Method for preventing malicious sharing of user identity and device thereof
A technology of user identity and user identity information, applied in the field of content access control, can solve the problems of easy theft of user identity, loss of content providing websites, malicious sharing, etc., to achieve the effect of simple investigation, high accuracy, and prevention of malicious sharing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
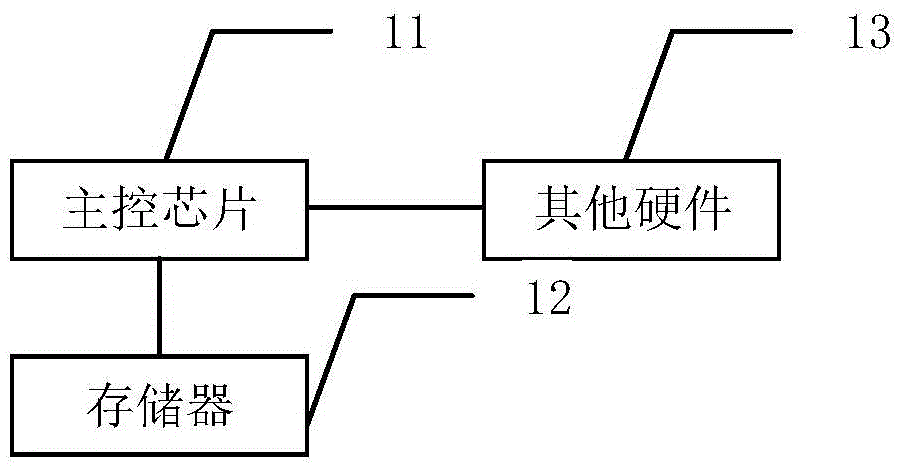
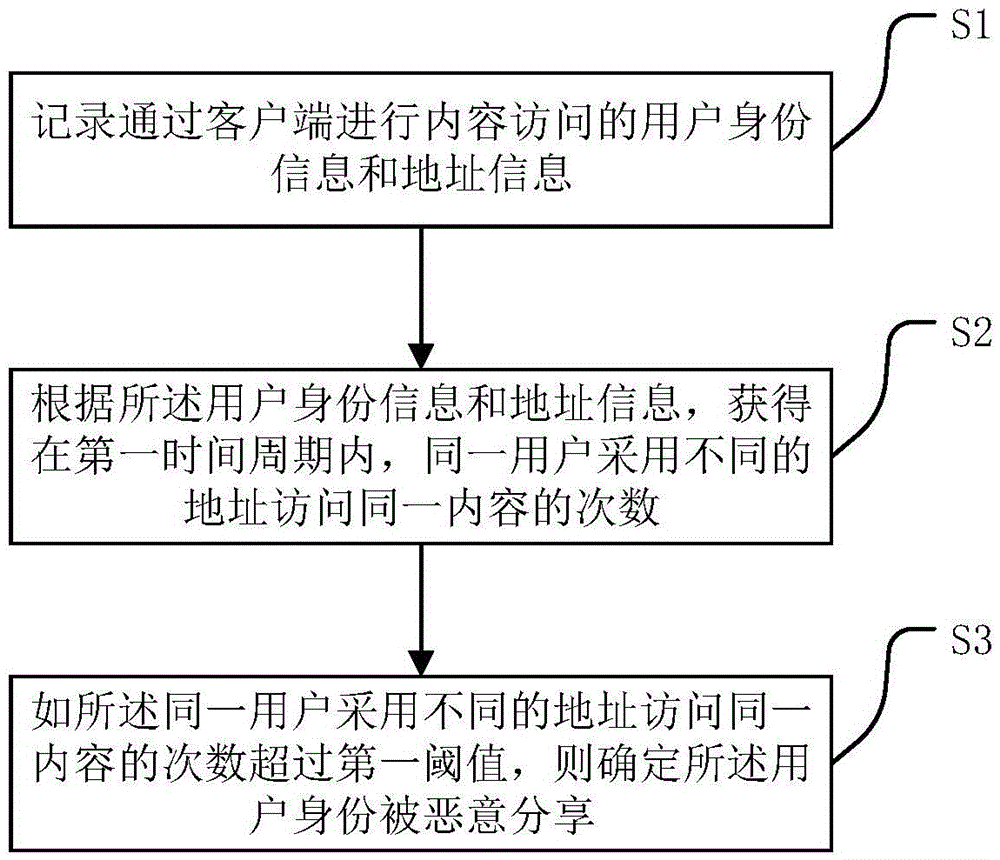
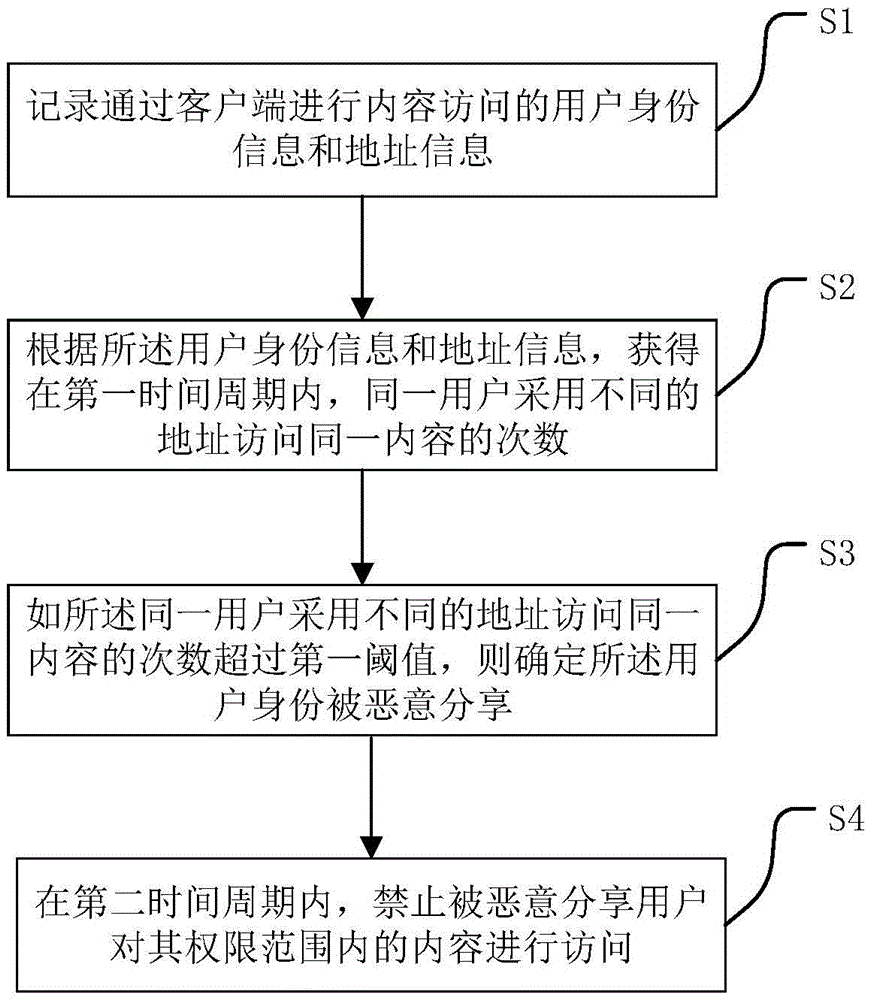
[0036] This application records the identity information and address information of users who access content through the client, and obtains the number of times the same user uses different addresses to access the same content within the first time period according to the user identity information and address information. If the number of times the same user accesses the same content using different addresses exceeds a first threshold, it is determined that the user identity has been maliciously shared. This application can easily realize the investigation of user identity information, prevent user identity from being maliciously shared, and has convenient operation and high accuracy.
[0037] Of course, implementing any technical solution of the present application does not necessarily need to achieve all the above advantages at the same time.
[0038] In order to enable those skilled in the art to better understand the technical solutions in the present application, the tech...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com