Internet of Things private data segmentation encryption method and block chain system
A technology of privacy data and encryption method, applied in the blockchain field, can solve problems such as data unauthorized access, data privacy leakage, separation, etc., and achieve the effect of flexible access control, ensuring privacy security, and ensuring efficient sharing and supervision
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0047] Embodiment 1 of this application introduces a method for segmenting and encrypting privacy data of the Internet of Things.
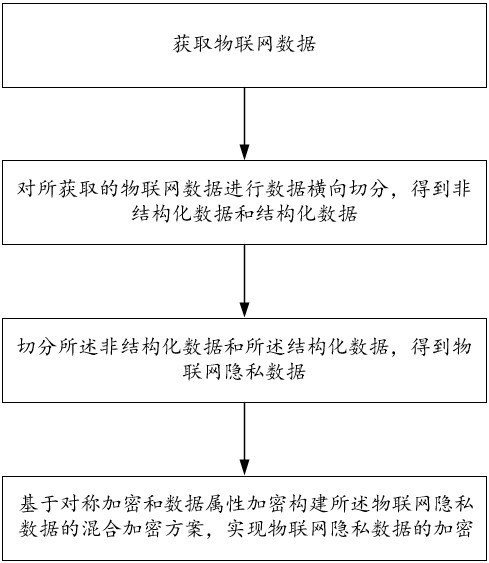
[0048] Such as figure 1 A method for segmenting and encrypting privacy data of the Internet of Things shown, is characterized in that, comprising the following steps:
[0049] Obtain IoT data;
[0050] Carry out data horizontal segmentation on the acquired IoT data to obtain unstructured data and structured data;
[0051] Segmenting the unstructured data and the structured data to obtain IoT privacy data;
[0052] Based on symmetric encryption and data attribute encryption, a hybrid encryption scheme for the privacy data of the Internet of Things is constructed to realize the encryption of privacy data of the Internet of Things.
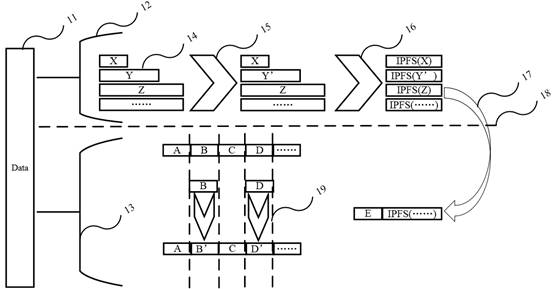
[0053] Collect IoT data based on IoT devices, divide the collected data into structured data and unstructured data, and divide them into public data and private data respectively.
[0054] The segmentation steps of st...
Embodiment 2
[0066] Embodiment 2 of the present application introduces a fine-grained access control method for Internet of Things data, which is implemented on the basis of the method for segmenting and encrypting private Internet of Things data introduced in Embodiment 1.
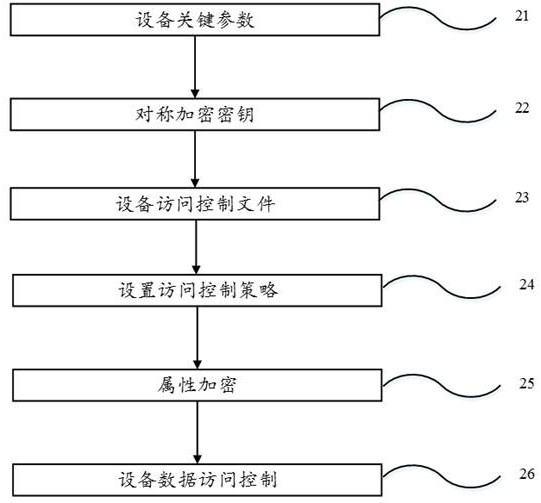
[0067] The fine-grained access control of IoT data is completed when the attributes of the device are encrypted. IoT data sharing is not open to everyone, but needs to be open to people from different organizations, different identities, and different locations, so it needs to be set.
[0068] A fine-grained access control method for Internet of Things data, comprising:
[0069] Step 1, using IoT devices as an effective means of data access control, realizes the binding of data access control and data sources.
[0070] The IoT device as an effective means of data access control specifically includes: the IoT device first registers to the network, and the administrator assigns key parameters such as a key for symmetric...
Embodiment 3
[0094] Embodiment 3 of this application introduces a block chain system for dividing and encrypting privacy data of the Internet of Things.
[0095] Such as Figure 4 An IoT privacy data segmentation encrypted blockchain system is shown, including:
[0096] The acquisition module is configured to obtain the Internet of Things data based on the Internet of Things device;
[0097] The segmentation module is configured to perform data horizontal segmentation on the acquired IoT data to obtain unstructured data and structured data, and segment the unstructured data and the structured data to obtain IoT privacy data ;
[0098] The encryption module is configured to construct a hybrid encryption scheme for the privacy data of the Internet of Things based on symmetric encryption and data attribute encryption, so as to realize the encryption of privacy data of the Internet of Things;
[0099]The fine-grained access control module is configured to set the control authority for Inter...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com