Network security audit and access system based on Openflow, network security audit method based on Openflow, and network security access method based on Openflow
A network security and security audit technology, applied in the field of network communication, can solve the problems of complex implementation technology and high equipment cost, and achieve the effect of simplifying the operation process and reducing the cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example Embodiment
[0040] The present invention will be further described below in conjunction with the drawings and embodiments.
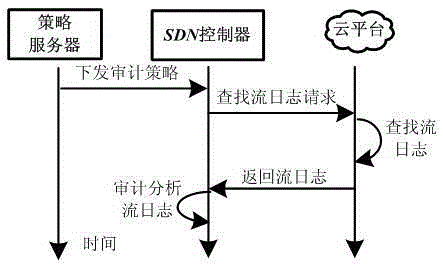
[0041] A security audit method includes the following steps:
[0042] A. The basic steps to extract audit logs from flow information are as follows:
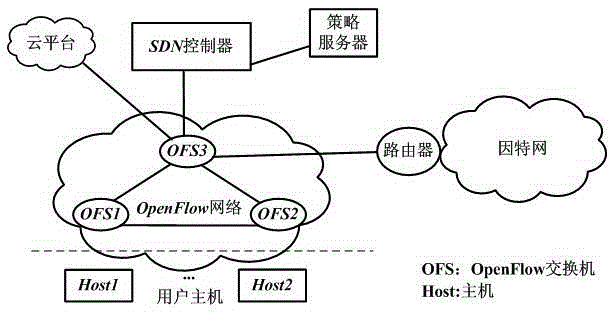
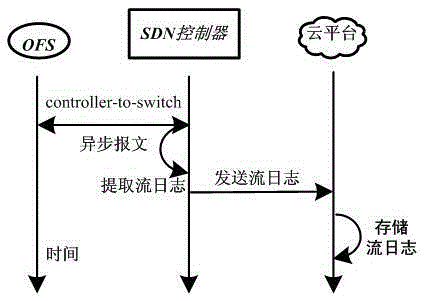
[0043] 1) When the SDN controller sends the controller-to-switch's Modify-state, Read-state, and Send-packet three subtypes to the switch, and the switch initiates Packet-in, Flow-removed, Port-status and When there are 4 kinds of asynchronous messages such as Error, the controller extracts relevant flow information to form a flow record;
[0044] 2) The flow record includes the timestamp, destination / source IP address, destination / source MAC address, transport layer protocol type, destination / source port number, OpenFlow switch ID, OpenFlow switch interface and event type when extracting flow information;
[0045] 3) The SDN controller uses "destination IP address" + "time stamp" as the row key to insert the above flow record...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com