Patents
Literature
280results about How to "Avoid direct access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
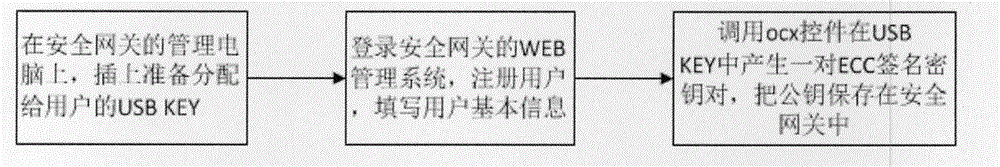
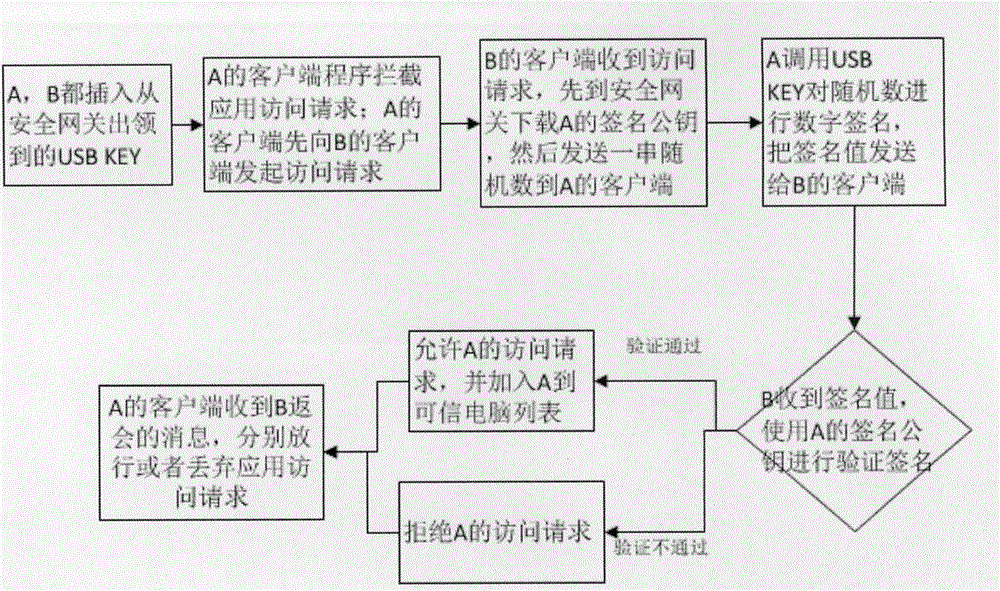
Terminal access method and terminal access device
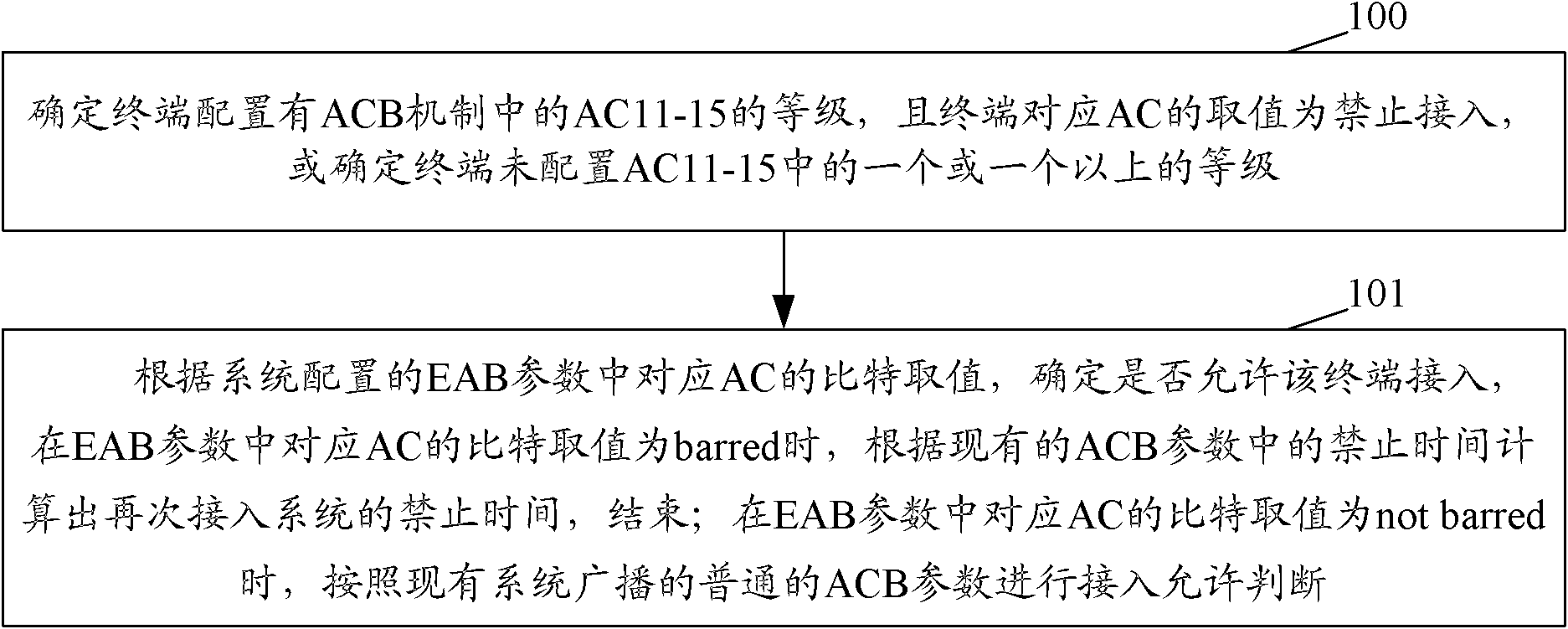
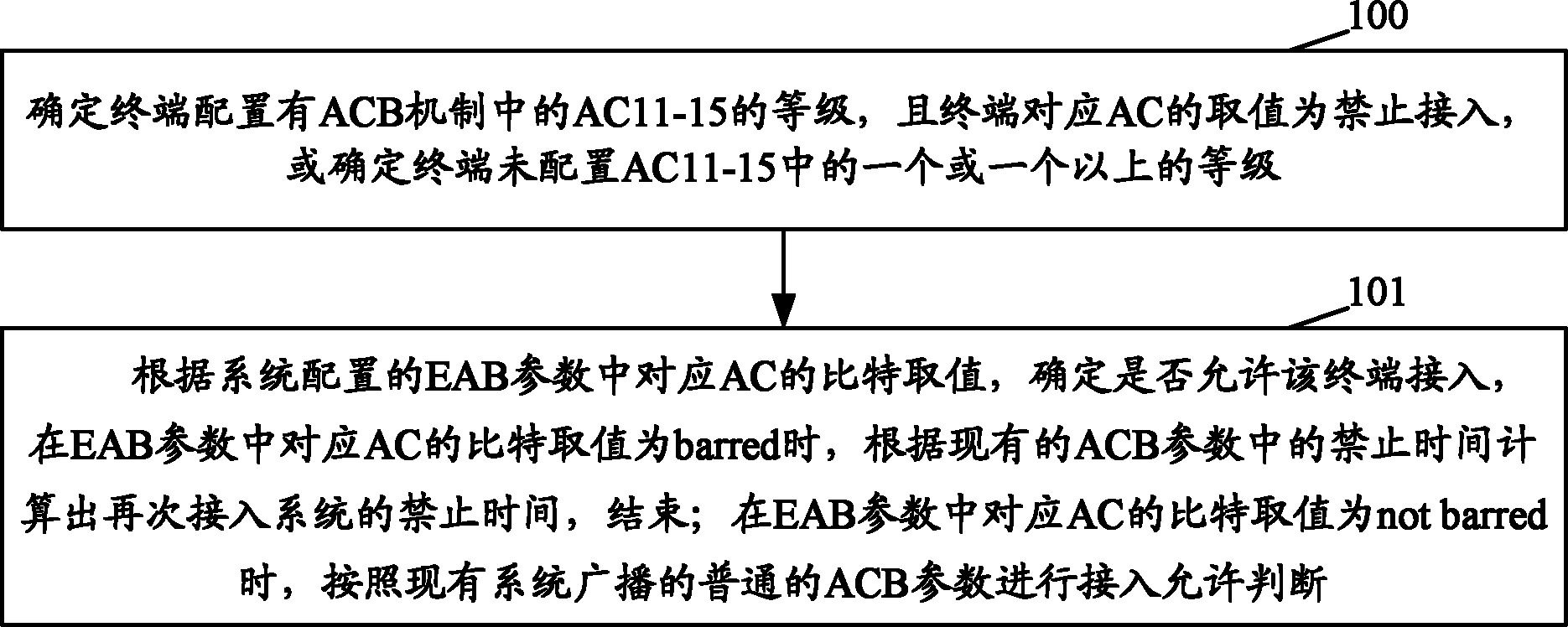
The invention discloses a terminal access method and a terminal access device. The terminal access method comprises the following steps: on the basis of a bit value of a corresponding Access Class (AC) within an Enhanced Access Barring (EAB) parameter configured by a system, determining whether to allow the AC terminal to access; if the bit value of the corresponding AC within the EAB parameter is barred, then, on the basis of a barred time within the existing Access Class Barring (ACB) parameter, calculating a barred time for re-accessing the system and ending the process; and if the bit value of the corresponding AC within the EAB parameter is not barred, then, according to an existing system-broadcasted common ACB parameter, determining that access is allowed. According to the terminal access method and the terminal access device, the EAB and an existing ACB mechanism are combined for processing so as to solve the problem of possible impact on the system when the network is accessed concurrently by large numbers of delay-insensitive or low-priority services or terminals. Also, during the occurrence of an unexpected event, as the EAB applicable terminal is provided with appropriate control, the terminal is prevented from directly accessing the system without constraint, thereby shortening the delays and the duration of system congestion during the unexpected event.
Owner:ZTE CORP
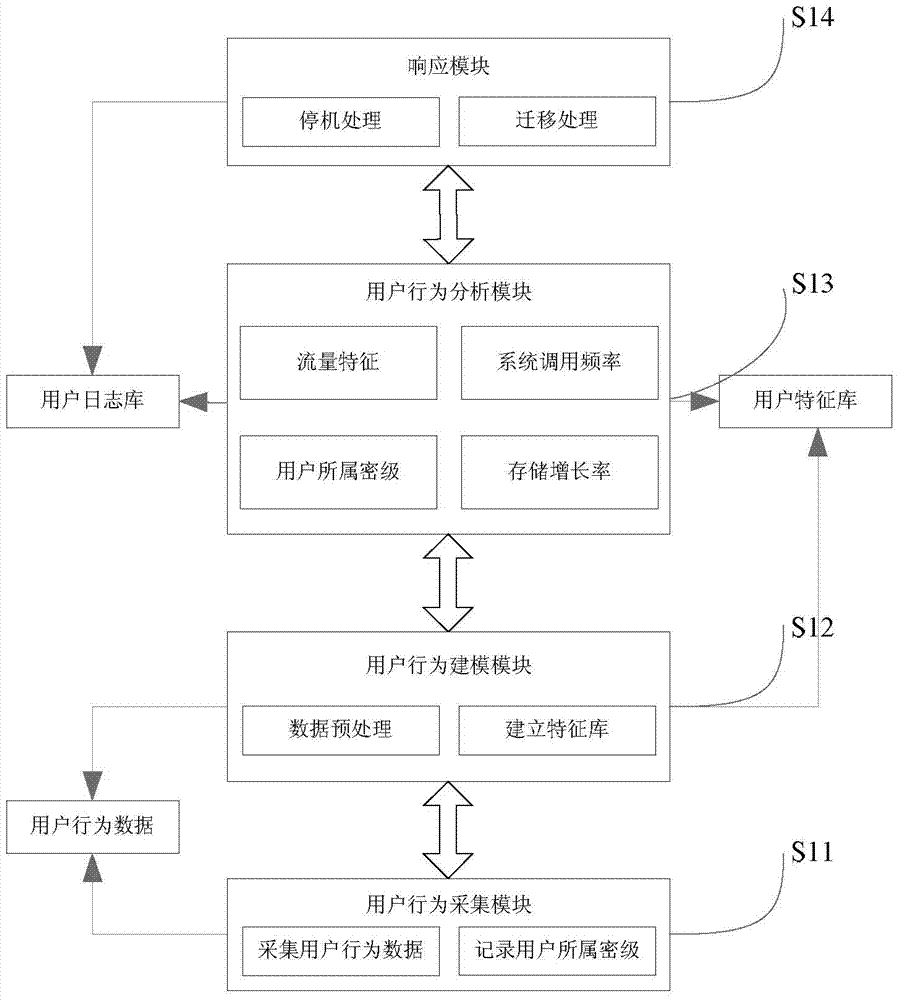
Virtual machine security isolation system and method oriented to multi-security-level virtual desktop system
ActiveCN103902885AAvoid direct accessReduce dependenceError detection/correctionPlatform integrity maintainanceAnomaly detectionSystem call
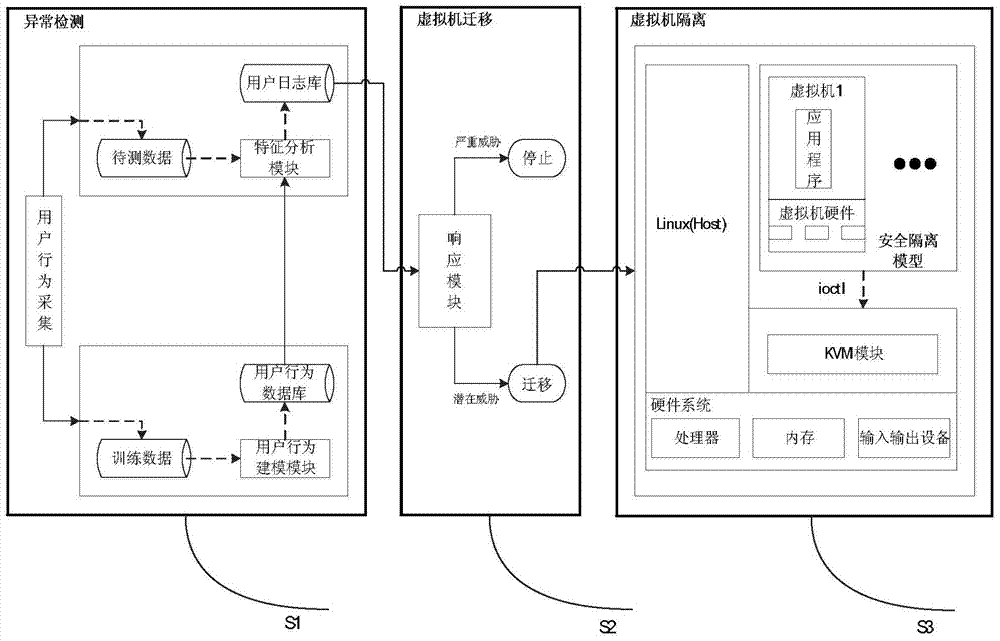
The invention discloses a virtual machine security isolation system and method oriented to a multi-security-level virtual desktop system and belongs to the field of information security. According to the virtual machine security isolation system and method, three implementation stages including detection of abnormal user behaviors, migration of virtual machines and security isolation are conducted. The virtual machine security isolation method comprises the steps that firstly, users of networks of the same security classification and virtual machines are bound together, and a user behavior feature library is established through the similarity between the operation behaviors of the users of the networks of the same security classification; secondly, matching between real-time actual user behavior features and a historical user behavior feature liberty is conducted, the threat level of the current operation of each user is worked out, a target host is selected and migrated, and the virtual machines with potential threats are migrated to a virtual machine security isolation model for execution; finally, the virtual machine security isolation model replaces the virtual machines to execute system call required by the virtual machine process. By the adoption of the virtual machine security isolation method oriented to the multi-security-level virtual desktop system, the situation that the virtual machine process directly has access to resources of a host machine system is avoided, the dependence of the virtual machine process on a kernel is reduced, the safety of the host machine system is improved, and the purpose of security isolation of the virtual machines is achieved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM +1
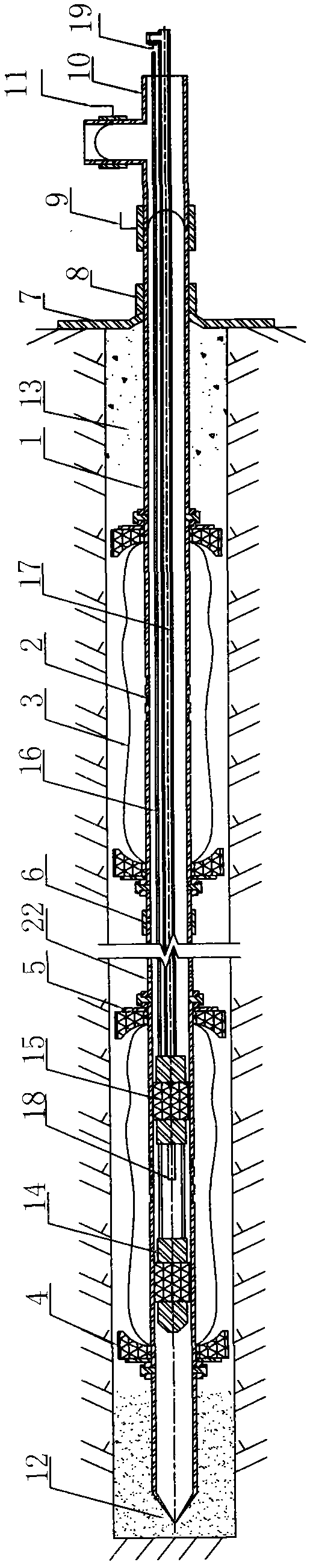
Mold bag grouting method and device for quickly and uniformly reinforcing soft stratum
InactiveCN102003189AFast and uniform reinforcementAvoid direct accessUnderground chambersTunnel liningBall valveMechanical index
The invention belongs to reinforcement and improvement technology of soft surrounding rocks of tunnels and underground engineering, and mainly provides a mold bag grouting method and a mold bag grouting device for quickly and uniformly reinforcing a soft stratum. The device is provided with a primary grouting unit and a secondary grouting unit; the pipe wall of a grouting pipe (1) of the secondary grouting unit is provided with a plurality of slurry outlets (2), a mold bag (3) is sleeved on the grouting pipe (1) of the secondary grouting unit, and two ends of the mold bag are hooped on the grouting pipe; a pre-tightening unit consisting of a cushion plate (7) and a nut (8) is sleeved on the grouting pipe (1) of the secondary grouting unit at the orifice position, and the other end of the grouting pipe (1) of the secondary grouting unit is connected with a secondary grouting pipeline through two ball valves; and the primary grouting unit is provided with a grouting device consisting of a double-bag grouting plug (14), a primary grouting unit slurry conveying steel pipe (17) and a hand pump. The method and the device can realize quick and uniform reinforcement of the soft surrounding rocks, improve the physical and mechanical indexes of the soft surrounding rocks, increase the stability of the soft surrounding rock, meanwhile, realize region controlled grouting and avoid slurry loss.
Owner:CHINA RAILWAY TUNNEL GROUP CO LTD
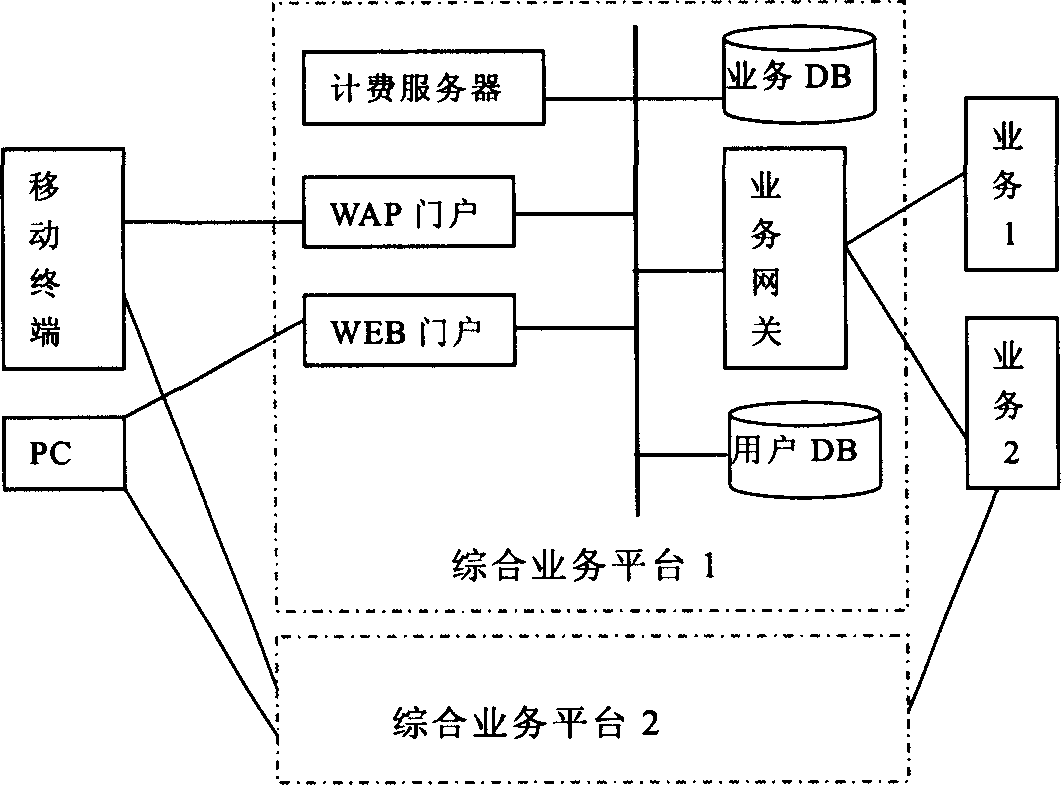
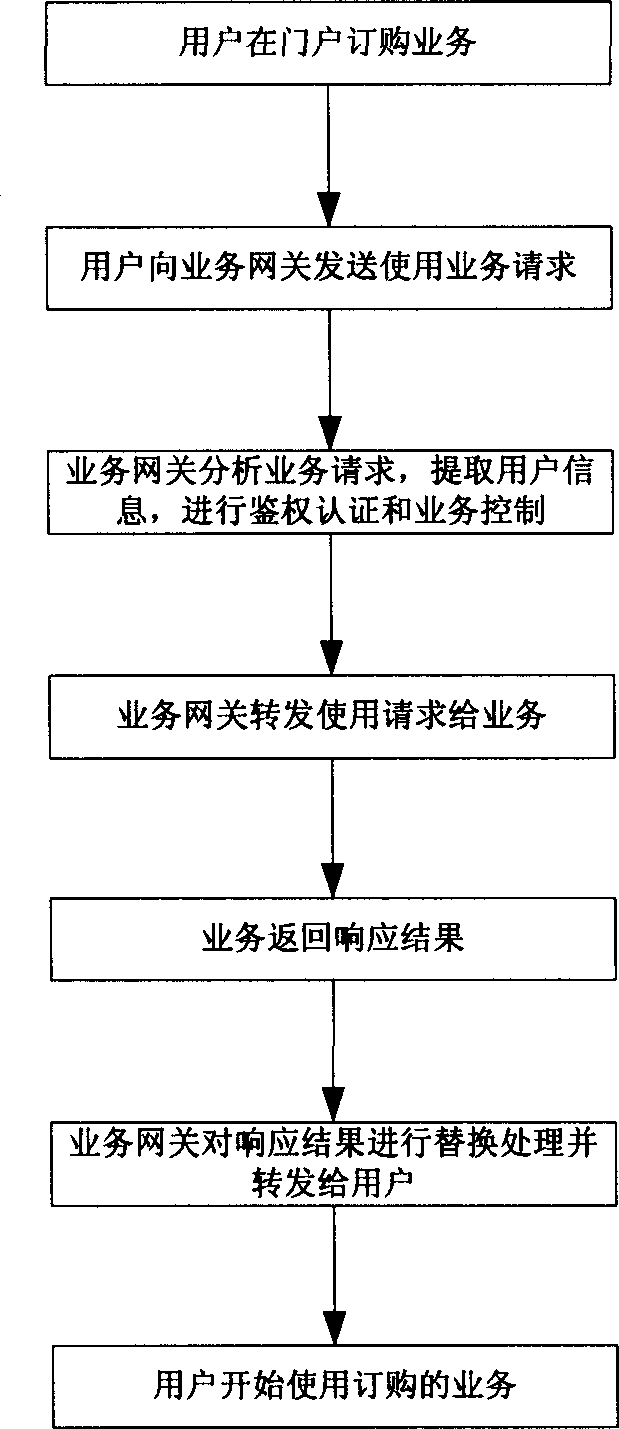
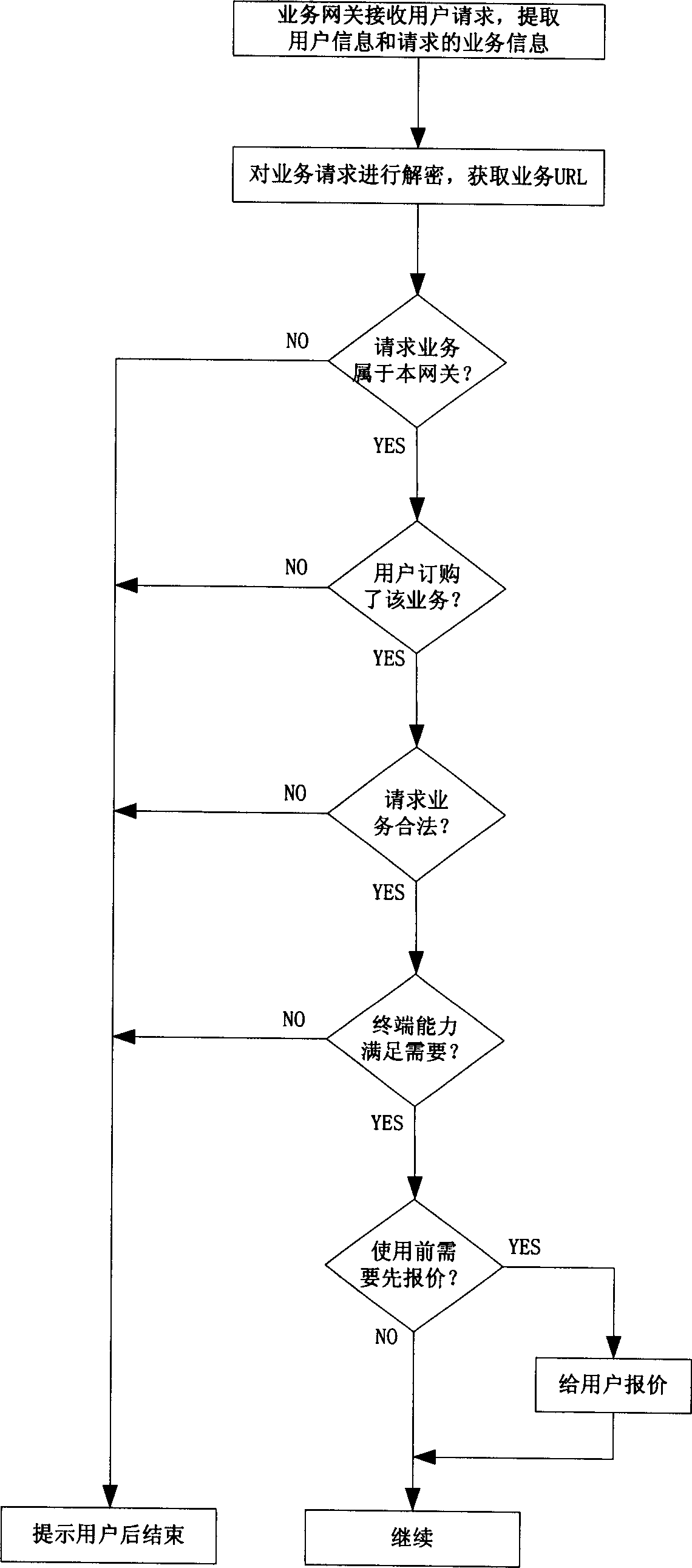
Comprehensive business platform and its business flow path control method
InactiveCN1556634AReduce the burden onIncrease independenceNetwork connectionsService gatewayMedia access control
The invention discloses a synthesis service platform and the service flow control method, which belongs to data communication field. The invention adds a service gateway between the client and the service, which completes the services accessing control except completing the flow control and changing function of WAP gateway and the certification and authority incrimination. The service gateway uses the alternation of URL and Cookie, prevents the user from winding the service gateway to access service. The service gateway can include other functions, such as log recording, statistic analysis. Compared with original synthesis service platform and service flow control method, the method reduces the burdens of the WAP gateway greatly, enhances the independence of the WAP gateway; otherwise, it increases the flexibility of the synthesis service platform, thus the platform can carry on flexible charging method to the service; and it supports multiple synthesis service platforms, and reduces the cost.
