A wireless connection authentication method and device
A wireless connection and verification code technology, applied in the computer field, can solve the problems of inflexible use, inflexible and convenient password management of wireless connection devices, etc., and achieve the effect of improving the flexibility of use and increasing the difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
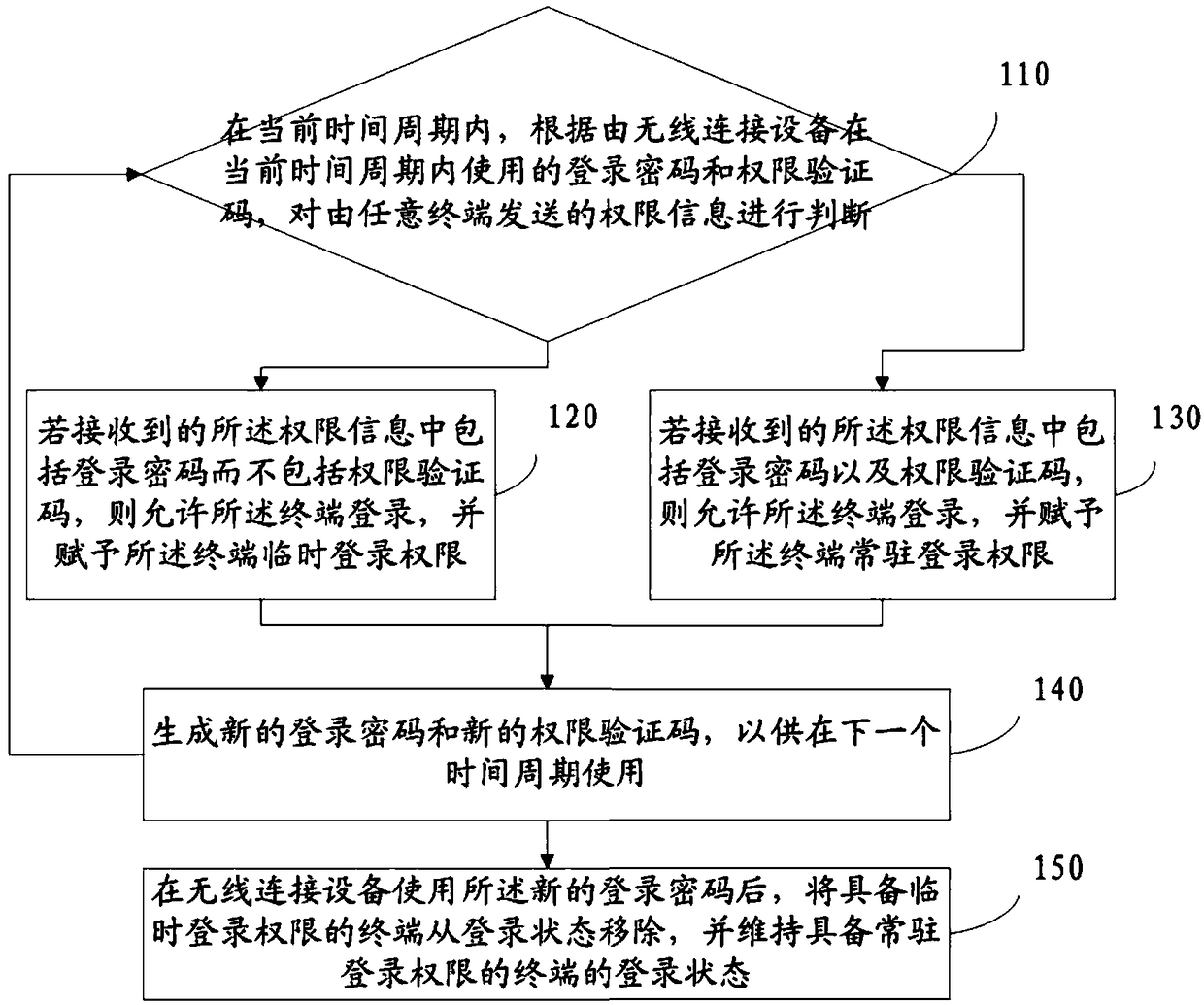
[0089] Reference figure 1 , Which shows a schematic flowchart of a wireless connection authentication method according to an embodiment of the present invention, which may specifically include:
[0090] Step 110: In the current time period, judge the permission information sent by any terminal according to the login password and the permission verification code used by the wireless connection device in the current time period.
[0091] In the embodiment of the present invention, for each time period, the wireless connection device obtains the login password used to log in to the wireless connection device in the current time period, and the authorization verification code used to confirm the authority of the resident user.
