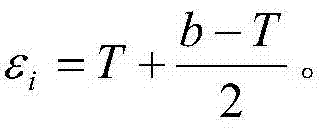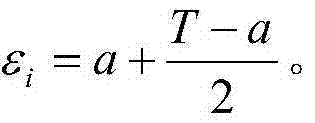Access control method based on dynamic trust thresholds
An access control and trust value technology, applied in the direction of electrical components, transmission systems, etc., can solve the problems of not being able to obtain all information, and the access control technology based on identity or role cannot fully meet the security needs of an open dynamic network, so as to ensure security performance and meet the needs of dynamic access control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
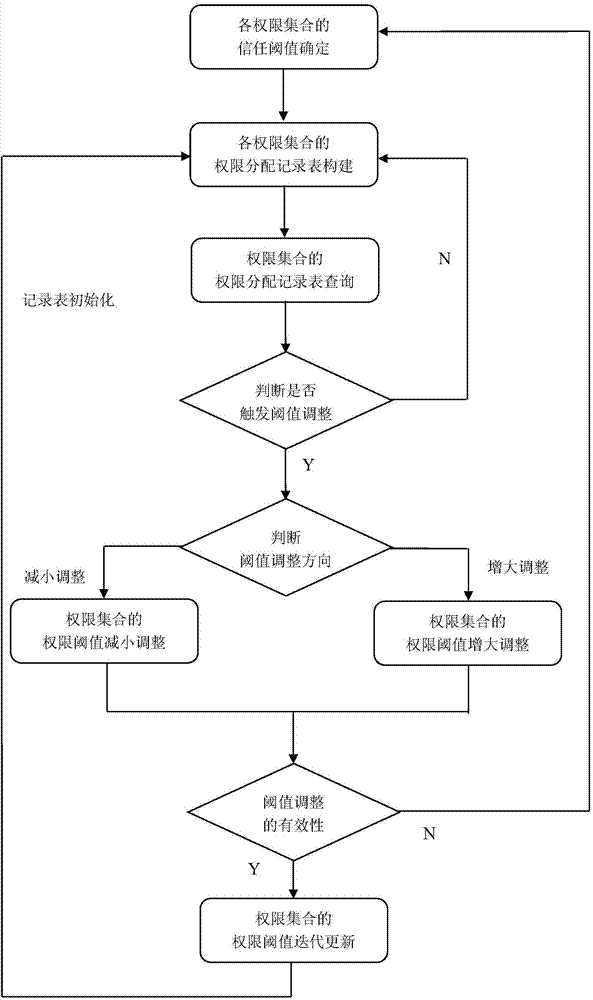
[0033] The present invention will be described in detail below through specific embodiments.
[0034] Specific application examples:
[0035] (1) All permissions that can be assigned to the subject for the file File are: Read, Write, Modify, Print, Copy, and the trust thresholds of the corresponding permissions are: ε_read=0.4, ε_write=0.7, ε_modify=0.9, ε_print= 0.5, ε_copy=0.7.
[0036] (2) The permission sets of the file File are: R 0 ={Read},R 1 ={Print},R 2 = {Write, Copy}, R 3 ={Modify}, the trust thresholds of the corresponding permission sets are: ε 0 = 0.4, ε 1 = 0.5, ε 2 =0.7,ε 3 = 0.9.
[0037] (3) The file File has an allocation record table for each permission set, that is, it has 4 permission set allocation record tables. The structure of the allocation record table of each authority set is: subject identification, subject trust value, access authority, and access feedback evaluation. Each record in the allocation record table stores the details of eac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com