Cloud computing identity authentication method
An identity authentication and cloud computing technology, applied in the field of cloud computing security, to achieve the effect of easy-to-use and friendly, convenient access control, and make up for potential security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
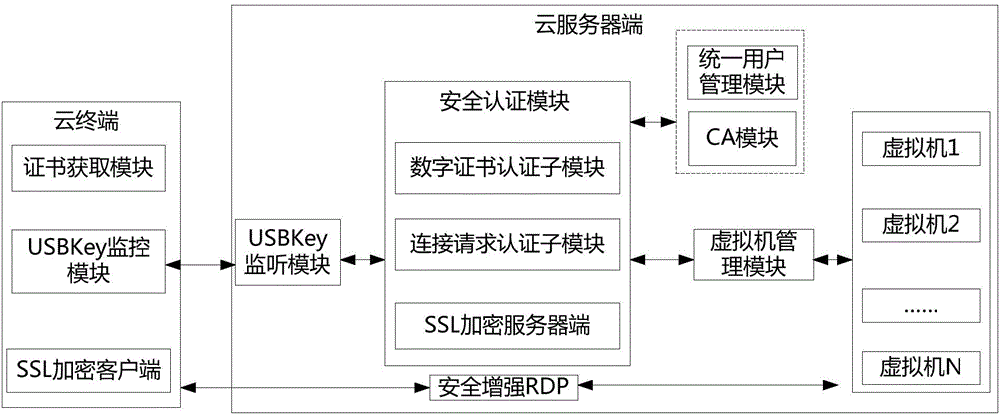
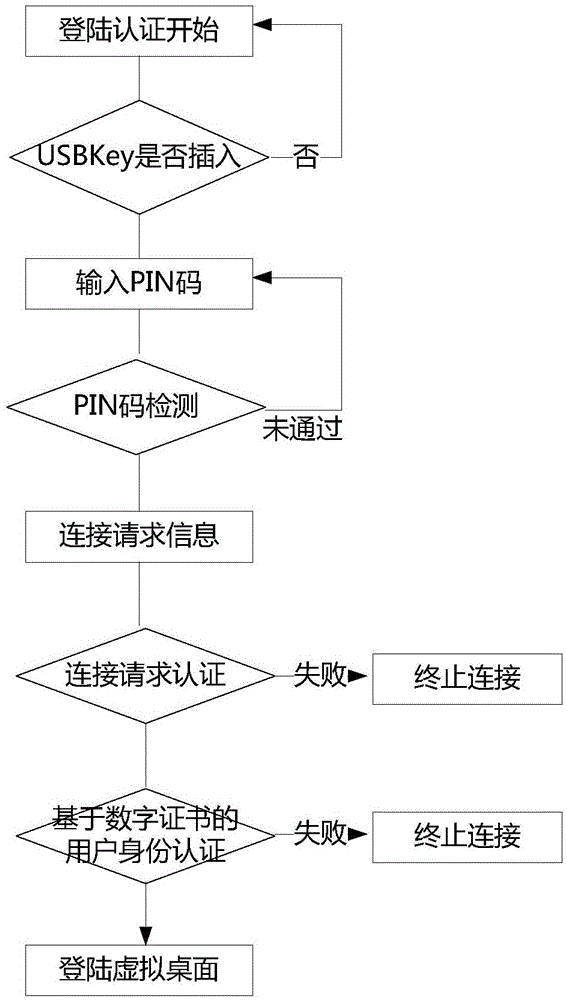
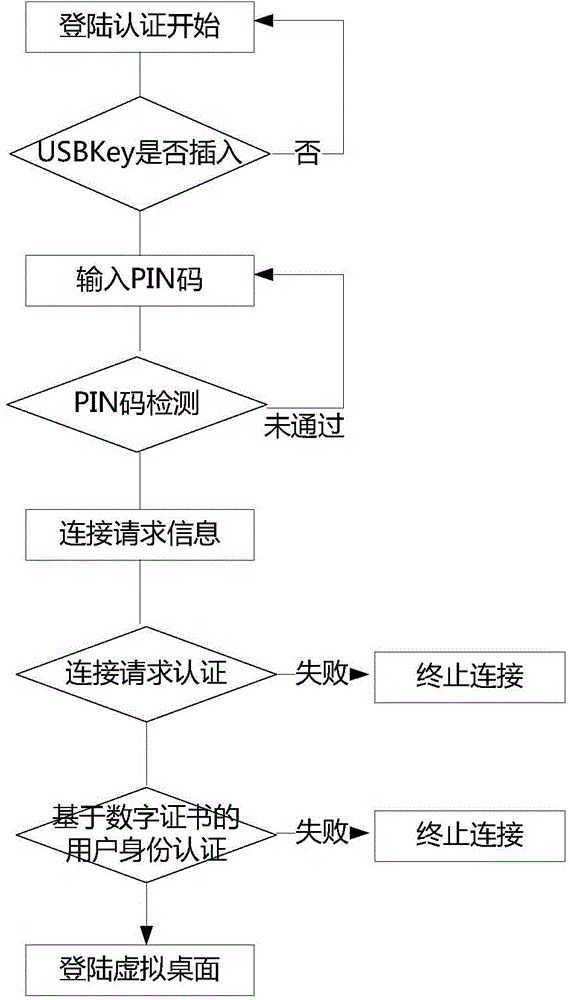
[0037] The invention provides a cloud computing identity authentication method based on USBKey and security-enhanced RDP. The method uses USBKey as a password device, uses digital certificate technology, SSL (Secure Socket Layer, secure socket layer) encryption technology, and securely enhances Remote Desktop Protocol RDP (Remote Desktop Protocol, Remote Desktop Protocol), by deploying security components on cloud terminals and cloud servers respectively, realizes strong identity authentication for cloud terminal users logging in to cloud servers and security authentication for virtual desktop users.
[0038] The present invention will use the USBKey in the cloud terminal (TC or traditional PC terminal), use the "USBKEY+PIN code" method to realize "two-factor" strong identity authentication, and combine the digital certificate technology to enhance the security of the existing RDP protocol, Map the USBKey device of the cloud terminal to the virtual desktop in a safe and control...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com