Network equipment behavior analysis method and system
A network device and behavior analysis technology, applied in the field of information network security, can solve problems such as undetectable abnormalities, and achieve the effect of overcoming prevention and monitoring
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
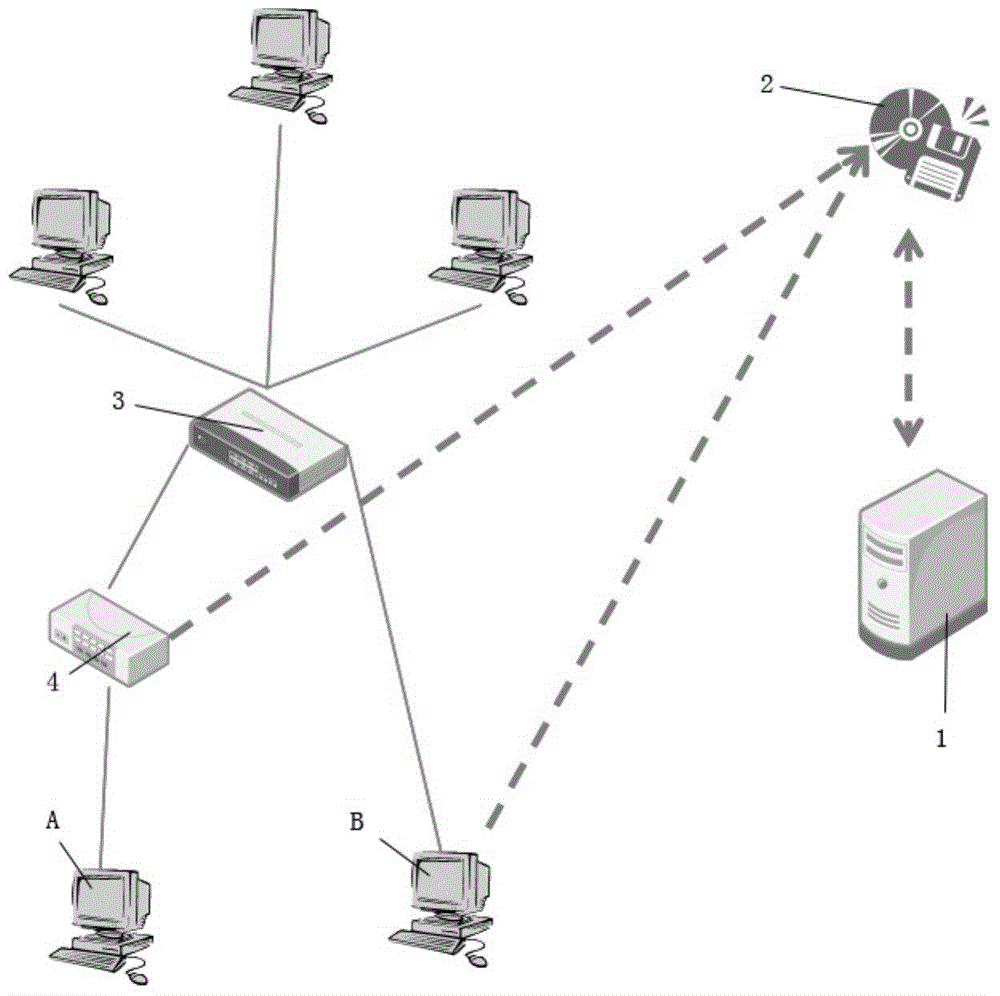
[0020] Such as figure 1 As shown, the data storage device 2 can exchange data with the behavior analysis engine 1, and the data collection device 4 is connected to the data storage device 2 and provides the data storage device 2 with network data of the user device A. The user equipment B directly provides its own network data to the data storage device 2, and the switch 3 ensures the communication of all user equipment. The network device behavior analysis method of the present invention is divided into the following two stages:
[0021] 1. Build a behavioral model
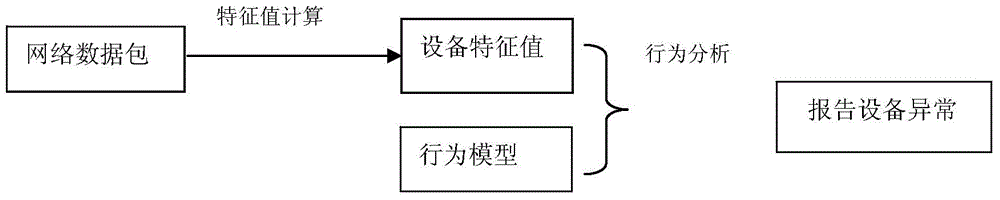
[0022] Such as figure 2 In the illustrated process of establishing a behavior model for network devices, the data collection device 4 and the user device B collect data packets received and / or sent during a period of time when the user devices A and B are in a normal working state. The analysis engine 1 quantifies the collected data packets into characteristic values that contain multiple attributes. The character...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com