Video monitoring based public security image detection method
A video surveillance and image technology, applied in the field of image detection, can solve the problems of single image detection, no involvement, etc., achieve the effect of reasonable detection method, reduce economic cost, and reduce labor input
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
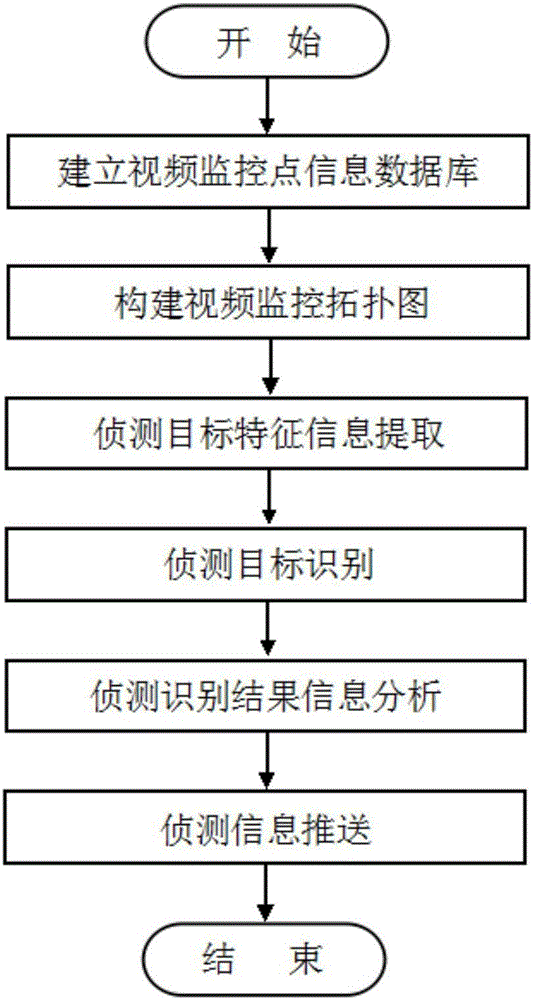
[0032] Embodiment 1: a kind of public security image detection method based on video monitoring, at first, set up video monitoring point information database for all video monitoring points in a certain area, and construct video monitoring topological map according to the data in the video monitoring point information database ;Secondly, extract the feature information of the detection target, identify the detection target, and analyze according to the detection and recognition results; finally, push the detection and recognition analysis result information to the command center.
[0033] The specific steps of the public security image detection method based on video monitoring are as follows:
[0034] Step1: Establish a video monitoring point information database; uniformly code and identify all video monitoring points in the area, recorded as: S=[S 1 ,S 2 ,S 3 ,...,S i ] (i=1,2,3,...); and sequentially register and record the location information and topology information ...
Embodiment 2
[0057] Step1: It is known that there are 12 video monitoring points in a certain area, and the unified code identification of the 12 video monitoring points is recorded as: S=[S 1 ,S 2 ,S 3 ,...,S 12 ]; the avatar information of the detected target, the last time the detected target appeared in the area, and the closest video monitoring point is S 1 , The time when the detection target appears for the last time in the area is T=16, and t=2;
