Safety mechanism adopting mouse
A security mechanism, mouse technology, applied in the protection of internal/peripheral computer components, etc., can solve problems such as inconvenience and achieve the effect of protecting security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
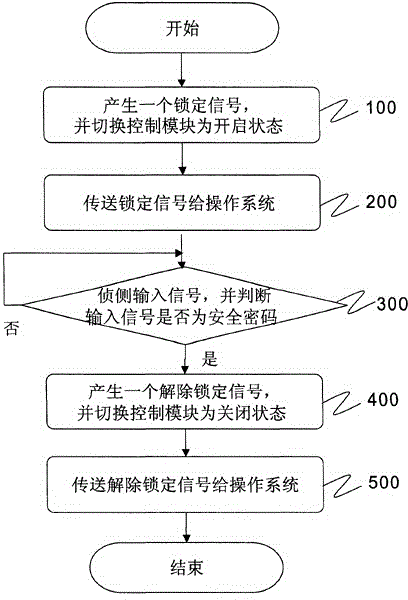
[0014] In order to further illustrate the present invention, further describe below in conjunction with accompanying drawing:
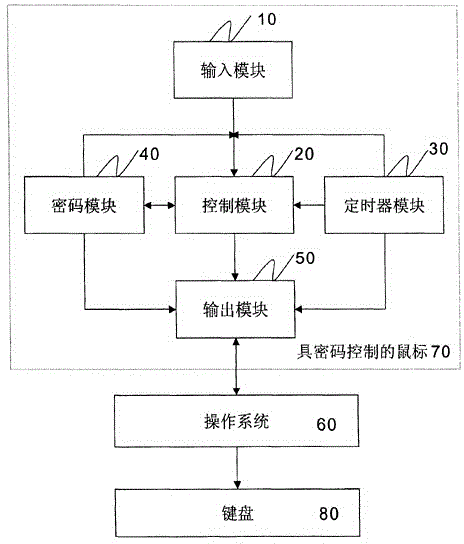
[0015] see figure 1 , for the mouse 70 of tool password control in the present invention comprises input module 10, control module 20, timer module 30, password module 40 and output module 50, the operation relation between each module is described as follows respectively below:
[0016] The mouse 70 with password control includes an input module 10, and the input module 10 includes a group of input buttons, and the input buttons include a left button, a right button, and a middle button. Corresponding input signals can be generated by pressing the input button, including a left button signal, a right button signal, and a middle button signal, and then the input signal is transmitted to the control module 20 . But not all input keys are composed of left key, right key, and middle key. Some input keys only have two keys, left key and right key, and so...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com