Encryption method, decryption method, communication method, system and device
An encryption method and a technology for encrypting strings, which are applied in secure communication devices, encryption devices with shift registers/memory, transmission systems, etc. Universality, the effect of improving real-time security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
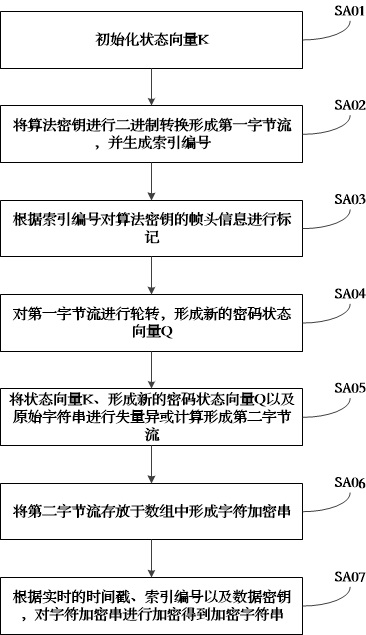
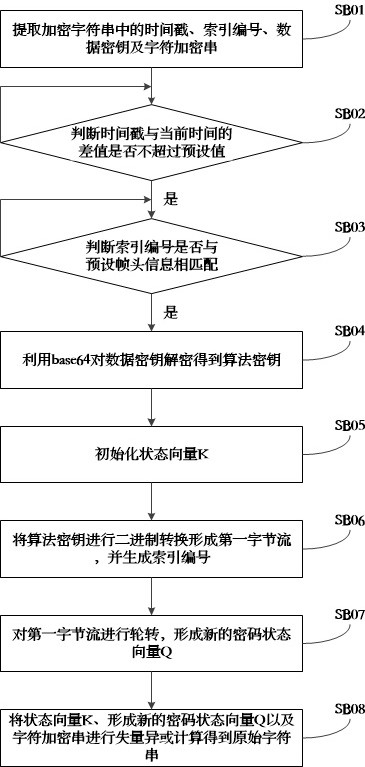
[0061] The present invention will be further described below in conjunction with the accompanying drawings. The following examples are only used to illustrate the technical solution of the present invention more clearly, but not to limit the protection scope of the present invention.
[0062] The invention provides a communication method, comprising the following steps:
[0063] For a raw string "HardwareType#1#1004",
[0064] Process 1 encrypts the original string to obtain the encrypted string 0YFhpus01y98UpMg1bAs0fICp9vHY7DEExd8p1XcQeE42Riuu6Iv.
[0065] Process one sends the encrypted string to process two.
[0066] After process 2 receives the encrypted string, it decrypts the encrypted string to obtain the original string HardwareType#1#1004.
[0067] Based on the same inventive concept, the present invention also provides a communication system, including an encryption module, a sending module, a receiving module and a decryption module.
[0068] Based on the same i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com