Recording encryption and decryption method and device
A technology for encrypting and decrypting and recording files, applied in the field of recording encryption and decryption methods and devices, can solve the problems of privacy leakage, low security, loss, etc., and achieve the effect of ensuring security and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
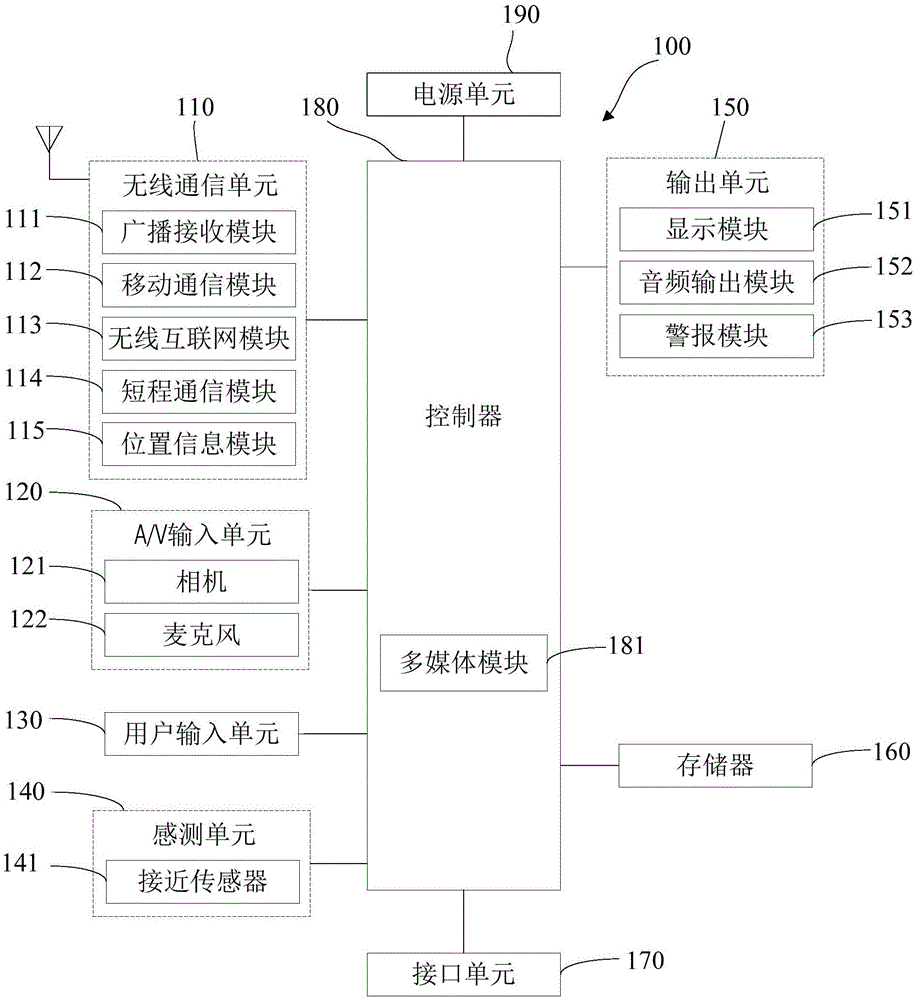
Image
Examples
no. 1 example
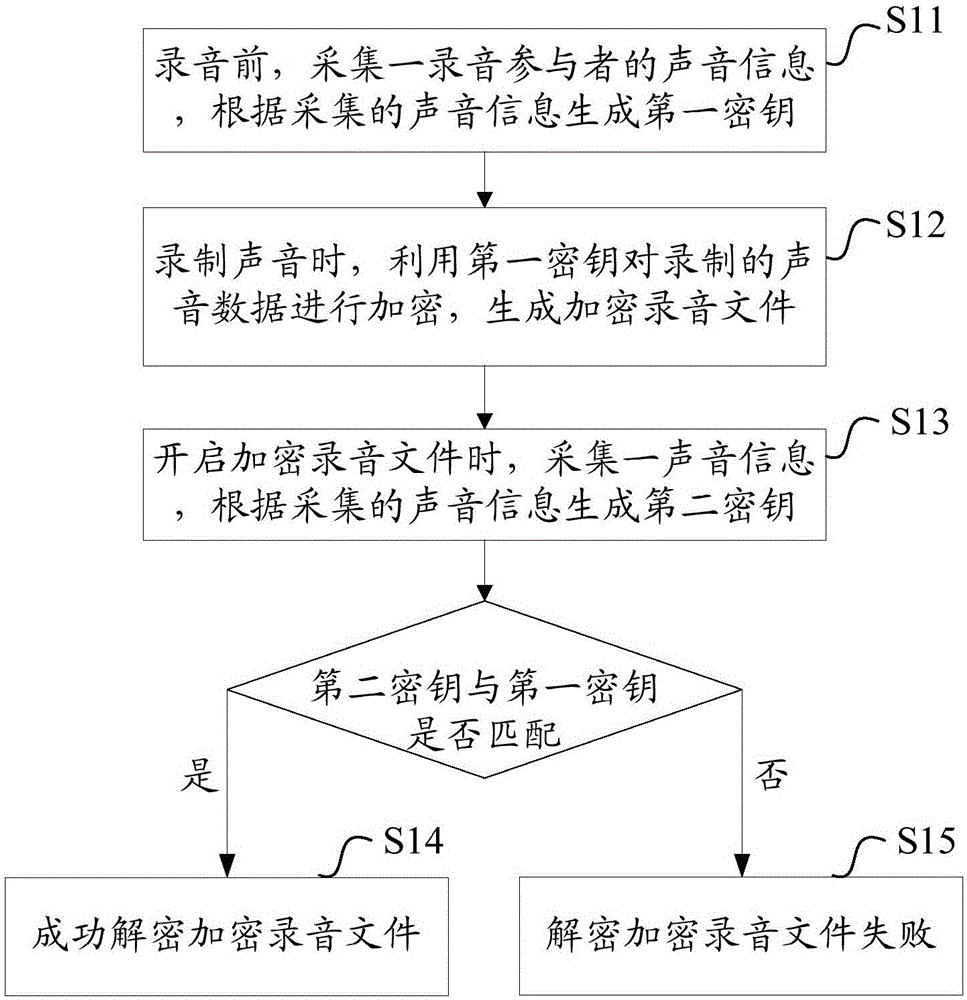
[0064] see figure 1 , propose the first embodiment of the recording encryption and decryption method of the present invention, the method includes the following steps:
[0065] S11. Before recording, collect voice information of a recording participant, and generate a first key according to the collected voice information.
[0066] This step S11 is the preparatory process before the recording, and before the recording officially starts, the first key is firstly set. Specifically, prompting a recording participant to make a sound, collecting the voice information of the recording participant, and then using a common algorithm to generate the voice information into a first key, and the first key is used to encrypt subsequent recordings.
[0067] For example, through the frequency information of the collected sound, the frequency is converted into a corresponding binary data string, and then the binary string is repeated twice, and 1 is added to obtain the first key. For exampl...
no. 2 example
[0081] see figure 2 , propose the second embodiment of the recording encryption and decryption method of the present invention, the method includes the following steps:
[0082] S21. Before recording, respectively collect voice information of two recording participants, and generate a first key according to the collected two voice information.
[0083] This step S21 is the preparatory process before the recording, and before the recording officially starts, the first key is firstly set. Specifically: Prompt one recording participant to speak, collect the voice information of one recording participant, then prompt another recording participant to speak, collect the other recording participant's voice information; then use a general algorithm to combine the collected two The sound information is combined into a first key, which is used to encrypt subsequent recordings.
[0084] For example, through the frequency information of the two sounds collected, the binary data strings...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com