Virtual machine security isolation system and method oriented to multi-security-level virtual desktop system
A security isolation and virtual desktop technology, which is applied in the field of virtual machine security isolation system, can solve the problems that cannot realize the direct reuse of host system resources, cannot effectively resist attacks, attacks, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] A non-limiting embodiment is given below in conjunction with the accompanying drawings to further illustrate the present invention.
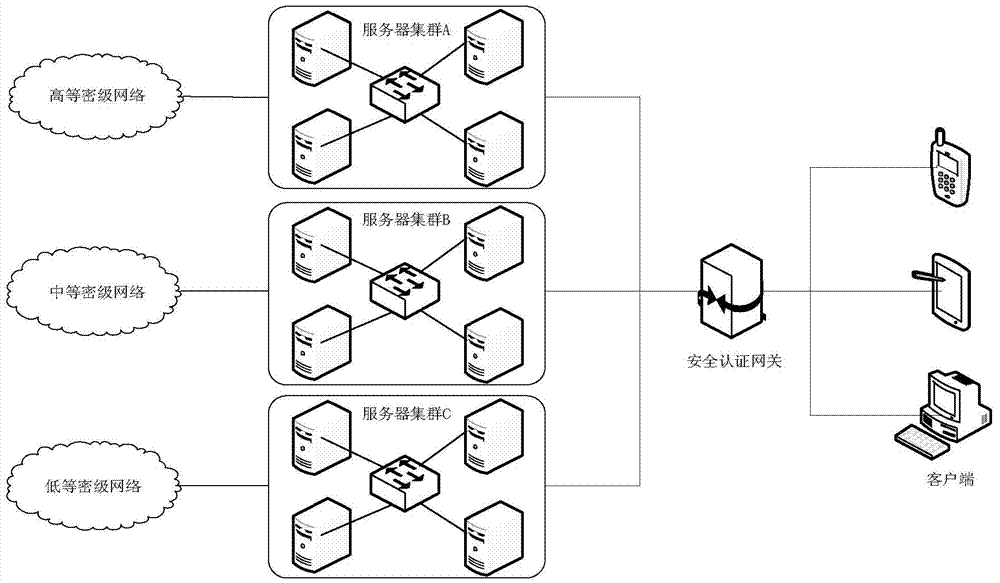
[0033] Such as figure 1 Shown is the system structure diagram of the embodiment of the present invention, including three modules: client, security authentication gateway, and server. Among them, the user-oriented client can be an ordinary computer, a thin client or a dedicated minicomputer terminal; the function of the security authentication gateway is to provide a complete multi-level network unified identity authentication, and realize the unified authentication and authentication of multi-level network users. Management; the server-side hardware can adopt mid-end or high-end configuration servers, and virtual machines can be created on-demand on the host system through server virtualization technology, and each virtual machine corresponds to a terminal desktop user.
