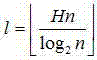Location privacy protection method based on l-inquiry
A privacy protection and query request technology, applied in location-based services, security devices, electrical components, etc., to reduce system resource overhead, prevent intersection operation attacks, and improve security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
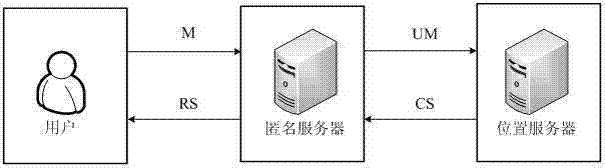
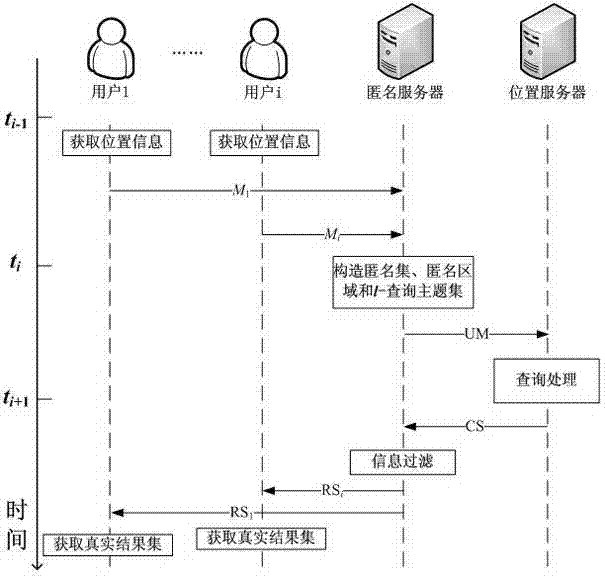
[0019] The invention is based on l -A location privacy protection method for query, comprising the following steps:
[0020] (1) When the user needs location services, initiate a query request to the anonymous server;
[0021] (2) The anonymous server is at the location k - On the basis of anonymity, by combining query requests from the same region at the same time and inserting fake queries, construct a k users and l An anonymous query request for a query subject and submit it to the location server;
[0022] (3) The location server is responsible for l Each query topic is processed one by one, and then the combined result set of the query results is returned to the anonymous server;
[0023] (4) After the anonymous server filters out the false query results from the result set, sorting and secondary refinement are performed according to the query topics of different users, and the final location query results are obtained, and then returned to each user respectively.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com