Owner:ZTE CORP
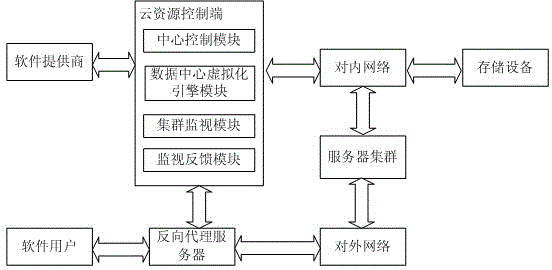
Architecture of elastic cloud
InactiveCN103957237AReduce loadSave resourcesTransmissionSoftware simulation/interpretation/emulationElastic cloudReverse proxy
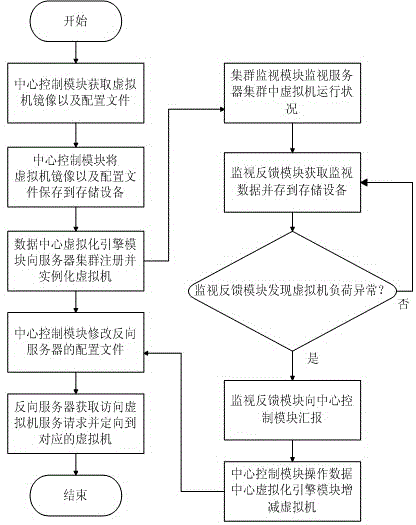
The invention provides an architecture of elastic cloud. The architecture of elastic cloud comprises a cloud resource control end, an internal network, a storage device, a reverse proxy server, an external network and a server cluster, wherein the cloud resource control end, the internal network and the storage device are connected in sequence, the reverse proxy server and the external network are connected in sequence, the cloud resource control end is connected with the reverse proxy server, a software provider has access to the cloud resource control end, virtual machine images and configuration files are uploaded and are stored in the storage device by the cloud resource control end through the internal network, virtual machines are registered in the server cluster and instantiated, and the configuration files of the reverse server are modified. According to the architecture of elastic cloud, by monitoring the virtual machines running in elastic cloud, service in the elastic loud is guaranteed to be always in the healthy state according to the load dynamic flexible service capacity of the virtual machines, and it is guaranteed that after the server cluster changes, a user request can not be sent to the service virtual machines which do not exist any more.
Owner:SOUTH CHINA UNIV OF TECH
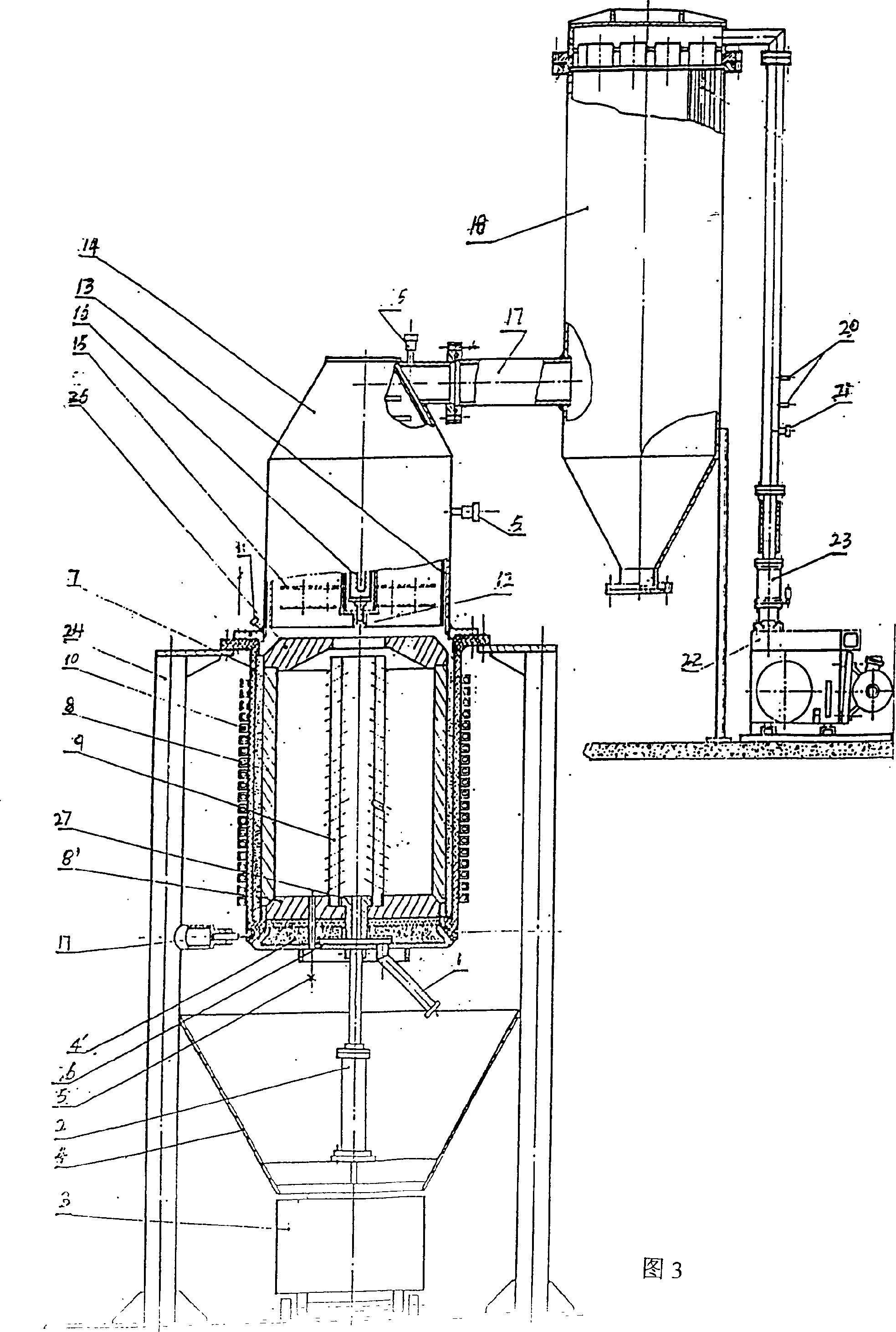
Rose essential oil and rose pure dew extraction equipment
InactiveCN101353611AAvoid direct accessInhibition of dissolutionEssential-oils/perfumesDistillationEngineering
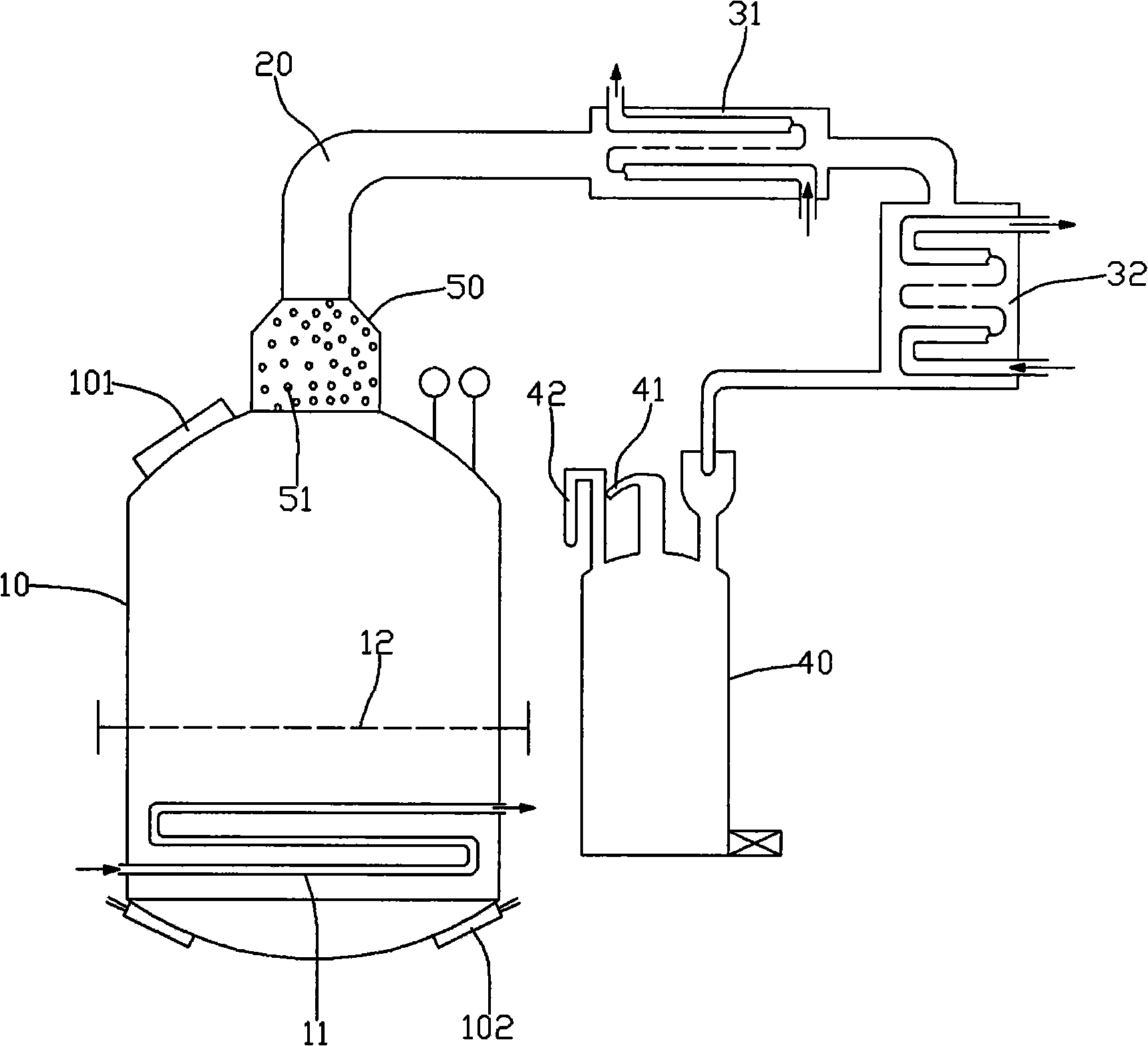
The invention discloses extraction equipment for rose essential oil and rose hydrosol which mainly includes a distillation still, a steam conduit, a condenser and an oil-water separator, wherein, the distillation still is connected with the oil-water separator by the steam conduit and the condenser; the lower end of the interior of the distillation still is provided with a steam heating coil; and the upper part of the steam heating coil is provided with a transverse plate sieve which can be opened freely. An adsorption plant is arranged between the top of the distillation still and the steam conduit and internally filled with active ceramic rings serving as an absorbent. The extraction equipment of the invention has the advantages of simple operation, convenient use and high production efficiency, and can greatly enhance the quality of the rose essential oil and the rose hydrosol.
Owner:许向梅
Safe processing and accessing method of cloud resource
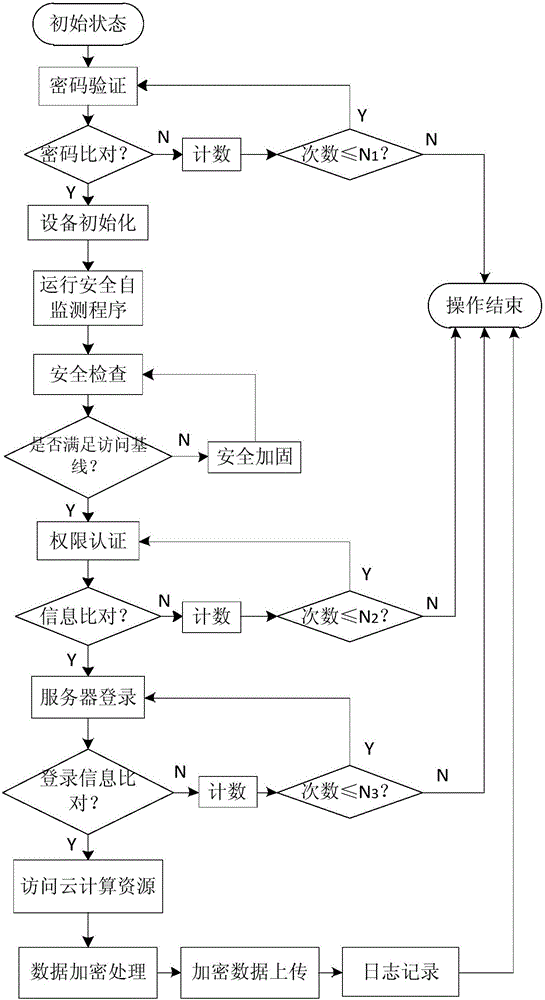
The invention discloses a safe processing and accessing method of a cloud resource, wherein the safe processing and accessing method of the cloud resource is based on a standalone third-party mobile storage device and a hardware platform which is used for interacting with a user; the third-party mobile storage device includes a control chip and a memory; programs running in the control chip include a control module and a file system module; the memory consists of an encrypted storage area and an ordinary storage area; the control chip calls the file system module, through the control module, to access the encrypted storage area and the ordinary storage area of the memory; the ordinary storage area includes a terminal safety monitoring program; the encrypted storage area includes a device password, identity authentication information, an encryption secret key and an algorithm software carrier. By using the safe processing and accessing method of the cloud resource, which is provided by the invention, a whole operating environment is guaranteed to be safe and reliable; data stored in a cloud database is encrypted; an illegal user is prevented from directly obtaining plaintext data; the data of the user are guaranteed not to be stolen and leaked.
Owner:新昌县七星街道明盛模具厂
Optical sensor for high-flux dust particle counter
InactiveCN101470066AImprove power densityReduce feverMaterial analysis by optical meansIndividual particle analysisAspheric lensRoad surface
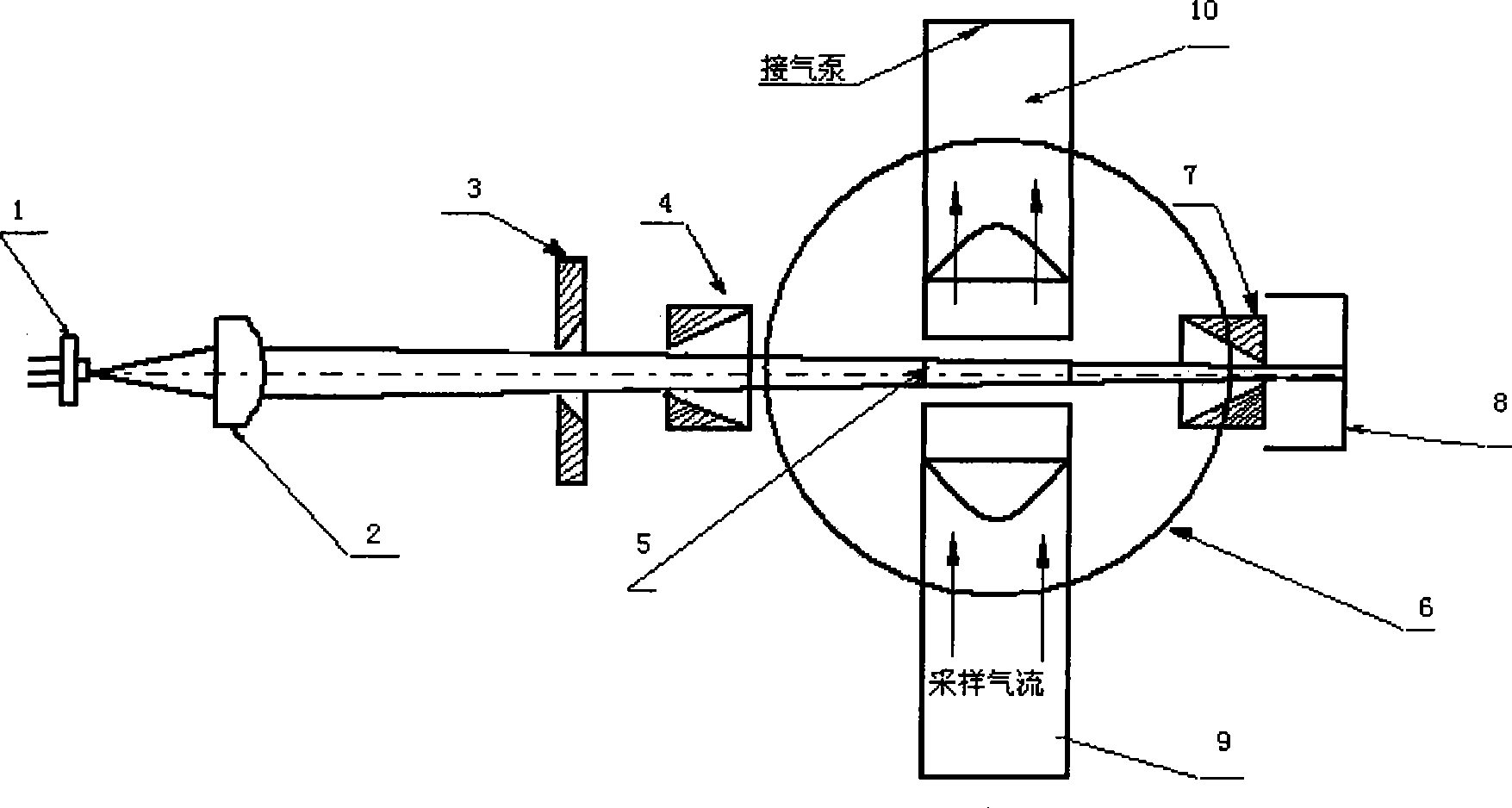
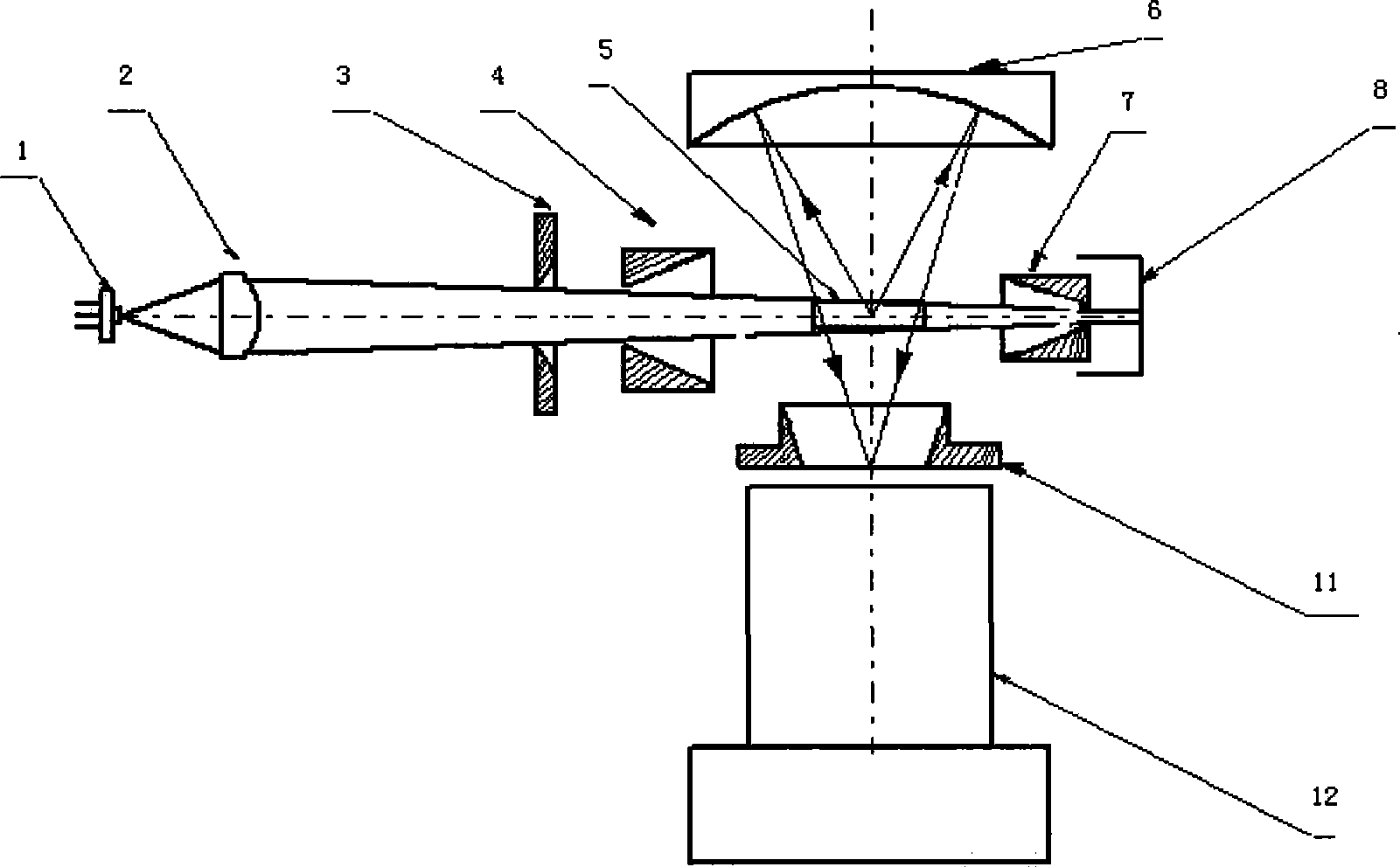
The invention relates to an optical sensor of large flux dust particle counter, comprising a laser source, wherein the light path of the laser source is provided with an aspheric lens, an indicant stop, an outgoing stop and a light trap in turn; a light path surface mirror, field stop and a photoelectric detector are arranged between the incident stop and the outgoing stop and vertical to the light path; a light sensitive zone and the light sensitive surface of the photoelectric detector are respectively arranged at two sides of the spherical center of the spherical mirror; the rectangle field stop is arranged at the front of the photoelectric detector and fit with the shape of the light sensitive zone. The illumination light path and scattered light collection light path of the optical sensor have simple design and easy adjustment. A stop is arranged at the front of the light sensitive zone to reduce the scattered light entering into the chamber, and a stop is arranged between the light sensitive zone and the light trap to prevent the light beam entering into the light trap from being reflected back to the chamber, thereby improving the signal noise ratio of the sensor. The field stop adopts a horn mouth type obscuration stop for preventing scattered light on the light path from directly entering into the detector.
