Method and device for intercepting resource requests
A resource request and resource technology, applied in the field of computer security, can solve problems such as HTTP request interception errors
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
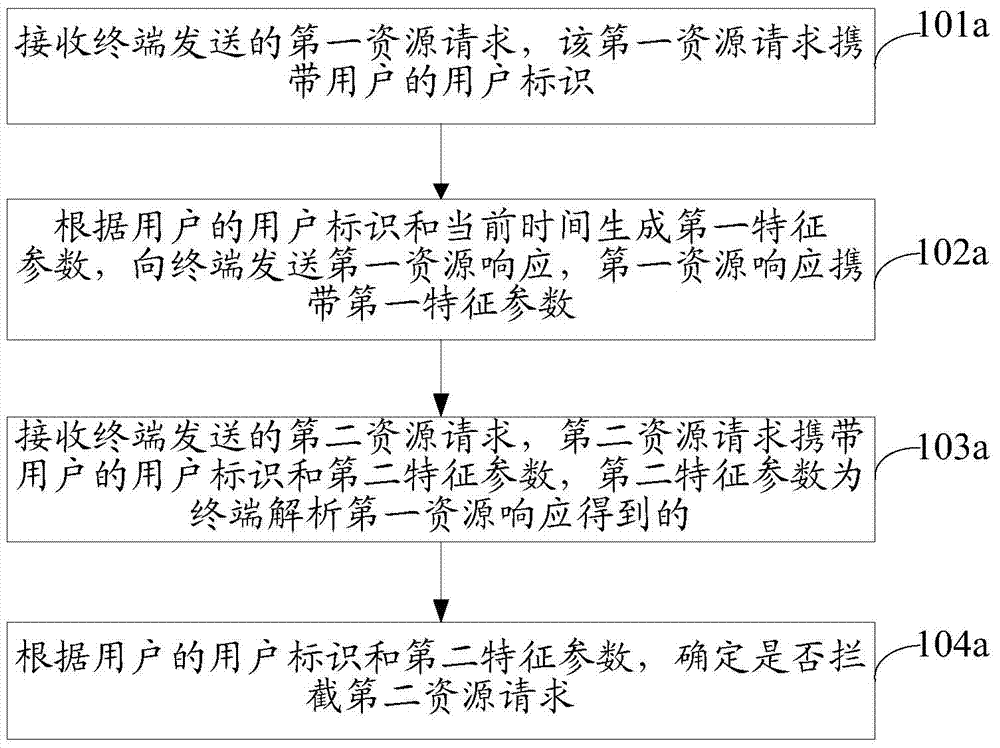
[0090] The embodiment of the present invention provides a method for intercepting resource requests, the execution subject of the method is a server, see Picture 1-1 , where the method includes:
[0091] Step 101a: receiving the first resource request sent by the terminal, the first resource request carrying the user ID of the user;
[0092] Step 102a: Generate a first feature parameter according to the user ID of the user and the current time, and send a first resource response to the terminal, where the first resource response carries the first feature parameter;
[0093] Step 103a: receiving the second resource request sent by the terminal, the second resource request carries the user ID of the user and a second characteristic parameter, and the second characteristic parameter is obtained by the terminal parsing the first resource response;
[0094] Step 104a: Determine whether to intercept the second resource request according to the user ID of the user and the second fea...