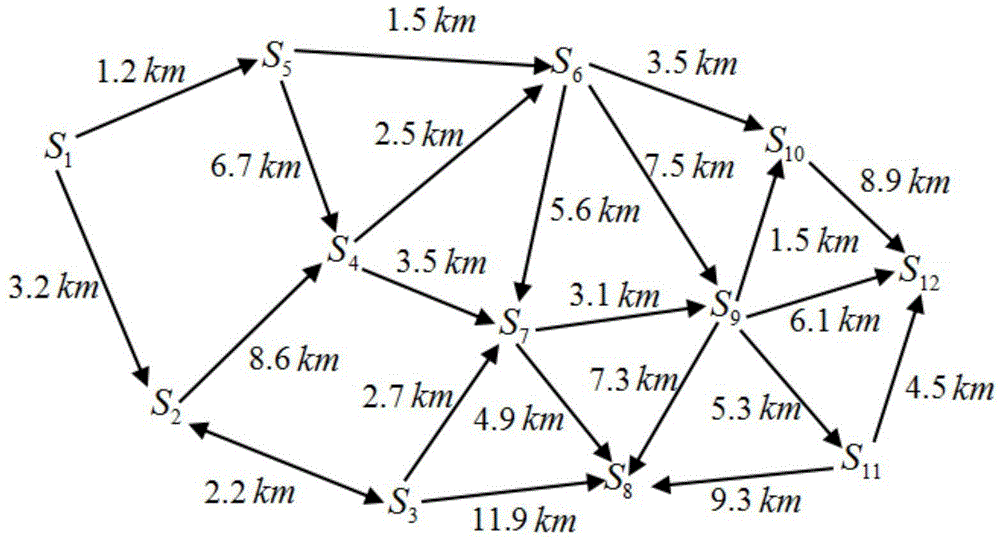
[0058] Step2: Construct a video surveillance topology map according to the location information and topology information of each video surveillance point, specifically as follows figure 2 shown;
[0059] Step3: Use the method of image processing to extract the feature information of the head portrait of the detection target;
[0060] Step4: Detection target recognition;
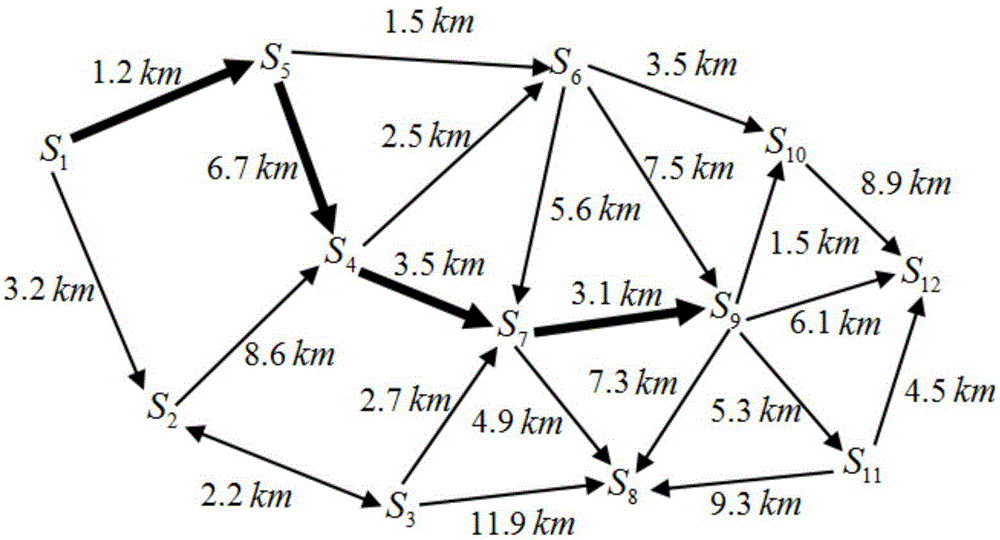
[0061] 1. Confirm S 1 As the current video monitoring center point; according to the video monitoring topology map, determine the set S'={S 5 ,S 2}; the monito...
Embodiment 3
[0069] Step1: It is known that there are 20 video monitoring points in a certain area, and the unified code identification of 20 video monitoring points is recorded as: S=[S 1 ,S 2 ,S 3 ,...,S 20 ]; the avatar information of the detected target, the last time the detected target appeared in the area, and the closest video monitoring point is S 4 , The time when the detection target appears for the last time in the area is T=3, and t=3;
[0070] Step2: Construct a video surveillance topology map according to the location information and topology information of each video surveillance point, specifically as follows Figure 4 shown;
[0071] Step3: Use the method of image processing to extract the feature information of the detected target license plate number;
[0072] Step4: Detection target recognition;
[0073] 1. Confirm S 4 As the current video monitoring center point; according to the video monitoring topology map, determine the set S'={S 3 ,S 8 ,S 5}; the monito...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com