Owner:NANJING UNIV OF SCI & TECH
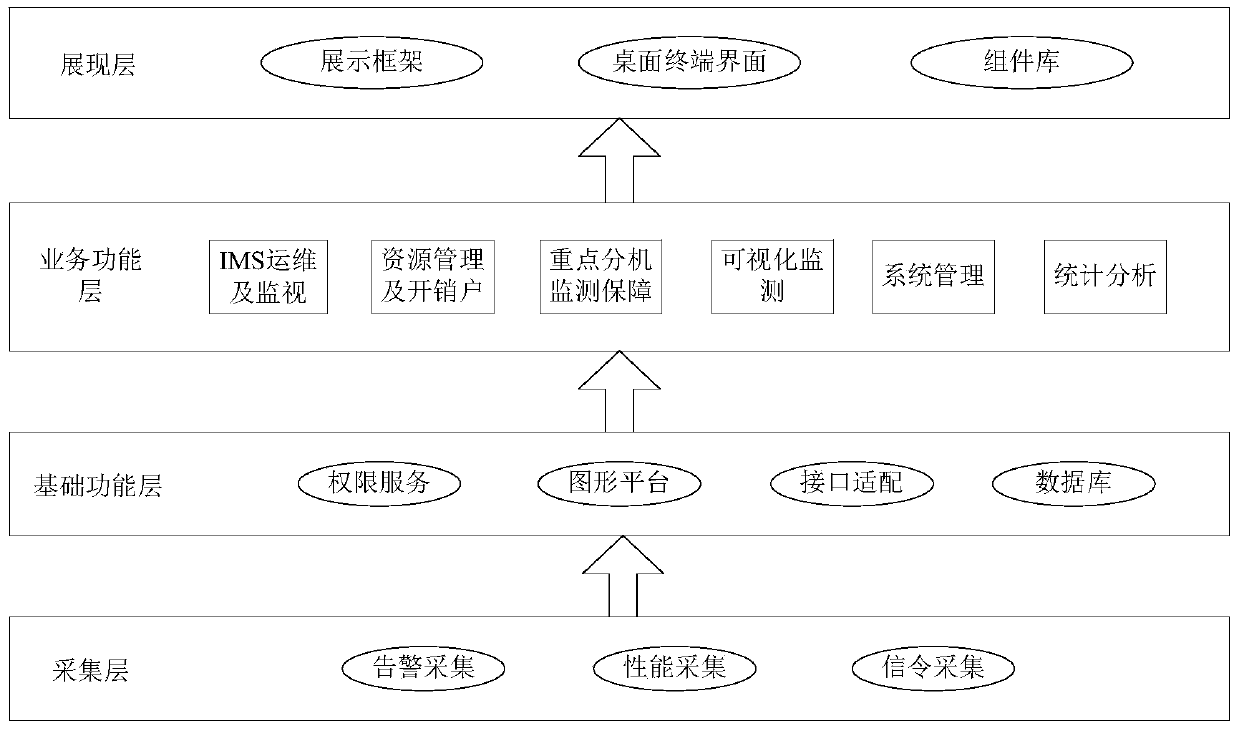
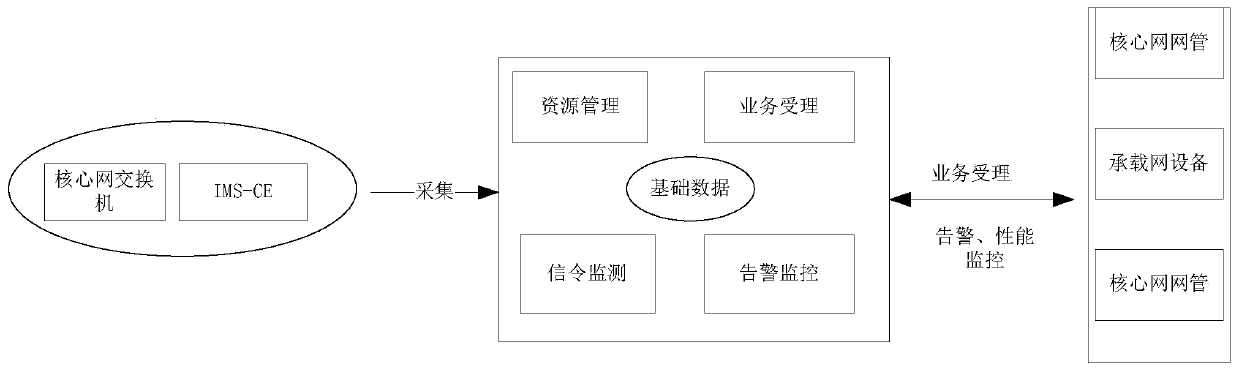
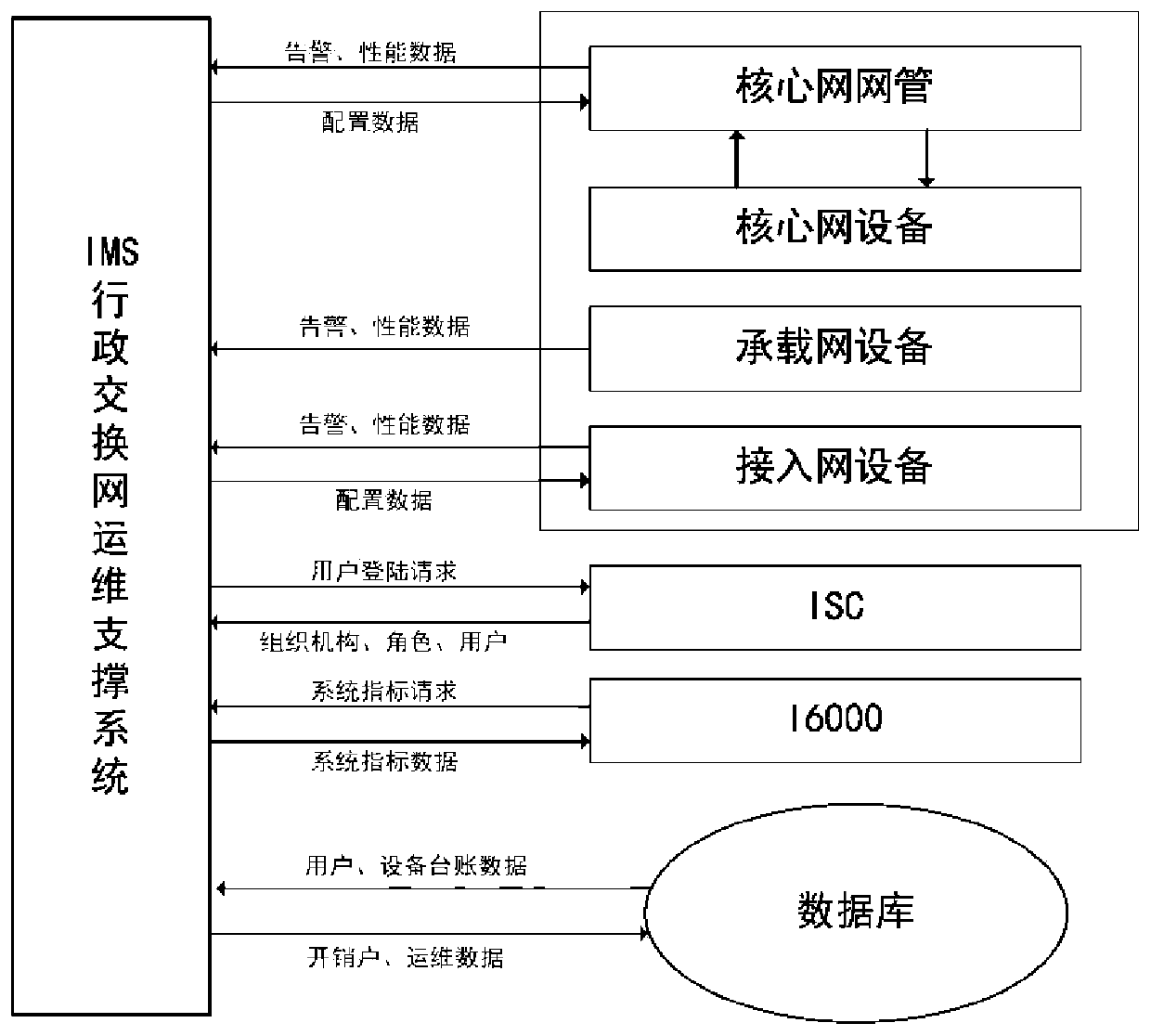
An IMS full-service network monitoring intelligent operation and maintenance support system based on big data analysis
ActiveCN109831327ARealize the real-name systemImprove efficiencyData switching networksExchange networkStatistical analysis
The invention discloses an IMS full-service network monitoring intelligent operation and maintenance support system based on big data analysis, and the system comprises a processor which receives resource management data, service acceptance data, signaling monitoring data, and alarm monitoring data collected by a data collection end, and carries out analysis, storage, and display; the processor comprises an IMS operation, maintenance and monitoring module, a resource management and overhead account module, a key extension monitoring guarantee module, a visual monitoring module, a system management module and a statistical analysis module. The method has the advantages that integrated, intelligent and automatic operation and maintenance management of all devices and terminals of the IMS exchange network is achieved, a user real-name system is achieved, the operation and maintenance work efficiency and the operation safety and reliability of the IMS exchange network are improved, and better technical support is provided for operation and maintenance and management of electric power communication.
Owner:STATE GRID INFORMATION & TELECOMM BRANCH
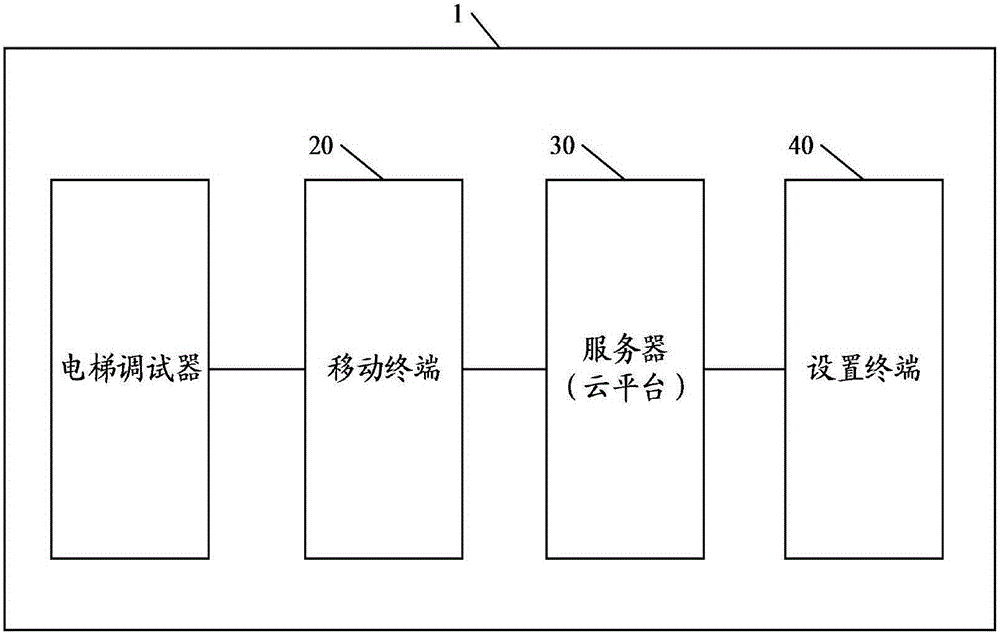
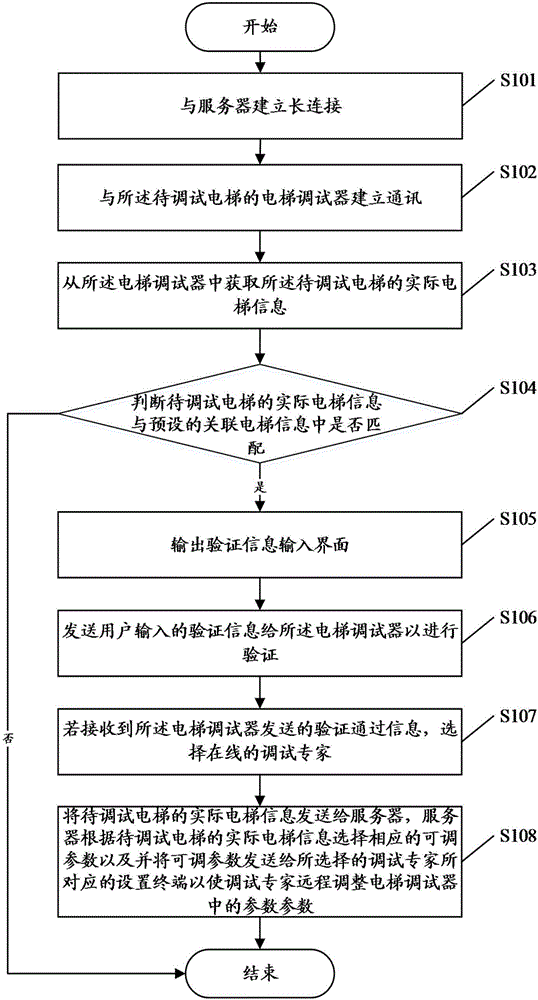
Elevator remote debugging method, application terminal and debugging system
The embodiment of the invention discloses an elevator remote debugging method. The elevator remote debugging method comprises the steps that a long connection is established with a server; communication is established with an elevator debugger of an elevator to be debugged; actual elevator information of the elevator to be debugged is obtained from the elevator debugger; whether the actual elevator information is matched with preset associated elevator information or not is judged; if the actual elevator information is matched with the preset associated elevator information, a verification information input interface is output; verification information input by a user is sent to the elevator debugger to be verified; if verifying-passing information is received, an on-line debugging specialist is selected; and the actual elevator information of the elevator to be debugged is sent to the sever, and the sever selects a corresponding adjustable parameter according to the actual elevator information of the elevator to be debugged and send the adjustable parameter to a setting terminal corresponding to the selected debugging specialist to enable the debugging specialist to remotely regulate the adjustable parameter in the elevator debugger. The embodiment of the invention further discloses an application terminal and a debugging system. According to the elevator remote debugging method, the application terminal and the debugging system, the elevator debugging efficiency and debugging safety are improved.
Owner:INVT ELEVATOR CONTROL TECH WUXI
Backlight module and liquid crystal display device
InactiveCN102748658AAvoid spotlightImprove the problem of uneven distribution of light and darkPoint-like light sourcePlanar/plate-like light guidesLiquid-crystal displayLight guide
The invention provides a backlight module and a liquid crystal display device. The backlight module comprises a light guide plate, a light bar and an optical membrane, wherein the light guide plate comprises a light-in surface and a light-out surface connected with the light-in surface; the light bar is arranged on one side of the light-in surface; multiple LED light sources are spaced on the side of the light bar close to the light-in surface; the optical membrane is arranged on the light-out surface; multiple notches are arranged on the side of the optical membrane close to the light bar; and the multiple notches are in one-to-one correspondence with the multiple LED light sources. In the invention, by use of the optical membrane subjected to shape cutting according to the arrangement of the LED light sources, the problem of non-uniform brightness distribution on the light-in side of the backlight module is solved, the quality of the backlight module is improved, and the problem of light leak of the backlight module due to the narrow frame is solved.
Owner:SHENZHEN CHINA STAR OPTOELECTRONICS TECH CO LTD
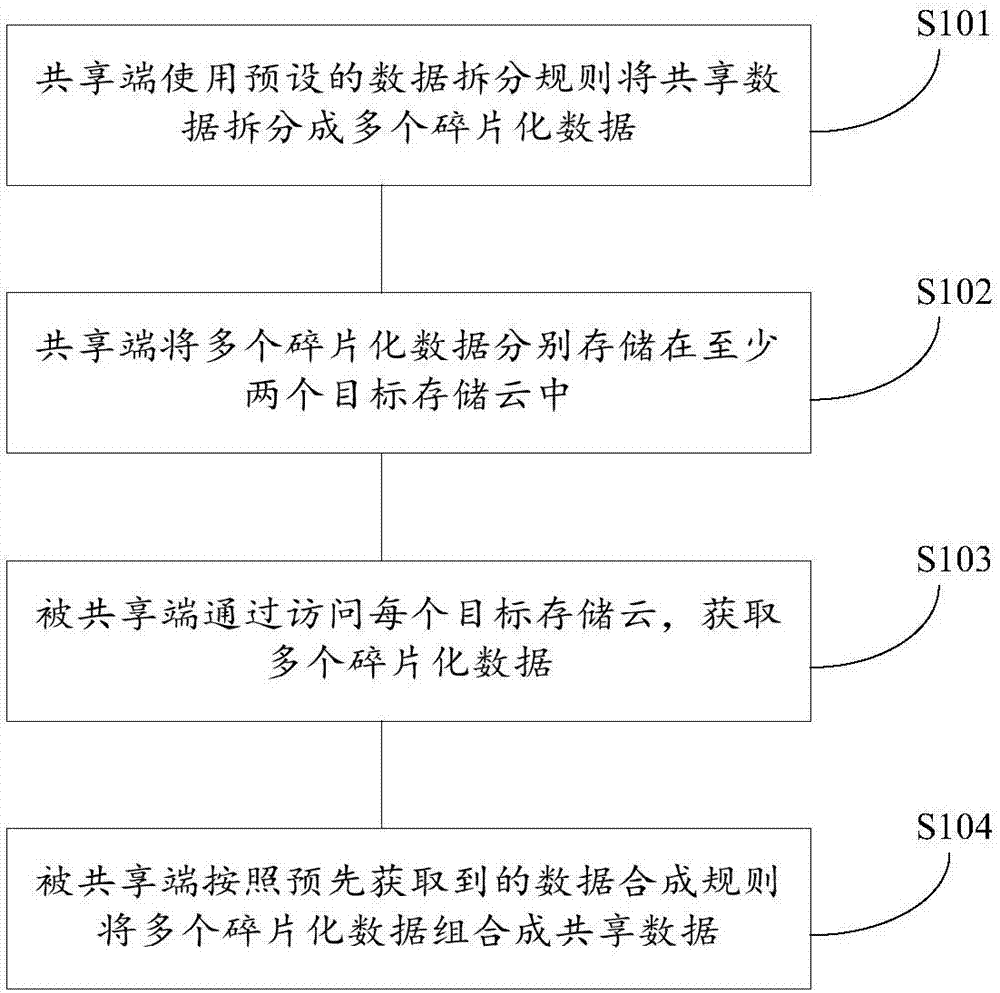
Data sharing method and system based on multi-cloud storage
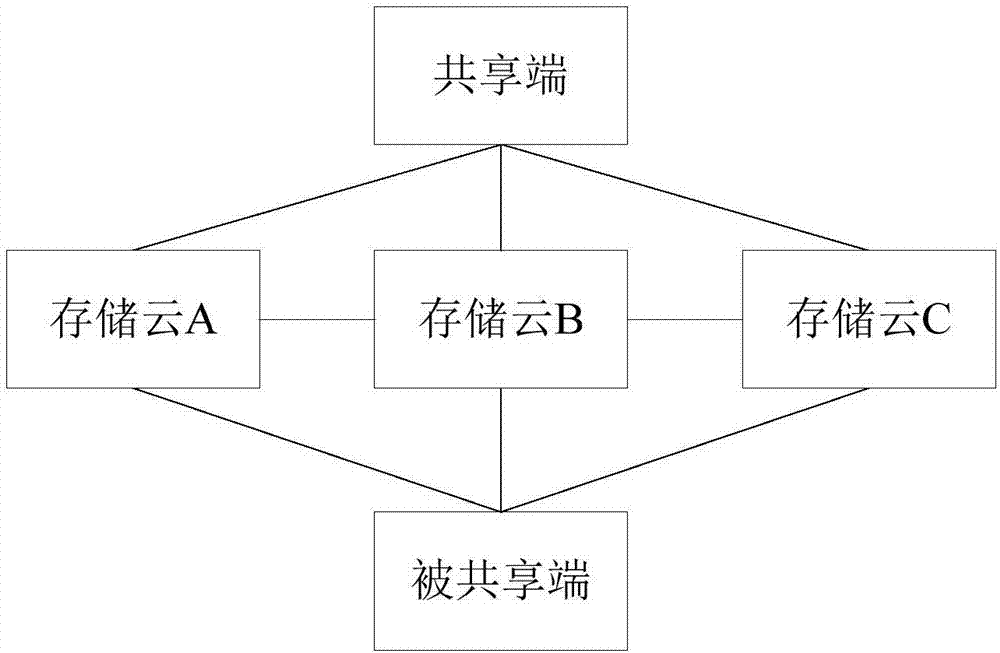
InactiveCN106911770AAvoid direct accessEnsure safetyTransmissionSpecial data processing applicationsThird partyData needs
The invention provides a data sharing method and system based on multi-cloud storage, and relates to the technical field of the cloud. The data sharing method based on the multi-cloud storage provided by the invention comprises the following steps: firstly splitting shared data needing to be shared into multiple fragmented data by a sharing end, and respectively storing the fragmented data into at least two target storage clouds; accessing the target storage clouds to acquire all fragmented data when a shared end wants to acquire the shared data, and then forming the complete shared data by use of data synthesis rule obtained in advance, namely, accomplishing the sharing process of the data. In the sharing process, the fragmented data is respectively stored in at least two target storage clouds so as to prevent the third-party from directly acquiring all data; and the third-party is difficult to know the data synthesis rule, so that the fragmented data cannot form the complete shared data even the fragmented data are acquired, and the data security is guaranteed.
