A root certificate storage device and secure access method
A storage device and secure access technology, applied in the field of communication security, can solve the problems of inability to receive, user information and financial information leakage, increase application risks, etc., to achieve the effect of enhancing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The scope of applicability of the present invention will become apparent from the detailed description given below. It should be understood, however, that the detailed description and specific examples, while indicating the preferred embodiment of the invention, are given for purposes of illustration only.
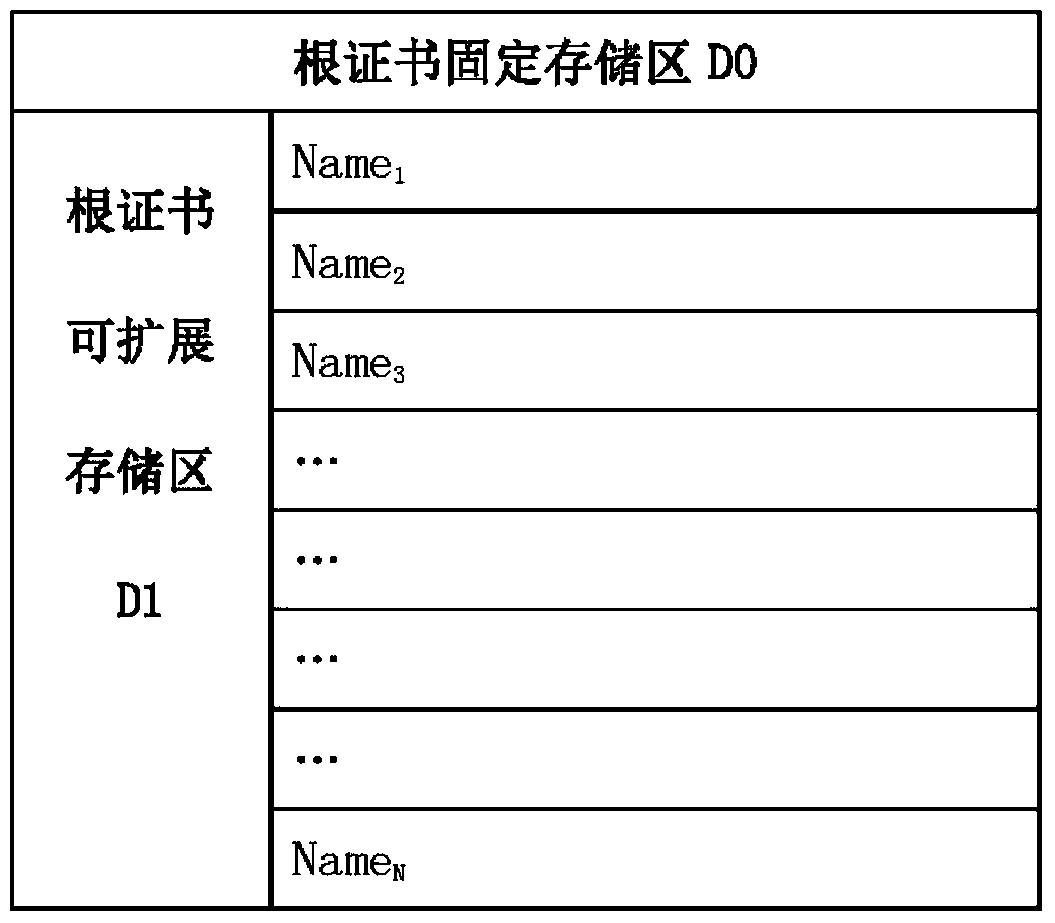
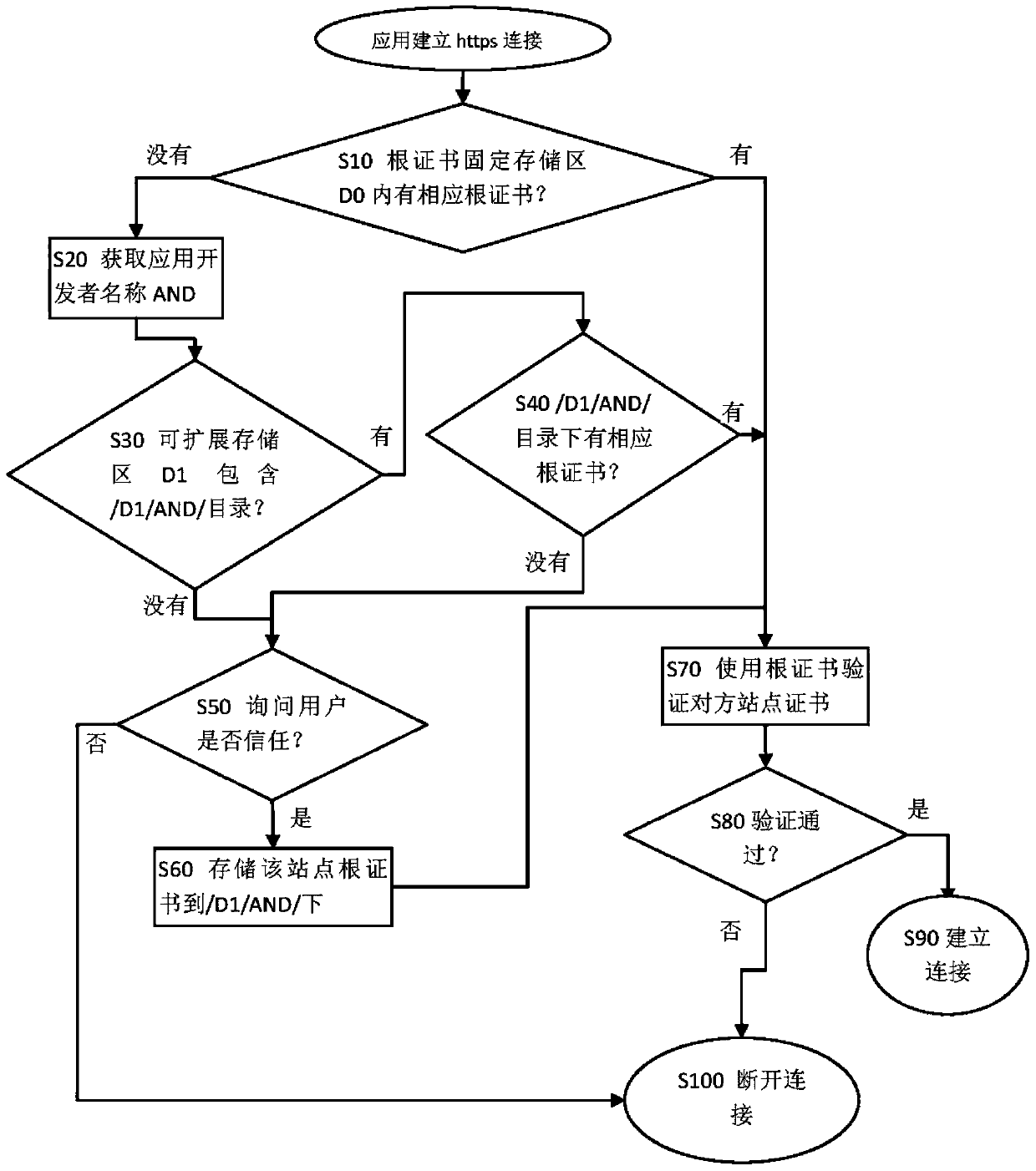
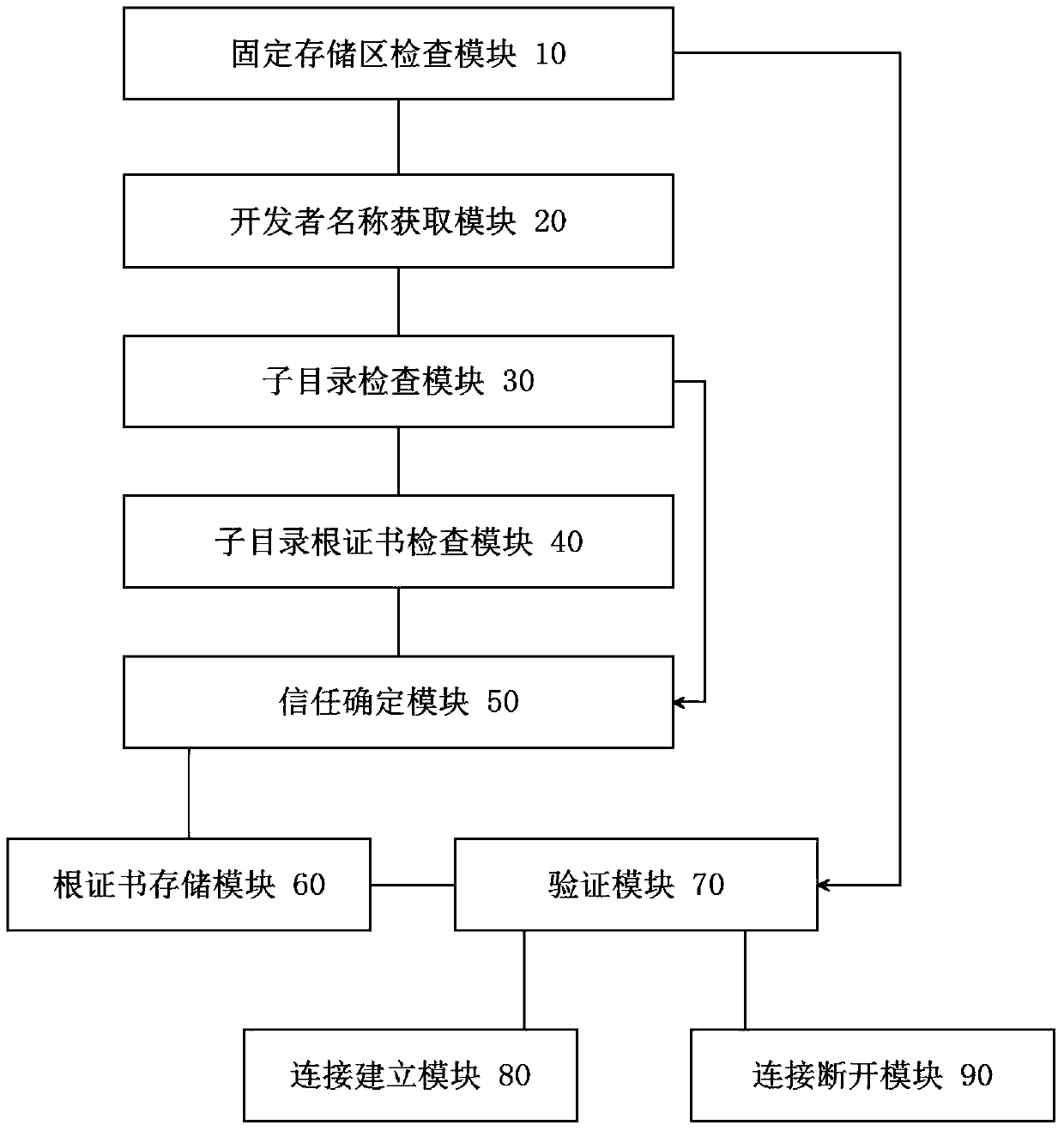
[0028] figure 1 Shows a schematic structural diagram of the root certificate storage area of the root certificate storage device 100 of the present invention, wherein the root certificate storage device 100 is a built-in memory of a mobile terminal such as a mobile phone or an SD card connected to a mobile phone, and the root certificate storage device 100 includes a The fixed storage area D0 of the well-known CA root certificate, the root certificate in it cannot be modified or added, and can only be read. The root certificate in this area is built into the mobile phone before leaving the factory, and is used to verify the certificate of the other party's site w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com