Data card and method, equipment, system for using equipment binding
A technology of data cards and devices, applied in the field of network communication, can solve the problem of no data card theft and other problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
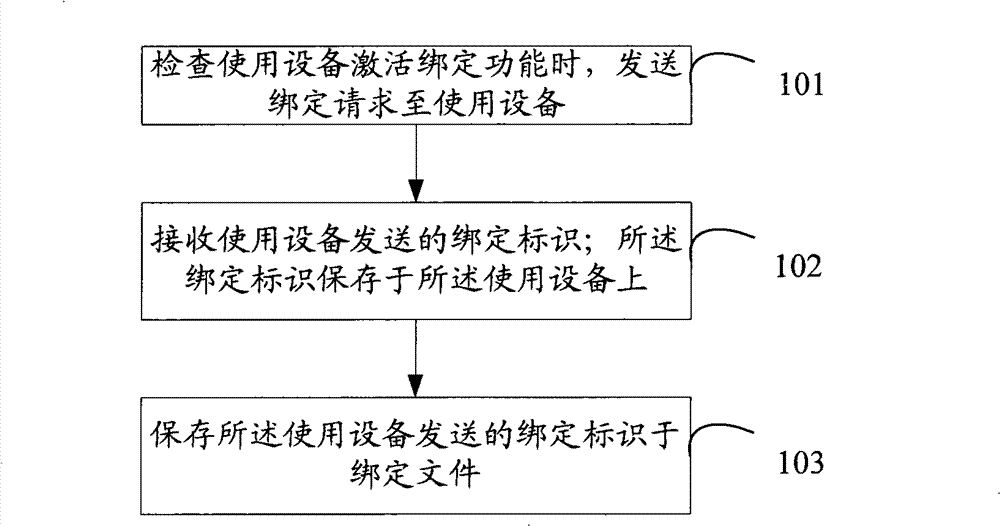
[0025] see figure 1 , which is a flowchart of the first embodiment of the method based on the present invention.
[0026] This embodiment describes in detail the method for binding a data card to a device.
[0027] S101: When checking that the binding function is activated by the use device, send a binding request to the use device.
[0028] When the data card is used for the first time, the binding file in the data card is empty. When the data card is inserted into the device, the data card automatically detects that the binding file is empty, and prompts whether to activate the binding function. When the binding function is selected, the data card sends a binding request to the device.
[0029] It should be noted that when the data card detects that the binding function is not activated, the data card will not write the binding flag into the binding file. Every time the data card is used in the future, if it is detected that there is a non-use binding flag in the binding ...
Embodiment 2
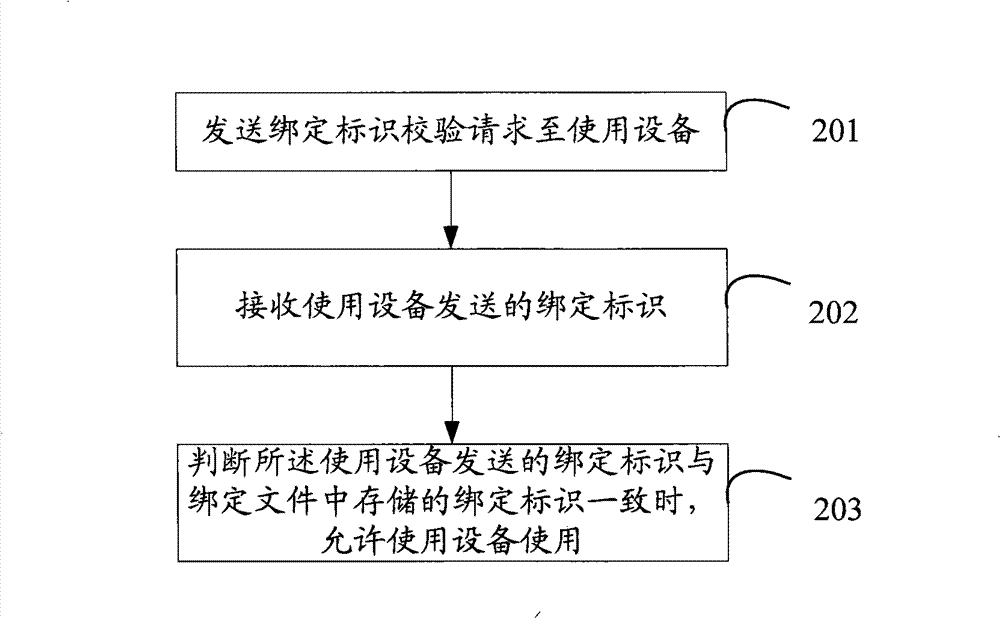
[0043] see figure 2 , which is a flowchart of the second embodiment of the method based on the present invention.
