An access control system based on two-dimensional code
An access control system, two-dimensional code technology, applied in the direction of instruments, time register, single input port/output port register, etc., can solve the problems of unsuitable promotion, no personal identity information in the card, complicated work and so on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
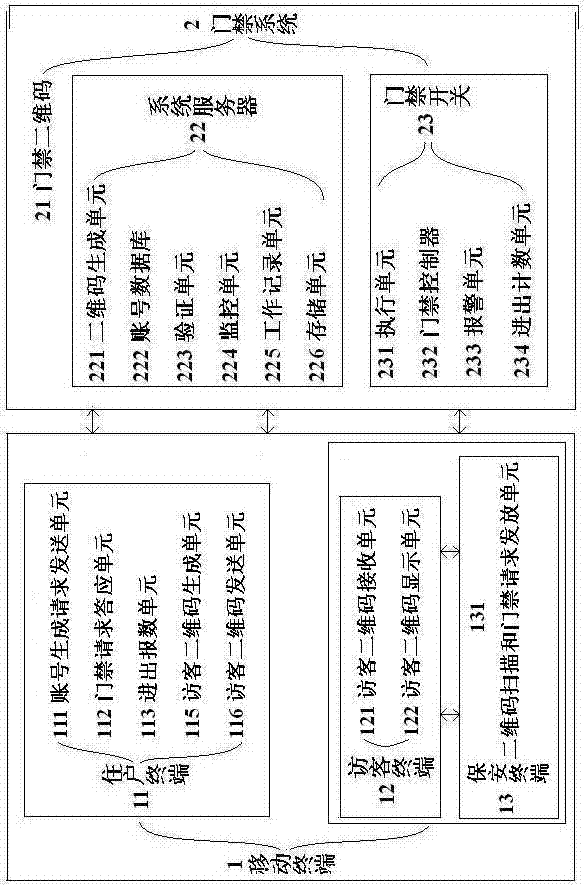
[0028] Develop and install a two-dimensional code-based access control system, including a mobile terminal 1 and an access control system 2, wherein the mobile terminal 1 includes a resident terminal 11, and the access control system 2 includes an access control QR code 21, a system server 22 and an access control system. switch 23.
[0029] The resident terminal 11 includes an account number generation request sending unit 111 and an access control request acknowledgment unit 112; the account number generation request sending unit 111 is that the owner mobile terminal 1 sends the mobile phone code and the bound resident room number to the system server 22 and then generates a resident terminal account, so that the identification information of the mobile terminal 1 is filed with the system server 22; the access control request acceptance unit 112 is that the owner mobile terminal 1 scans the access control two-dimensional code 21 and then sends the access request information t...
Embodiment 2
[0039] The mobile terminal 1 in the access control system based on the two-dimensional code in embodiment 1 is used as the owner's mobile terminal 11, and a visitor terminal 12 and a security terminal 13 are added in addition; the resident terminal 11 also includes a visitor two-dimensional code generating unit 115 and a visitor Two-dimensional code sending unit 116, the visitor terminal 12 includes a visitor two-dimensional code receiving unit 121, a visitor two-dimensional code display unit 122, and the security terminal 13 includes a two-dimensional code scanning and access control request issuing unit 131.
[0040]The visitor two-dimensional code generation unit 115 is used for the owner to receive the code of the visitor terminal 12, bind the code of the visitor terminal with the owner code, generate a visitor two-dimensional code for opening the access control switch, and store it in the system server 22 superior.
[0041] The visitor two-dimensional code sending unit 11...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com