Owner:BEIJING GUPANCHUANGSHI SCI & TECH DEV
Satellite attitude rapid maneuver switching control method
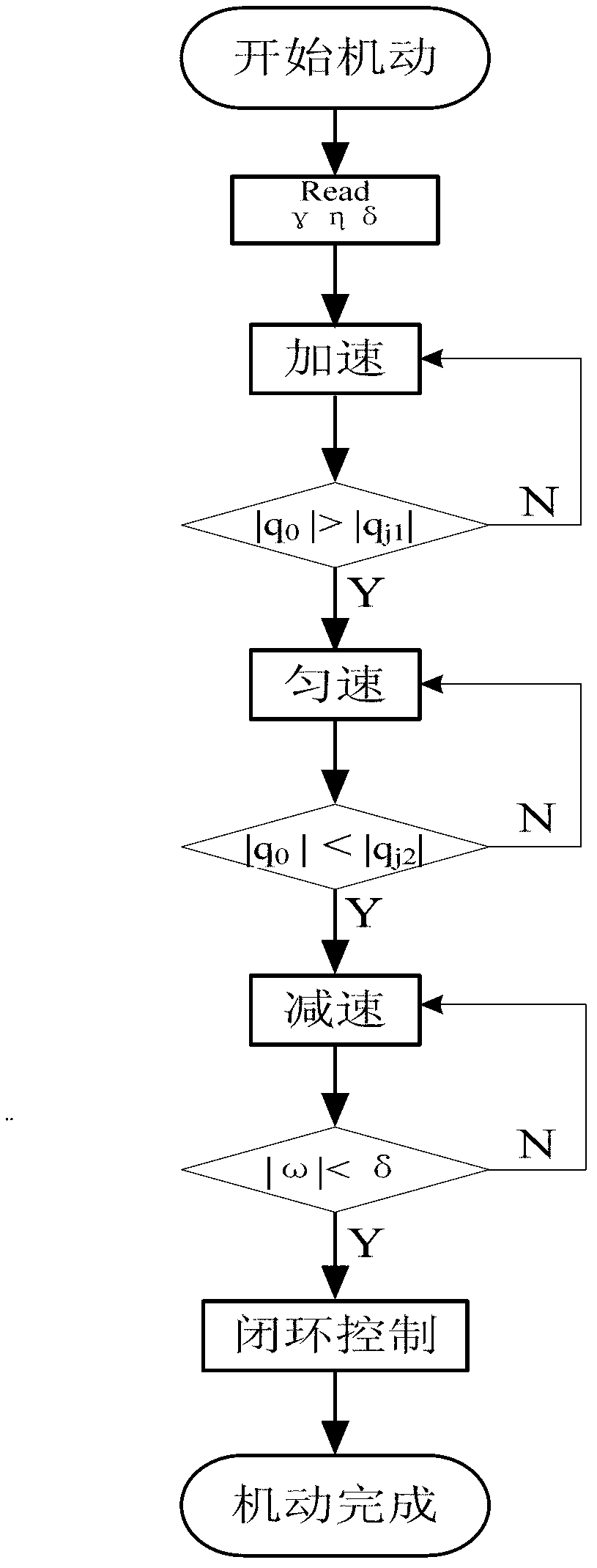
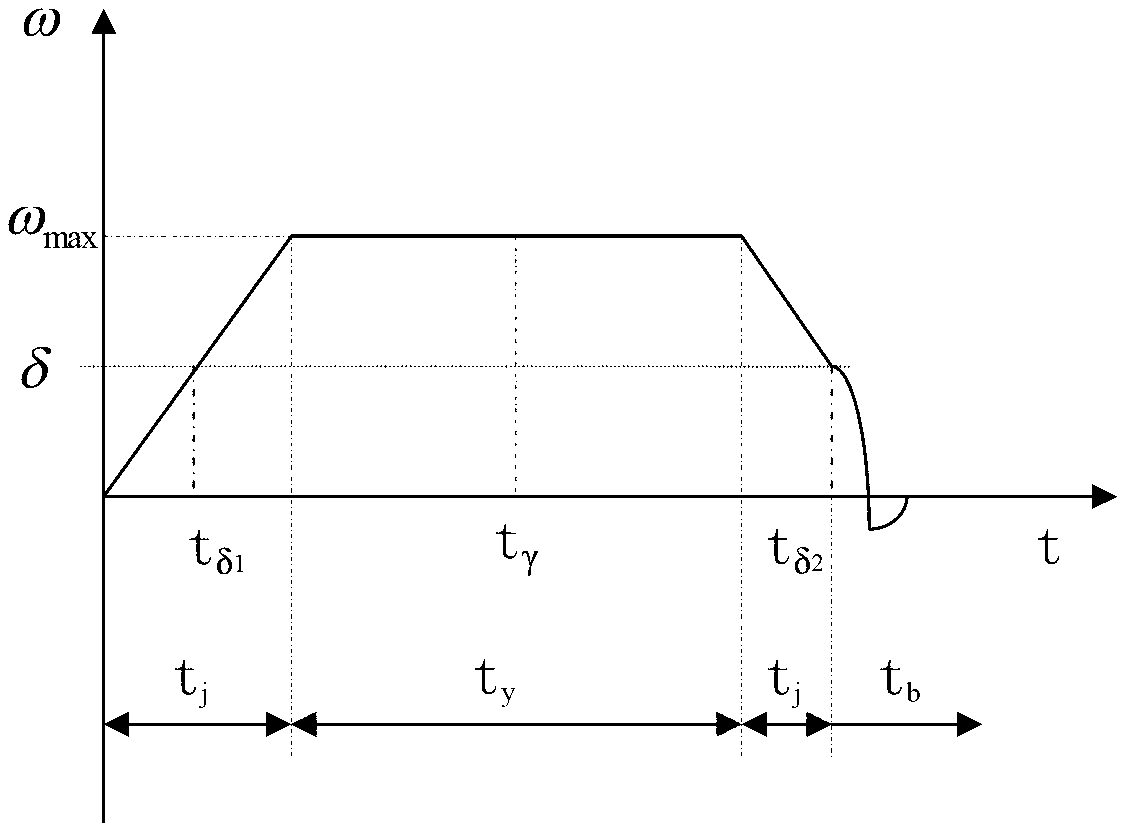
ActiveCN103279036AAvoid the problem of not being able to enter closed-loop controlAvoid direct accessAttitude controlAdaptive controlHandoff controlLoop control
The invention discloses a satellite attitude rapid maneuver switching control method. A used switching parameter delta is used for judging an amplitude of an angular speed to carry out switching, so that compared with an angular position judging method, the rapid and flexible satellite attitude switching control method can avoid the problem that a satellite attitude cannot enter closed-loop control stage due to factor influence of external interference, inertia perturbation and the like; a used switching parameter gamma can avoid partial time during which a small angular speed is included in when maneuver is started, and avoids the satellite attitude directly entering a closed loop stage during the time when maneuver is started, wherein the partial time meets the condition that the absolute value of omega is less than or equal to delta; and a used switching parameter eta can be used to consider engineering constraint and implement automatic switching of acceleration, constant speed, deceleration and closed loop of the attitude maneuver according to received relative attitude quaternion information. The satellite attitude rapid maneuver switching control method realizes accurate switching; rapid attitude maneuver control can be implemented; maneuver around a quaternion Euler axis is implemented; and path planning and time optimization of attitude maneuver are implemented.
Owner:SHANGHAI XINYUE METER FACTORY
Method and device for generating multidimensional cubic based on relational database
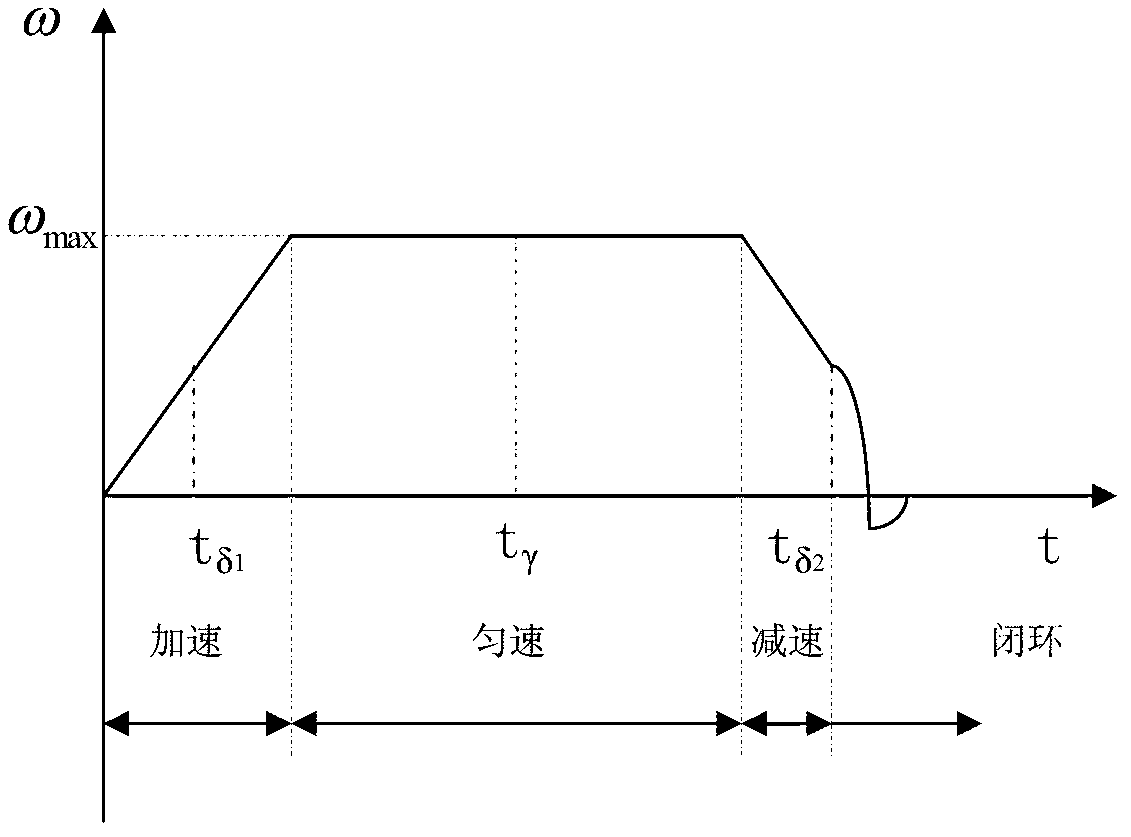
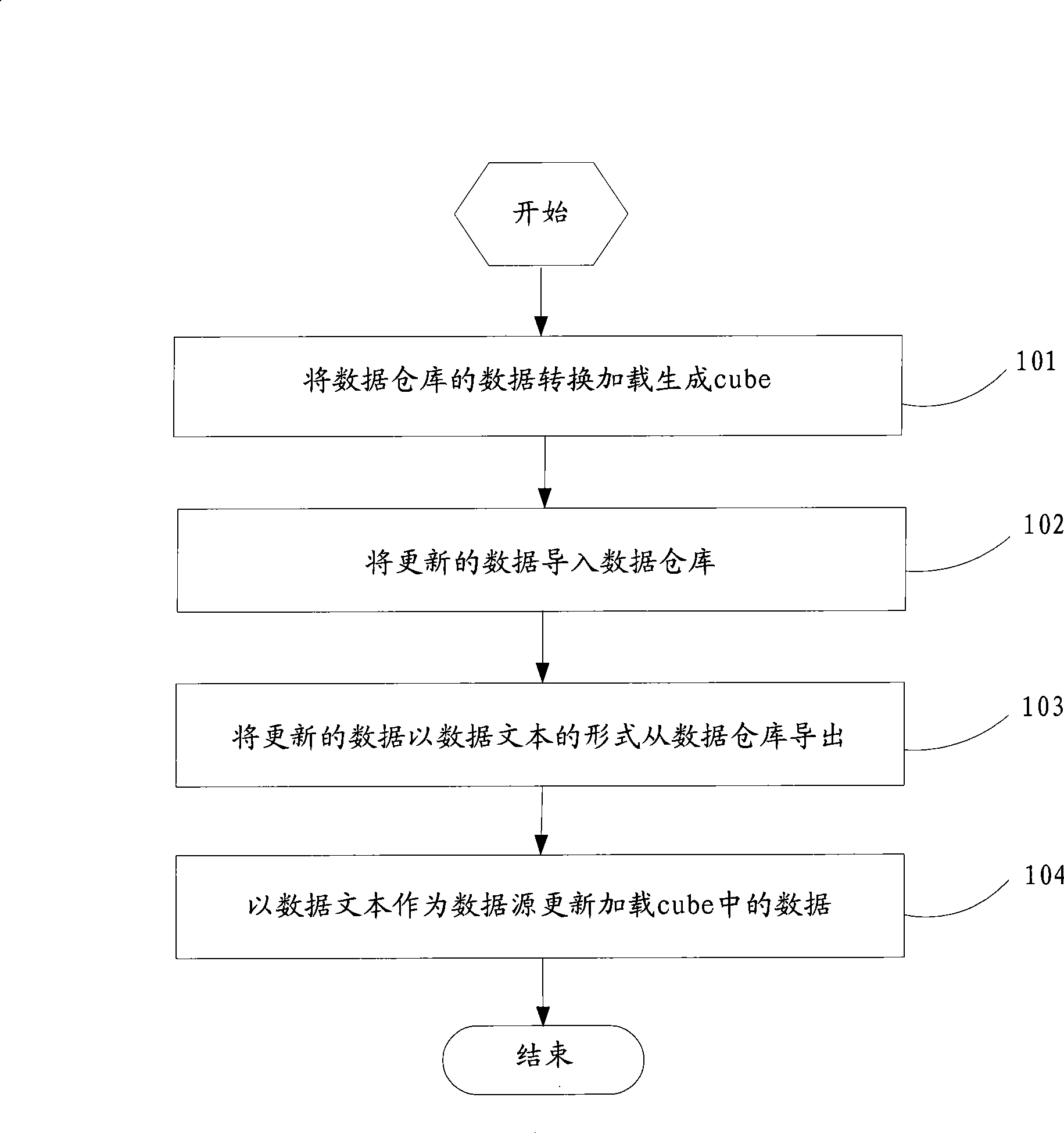
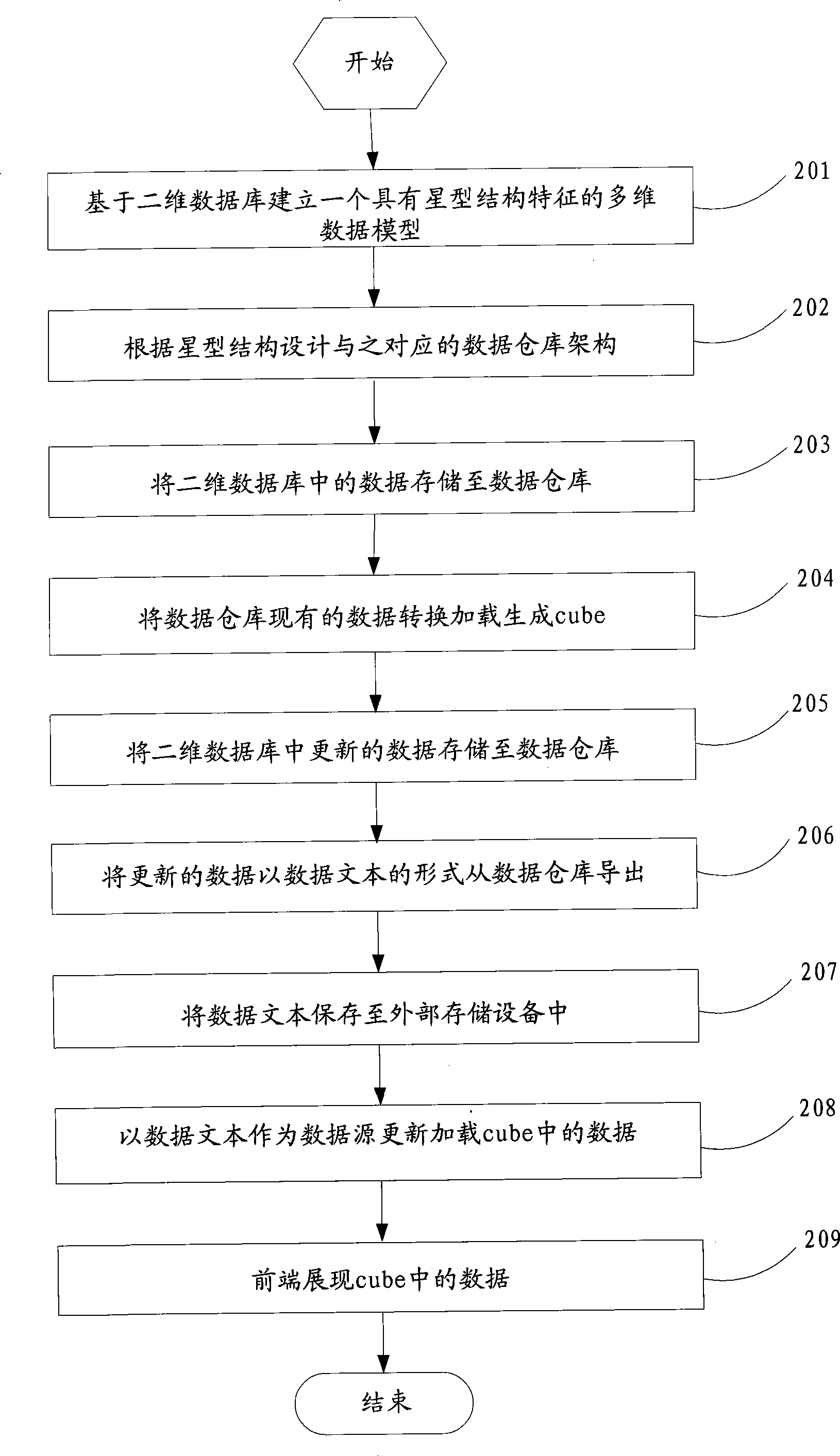
InactiveCN101452485AImprove production efficiencyAvoid direct accessSpecial data processing applicationsData warehouseMultidimensional scaling
The invention discloses a method for generating a multi-dimensional cube based on a relational database. The method comprises: converting and loading data of a data warehouse which is the relational database with a star structure to generate cube; importing updated data into the data warehouse; exporting the updated data from the data warehouse in the form of data text; and taking the data text as a data source to update and load the cube. The method exports the data from the data warehouse in the form of the regular data text first and then takes the data text as the data source to load and update the cube, so as to avoid direct access of the data warehouse when updating the cube, lighten the load pressure caused by frequent access of the data warehouse, and improve the efficiency of cube generation.
Owner:CHINA CONSTRUCTION BANK
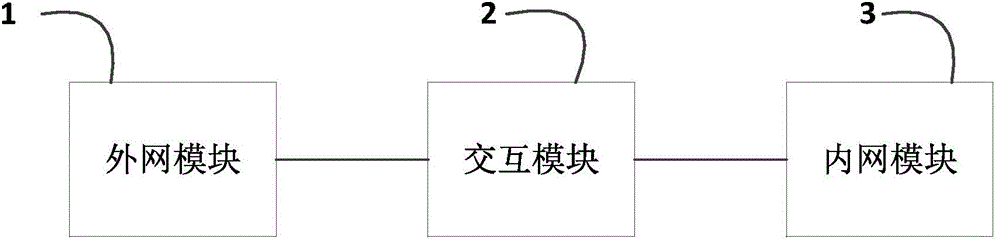
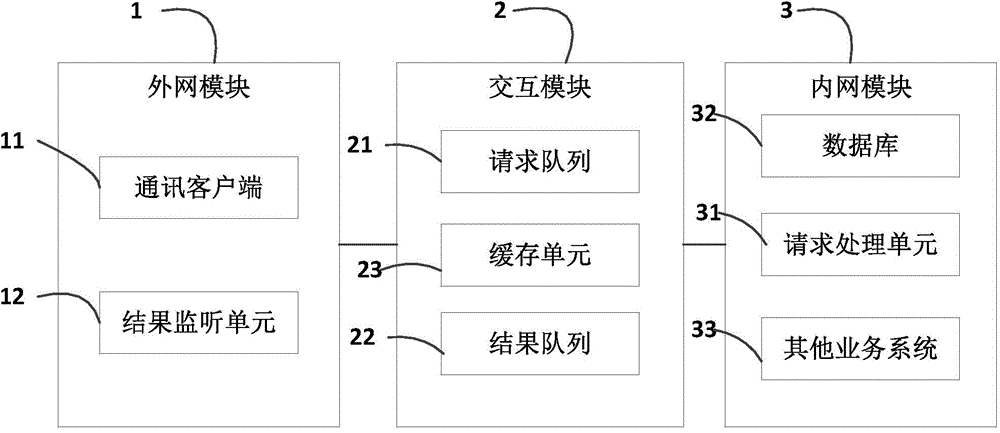
Inner/outer network interaction method and system
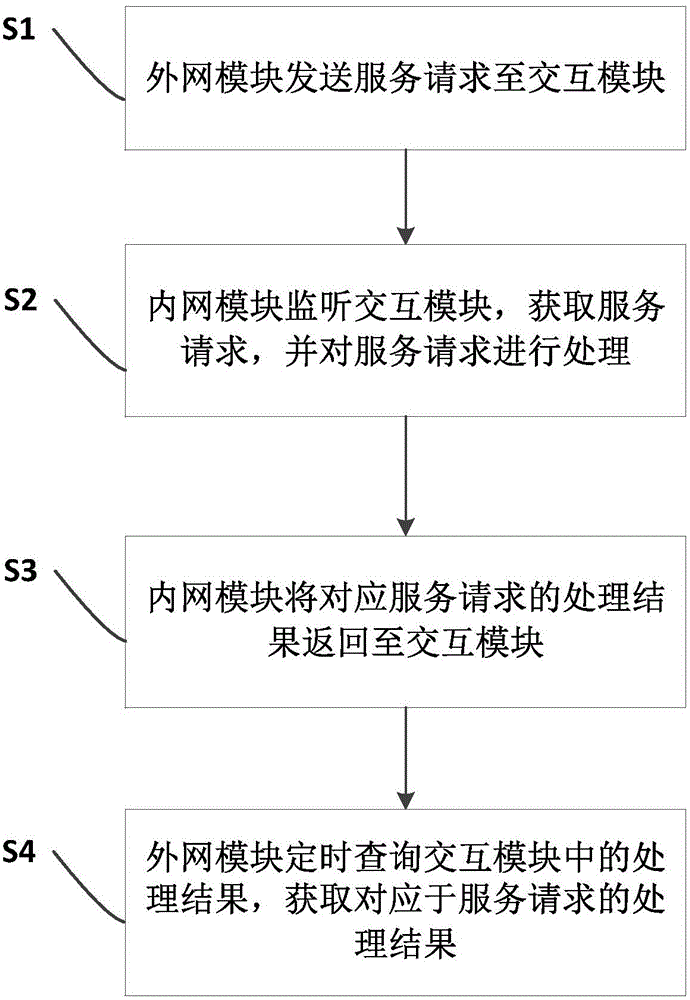
The present invention relates to the computer technology field, and provides an inner / outer network interaction method. The method comprises the steps that an outer network module sends a service request to an interaction module; an inner network module monitors the interaction module, obtains the service request and processes the service request; the inner network module returns a processing result corresponding to the service request to the interaction module; the outer network module queries the processing result in the interaction module periodically and obtains the processing result corresponding to the service request. According to the present invention, the interaction module is added for the interaction between the inner and outer networks, so that the outer network module does not need to access the inner network module directly, and the network information safety is guaranteed. In addition, the present invention also provides an inner / outer network interaction system.
Owner:LONGSHINE TECH
Oral preparation containing andrographolide and preparation method thereof
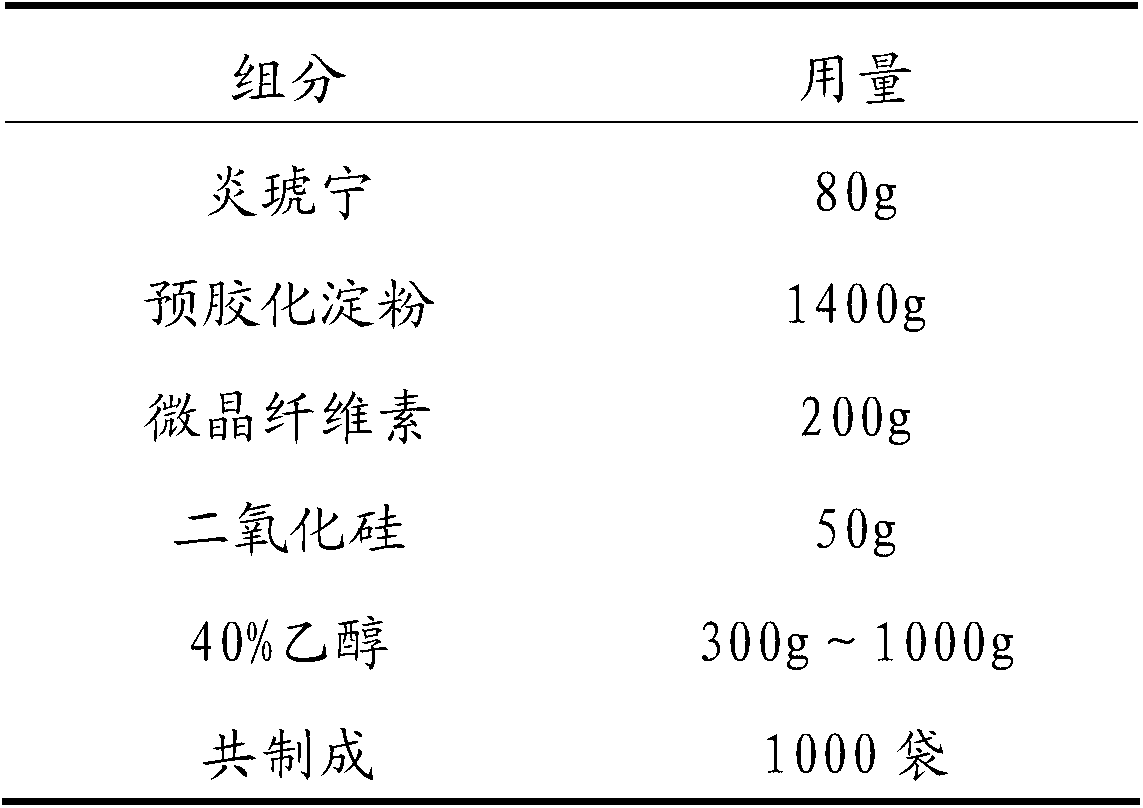
InactiveCN103070843AImprove toleranceAvoid direct accessOrganic active ingredientsAntiviralsEnteric-coated granulesSide effect
The invention relates to an oral preparation containing andrographolide and a preparation method thereof, belonging to the field of medicines. The oral preparation containing andrographolide is in dosage forms of enteric-coated granules, enteric-coated tablets, enteric-coated capsules and enteric-coated dispersible tablets which are prepared by mixing andrographolide and pharmaceutically acceptable auxiliary materials. The prepared oral preparation can reduce incidence of adverse reactions and side effects thereof and improve the medication safety while ensuring the therapeutic effect, and uses the andrographolide more widely.
