user to the bidding party;
[0076] C. The tenderee connects the USB flash drive to the terminal, and the secure USB flash drive management software detects the environmental characteristics of the terminal where no virus or Trojan horse is running, and starts the sandbox control module; receives the input account and password of the "bidding" scenario user, and compares the USB flash drive Authority certificate, matching qualified;
[0077] C. Click "Open Document" on the USB flash drive;
[0078] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com