Method for implementing distributed security policy, client terminal and communication system thereof
A security strategy and implementation method technology, applied in transmission systems, network connections, electrical components, etc., can solve problems such as being easily tampered by others, access control failure, etc., and achieve the effect of flexible access control, lightening burden, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
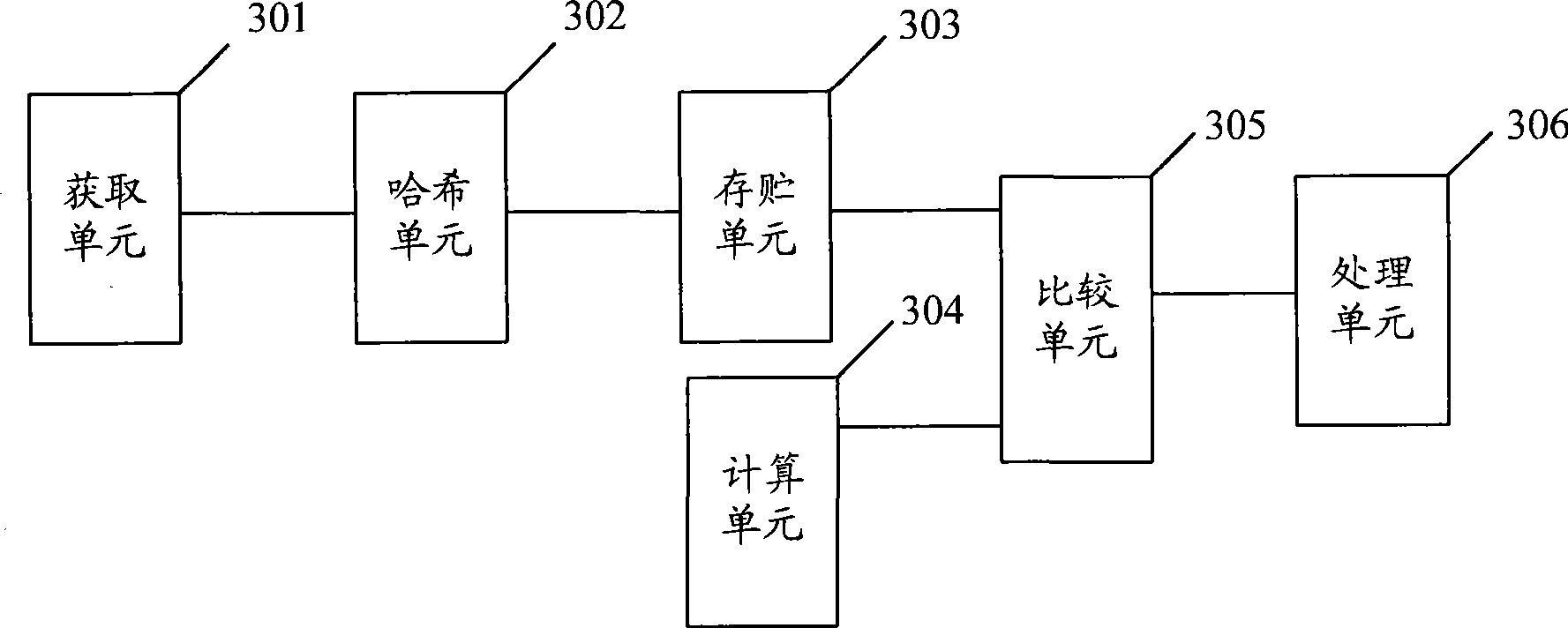
[0040] This embodiment describes a method for implementing a distributed security policy. Through this method, the integrity, confidentiality, and security of the access control list at the client side can be ensured when access control is processed in a distributed manner. A detailed description will be given below in conjunction with the accompanying drawings.