Owner:司鹏 +1
Printing and dyeing sludge pyrolysis treatment device and sludge treatment method
InactiveCN102344234APollution controlAvoid direct dischargeSludge treatment by pyrolysisByproduct vaporizationCombustion chamberSludge
The invention discloses a printing and dyeing sludge pyrolysis treatment device which successively comprises a sludge chamber, a combustion chamber and a product collecting chamber from top to bottom, wherein a feed port is arranged on the sludge chamber, and a support plate with holes is arranged between the sludge chamber and the combustion chamber; the combustion chamber is connected with a combustion engine, and a pyrolysis cavity is arranged in the combustion chamber; and a dump valve is arranged between the combustion chamber product collecting chamber. The invention also discloses a printing and dyeing sludge treatment method. In the invention, by adopting the vertical arrangement from top to bottom, the automatic flowing nature of the substance is fully utilized, and the problems of high viscosity and hard feeding of printing and dyeing sludge are solved. Sludge drying, pyrolysis, pyrolysis gas recycling and control are integrated, and energy consumption is effectively reduced. Not only is the recycling of the printing and dyeing sludge realized, but also the harm to environment is greatly lowered. Therefore, the demands of industry development and environmental protection can be well adapted and satisfied.
Owner:GUANGZHOU UNIVERSITY
Application software business control method and system based on business componentization
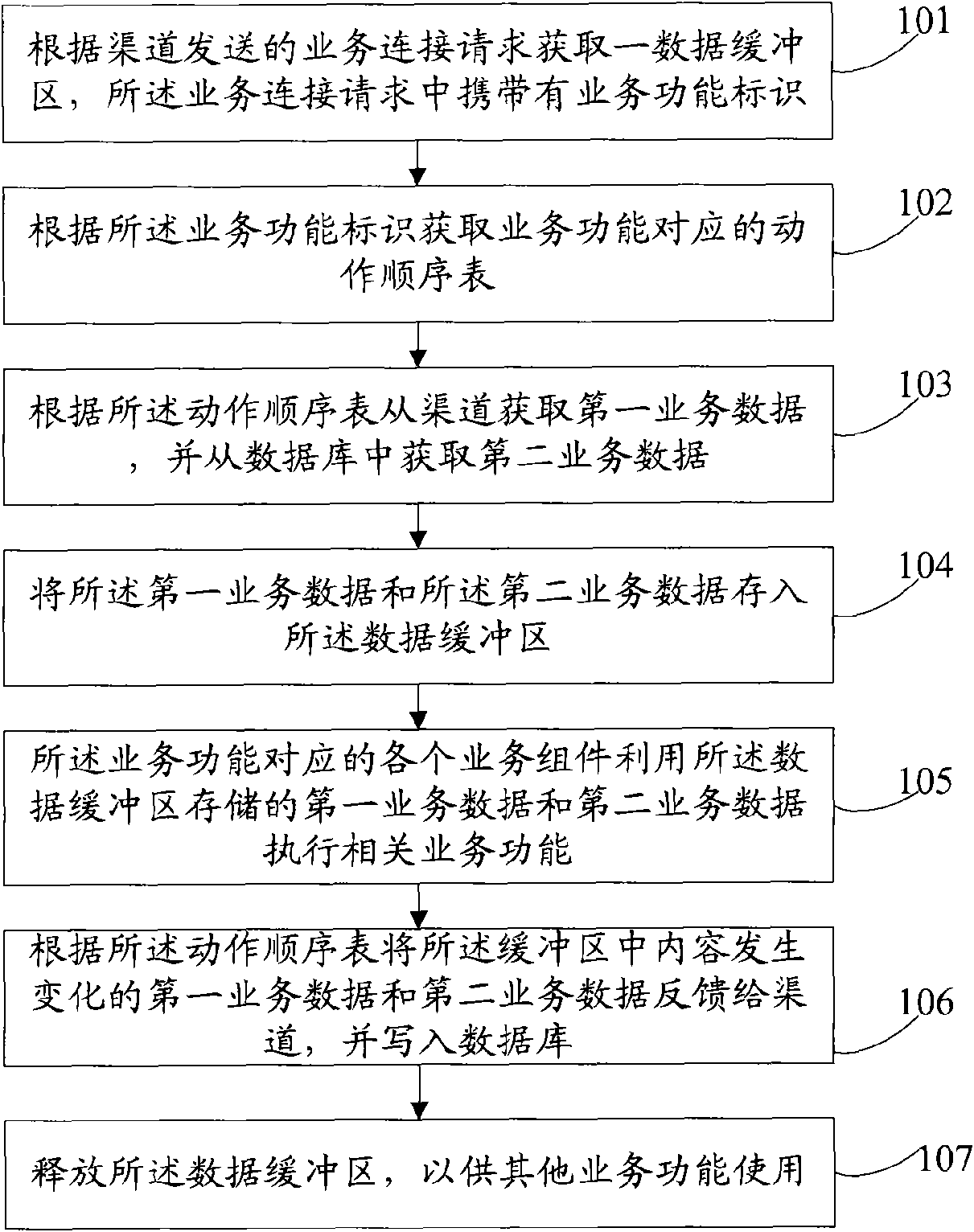
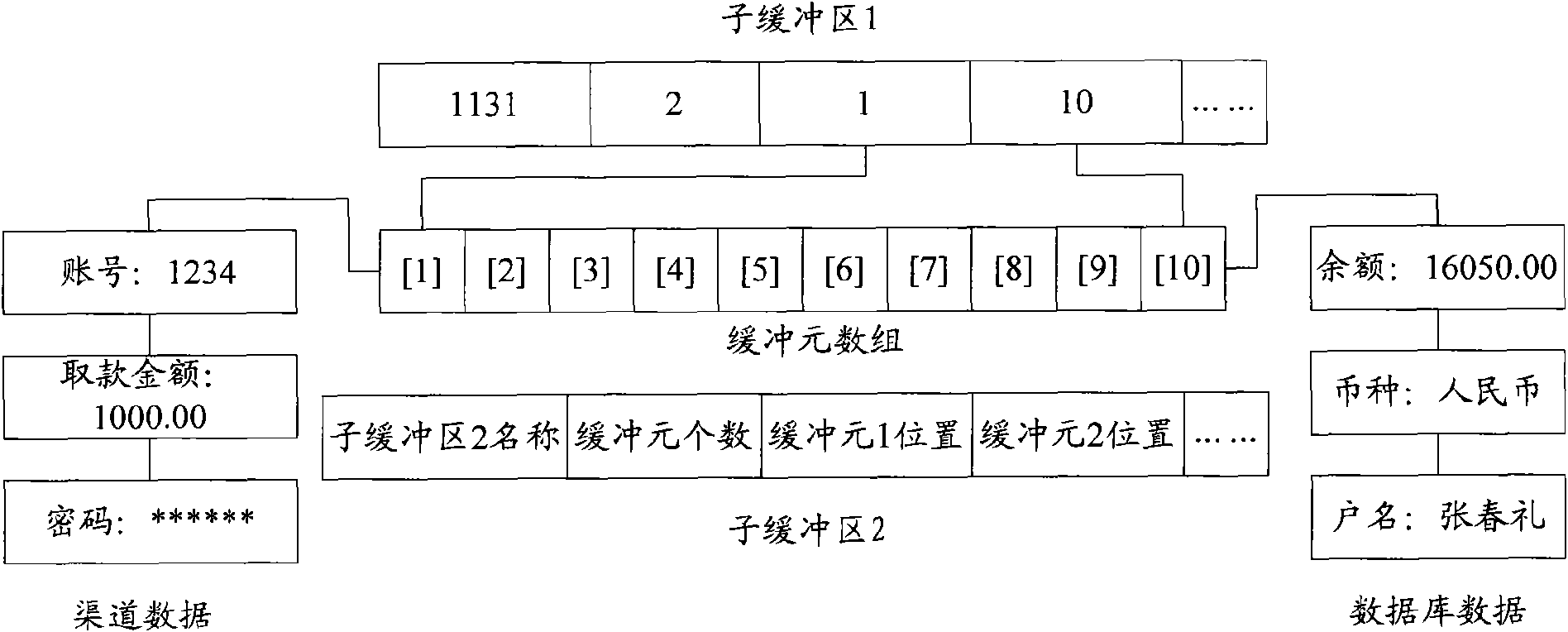
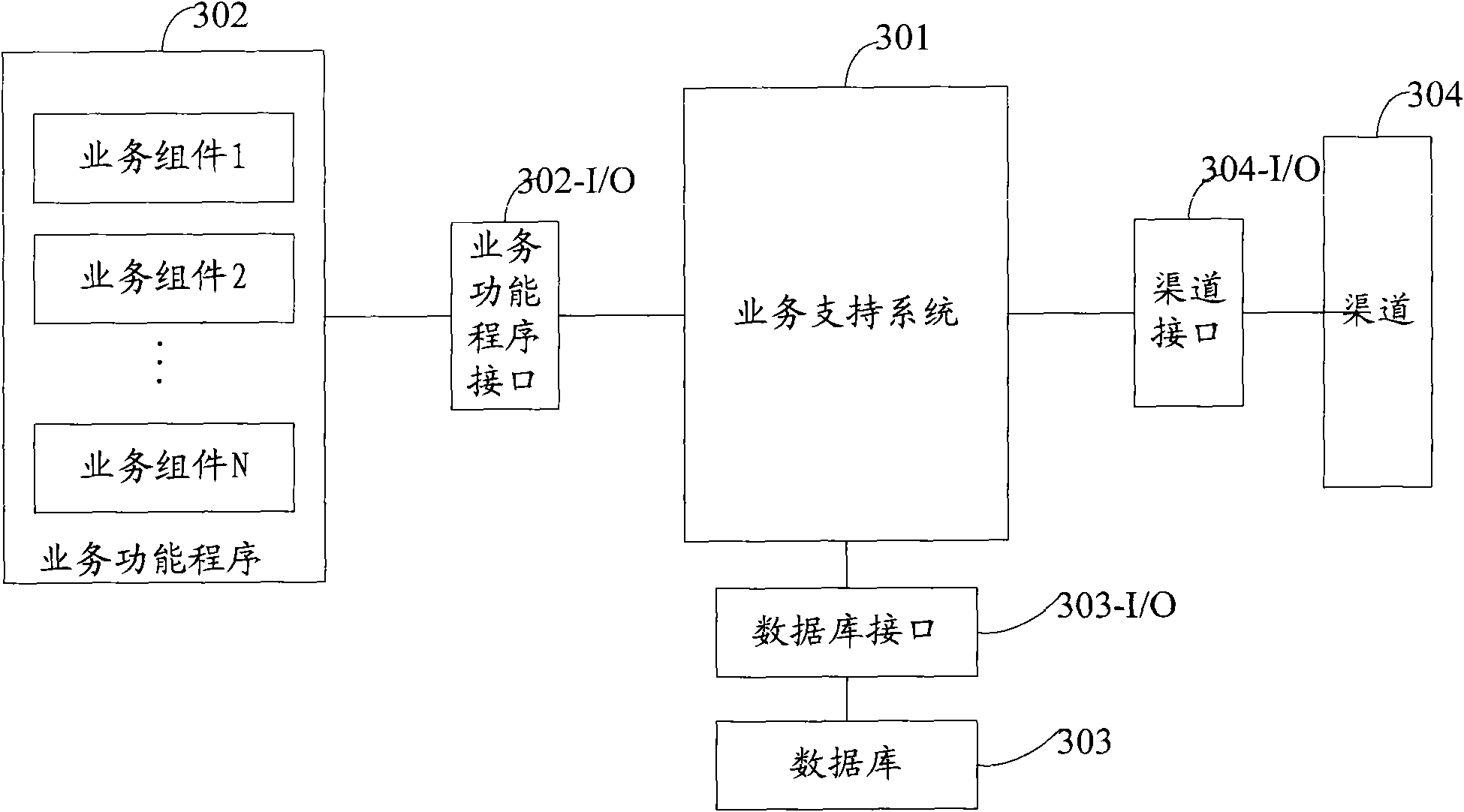
InactiveCN101625699AAvoid direct accessSolve overload and even deadlock problemsDigital data information retrievalSpecial data processing applicationsControl systemBusiness data
The embodiment of the invention discloses an application software business control method and an application software business control system based on business componentization. The method comprises the following steps: acquiring a data buffer area according to a business connecting request transmitted by a channel, wherein the business connecting request carries a business function mark; acquiring an action sequence list which corresponds to a business according to the business function mark; acquiring first business data from the channel according to the action sequence list and acquiring second business data from a database; storing the first business data and the second business data into the data buffer area; after all business components which correspond to the business execute relevant businesses, feeding the first business data and the second business data with changed contents in the data buffer area back to the channel and writing the first business data and the second business data into the database. The method fundamentally prevents the direct access of all the business components in application software on the database, thereby fundamentally solving the problem of database overloading and even deadlock in the running process of the application software.
Owner:DALIAN NEWCHOILINK SOFTWARE GROUP
Method for separating acetic acid from water by rectification of acetic acid dehydrating tower
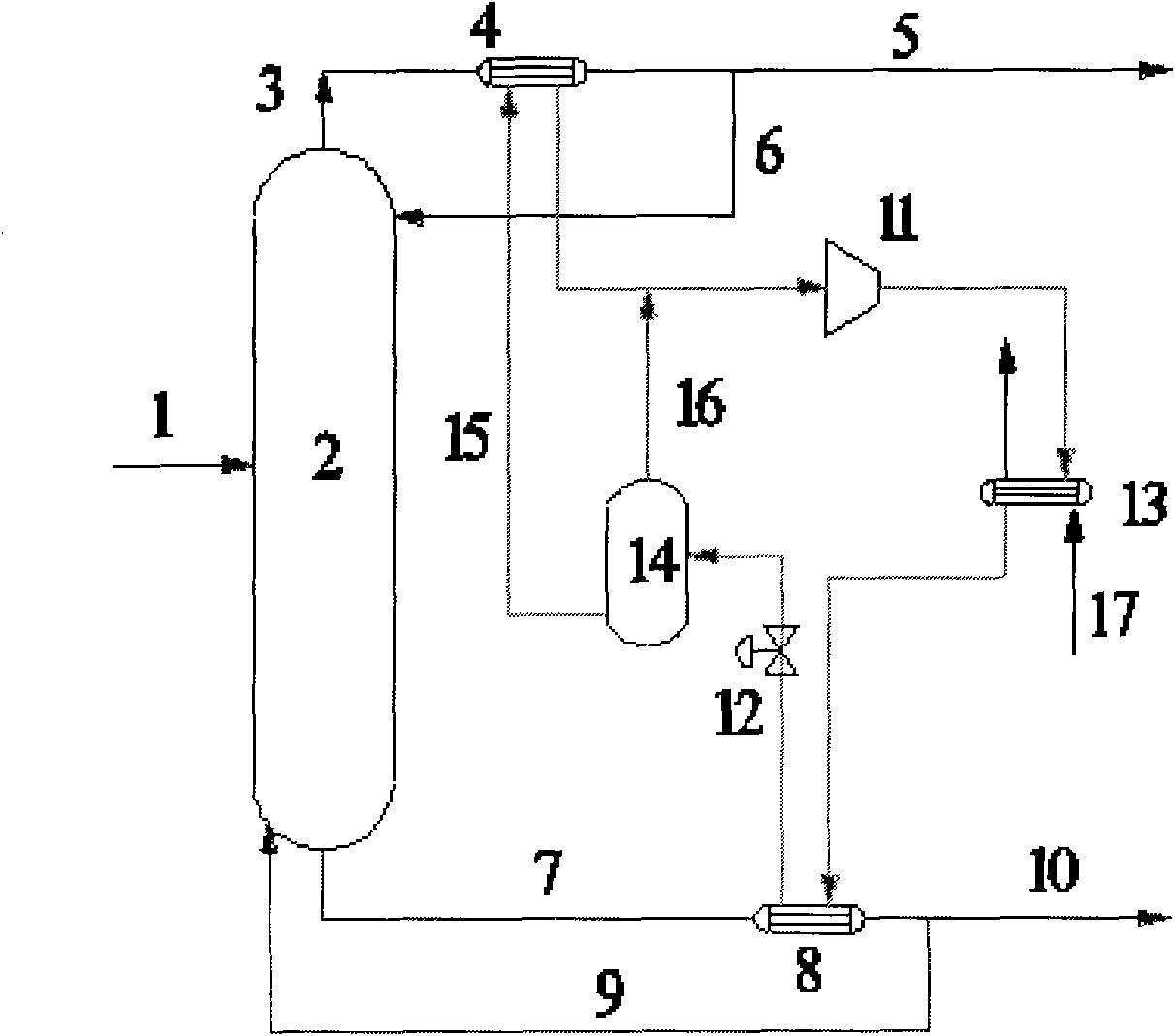
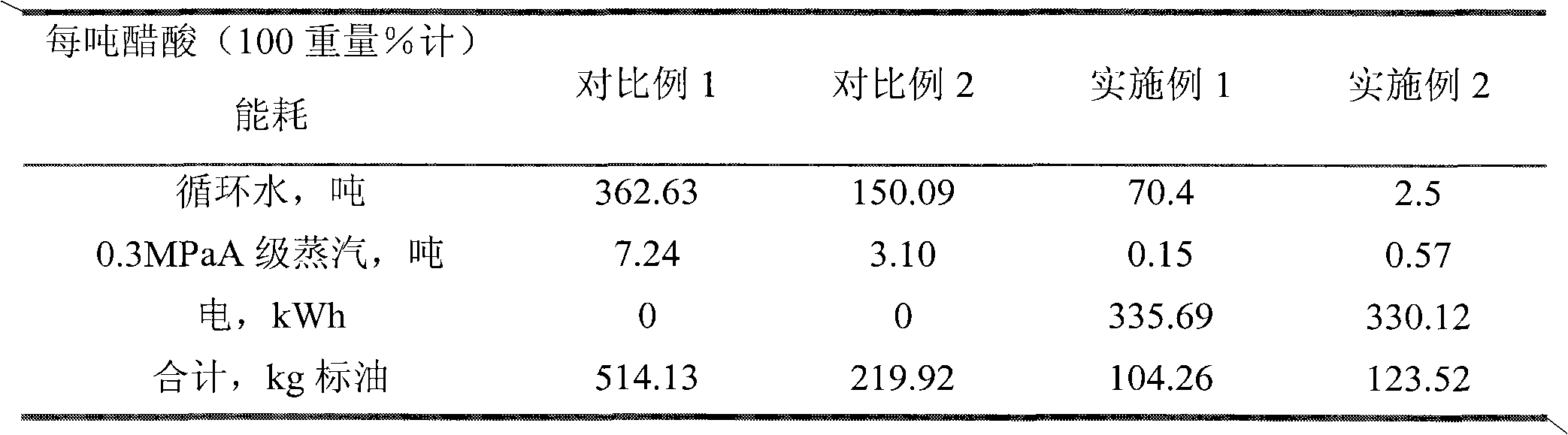
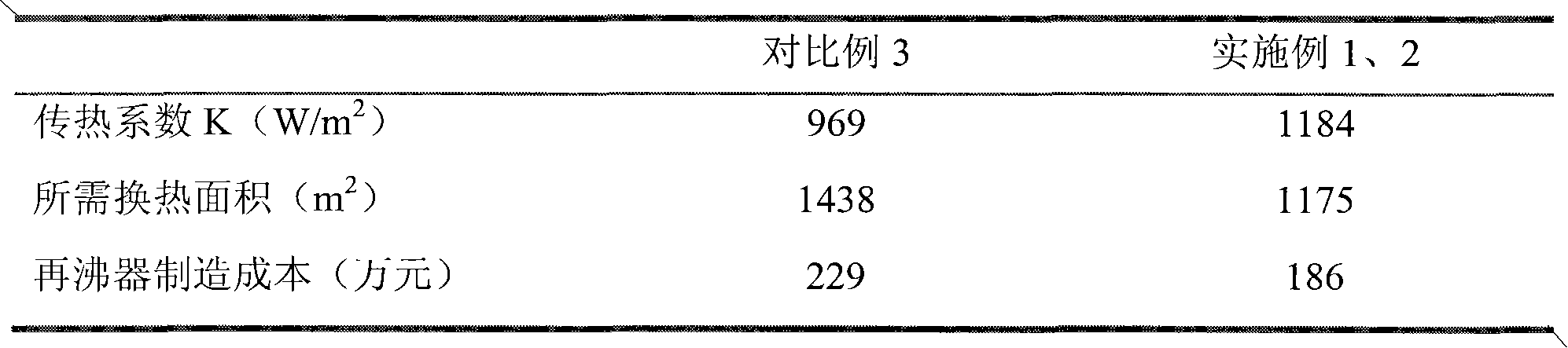
ActiveCN102451572AImprove stabilityAvoid direct accessFractional distillationCarboxylic compound separation/purificationChemistrySuperheater
The invention relates to a method for separating acetic acid from water by rectification of an acetic acid dehydrating tower, mainly solving the problems of high energy consumption, high equipment manufacture cost and high operation cost in a process of dehydrating acetic acid in the prior art. The method comprises the steps of: carrying out azeotropic distillation by adopting the acetic acid dehydrating tower for dehydrating, adopting water or cyclohexane in a heat pump circulation as a heat exchange medium, absorbing heat released by condensation of top discharged materials of the acetic acid dehydrating tower through a heat exchange medium in a closed heat pump process, raising the temperature after the heat exchange medium absorbs the heat of the top discharged materials and then compressed, desuperheating high-temperature overheat steam by a desuperheating device to form saturated steam, introducing into a kettle reboiler and exchanging heat with bottom discharged materials; throttling and decompressing the steam subjected to kettle heat exchange and then entering into a gas and liquid separation tank, enabling the separated liquid phase to a tower top condenser for exchanging heat, mixing the separated gas phase with gas at an outlet of the tower top condenser together to enter into a compressor for exchanging heat with a kettle again. According to the technical scheme, the problem is better solved, thus the invention can be applied to industrial production of separating the acetic acid from the water.
Owner:CHINA PETROLEUM & CHEM CORP +1
Window capable of ventilating and insulating noise
InactiveCN101054880AImprove qualityAvoid direct accessVentilation arrangementNoise insulation doors/windowsPush and pullSash window
A window which can ventilate and separate noise comprises a window frame and a window sash in the window frame. The window sash of the invention is a combining window sash composed of a layer of single-sash pushing and pulling window and a layer of double-sashes folding window, wherein, the single-sash pushing and pulling window is mounted in one side of the window frame by hinges, and can only shelter half of the window frame when closing the window; the double-sashes folding window is mounted in another side of the window frame by hinges, and can completely unfold and shelter wholly the window frame when closing the window. Two ends of the single-sash pushing and pulling window and the double-sashes folding window are respectively mounted with filtering nets. The invention can still have better ventilation condition, meanwhile reducing the noise without mechanical ventilation device. In addition, the silencing window can save space of mounting mechanical ventilation device, and the sound absorption material or the filtering net has the action of filtrating air, and the air indoor can be purified. So the initial investment and the operating economical efficiency are better, the installation and maintenance are more convenient.
