Control method for accessing computer system and I/0 ports
A computer system and access control technology, applied in the field of computer systems, can solve the problems of inability to disclose secrets, inflexible methods, and inability for users to intuitively understand port disablement, etc., to achieve flexible access control and prevent access control functions.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
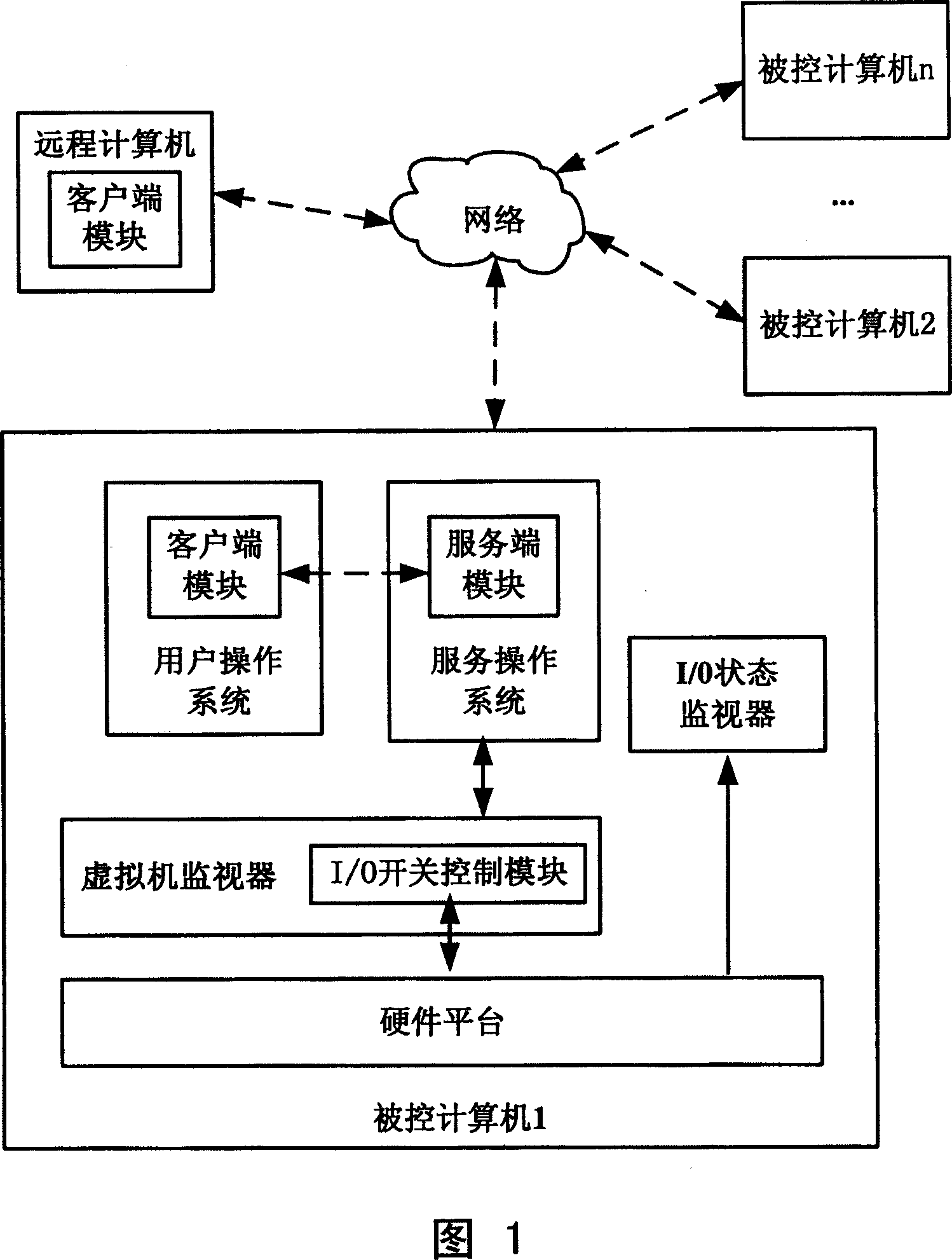
[0040] Fig. 1 shows the structural representation of computer system of the present invention, shown controlled computer comprises service operating system (SOS), user operating system (COS), virtual machine monitor (VMM), I / O state monitor and hardware platform. Among them, the user operating system is the operating system used by the end user, such as widows XP; the service operating system is the operating system that provides various services for the user operating system; the virtual machine monitor is the highest level " Privilege layer ", has the right to control system resources, is used to control the software layer allocated by system hardware resources (processor, memory, other equipment, etc.), and the user operating system and service operating system run on the virtual machine monitor; I The / O status monitor is used to display the current disabled status of the I / O port; wherein, the hardware platform supports virtual computing instructions.
[0041] The above-...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com