Secret data matching device, secret data updating method, and recording medium
A technology of secret data and matching device, applied in the direction of secure communication device, digital data protection, digital data authentication, etc., can solve the problem that the server cannot easily update the biological information, the biological information cannot be updated safely or easily, the server does not Issues such as being able to update biometric information securely
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 approach
[0028] (Configuration of secret data matching system)
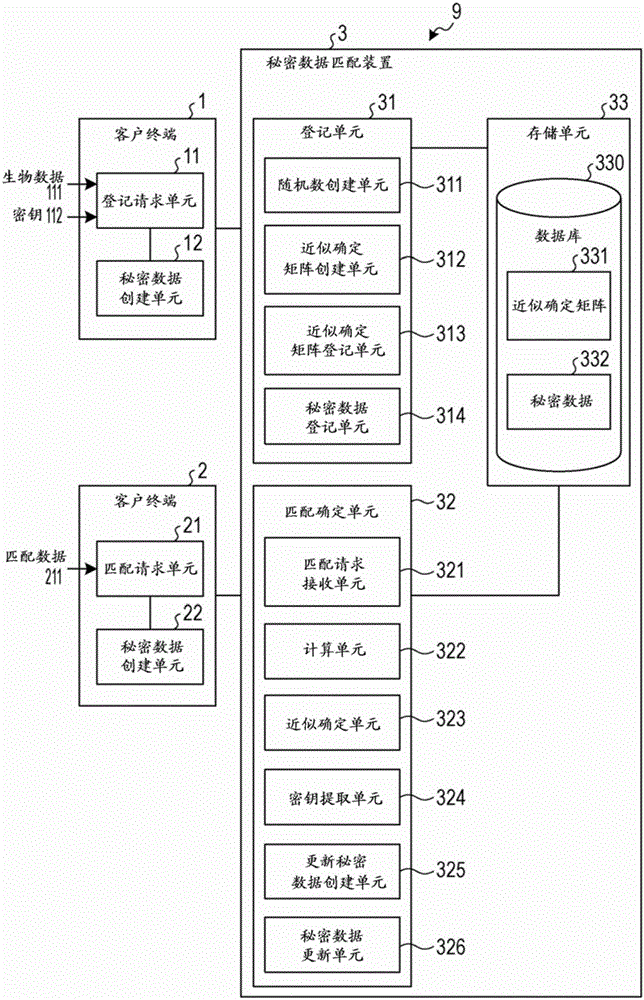
[0029] figure 1 is a diagram for explaining an example of the functional configuration of the secret data matching system according to the first embodiment. Such as figure 1 As shown, the secret data matching system 9 includes a client terminal 1 , a client terminal 2 and a secret data matching device 3 . A database 330 is included in the secret data matching device 3 . The secret data matching device 3 is connected with the client terminal 1 and the client terminal 2 through a network.
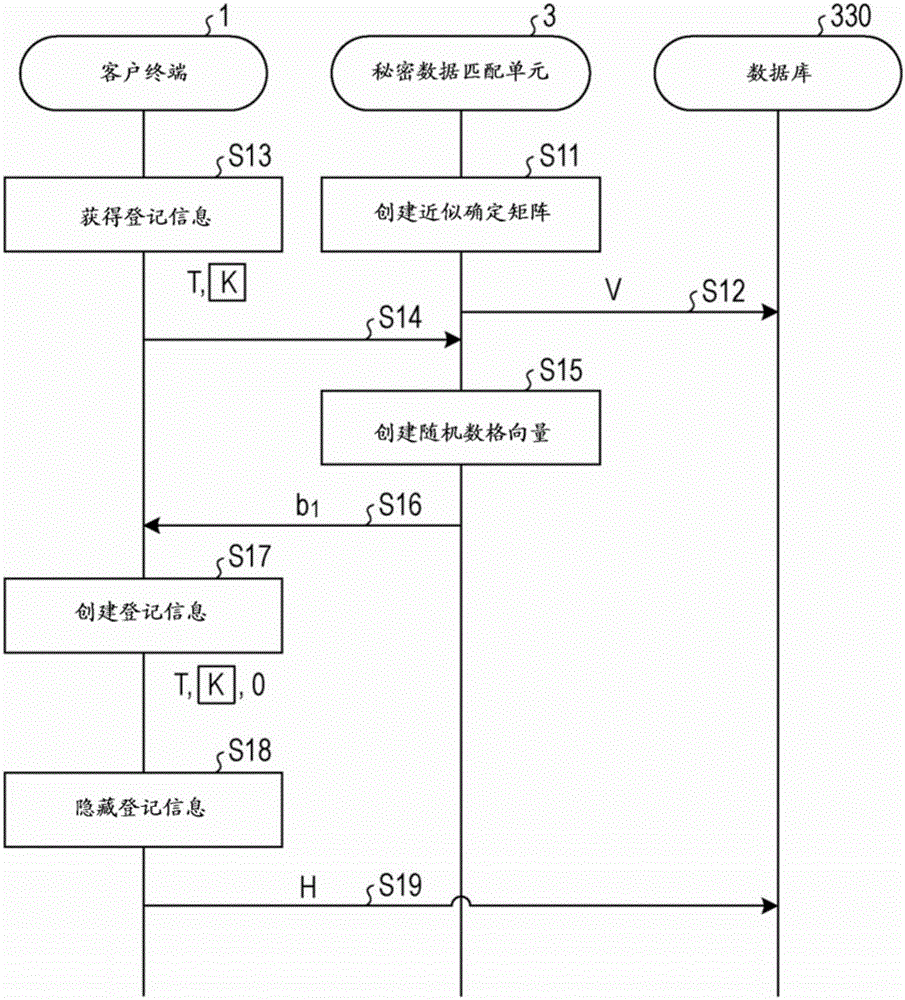
[0030] The secret data matching system 9 hides the customer's biological data and the customer's feature key data based on a specific random number (lattice element) called lattice masking, and registers the first secret data obtained by hiding in the database 330 in. When a client requests to match biological data, the secret data matching system 9 hides the biological data to be matched based on different lattice elements to obtai...