Owner:CHONGQING UNIV
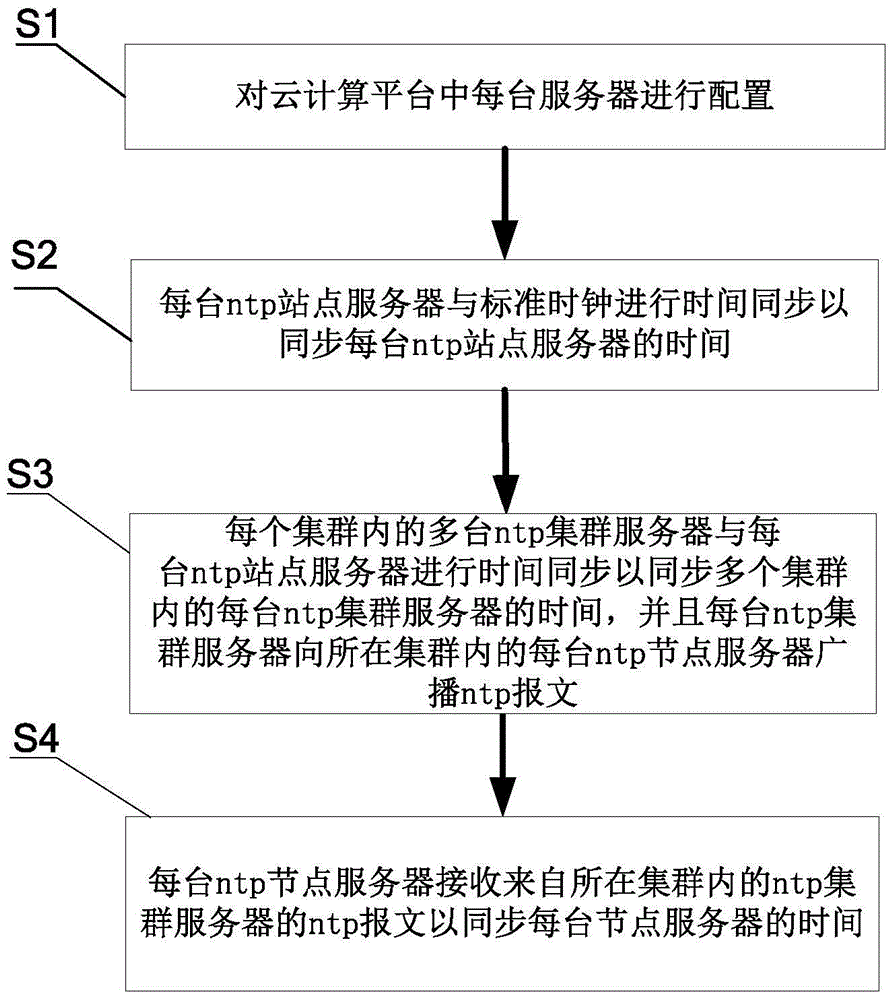
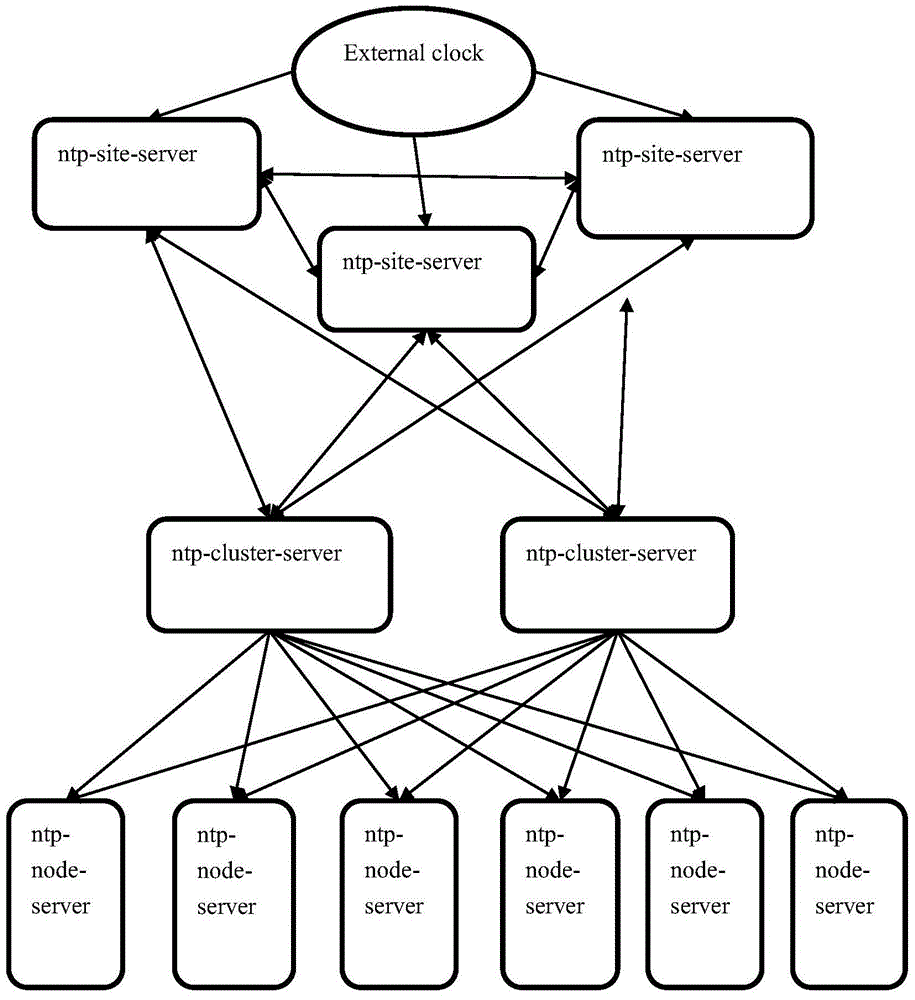
Cloud computing platform and server time synchronization method thereof
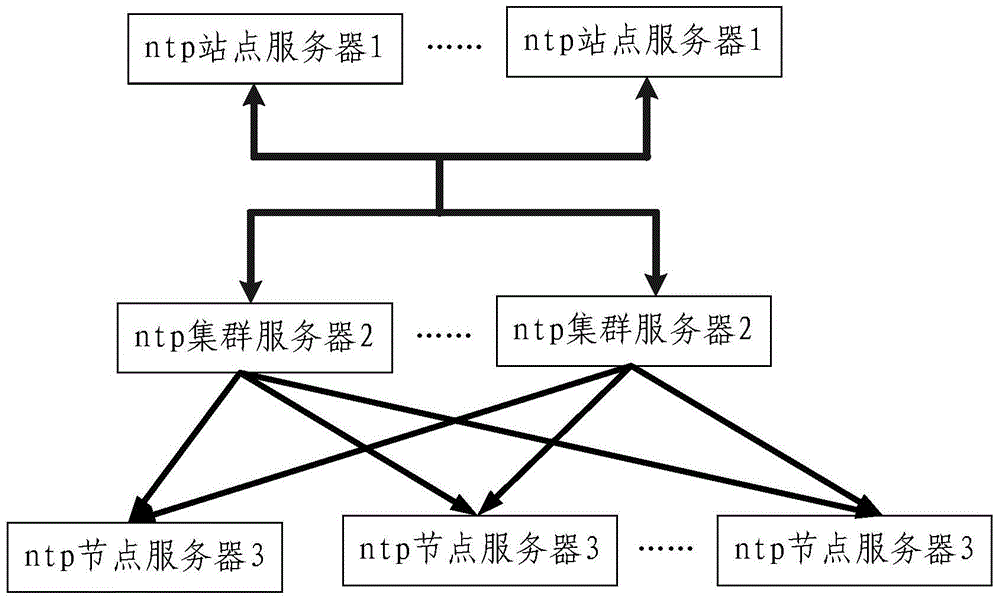
InactiveCN103916231AImprove time synchronization efficiencyAvoid direct accessSynchronising arrangementClock timeDistributed computing
The invention relates to a server time synchronization method of a cloud computing platform and the cloud computing platform. The method comprises the steps that all servers in the cloud computing platform are configured; time synchronization is conducted on all ntp site servers and the standard clock time to synchronize the time of all the ntp site servers; time synchronization is conducted on all ntp cluster servers in all clusters and all the ntp site servers to synchronize the time of all the ntp cluster servers in multiple clusters, all the ntp cluster servers broadcast ntp messages to all ntp node servers in the corresponding clusters of all the ntp cluster servers , all the ntp node servers receive the ntp messages of the ntp cluster servers in the corresponding clusters to synchronize the time of all the node servers. By means of the cloud computing platform and the server time synchronization method thereof, ntp server multi-layer networking is achieved, and time synchronization efficiency of the whole cluster is improved.
Owner:OPZOON TECH
Unlocking device for concealing keyhole of lock
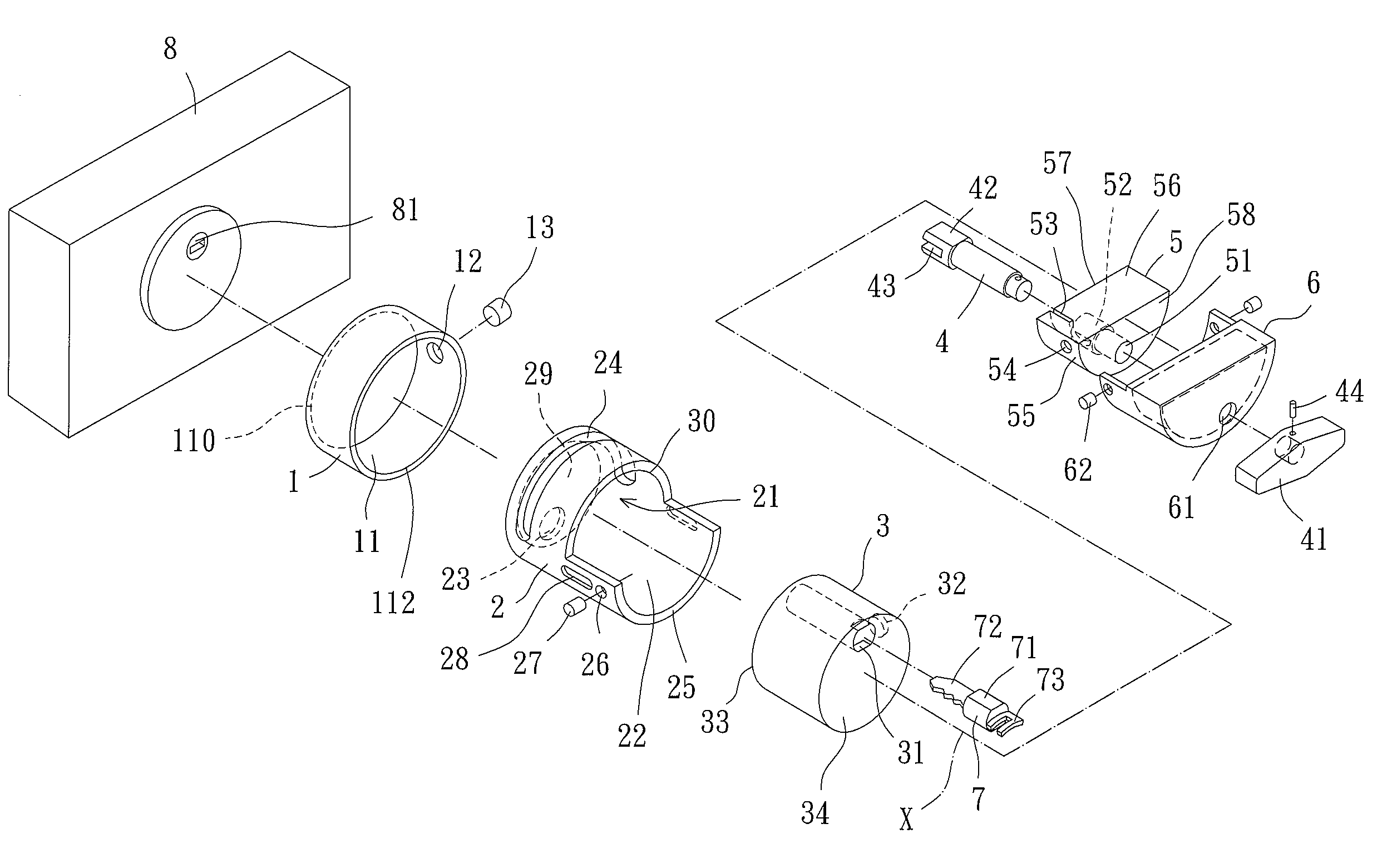
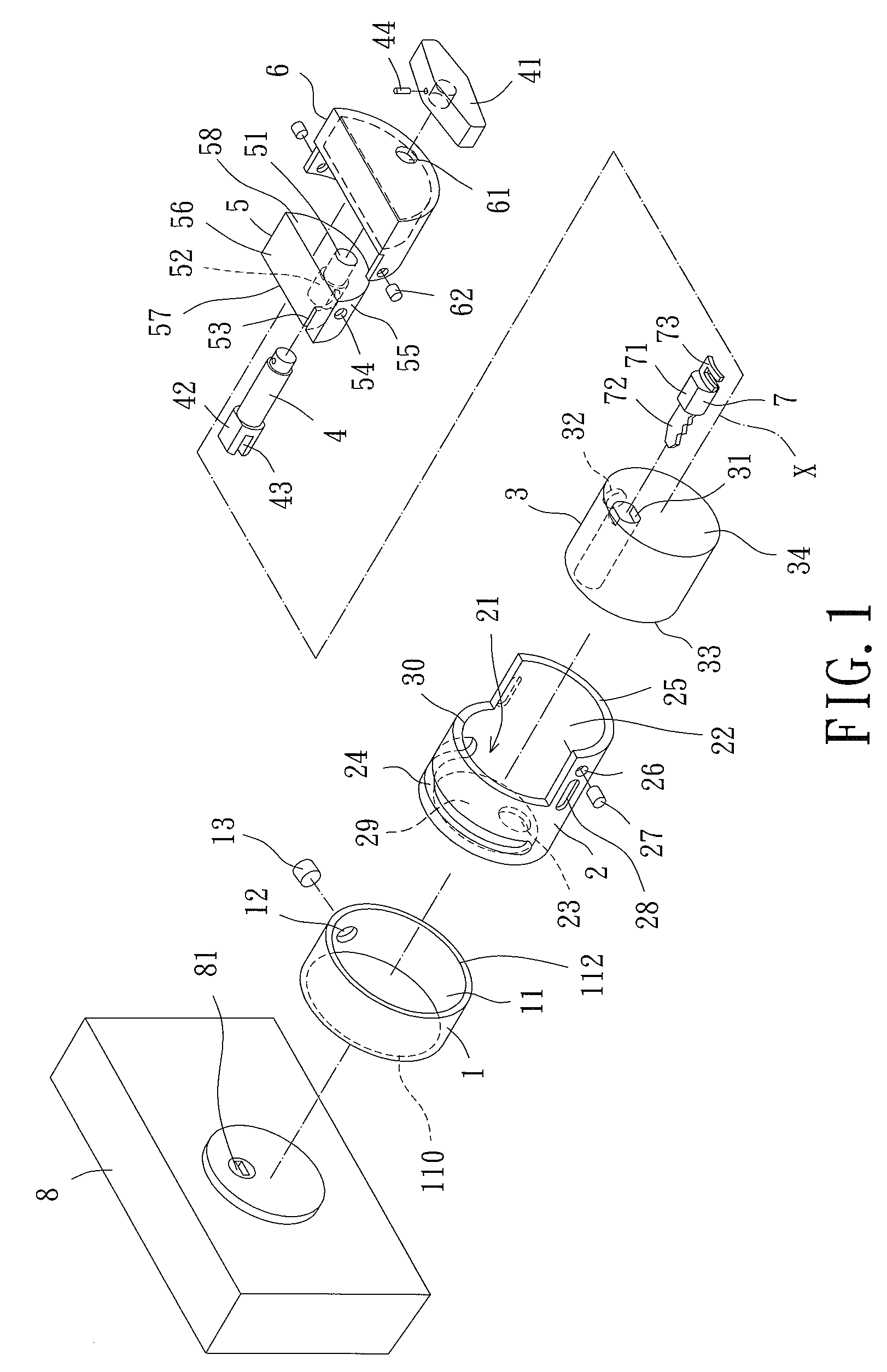
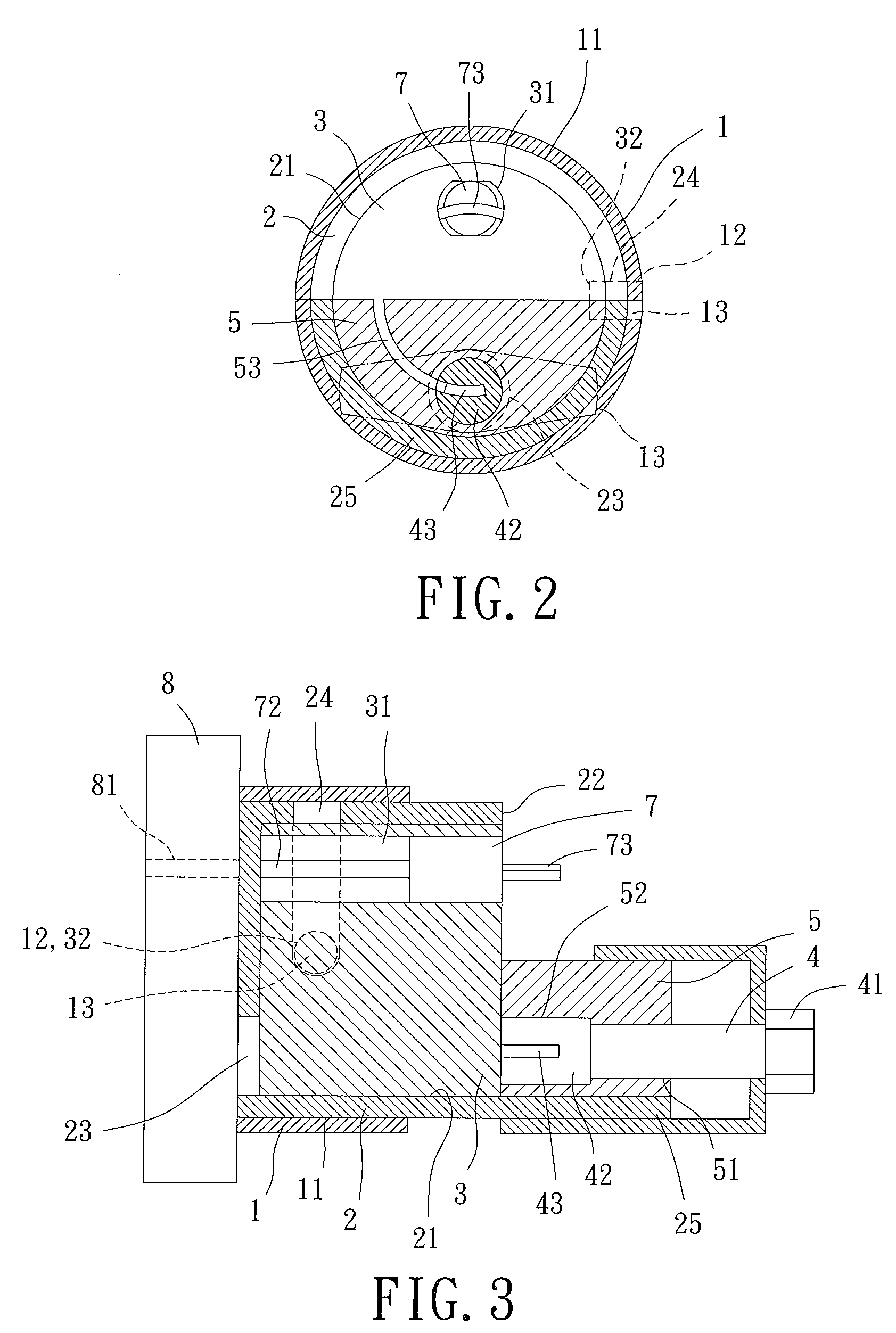
InactiveUS7866194B2Avoid direct accessDirect accessKeyhole guardsKeysEngineeringMechanical engineering
An unlocking device includes a casing mounted to a side of a lock having a keyhole. A movable body is rotatably received in the casing about an axis. The movable body has a closed end having a hole. A key receiving seat is received in the movable body and has a key receiving hole. The keyhole is normally blocked by the closed end of the movable body. The movable body can be rotated to align the hole with the keyhole and the key receiving hole. A block is fixed to the movable body and includes a through-hole extending along the axis. A manually rotatable linking rod extends through the through-hole and has an engaging portion for coupling a key received in the key receiving hole. The key can be moved into the keyhole by moving the linking rod along the axis and can be rotated for locking or unlocking operation.
Owner:LIU SHIH TE
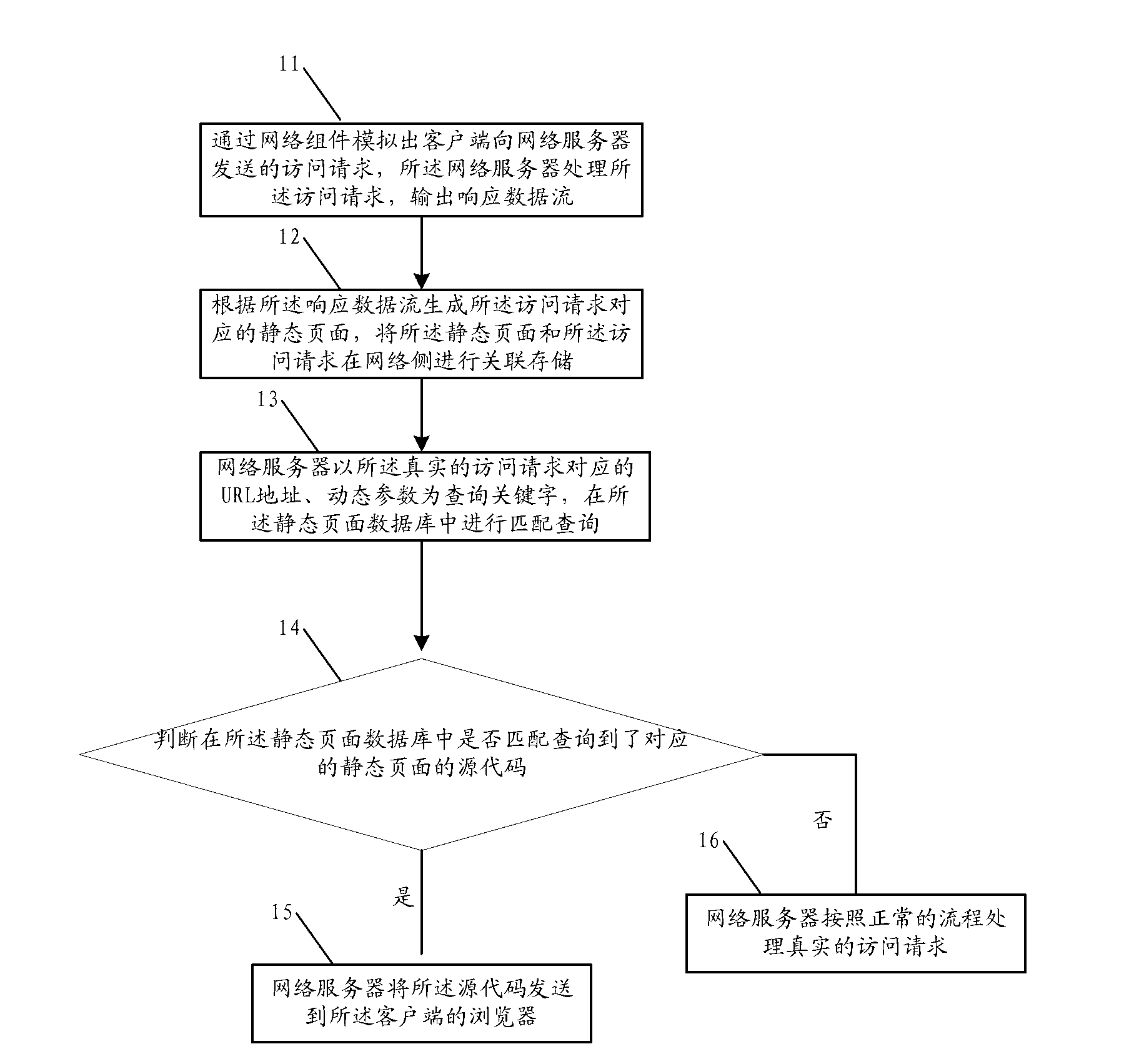
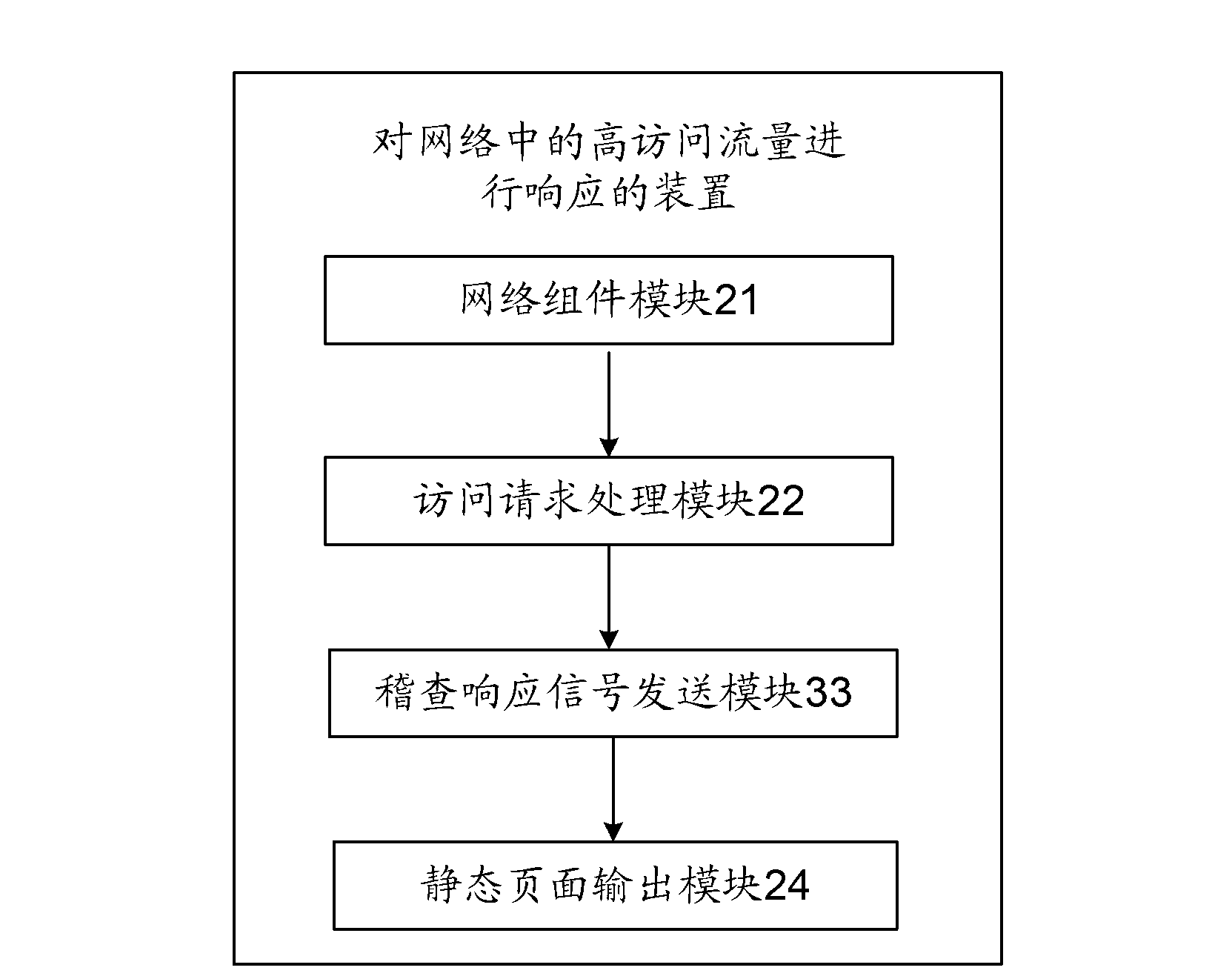
Method and device for responding to high visiting flow in network
InactiveCN103237003AQuick responseAvoid direct accessTransmissionSpecial data processing applicationsTraffic capacityData stream
An embodiment of the invention provides a method and a device for responding to high visiting flow in a network. The method mainly includes imitating access requests sent by a client side to a network server through the website, processing the access requests by the network server and outputting responding data flow, generating static website pages corresponding to the access requests according to the responding data flow, performing relative storage at a network side according to the static website pages and the access requests, and returning the static website pages to the client side after the network server receives the real access requests of the network server sent by the client side. The responding speed between the network server and the client side is greatly increased, the condition that a large number of users get access to the network server directly for non-trade information or private information is avoided, pressure on the server is greatly reduced and system performance is improved.
