Computer with dual operating systems and implementation method thereof
A dual-operating system, operating system technology, applied in the protection of internal/peripheral computer components, instruments, digital data authentication, etc., can solve the problems of file leakage, inability to encrypt at the disk level, and inability to support multi-system computer encryption processing, etc. The effect of ensuring availability and ensuring system security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0073] The dual operating systems in the computer in Example 1 are dual Win7 dual systems.
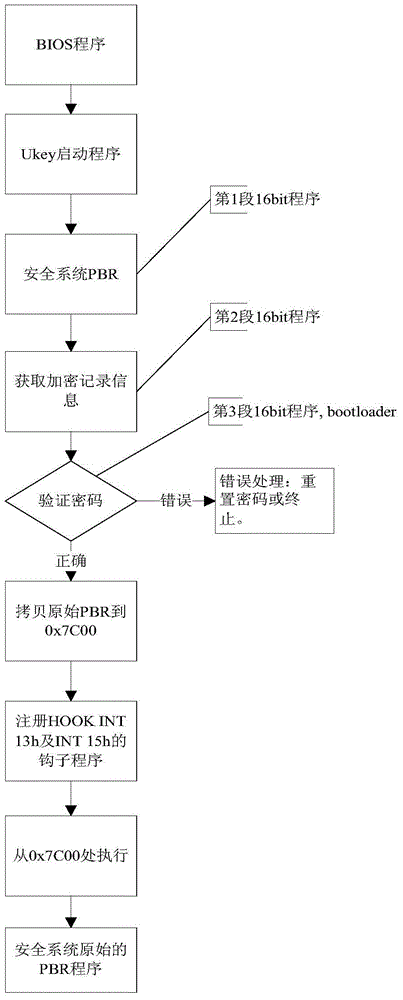
[0074] The detailed implementation process of the technical solution of embodiment 1 is as follows, see attached Figure 4 :
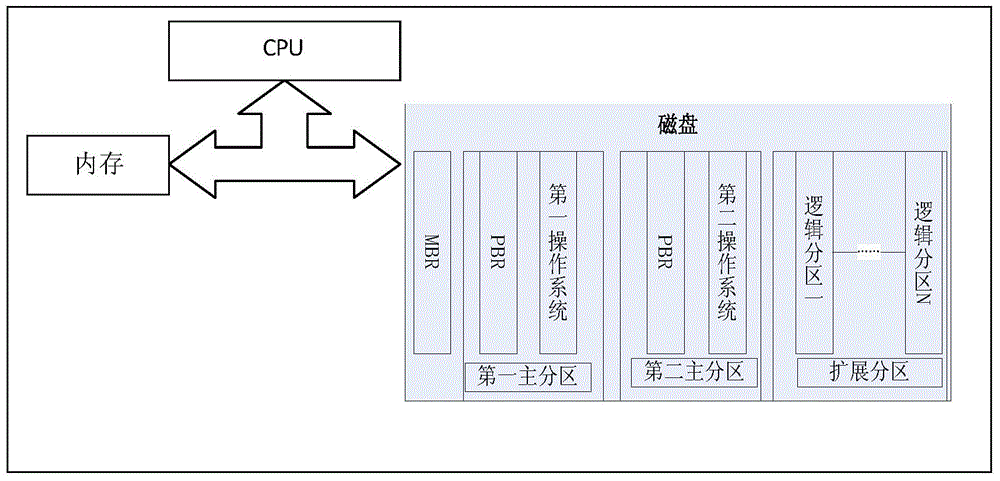
[0075] 1) Partition the hard disk. In this example, the disk is divided into 6 partitions, where C: and D: are the main partition types, and then all the remaining space is created as an extended partition, and then logical partitions E:, F are created separately :, G: and H:.
[0076] Install Win7 A to C: partition and Win7 B to D: partition. The plan is used for the partitions of Win7 A and Win7 B respectively. In this example, partitions C:, E: and F: are used for Win7 A, and partitions D:, G: and H: are used for Win7 B.
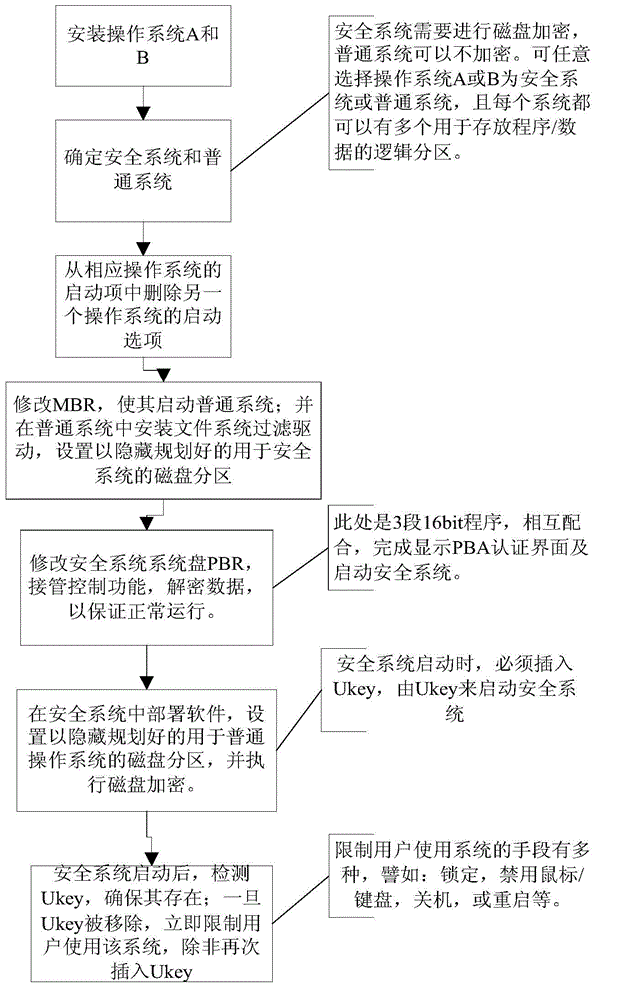
[0077] 2) Make sure that Win7 A is a free system and Win7 B is a safe system.
[0078] 3) Use the bcdedit.exe program that comes with the Win7 system to delete each other's startup items from the startup items of Win7 A and Win7 B.
[0079] 4) Mod...
specific Embodiment 2
[0089] The dual operating systems in the computer in Example 1 are WinXP / Win7 dual systems
[0090] With reference to the above drawings, the detailed implementation process of the technical solution of the second embodiment is described as follows, see attached Figure 5 :
[0091] 1) Partition the hard disk. In this example, the disk is divided into 6 partitions, where C: and D: are the main partition types, and then all the remaining space is created as an extended partition, and then logical partitions E:, F are created separately :, G: and H:.
[0092] Install WinXP to C: partition and Win7 to D: partition. It is planned to be used for WinXP and Win7 partitions respectively. In this example, partitions C:, E: and F: are used for WinXP, and partitions D:, G: and H: are used for Win7.
[0093] 2) Make sure that Win7 is a free system and WinXP is a safe system.
[0094] 3) Use the bcdedit.exe program that comes with the Win7 system to delete the WinXP startup items from the Win7 s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com