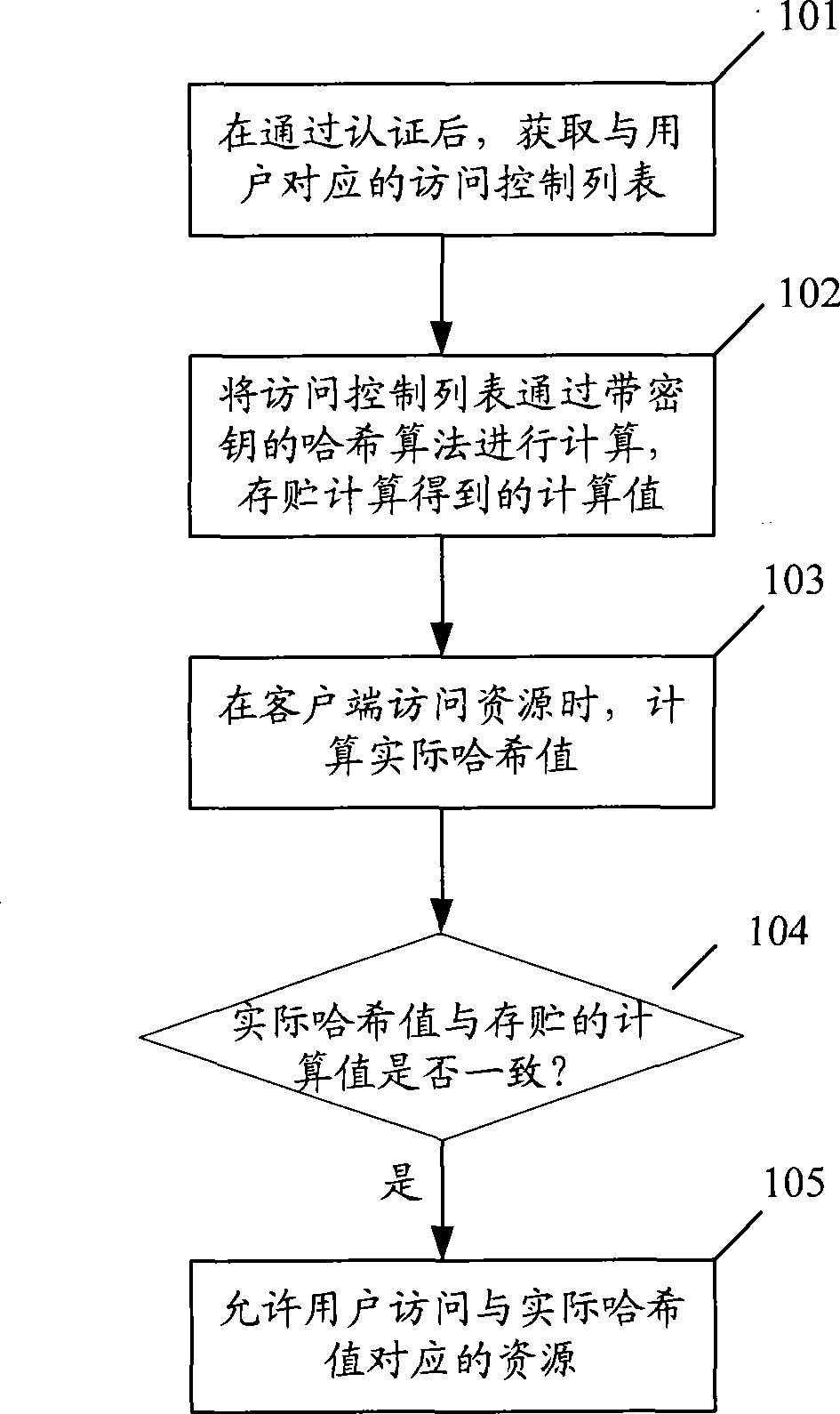
[0041] see figure 1 , the method of this embodiment may include the following steps:
[0042] Step 101: After passing the authentication, obtain the access control list corresponding to the user;
[0043] Before step 101, it may also include:
[0044] Initiate a request to establish a secure socket layer connection to the gateway;
[0045] After establishing the secure socket layer request, sending an authentication request to the gateway;
[0046] If the gateway passes the authentication, go to step 101.
[0047] Step 102: Calculate the access control list through a keyed hash algorithm (HMAC), and store the ca...
Embodiment 2
[0070] This embodiment describes a method for implementing a distributed security policy. Through this method, the integrity, confidentiality, and security of the access control list at the client side can be ensured when access control is processed in a distributed manner. A detailed description will be given below in conjunction with the accompanying drawings.