[0092] The user can send permission information to the wireless connection device in any time period, and the wireless connection device judges the received permission information according to the login password and the permission verification code.
[0093] In pra...
Embodiment 2
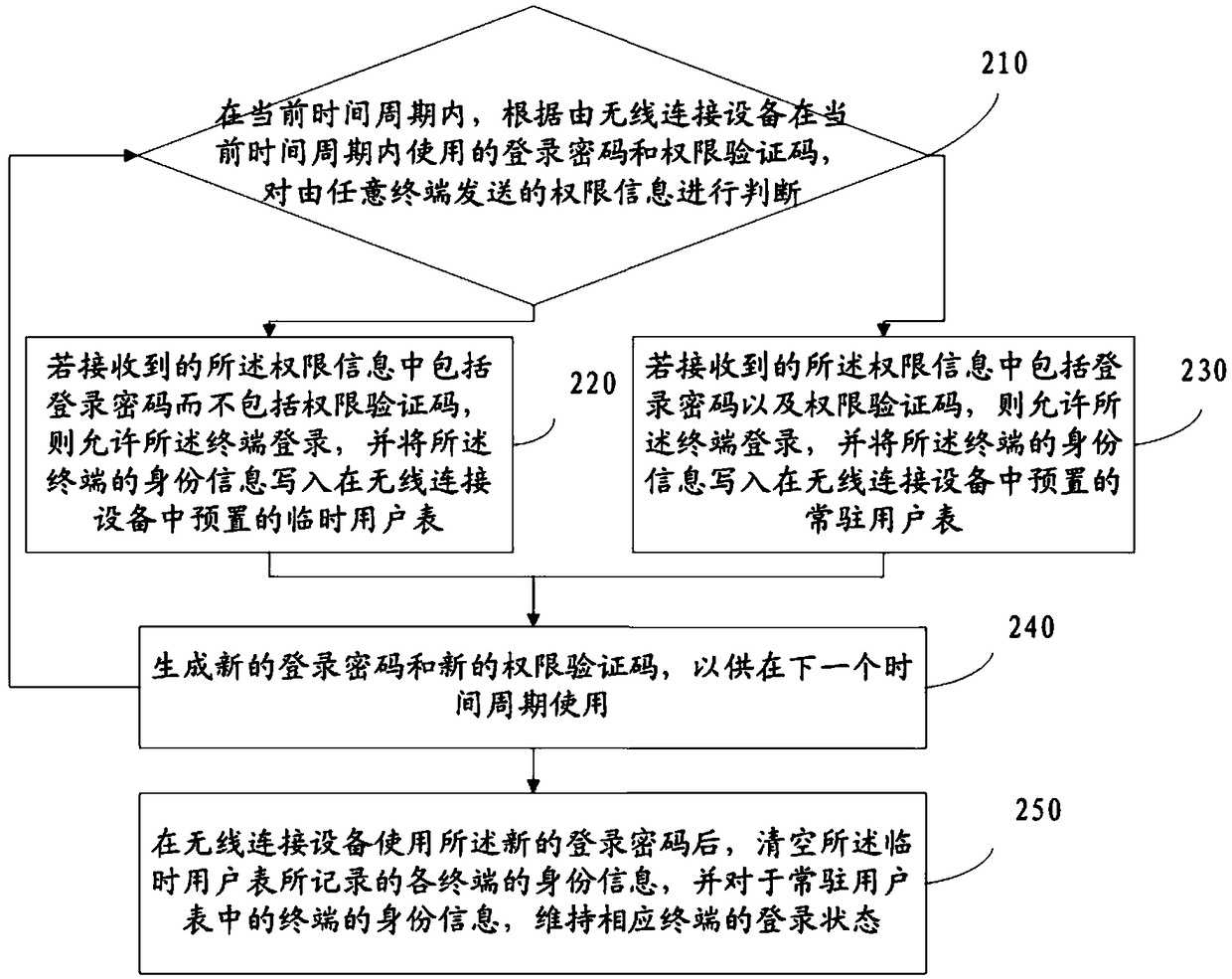
[0150] On the basis of the first embodiment, the embodiment of the present invention uses a temporary user table in the wireless connection device to grant temporary login authority to the terminal of the temporary user, and uses the resident user table to grant the login authority of the resident user to the terminal of the resident user .
[0151] Reference figure 2 , Which shows a schematic flowchart of a wireless connection authentication method according to an embodiment of the present invention, which may specifically include:
[0152] Step 210: In the current time period, judge the permission information sent by any terminal according to the login password and the permission verification code used by the wireless connection device in the current time period.
[0153] Step 220: If the received authorization information includes the login password but not the authorization verification code, the terminal is allowed to log in, and the terminal's identity information is written i...
