Multi-user collaboration jamming power distribution method under restraint of confidentiality interrupt probability
A technology of multi-user cooperation and interference power, which is applied in the field of multi-user cooperation interference power allocation, and can solve problems such as not applicable to cellular mobile communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
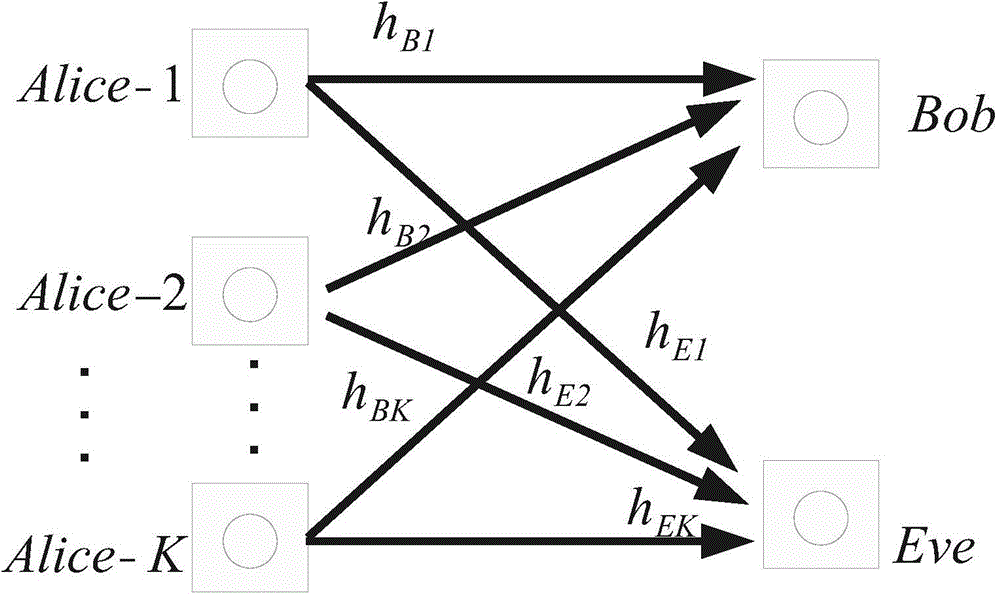
[0021] Such as figure 1 As shown, the communication system model that the present invention adopts comprises: K single-antenna transmitting ends, respectively Alice-1, ..., Alice-K, a single-antenna expected receiving end Bob and a single-antenna eavesdropping end Eve, transmitting user Alice -1 forms a communication pair with the expected receiver Bob. Remember h B,i is the channel coefficient from Alice-i to Bob, h E,i Indicates the channel coefficient from Alice-i to Eve, assuming that the wireless channel fades slowly and is modeled as quasi-static Rayleigh fading, h B,i and h E,i are independent of each other, and all obey the complex Gaussian distribution with a mean value of zero, and their distributions are denoted as h B,i ~CN(0,Γ B,i ) and h E,i ~CN(0,Γ E,i ), where Γ B,i >0 and Γ E,i >0, indicating the variance of the complex Gaussian distribution, reflecting the large-scale fading of the channel. During the communication process, Alice-1 is fixed to trans...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com