Mobile terminal unlocking method and device and mobile terminal
A mobile terminal and unlocking device technology, applied in the field of communication security, can solve problems such as low security, achieve the effect of improving security and improving user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
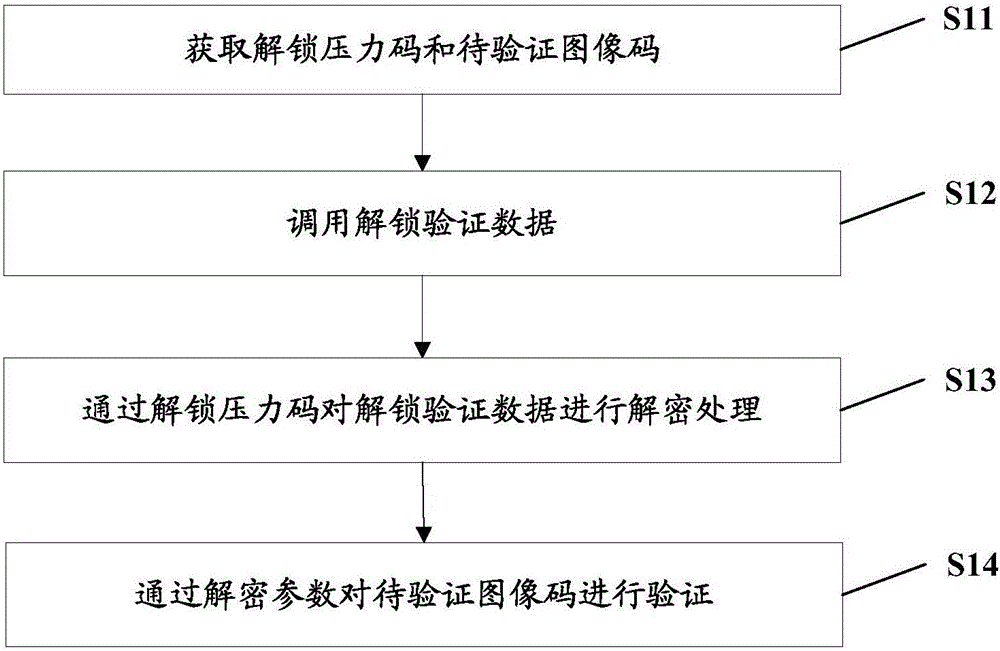
[0045] See figure 1 , figure 1 The flow chart of the mobile terminal unlocking method provided in this embodiment, the specific unlocking process is as follows:
[0046] S11. Obtain an unlocking pressure code and an image code to be verified.
[0047] Specifically, the pressure code generating device can convert the pressure value into a binary code, that is, generate binary pressure codes of different sizes according to the pressure value, and a pressure prompt will be given on the surface of the pressure code generating device so that the user can determine the pressure applied to the pressure code generating device. What is the pressure value of , so that the user can accurately obtain the binary pressure code when decrypting. Of course, the pressure value can also be converted into pressure codes of other bases by the pressure code generating device. Correspondingly, the unlocking pressure code can also be binary or other binary codes, and this embodiment uses the binar...
Embodiment 2
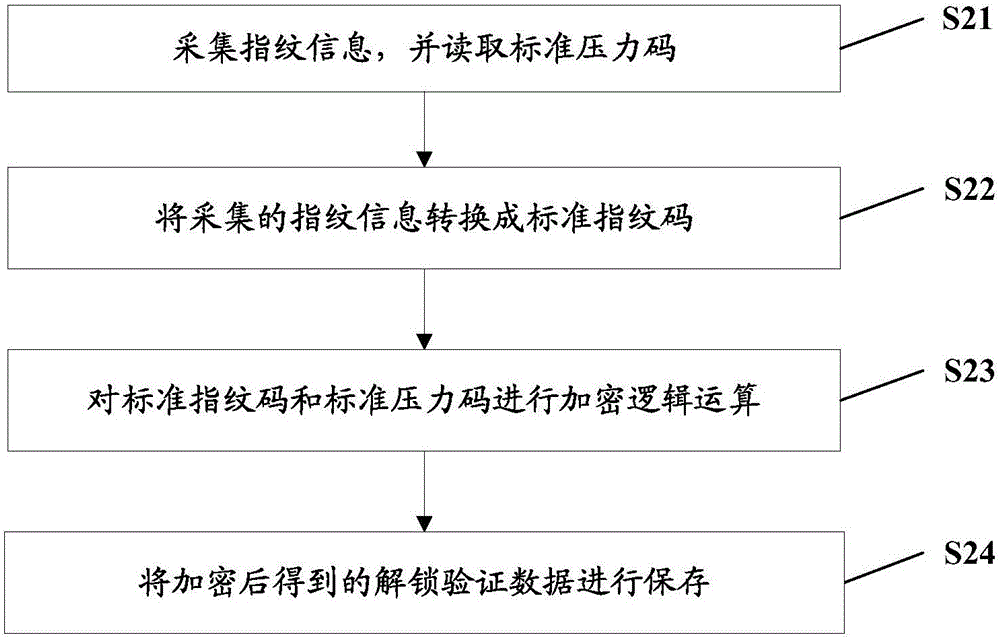
[0061] This embodiment further describes the mobile terminal unlocking method provided by the embodiment of the present invention based on the content of the first embodiment. See figure 2 , figure 2 It is a flow chart of the fingerprint information encryption method provided in this embodiment. In this embodiment, the mobile terminal is a mobile phone, the image information is fingerprint information, and the fingerprint code is extracted from the fingerprint information. The specific fingerprint information encryption process is as follows:
[0062] S21, collecting fingerprint information, and reading a standard pressure code.
