Security data storage method and system
A technology for secure data and secure storage, applied in the field of secure data storage methods and systems, to achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment 1
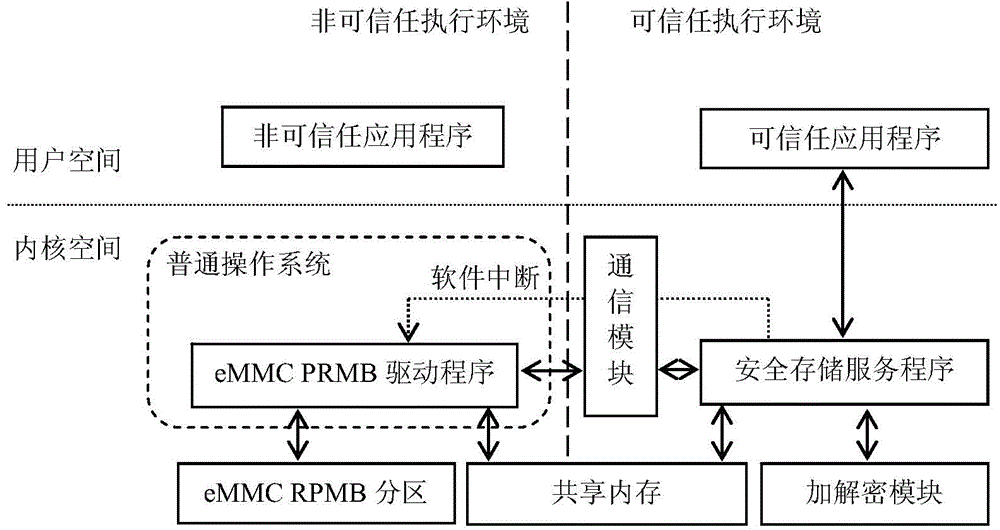
[0069] This embodiment provides an ARM TrustZone-based secure data storage system. The system uses a processor that supports ARM TrustZone, and uses eMMC that supports RPMB as a memory, and is applicable to various consumer electronics embedded platforms such as mobile phones, tablet computers, and digital TVs. see figure 2 As shown, the system software execution environment is isolated into a non-trusted execution environment and a trusted execution environment by ARM TrustZone technology; wherein, the non-trusted execution environment includes a non-trusted operating system (i.e. a common operating system) and an eMMC RPMB driver program; the trusted execution environment includes a communication module, a trusted application program, a secure storage service program and an encryption and decryption module, specifically including:
[0070] The common operating system in this embodiment is responsible for providing necessary system interface support to various application p...
Embodiment 2
[0095] This embodiment provides a method for secure data storage based on ARM TrustZone.
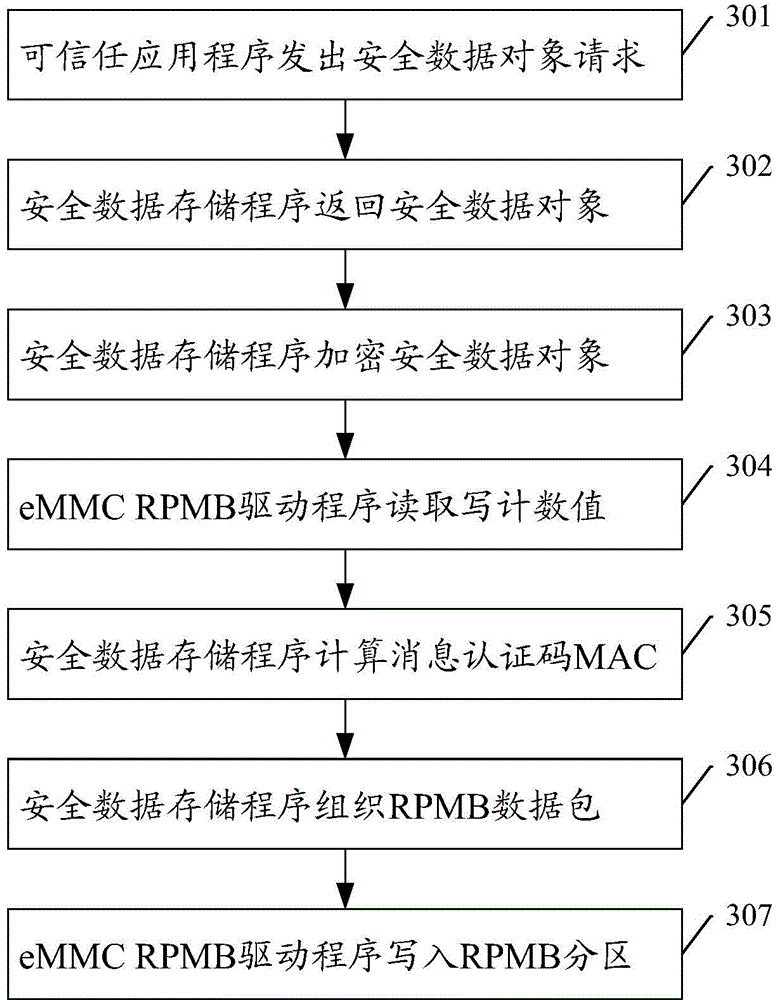
[0096] image 3 The flow chart for creating and storing secure data objects in this example, the steps include:
[0097] Step 301: In the trusted execution environment, the trusted application sends a request for creating, modifying, deleting, etc. a secure data object.
[0098] Step 302: The secure storage service program performs response processing according to the request type of the trusted application program, specifically including:
[0099] For the creation request, find the security data object, if it does not exist, then create a new security data object, otherwise return failure;
[0100] For the modification request, find the security data object, if it exists, then modify the corresponding security data object, otherwise return failure;
[0101] For the delete request, find the security data object, if it exists, delete the corresponding security data object, otherwise re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com