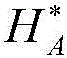A Multivariable Proxy Re-Signature Method Against Collusion Attacks
A collusion attack and re-signature technology, applied in the field of information security, can solve the problems of collusion attack private key information leakage and so on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
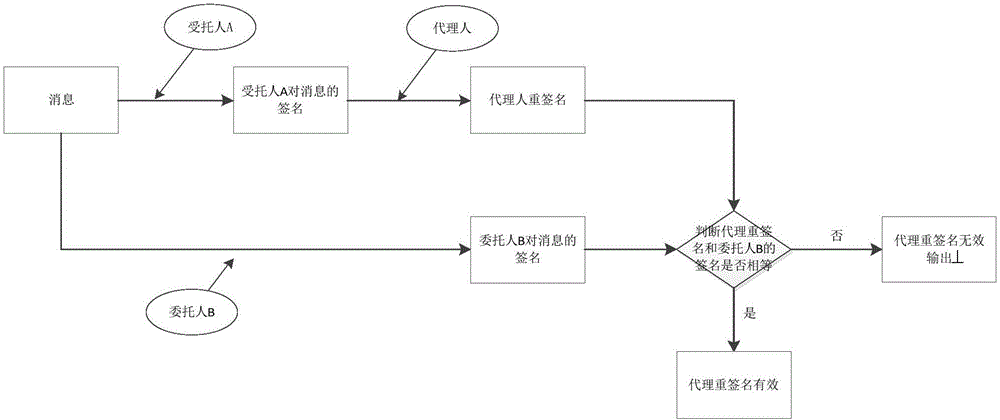
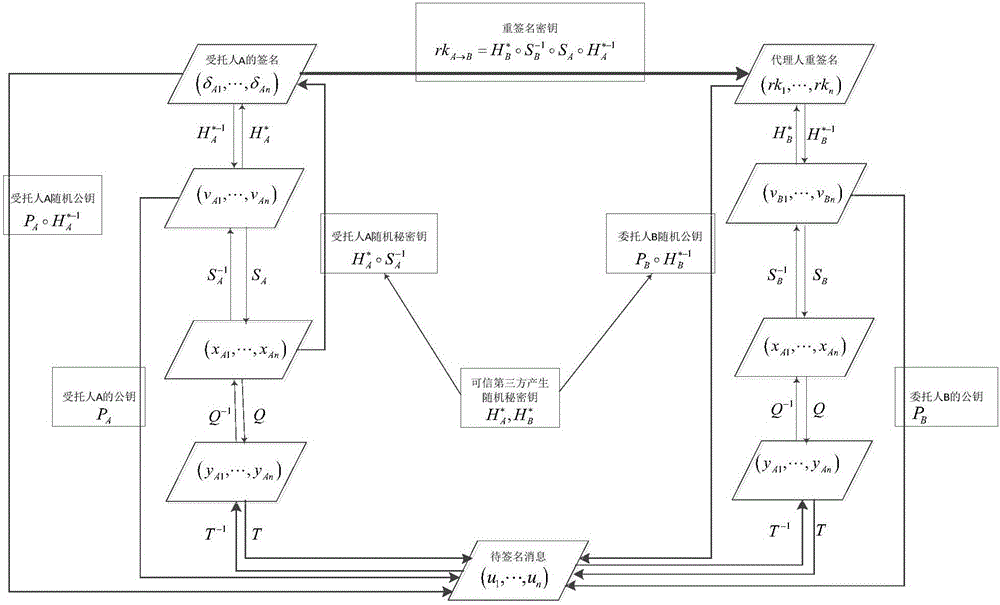
Image
Examples
Embodiment 1
[0102] Taking n=2 in the quadratic equation system, that is, the number of independent variables and the number of equations are both 2 as an example, the steps of the proxy re-signature method based on multivariable collusion attack resistance are as follows:
[0103] (1) Generation system
[0104] Select system parameters: take a finite field F 5 , that is, the field elements are {0,1,2,3,4}, and the operation is modulo 5 addition and modulo 5 multiplication, one element The inverse element of means that satisfies and Multiply and then modulo 5 to be 1 element, denoted as i.e. in F 5 On: -5=0mod5, -4=1mod 5, -3=2mod 5, -2=3mod 5, -1=4mod 5, 1 -1 =1,2 -1 =3,3 -1 =2,4 -1 =4; take n=2, that is, the number of independent variables and equations are both 2; take a 111 =0,a 112 = 1,a 122 =0,b 11 =0,b 12 =0,c 1 = 0; a 211 =0,a 212 =0,a 222 =0,b 21 =1,b 22 =0,c 2 =0, then the quadratic equation system Q is:
[0105]
[0106] The inverse Q of the correspondi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com