Owner:北京印天网真科技有限公司
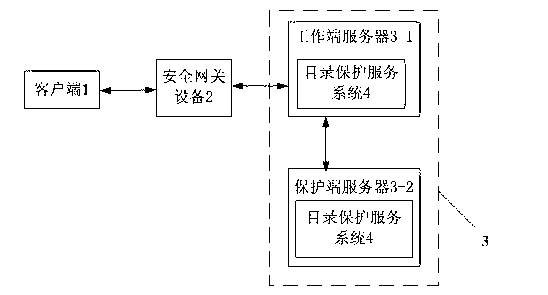
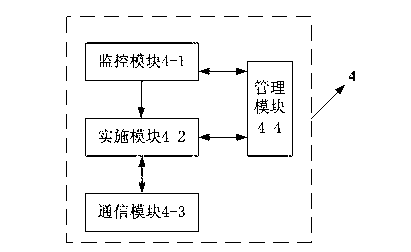
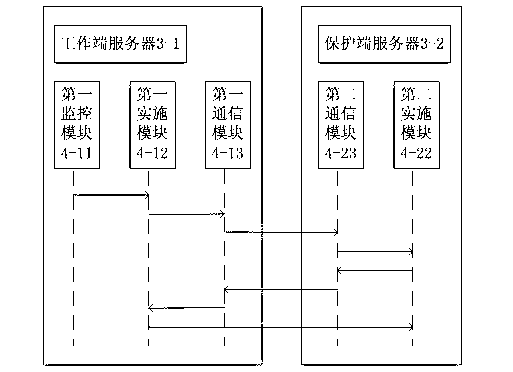
Webpage tamper-proofing device and method based on access control and directory protection
InactiveCN103236932APrevent tamperingTampering will notUser identity/authority verificationTamper resistanceMedia access control
The invention provides a webpage tamper-proofing device and a webpage tamper-proofing method based on access control and directory protection. The webpage tamper-proofing device comprises a client end and a service end, wherein security gateway equipment is arranged between the client end and the service end, the service end comprises a work end server and a protecting end server, the work end server and the protecting end server are connected in an interactive manner, the work end server is communicated with the client end, and directory protection service systems are respectively arranged inside the work end server and the protecting end server. The webpage tamper-proofing device and the webpage tamper-proofing method comprise two parts that 1, the access control is realized through the security gateway equipment, an internal website and an external website are separated, the access authority of users is determined, and the users are prevented from illegally accessing and modifying application system and data; and 2, the directory protection function is realized through the directory protection service systems, the real-time deletion and recovery is realized, and the real reliability of files is ensured.
Owner:ANHUI HIGHGUARD NETWORKS TECH
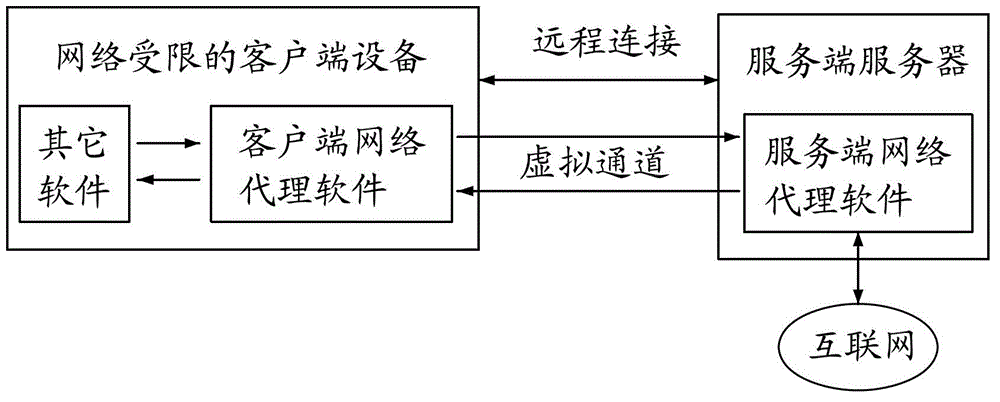
Network proxy method based on virtual channel in virtual desktop infrastructure (VDI) environment
The invention provides a network proxy method based on a virtual channel in a virtual desktop infrastructure (VDI) environment. The method comprises the following steps of: 1, establishing server network proxy software and client network proxy software on a server and a client respectively, wherein the server communicates with the client through the virtual channel; 2, transmitting network access request data of software on the client to the Internet through the client network proxy software, the virtual channel and the server network proxy software; and 3, transmitting a response from the Internet to the software on the client through the server network proxy software, the virtual channel and the client network proxy software, and completing a proxy process. By the method, the phenomenon that the client or the server cannot be directly accessed caused by hiding behind a router or a firewall is avoided, and the phenomenon that the server cannot be directly accessed because the server is a cluster server is avoided simultaneously.
Owner:FUJIAN CENTM INFORMATION
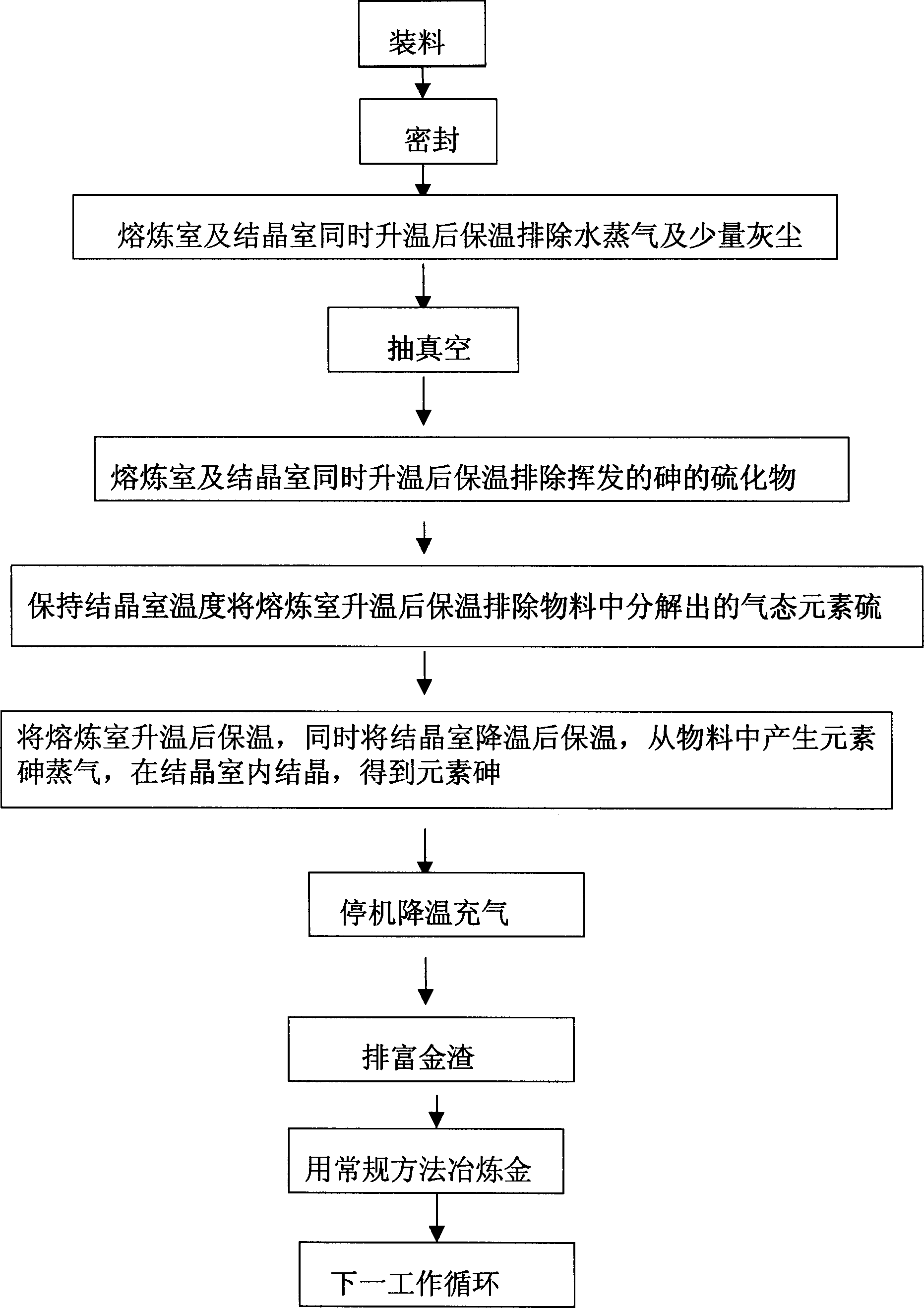
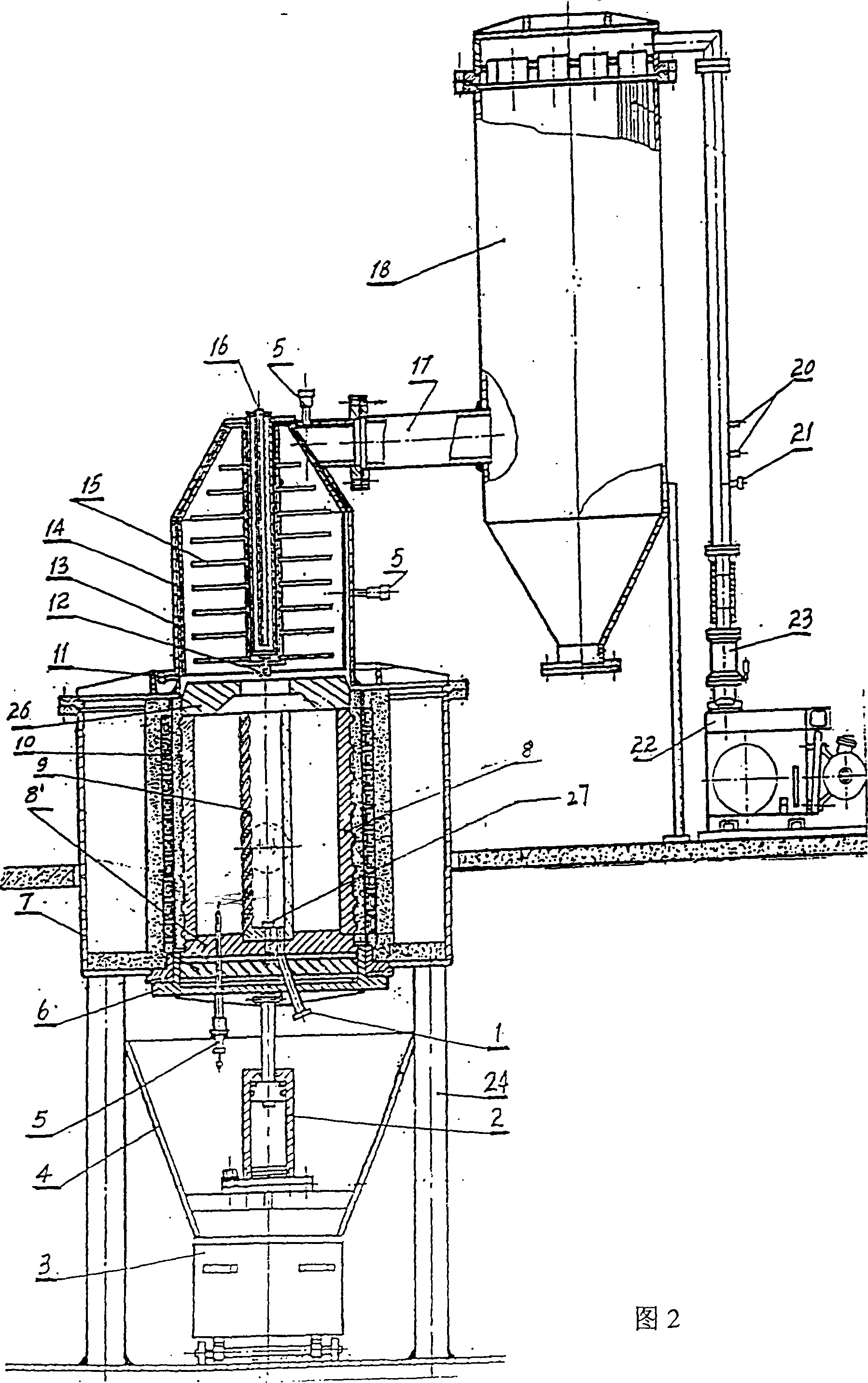
Method and system for extracting gold from arsenic contained headings
InactiveCN1490418ANo volatilization lossSolve the problem of low recovery rateGaseous elementVacuum pumping
A process for extracting gold from the As-contained gold ore concentrate includes such steps as heating the smelting chamber to 100-300 deg.C, holding the temp for removing the water vapour and dust, heating the smelting chamber and crystallizing chamber to 300-500 deg.C, holding the temp for removing the volatile sulfide of As, heating the smelting chamber to 500-600 deg.C while holding the temp of crystallizing temp for removing the gas-phase sulfur, heating smelting chamber to 600-760 deg.C while cooling crystallizing chamber to 270-370 deg.C to obtain As, cooling while aerating to obtain the gold-enriched dregs, and conventional extracting of pure gold. Its equipment is also disclosed.
Owner:BEIJING GOLDTECH
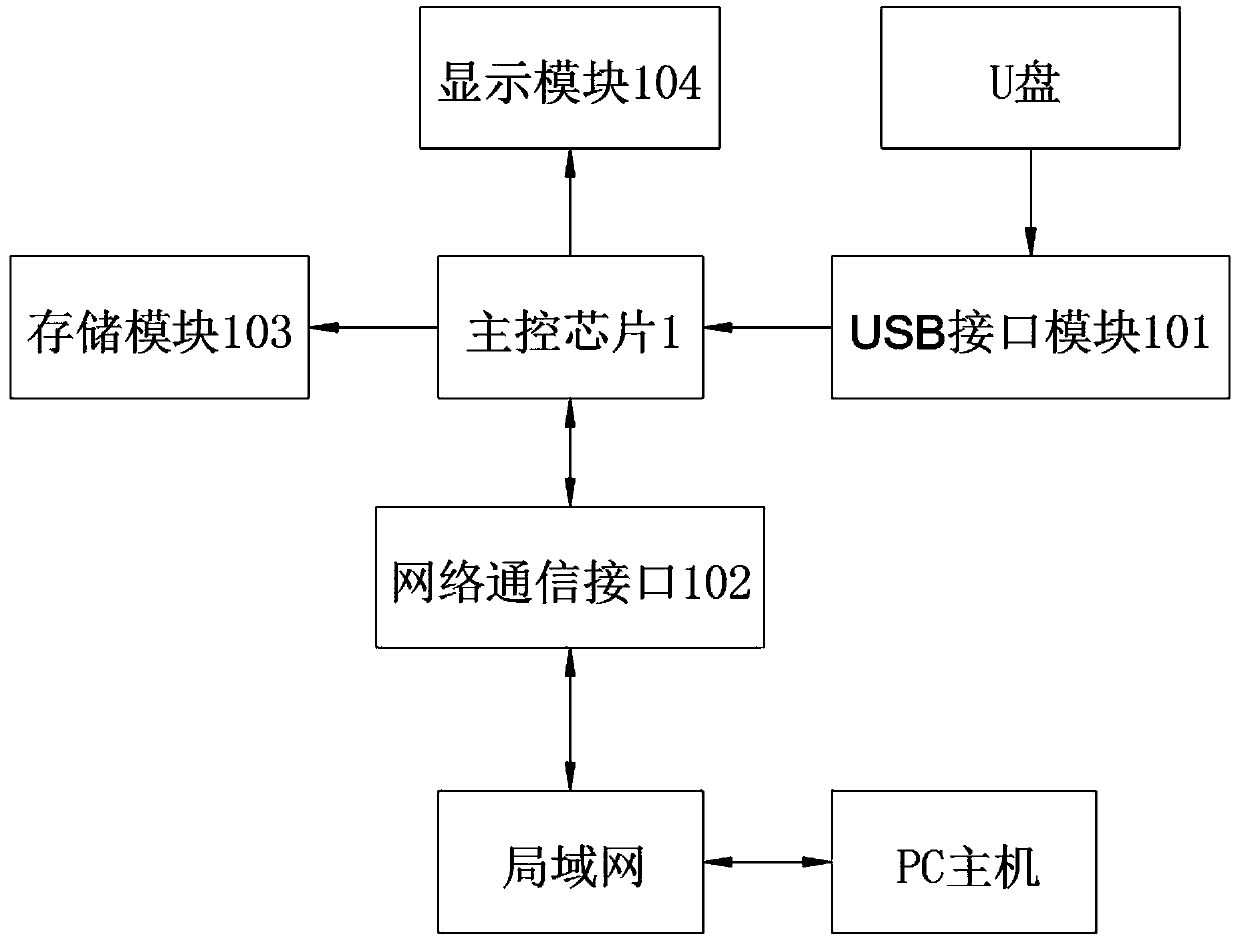
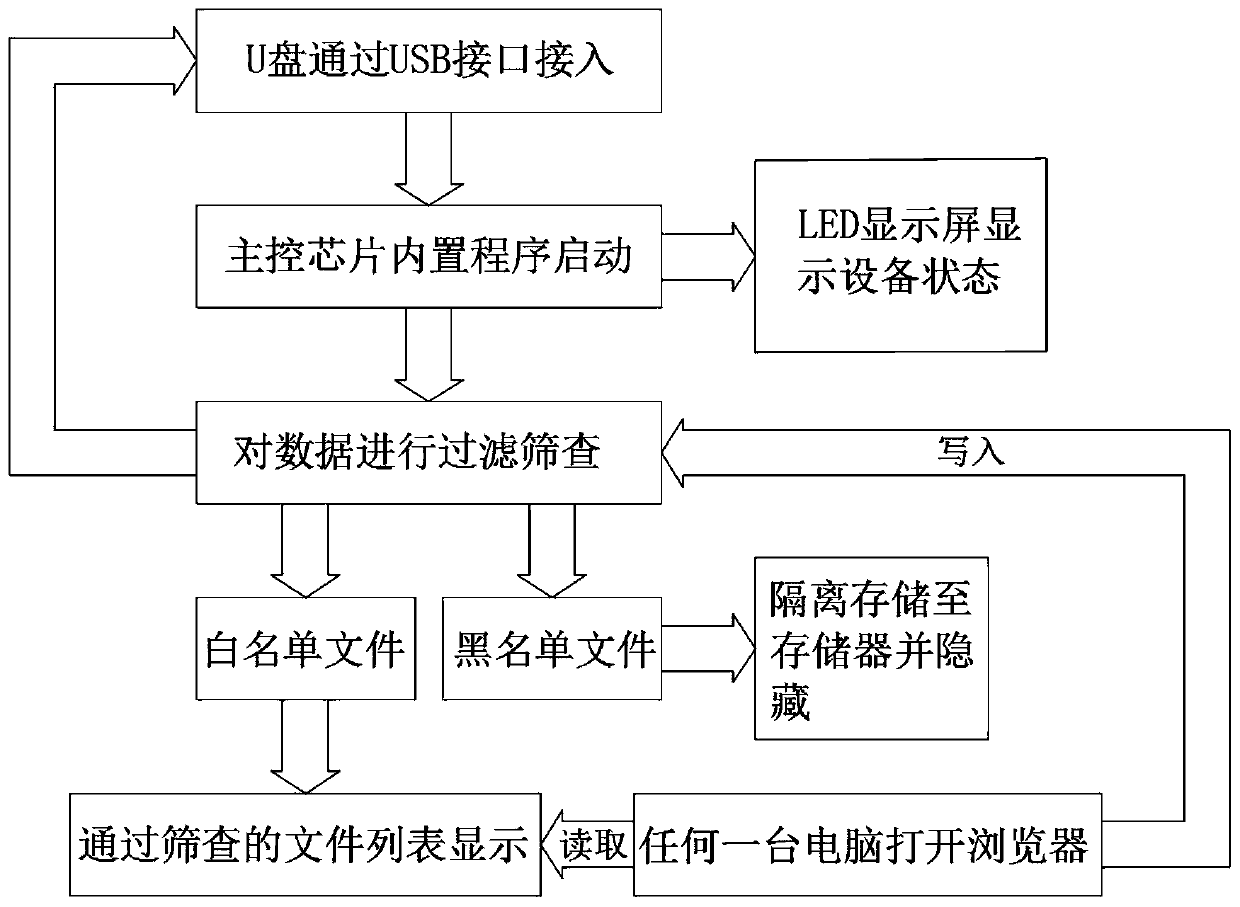
USB flash disk virus isolator and working method thereof
InactiveCN110688657AHigh self-securitySelf-safety guaranteeInternal/peripheral component protectionPlatform integrity maintainanceNetworking protocolData access
The invention relates to the technical field of USB flash disk virus isolation, in particular to a USB flash disk virus isolator and a working method thereof.The USB flash disk virus isolator comprises a main control chip used for strictly controlling and checking data access; the storage module is used for caching the isolated virus files; the network interface module is accessed to a local areanetwork by adopting an international general network protocol; the USB interface module is used for being externally connected with a USB flash disk; the display module is used for visually displayingthe equipment operation state; the storage module, the network interface module, the USB interface module and the display module are respectively connected with the main control chip through corresponding lines; uSB flash disk data is filtered and screened through a built-in system program of the main control chip; the system program automatically detects and identifies the safety file of the white list and the virus file of the black list, the safety content on the white list is allowed to be connected with the PC through the local area network to be read and written, and once the system program scans the content on the black list, the corresponding content is immediately isolated and hidden, so that virus spreading caused by misoperation of a client is avoided.
