Public key password system based LTE wireless network security certification system
A public-key cryptosystem and security authentication technology, which is applied in wireless communication, security devices, electrical components, etc., can solve the problems of insufficient security, cost, and poor scalability, so as to improve scalability and enhance security , the effect of high flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment 1
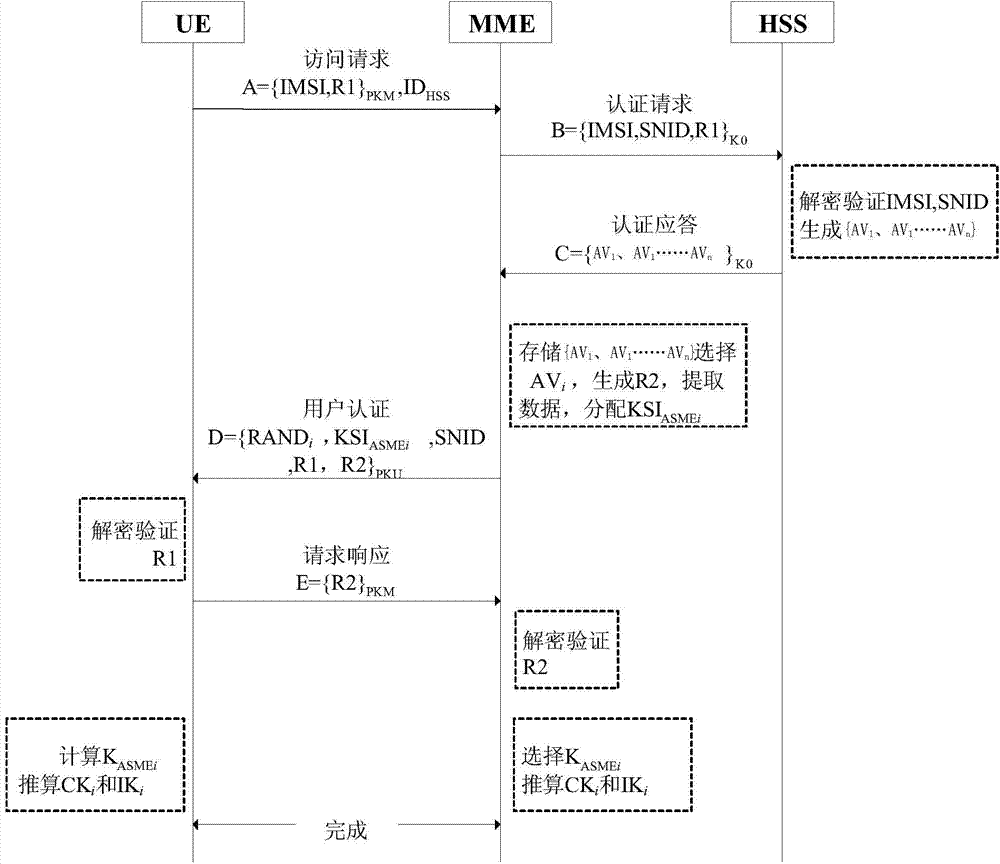
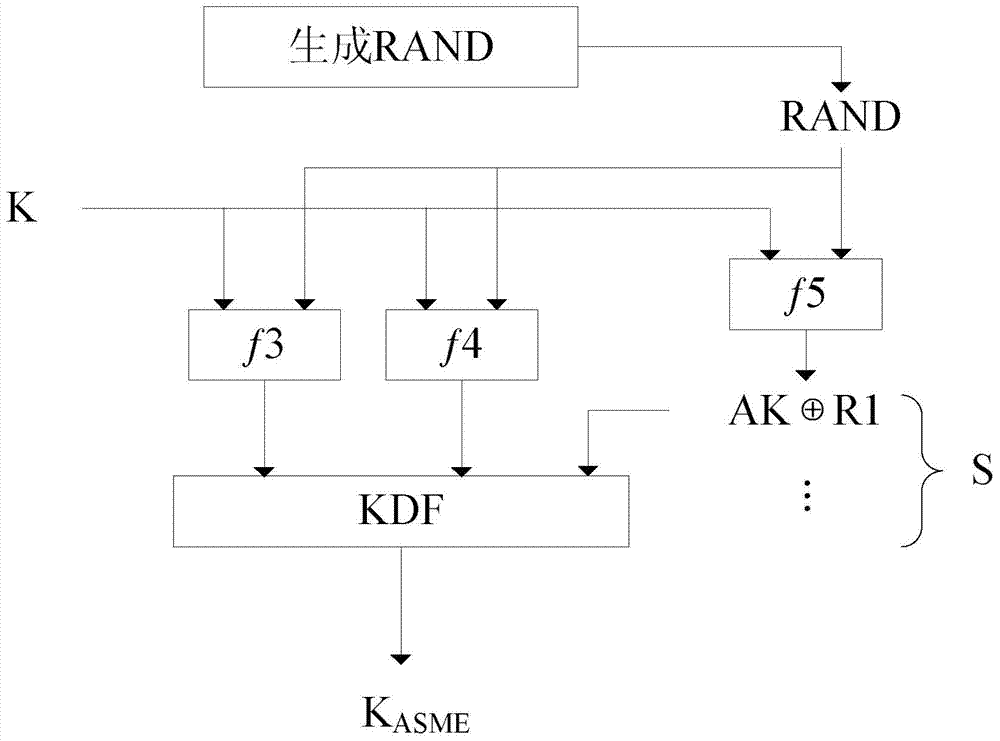
[0028] Such as figure 1 As shown, the authentication and key agreement process of the protocol is improved in the present invention. There are three entities involved in authentication and key negotiation: UE, MME and HSS. K represents the shared key between UE and HSS, K0 represents the pre-shared symmetric key between MME and HSS, PKU and PKM represent the public keys of UE and MME respectively, and PKU -1 , PKM -1 Denote the private keys of UE and MME respectively.
[0029] The concrete steps that adopt the method provided by the invention to carry out security authentication are:
[0030] (1) The UE initiates an access request to the MME. The request contains the UE's HSS ID HSS , IMSI and R1 encrypted with the MME public key PKM. Wherein, R1 is a random number generated by the UE, which is used for identity verification and participation in key generation.
[0031] (2) After the MME receives the UE's access request message, it decrypts to obtain the IMSI and the ra...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com