Embodiment approach 2
[0111] The previous discussion analyzed the case where the secret data 332 stored in one set of data per user is updated as secret data in which matching data is hidden during matching in the secret data matching device 3 according to the first embodiment. However, the secret data matching device 3 is not limited in this way, and a plurality of sets of secret data 332 may be stored for each user, and more secret data in which matching data is hidden during matching may be added.
[0112] A case will be discussed in which the secret data matching apparatus 3 in the second embodiment adds more secret data in which matching data is hidden during matching to store a plurality of sets of secret data 332 for each user.
[0113] (Configuration of secret data authentication system)
[0114] Figure 5 is a diagram for explaining an example of the functional configuration of the secret data matching system according to the second embodiment. are shown with the same reference numerals as...
no. 2 approach
[0129] (Advantages of the second embodiment)
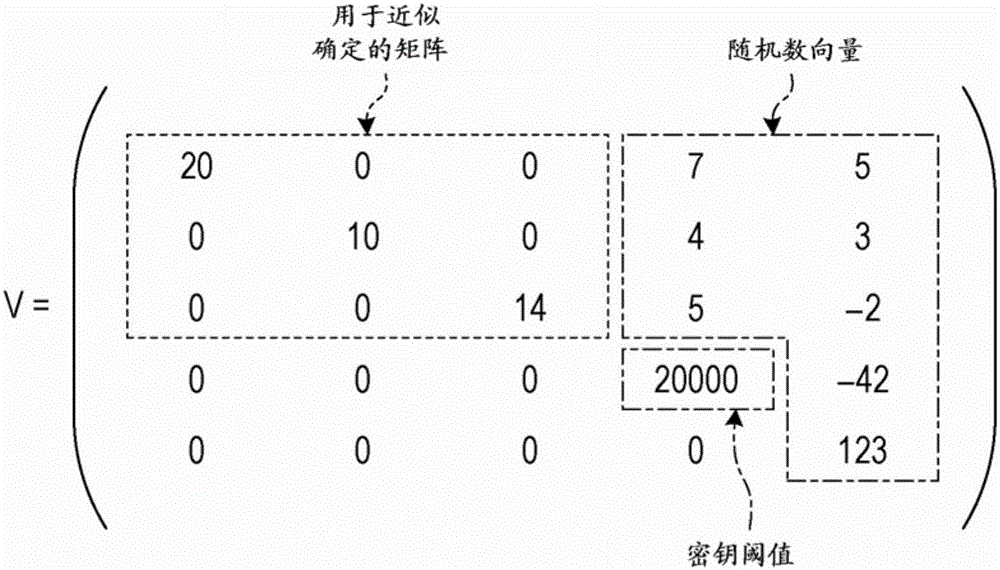
[0130] According to the second embodiment, the secret data matching device 3 registers in the database 330 the first secret vector obtained based on the first random number and the first linear combination using the row vectors of the approximation determination matrix 331 to hide the biological data and the key . The secret data matching device 3 obtains the second secret vector obtained by hiding the matching data based on the second random number and the second linear combination using the respective row vectors of the approximation determination matrix 331 . Then, the secret data matching device 3 calculates a remainder vector as a remainder obtained by applying the approximate determination matrix 331 as a modulus to the difference between the first secret vector and the second secret vector. The secret data matching means 3 determines whether the biological data approximates the matching data based on the calculated remaini...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com