Owner:福州浩恒影音工程有限公司
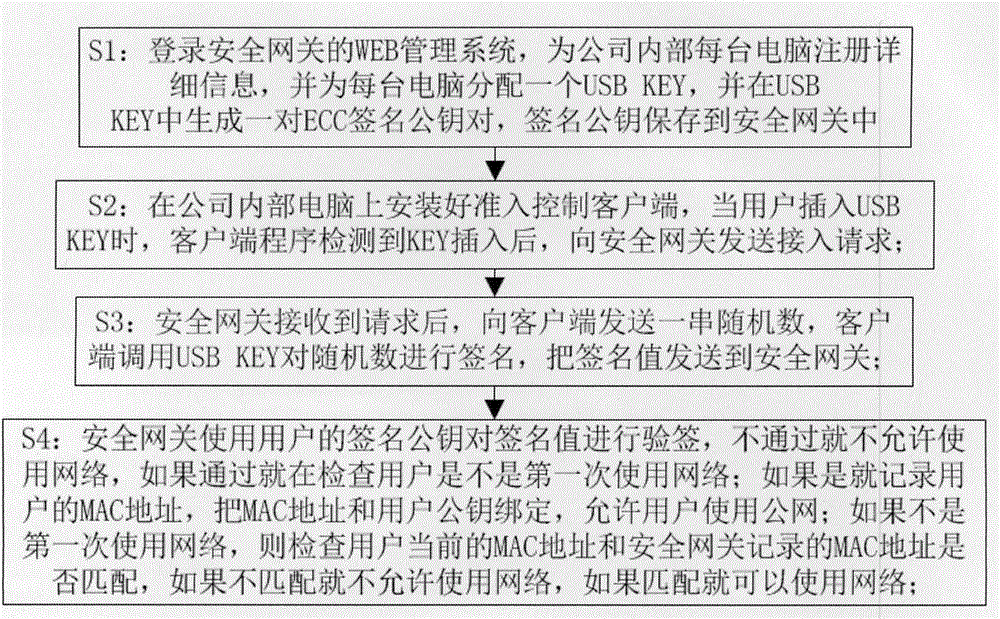
Control method for network access admittance
InactiveCN104468490AAvoid accessAvoid direct accessSecuring communicationWide area networksAccess methodPublic network
The invention discloses a control method for network access admittance. The control method for network access admittance is characterized in that a security gateway is arranged to conduct information preset on an internal computer in a company, meanwhile, strict information authentication is conducted on a foreign computer, and then the secondary authentication is conducted on a user who passes initial authentication. According to the control method for network access admittance, a safety network access method is achieved, the foreign computer is prevented from having access to an LAN and directly using a public network without permissions or copying the resource of the company without permissions, the computer in the company can also be prevented from directly visiting unauthentic computers, and the computer in the company is prevented from being infected by viruses.
Owner:WUXI CINSEC INFORMATION TECH
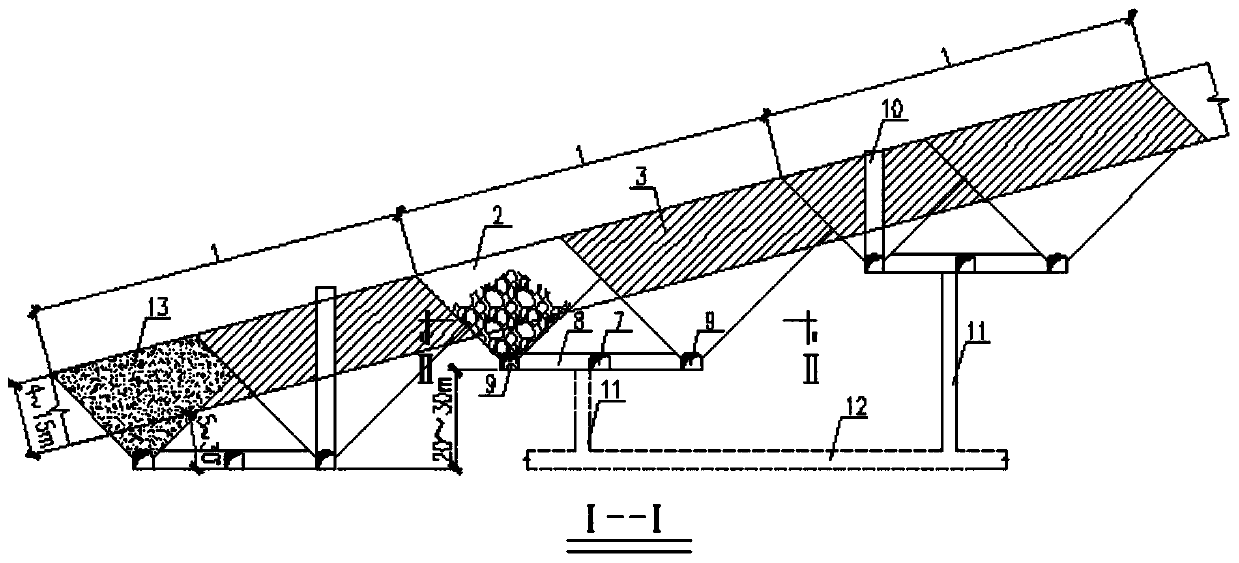
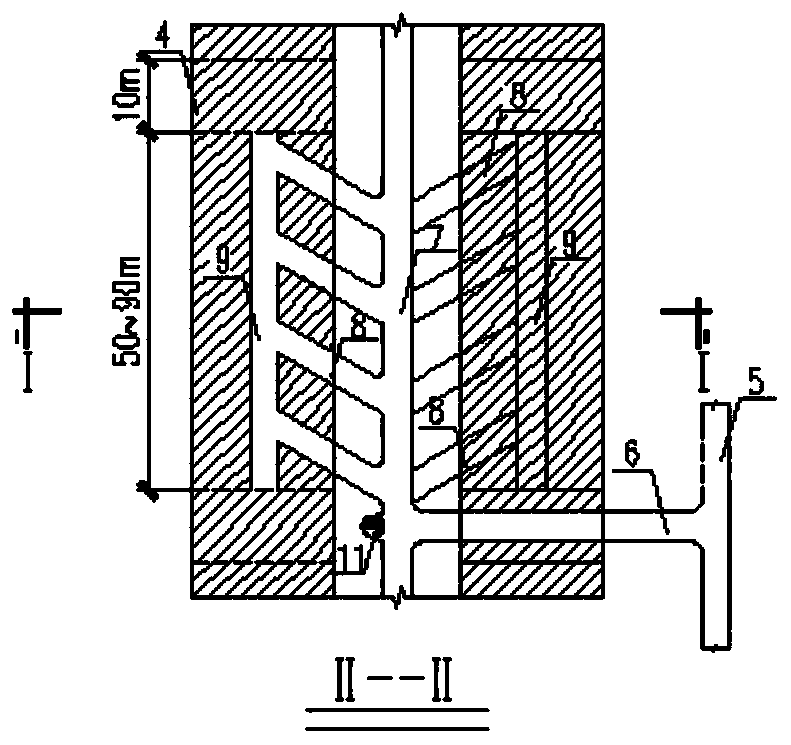
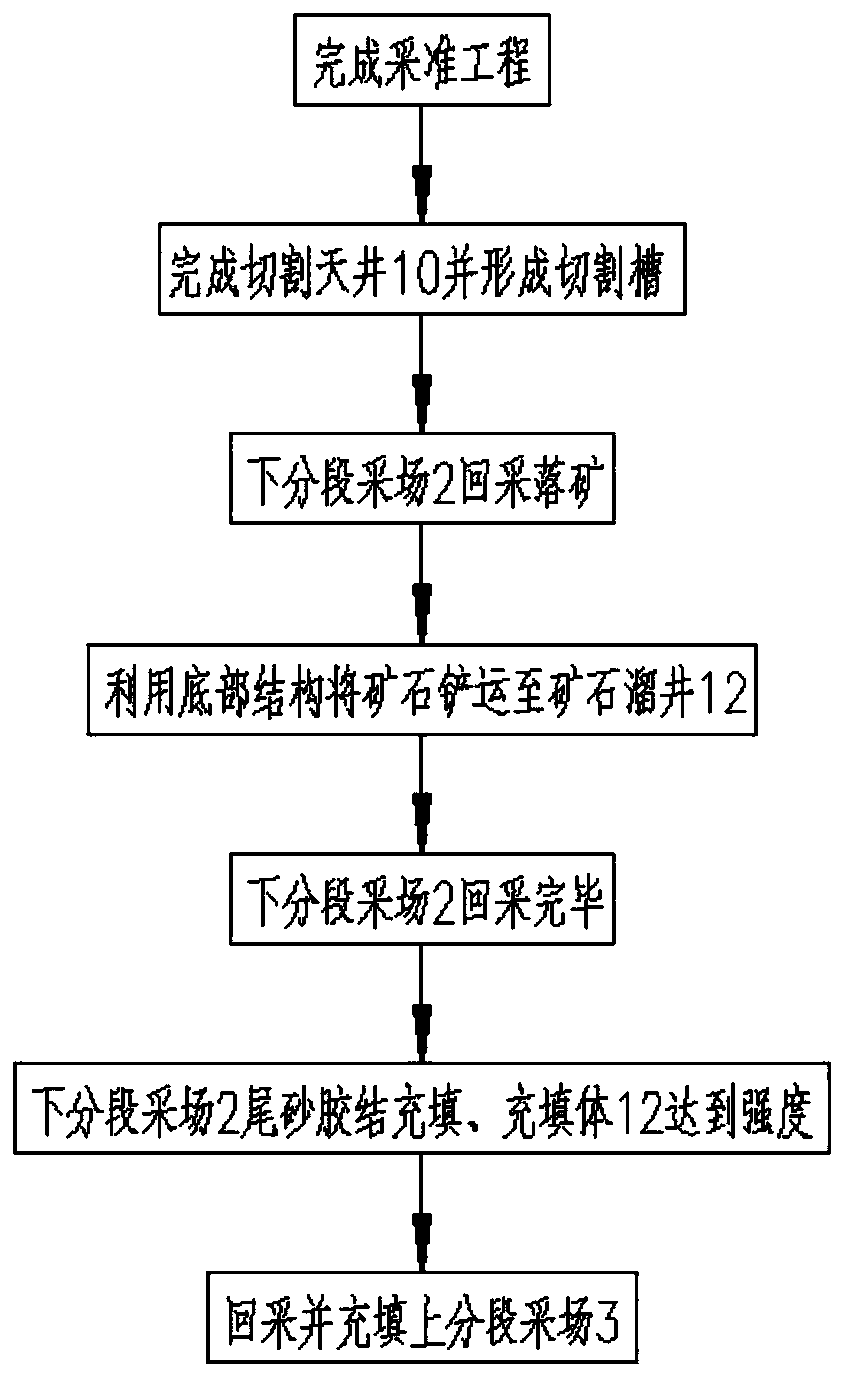
Gentle dip medium-thick ore body safety and low-cost combined segmented mining method
ActiveCN110359914AAvoid direct accessGuarantee job securityUnderground miningSurface miningEngineeringYard
The invention discloses a gentle dip medium-thick ore body safety and low-cost combined segmented mining method. Lower segmented stopes (2) and upper segmented stopes (3) are alternately arranged in the ore body vertical direction at each interval of 10-15 m, one recovery unit (1) is formed through combination of each lower segmented stope (2) and the corresponding upper segmented stope (3), and studs (4) are scratched at the end portions of the recovery units (1). In each lower segmented stope (2), a cutting groove is formed with a cutting open yard (10) as the free face, and ore falls into atrench (9). A shoveling and conveying machine is utilized for conducting ore loading in an ore loading access road (8), carries the ore into an ore drop shaft (11) through an ore discharging roadway(7) and then lowers the ore into a conveying roadway (12) for car loading and conveying-out. According to the gentle dip medium-thick ore body safety and low-cost combined segmented mining method, every two segmented stopes are gathered into one recovery unit for exploitation, the ore discharging roadway, the ore drop shaft, a slope ramp linking way and other projects are commonly used, the stopepreparation cost is reduced, the preparing time for the stope preparation work is saved, and the exploitation efficiency is improved. Exploited waste stone can be machined into building materials to be sold, and the stockpiling space is additionally arranged for tailing filling.
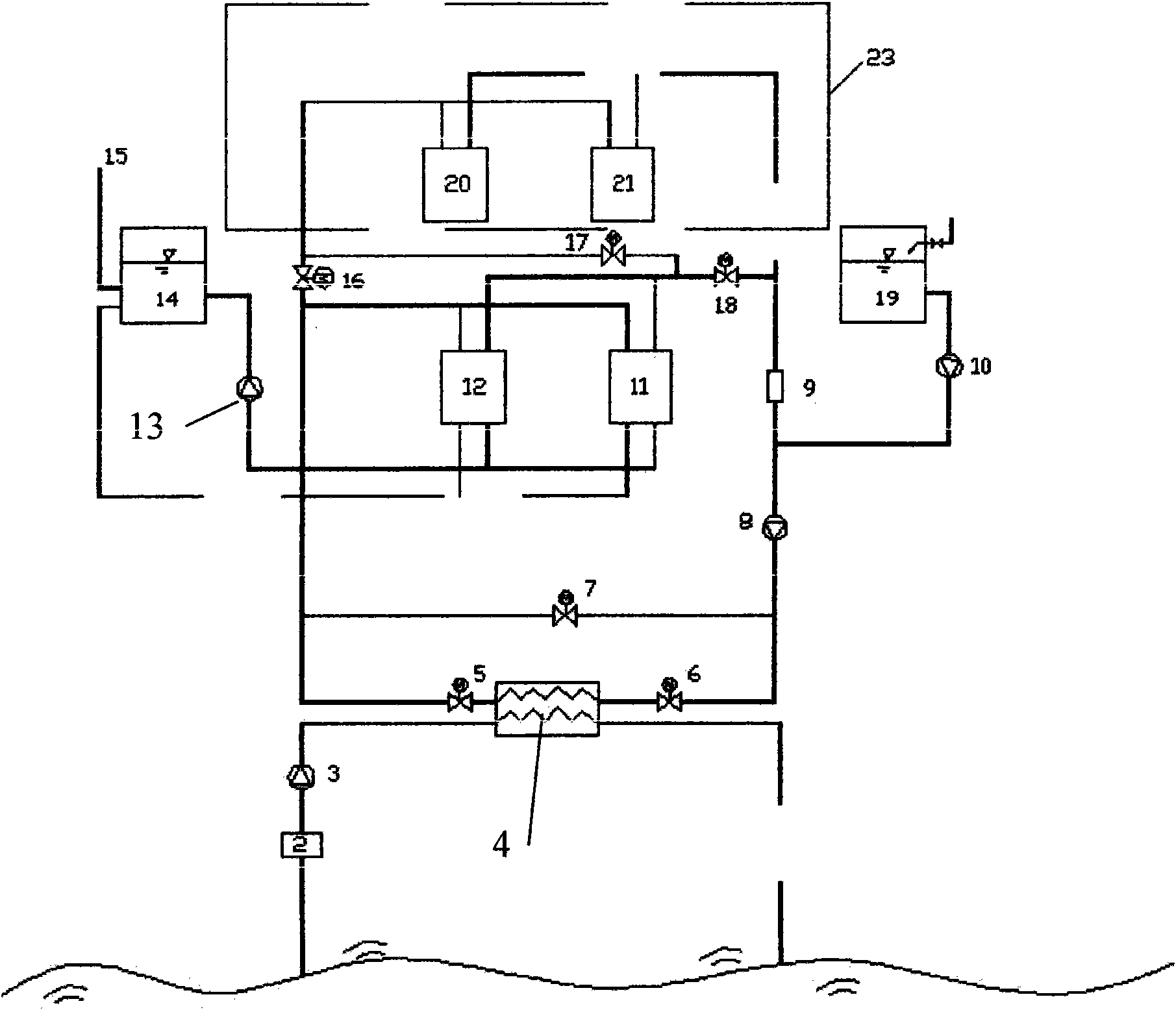
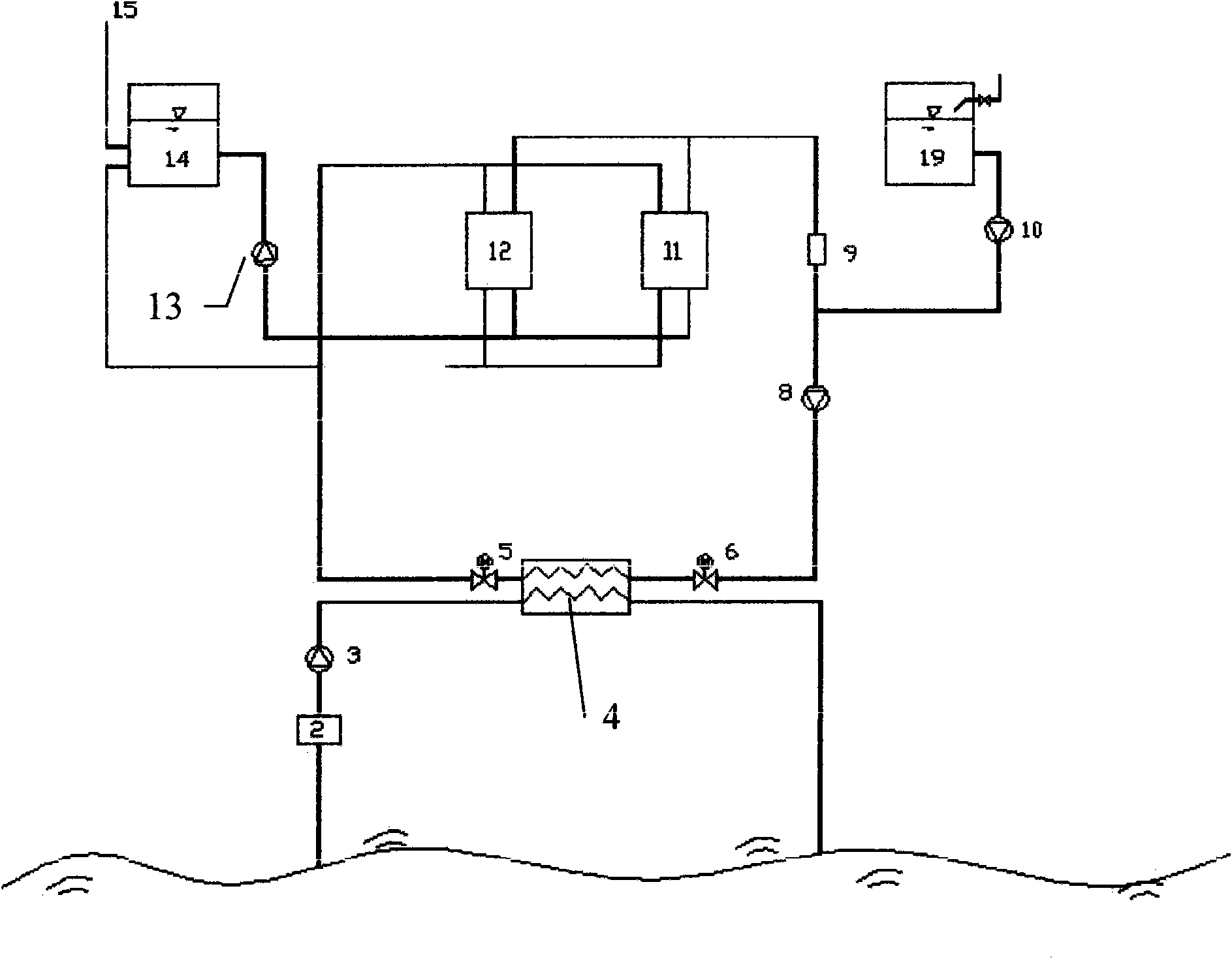
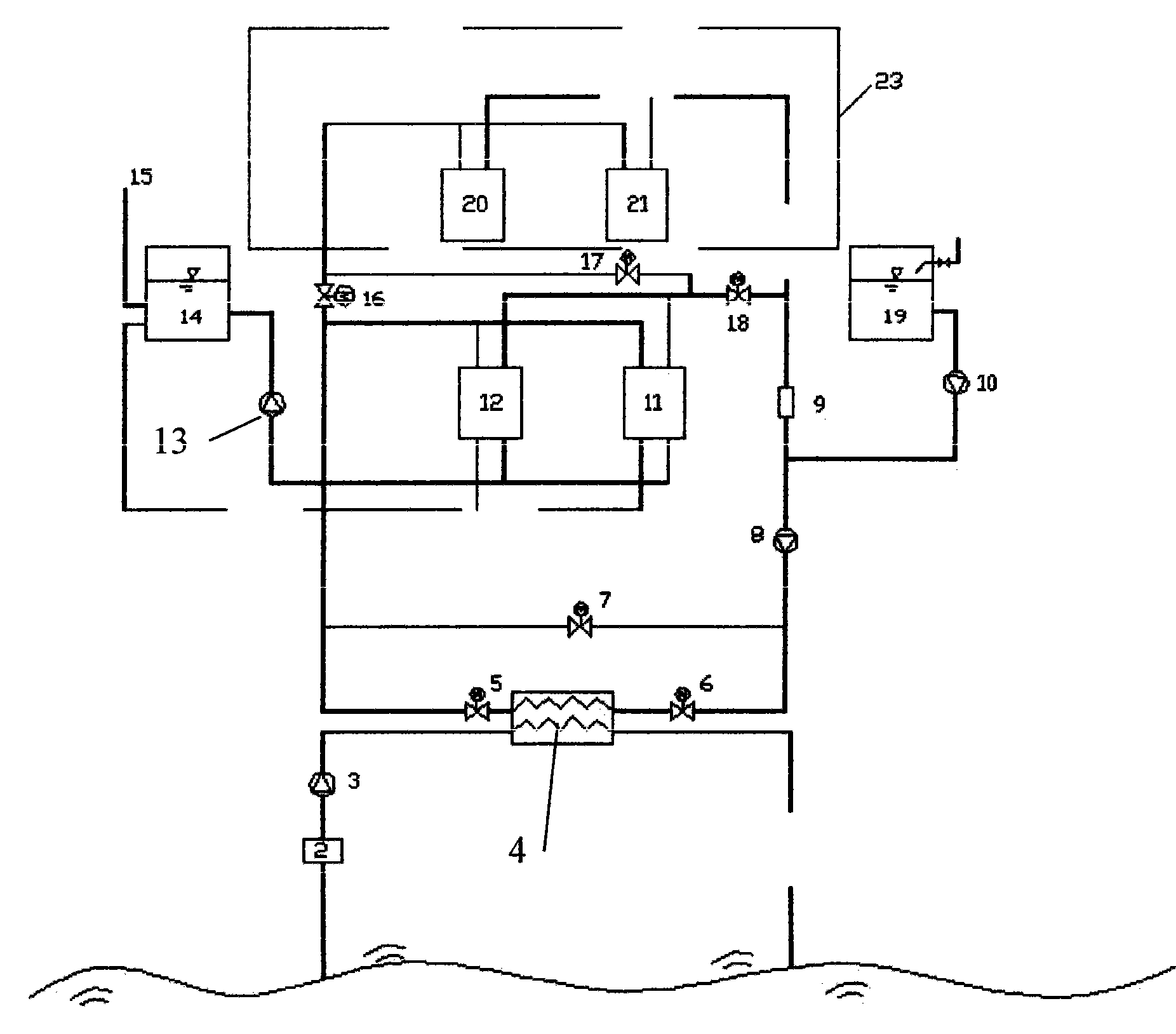
Seawater source water ring heat pump device for air-conditioning system
ActiveCN102095281AAvoid direct accessWill not corrodeHeat pumpsAir conditioning systemsMagnetic valveLower grade
The invention provides a water ring heat pump device for exchanging heat by using seawater heat. The device comprises a seawater plate-type heat exchanger, at least one water-water heat pump unit, a heat exchange medium storage device, at least one magnetic valve and a heat exchange medium transportation pipeline, wherein when one magnetic valve is provided, the magnetic valve is positioned on one side of the seawater plate-type heat exchanger; and when two or more magnetic valves are provided, the magnetic valves are positioned on the two sides of the seawater plate-type heat exchanger respectively. The low-grade energy of seawater is subjected to two heat exchange processes through the water ring heat pump device and is transferred to indoor air or hot water, so that the aims of supplying heat, cold, household hot water to the inside of a room are achieved. In the device, heat exchange between a heat exchange medium and the seawater is performed through the seawater plate-type heat exchanger; the water-water heat pump unit is prevented from being corroded when the seawater enters the heat pump unit; and due to the adoption of the mode, the evaporator and the condenser which are made of anticorrosion materials are not required to be used, the initial investment of equipment is reduced and the device is convenient to popularize and apply in reality.
Owner:QINGDAO TECHNOLOGICAL UNIVERSITY +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com