Embodiment 2
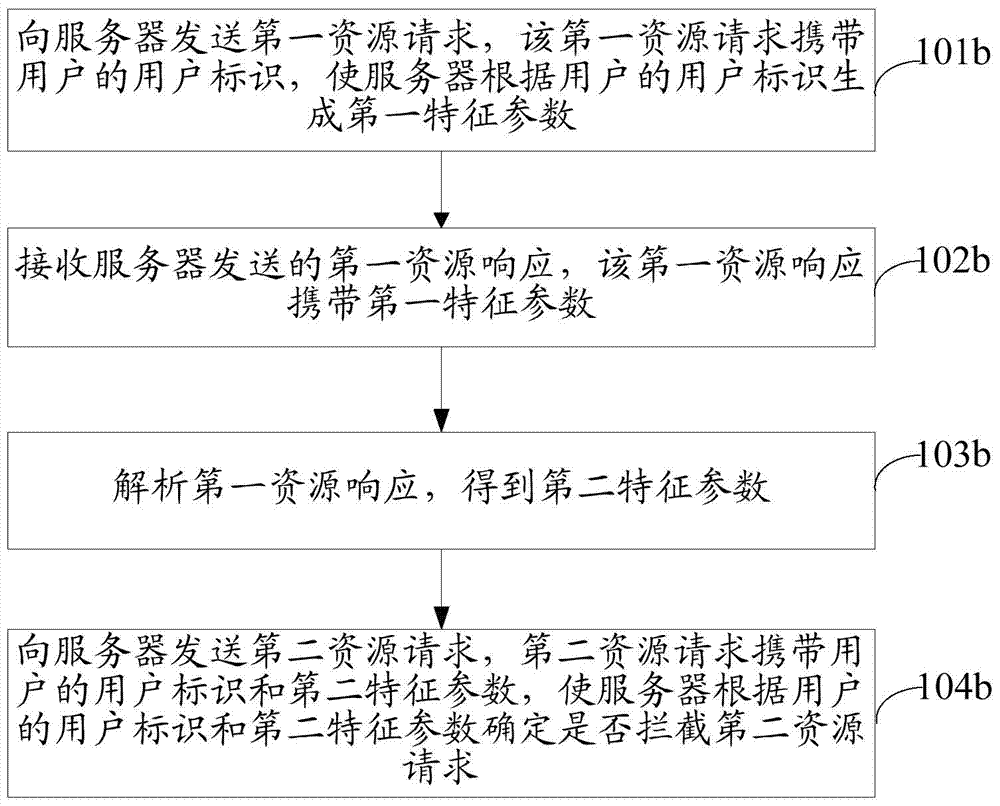
[0102] The embodiment of the present invention provides a method for intercepting resource requests.
[0103] Users can send resource requests to the server through the terminal to request the resources included in the server. However, in order to improve the efficiency of obtaining resources, many users do not manually send resource requests to the server through the browser, but use the A bot simulates a user sending a resource request to request a resource included in the server. For example, when a user participates in an online snap-up activity, in order to snap up a product as soon as possible, the user sends a resource request to the server by using a snap-up program. Since automatic programs send resource requests much faster than users manually send resource requests, if a user manually sends a resource request, the automatic program may send dozens or even hundreds of resource requests, which not only increases the burden on the server, but also affects the user. It...
Embodiment 3
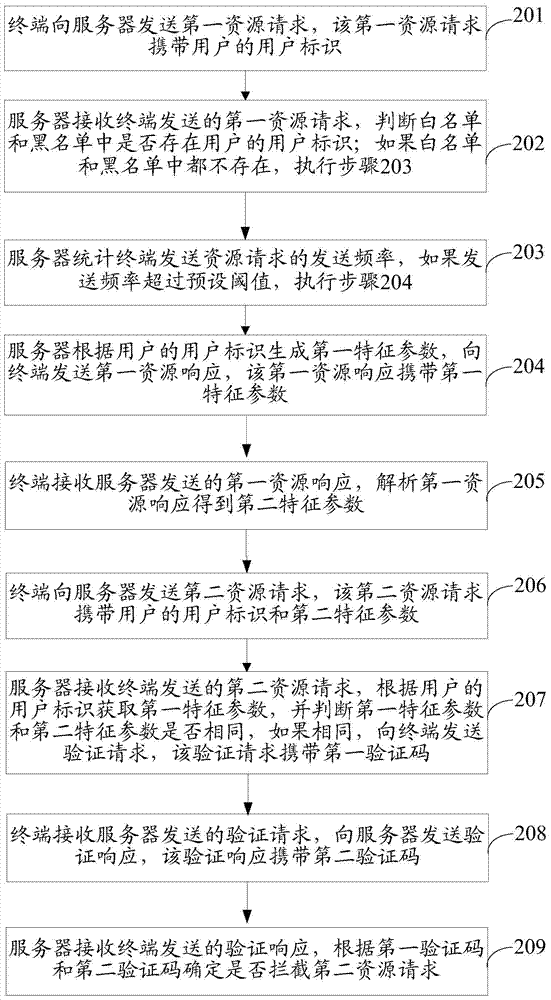
[0161] An embodiment of the present invention provides a device for intercepting resource requests, see image 3 , the device consists of:
[0162] The first receiving module 301 is configured to receive a first resource request sent by the terminal, where the first resource request carries a user identifier of the user;
[0163] A generating module 302, configured to generate a first characteristic parameter according to the user identifier of the user and the current time, and send a first resource response to the terminal, where the first resource response carries the first characteristic parameter;
[0164] The second receiving module 303 is configured to receive a second resource request sent by the terminal, where the second resource request carries the user ID of the user and a second feature parameter, and the second feature parameter is obtained by the terminal by parsing the first resource response;
[0165] A determining module 304, configured to determine whether ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com