Embodiment 3
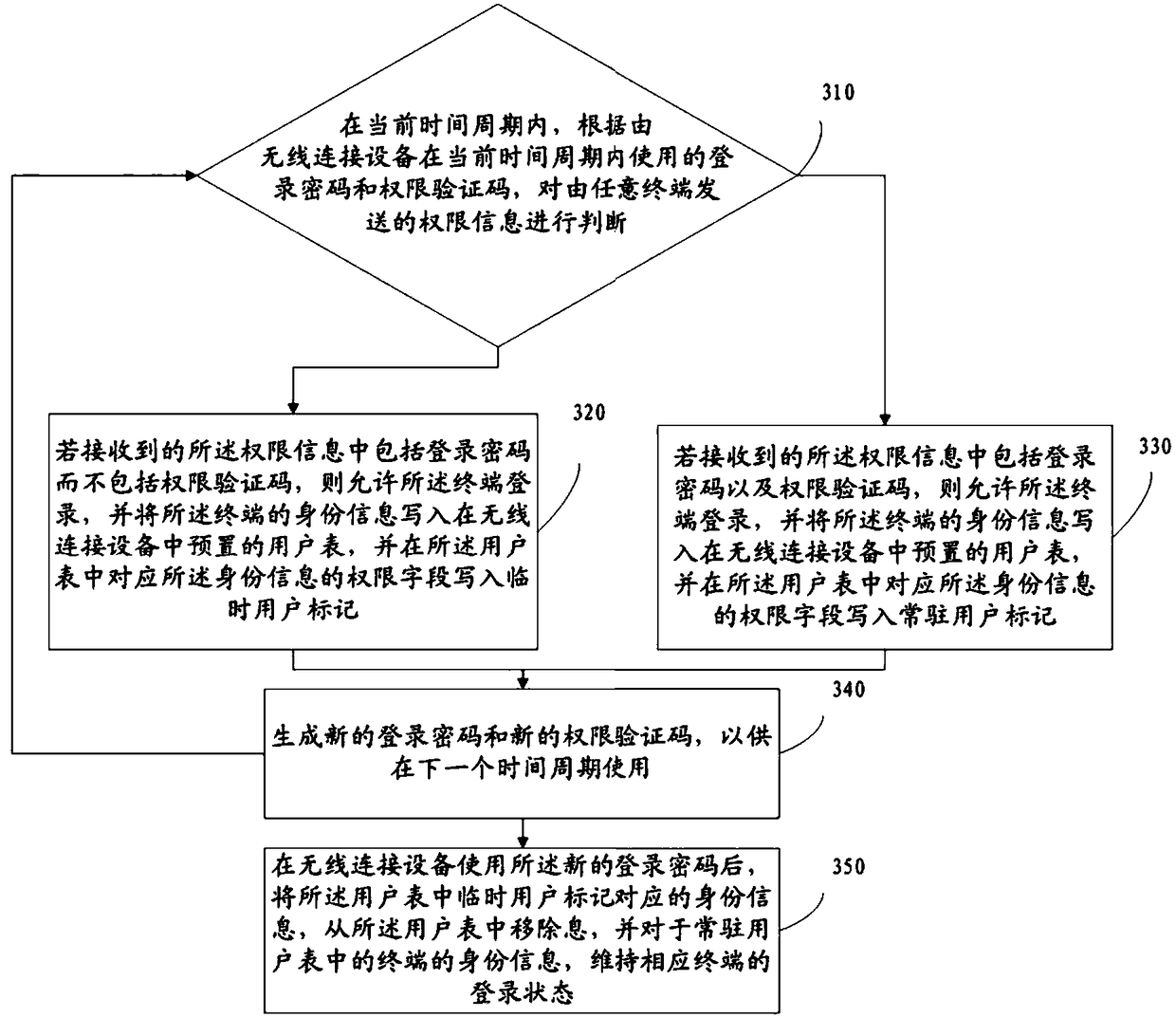
[0166] On the basis of the first embodiment, the embodiment of the present invention adopts a user table with a preset permission field. In the user table, temporary users’ terminals are given temporary login permissions in the form of temporary marks, and permanent users’ terminals are given permanent The form of resident mark gives its resident user the login authority.
[0167] Reference image 3 , Which shows a schematic flowchart of a wireless connection authentication method according to an embodiment of the present invention, which may specifically include:
[0168] Step 310: In the current time period, judge the permission information sent by any terminal according to the login password and the permission verification code used by the wireless connection device in the current time period.
[0169] Step 320: If the received authority information includes the login password but not the authority verification code, allow the terminal to log in, and write the terminal's identity ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com