Secure erasure method and apparatus
A safe and non-safe technology, applied in the direction of input/output to record carrier, etc., can solve problems such as blocking and freezing, and achieve the effect of improving running smoothness and good product experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
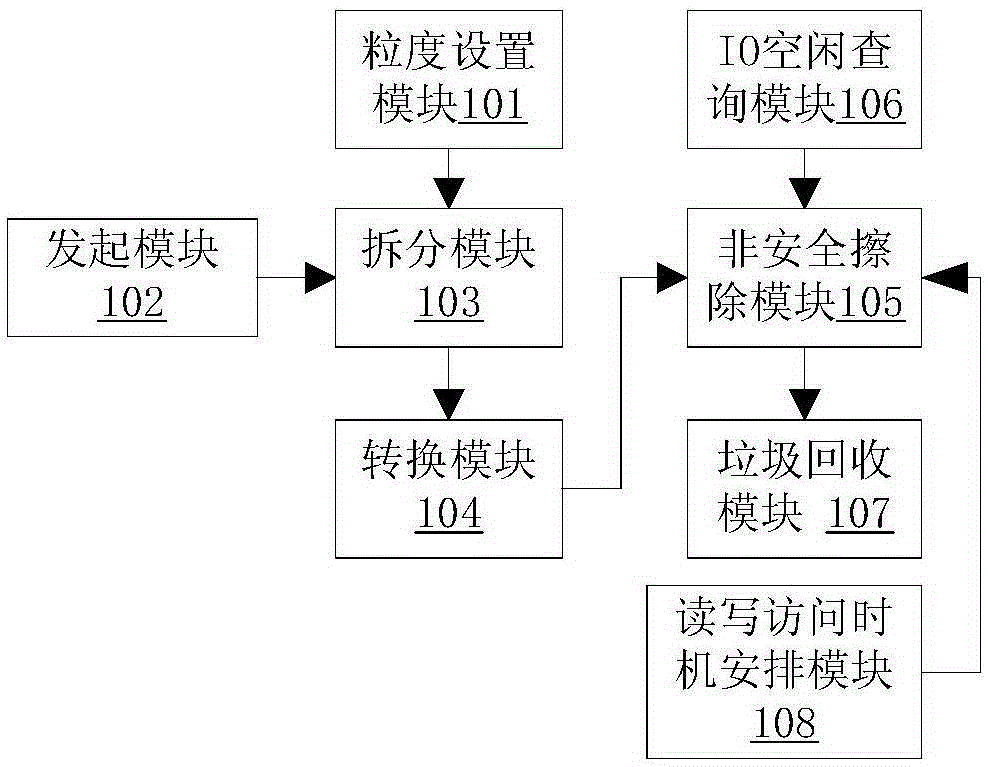
[0033] Such as figure 1 As shown, a preferred embodiment of the secure erasing device of the present invention includes
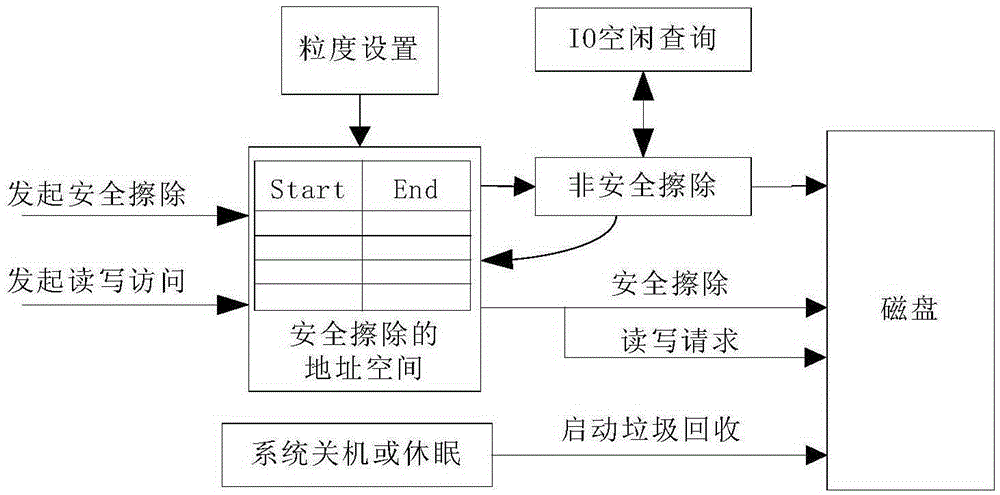
[0034] In the granularity setting module 101, the user presets the splitting granularity, and the granularity is used for the system to split the address space of the secure erasing of continuous large blocks.
[0035] The initiating erasure module 102 is used for initiating secure erasing in the user space, and the parameter is the address space of the secure erasing; the parameter is the address and length of the disk LBA required for the secure erasing.
[0036] The splitting module 103 is used for splitting the address space of the secure erase in the kernel space according to the splitting granularity preset by the user. When splitting, the address space to be executed for secure erasing is divided into equal lengths according to the splitting granularity.
[0037] The converting module 104 is used for converting between non-secure erasing and secure...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com