[0044] The embodiment of the present invention describes in detail the method for controlling the binding of the data card and the device after the data card is bound to the device.
[0045] S201: Send a binding identifier verification request to the using device.
[0046] S202: Receive the binding identifier sent by the device.
[0047] The binding identifier may include the IMEI of the device and / or the password set by the device.
[0048] S203: When it is judged that the binding identifier sent by the user device is consistent with the binding identifier stored in the binding file, allow the user device to use.
[0049] It should be noted that multiple IMEIs of devices may be stored in the binding file of the data card. After the data card obtains the IMEI of the used device, it calls out the used IMEI in the binding file and compares it with the obtained...
Embodiment 3
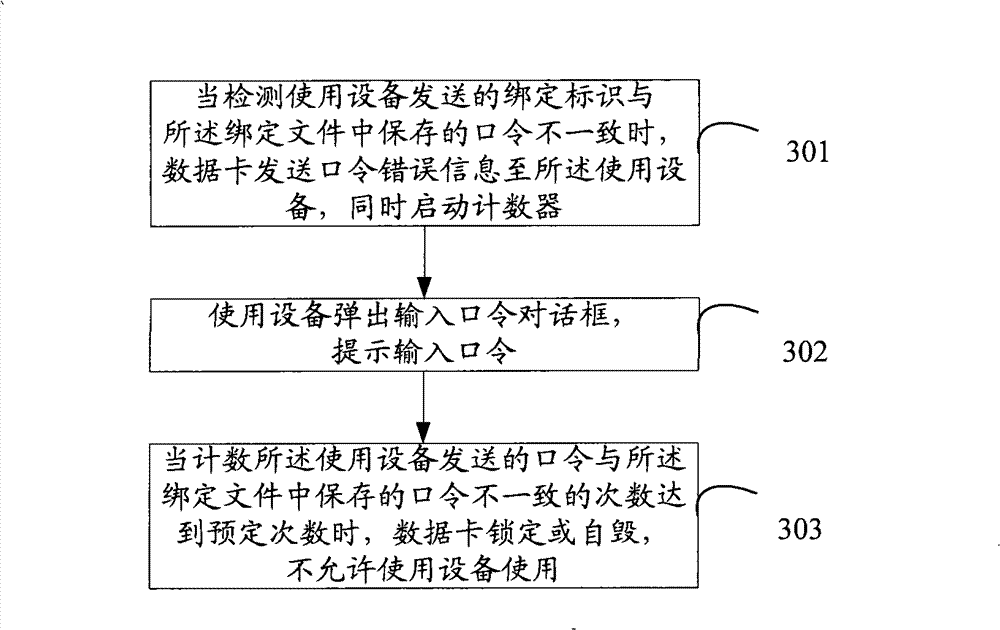
[0059] see image 3 , which is a flowchart of the third embodiment of the method based on the present invention.
[0060] The method for binding the control data card to the device when the device is illegal will be described in detail below.
[0061] S301: When detecting that the binding identifier sent by the user device is inconsistent with the binding identifier stored in the binding file, the data card sends a binding identifier verification error message to the user device; or when the user device does not send an error message to the data card When the identifier is bound, the data card sends prompt information to the device; at the same time, the counter is started.
[0062] S302: Use the device to pop up a password input dialog box, prompting to input the password.
[0063] It should be noted that, at this time, the user needs to manually input the password. The counter starts counting the number of times the password is manually entered.
[0064] S303: When count...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com