Data encryption method and decryption method and device
A data encryption and data technology, applied in the field of information security, can solve the problems of poor data confidentiality and security, low encryption efficiency, serious data expansion, etc., and achieve the effect of increasing the difficulty of cracking, increasing confidentiality and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
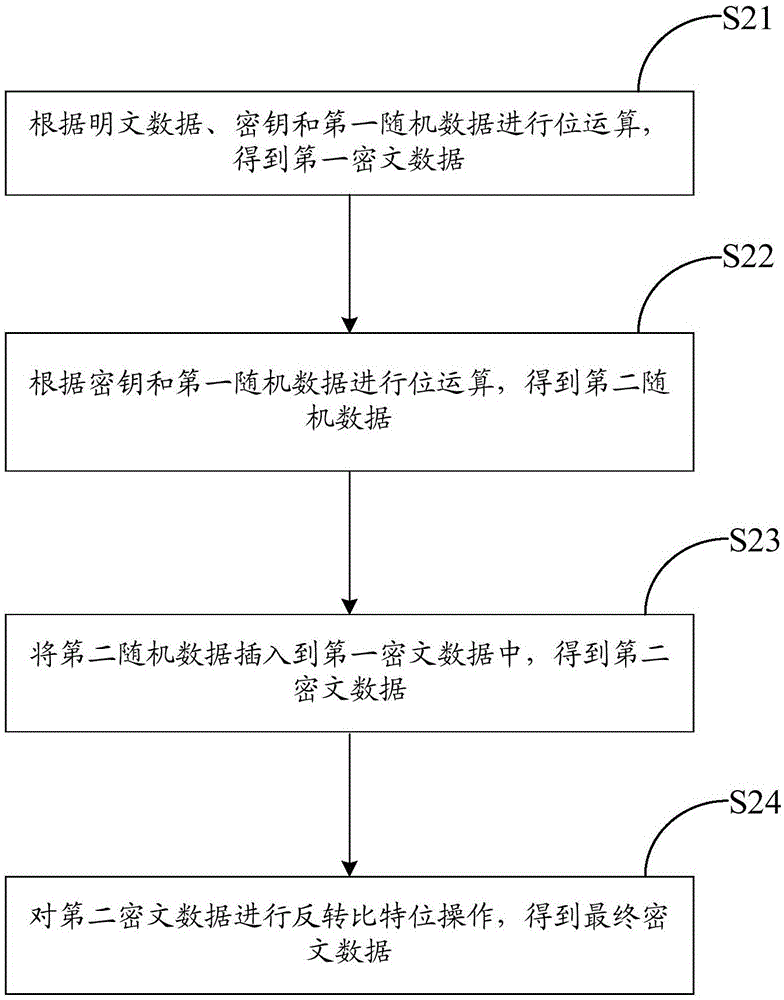
[0072] Such as figure 2 As shown, the first embodiment of the present invention provides a method for data encryption, the method comprising:
[0073] Step S21, performing bit operations according to the plaintext data, the key and the first random data to obtain the first ciphertext data;
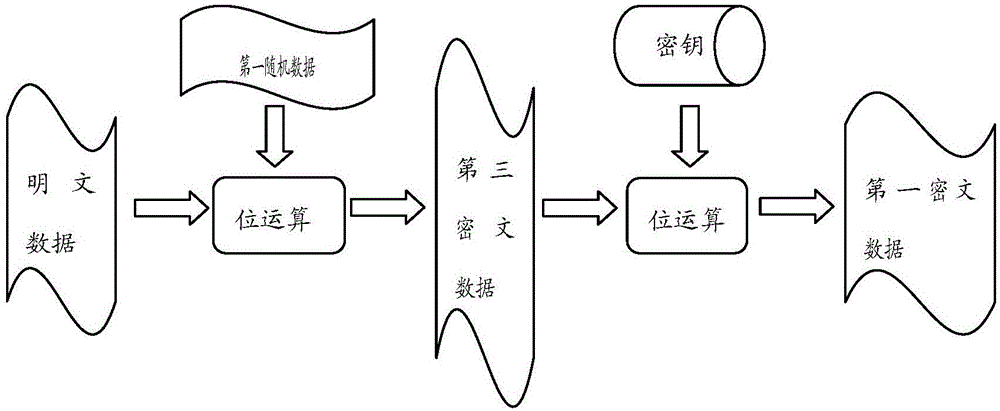
[0074] In the first embodiment of the present invention, as image 3 As shown, the plaintext data can first perform a bit operation (such as an XOR operation) with the first random data to obtain the third ciphertext, and then let the third ciphertext and the key perform a bit operation (such as an XOR operation) to obtain the first encryption text data. Of course, the plaintext data can also perform bit operations (such as XOR operation) with the key to obtain the third ciphertext, and then let the third ciphertext and the first random data perform bit operations (such as XOR operation) to obtain the first ciphertext data. Wherein the specific obtaining of the first ciphertext data c...
no. 2 example
[0084] Such as Image 6 As shown, the second embodiment of the present invention provides a method for data encryption, the method comprising:
[0085] Step S61, according to the first length value of the plaintext data, determine the second length value of the final ciphertext data, wherein the second length value is the minimum integer multiple of a natural number greater than the preset value, and the second length value is greater than the first length value;
[0086] In the second embodiment of the present invention, the above-mentioned preset value can be 2. Of course, it can be understood that in the second embodiment of the present invention, the specific value of the preset value is not limited, and can be adjusted according to actual needs .
[0087] Step S62, obtaining a third length value of the first random data according to the difference between the second length value and the first length value;
[0088] Step S63, generating first random data according to a ...
no. 3 example
[0115] Such as Figure 7 As shown, the third embodiment of the present invention provides a data encryption device, which includes:
[0116] The first operation module 71 is used to perform bit operations according to the plaintext data, the key and the first random data to obtain the first ciphertext data;
[0117] The second operation module 72 is used to perform bit operation according to the key and the first random data to obtain the second random data;
[0118] Insertion module 73, for inserting the second random data into the first ciphertext data to obtain the second ciphertext data;
[0119] The first operation module 74 is configured to perform a bit inversion operation on the second ciphertext data to obtain final ciphertext data.
[0120] Among them, the device also includes:
[0121] The first determination module is configured to determine the second length value of the final ciphertext data according to the first length value of the plaintext data, wherein th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com