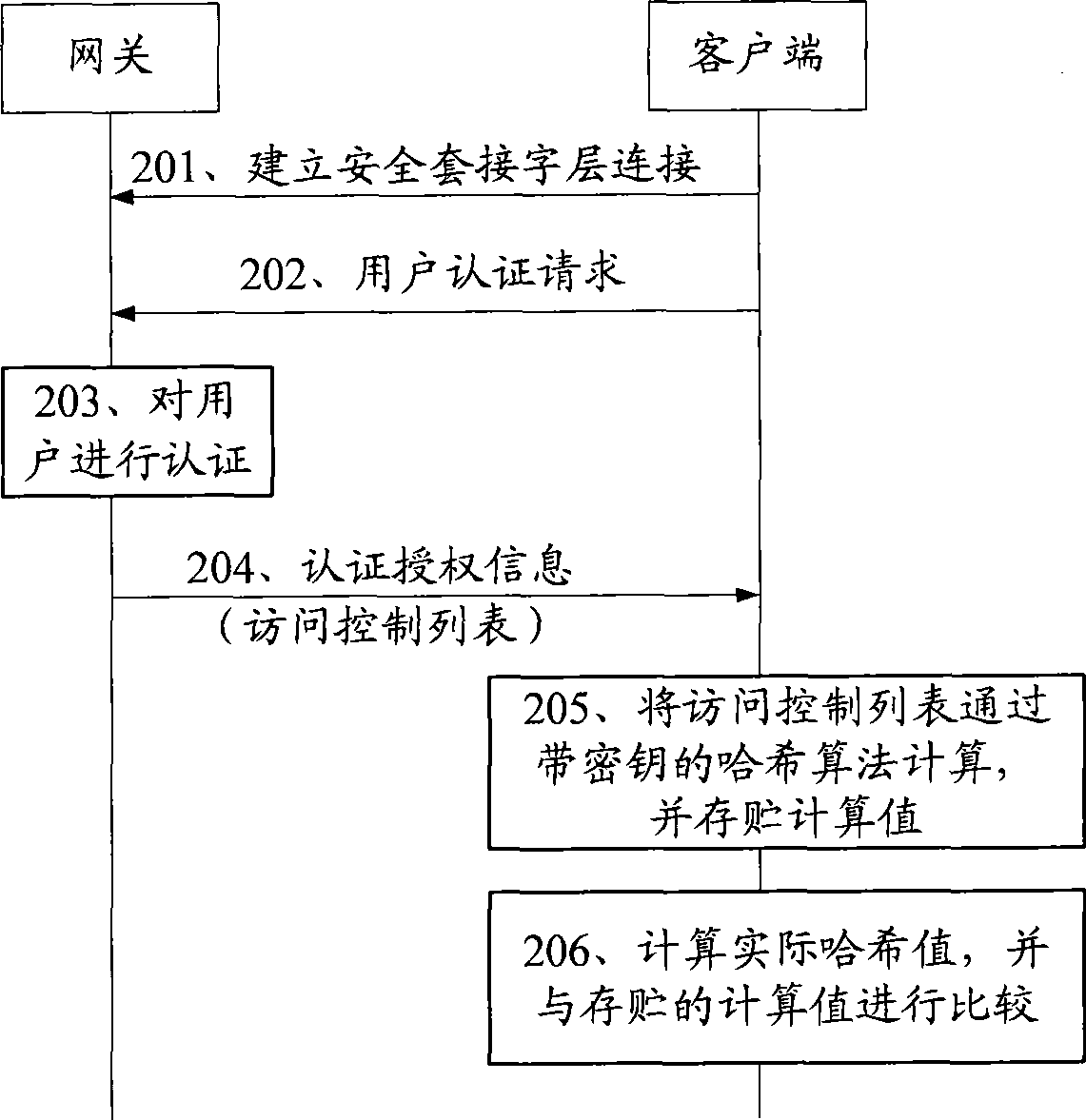
[0071] see figure 2 , the method of this embodiment may include the following steps:
[0072] Step 201: the client establishes an SSL connection with the gateway;
[0073] The client can establish an SSL connection with the gateway by sending an SSL connection establishment request message to the gateway.
[0074] Step 202: the client initiates a user authentication request to the gateway;
[0075] If the client wants to access the security gateway, it first needs to perform user authentication. The client can send a user authentication request message to the gateway, so that the gateway can authenticate the user...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com