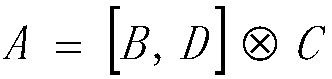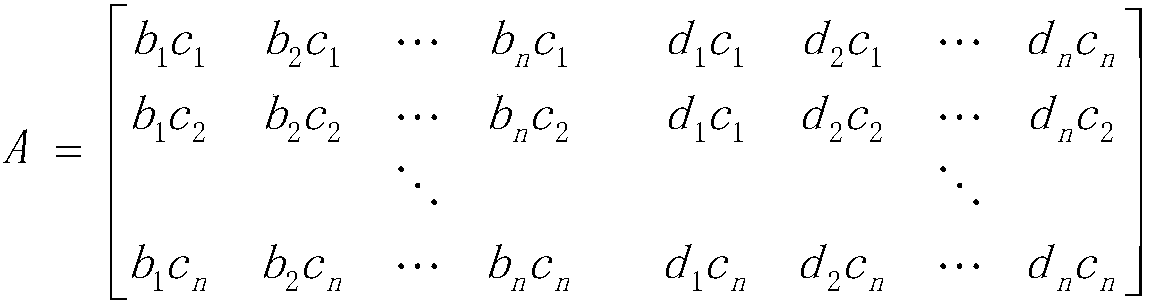Conference system based on digital voice encryption
A conference system, digital voice technology, applied in digital transmission system, transmission system, key distribution, can solve the problem of information security cannot be guaranteed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
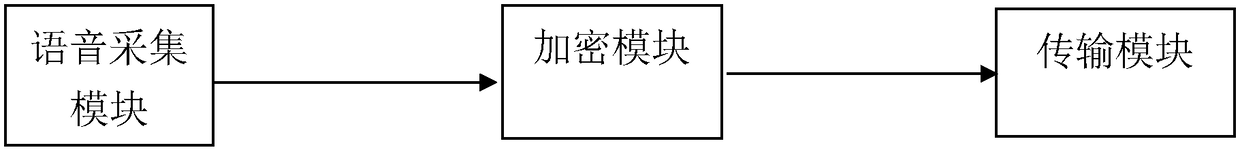
[0035] Such as figure 1 As shown, a conference system based on digital voice encryption, including:
[0036] Voice collection module, used to collect input conference voice signals;
[0037] An encryption module is used to encrypt conference voice signals;
[0038] The transmission module is used to transmit the encrypted voice signal based on the B / S structure to the conference call.
[0039] Preferably, the encryption module encrypts the above-mentioned voice signal in the following manner: assuming that N initial signals s 1 (t),...,s n (t) and M key signals k 1 (t),...,k M (t), the encryption formula is:
[0040] X(t)=[x 1 (t),...,x N (t)] T =As k (t)
[0041] Among them, X(t) represents N encrypted signals, s k (t)=[s 1 (t),...,s n (t),k M (t)] T , A is an encrypted matrix of N×(M+N), and each value is between [-1,1]. Let A=[A S ,A k ], where A S is an N×N matrix, A k It is an N×M matrix, and the encryption formula is expressed by the following formul...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com