[0063] Specifically, the fingerprint information is collected by a camera or by pressing, and a standard pressure code is read by a pressure code generating device. When reading the pressure code, the binary code can be read from the pressure code generating device through in-line or wireless transmission.
[0064] S22. Convert the collected f...
Embodiment 3
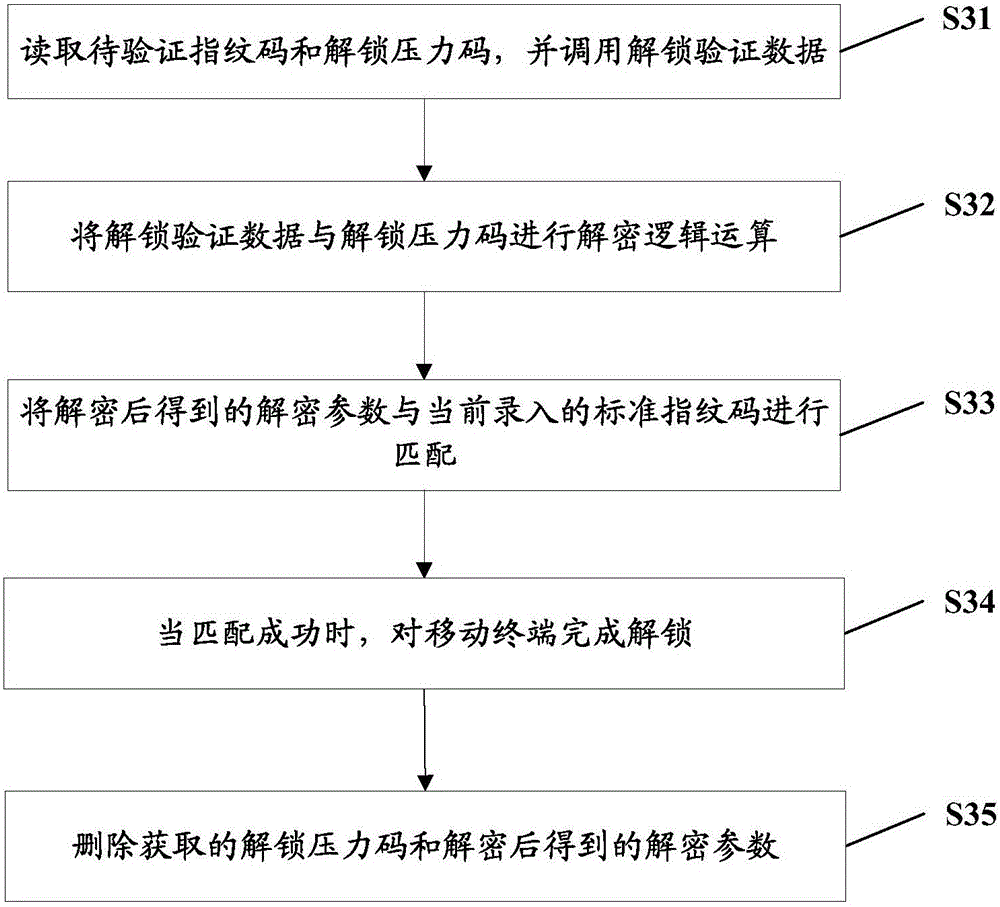
[0071] This embodiment further describes the mobile terminal unlocking method provided by the embodiment of the present invention based on the content of the first embodiment and the second embodiment. After the encryption of the fingerprint information in the second embodiment is completed, the fingerprint decryption process of this embodiment is executed. See image 3 , image 3 The flow chart of the fingerprint information decryption method provided in this embodiment, in this embodiment, the mobile terminal is also the fingerprint information, and the fingerprint code is extracted from the fingerprint information. The specific fingerprint information decryption process is as follows:
[0072] S31. Read the fingerprint code to be verified and the unlocking pressure code, and call the unlocking verification data.
[0073] Specifically, the unlocking verification data includes the verification parameters obtained by encrypting the standard image code with the standard pres...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com