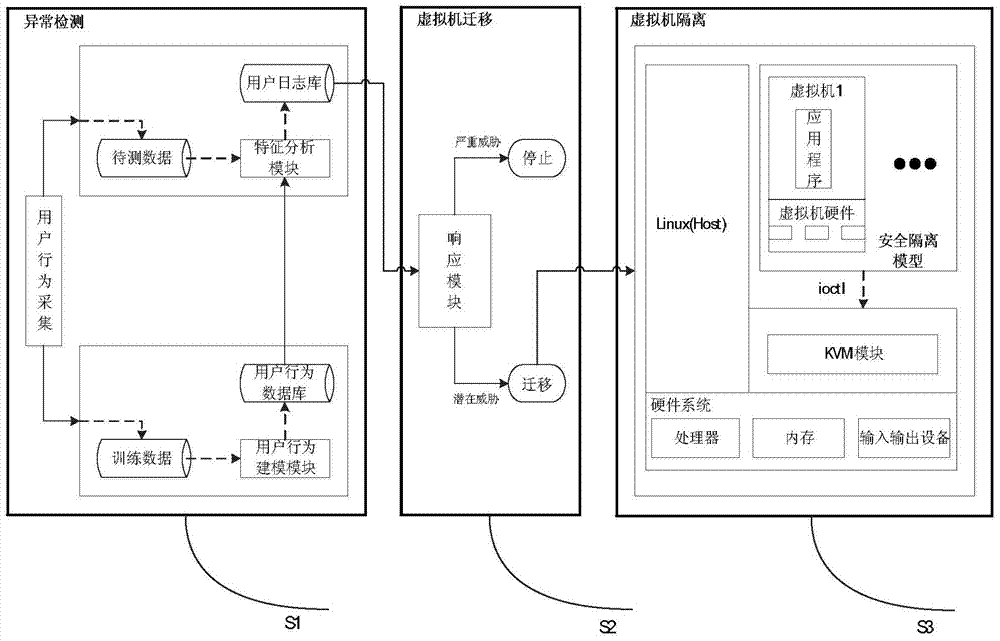
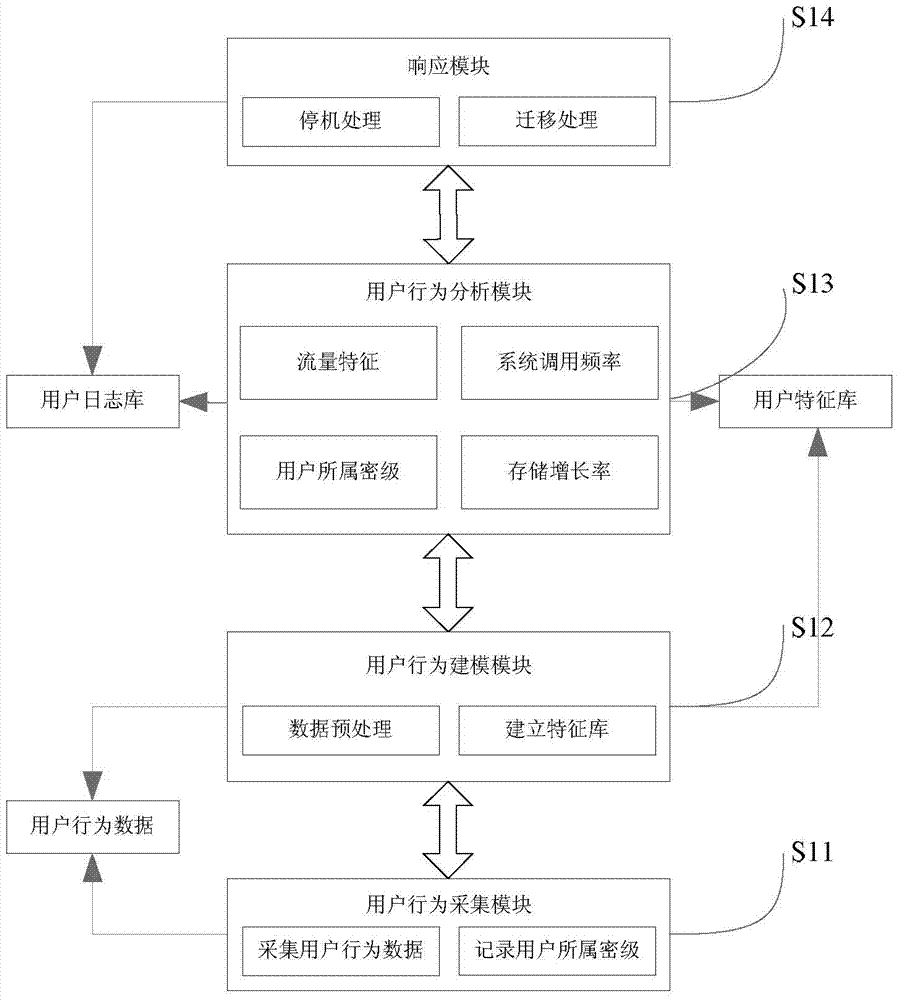
[0034] Such as figure 2 Shown is the implementation structure s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com