Control method for network access admittance
A control method and network access technology, applied in wide area network, data exchange through path configuration, digital transmission system, etc., can solve problems such as illegal copying of internal resources and security risks in the company
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
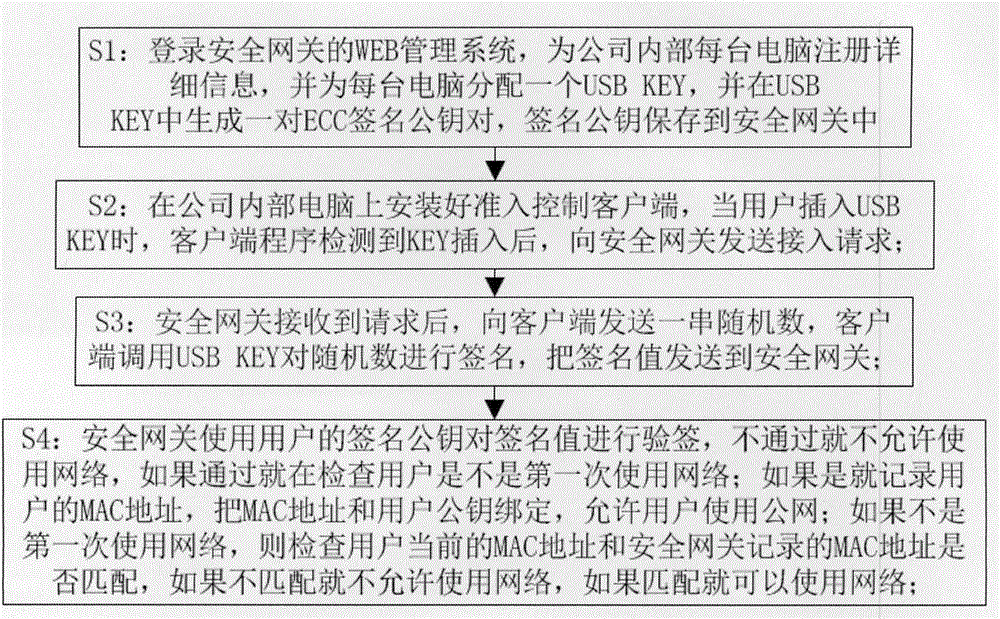
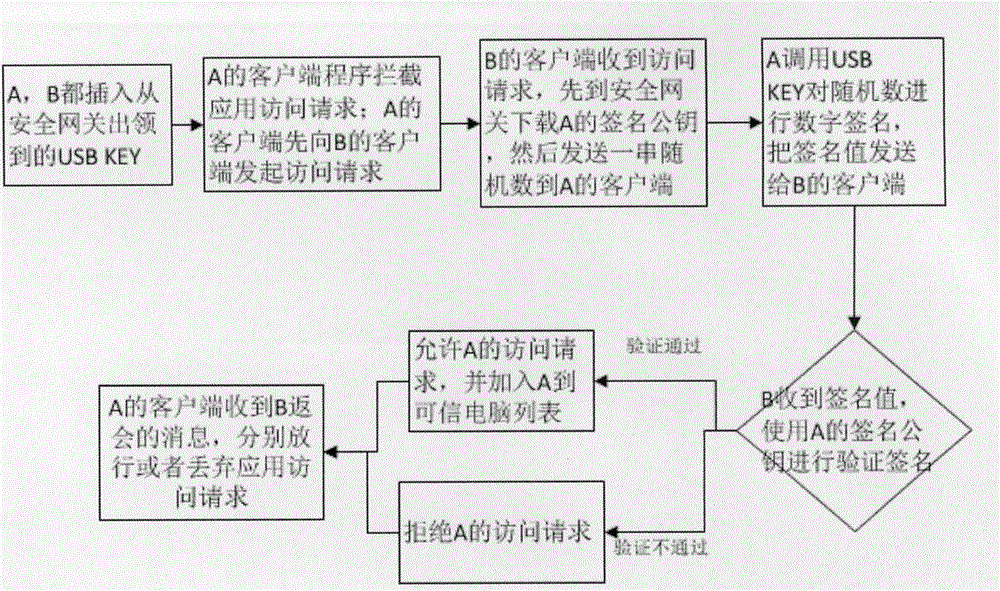
[0020] A network access control method provided by the embodiment of the present invention realizes a method for secure network access, preventing external computers from accessing a local area network, directly using the public network without permission, or copying company resources without permission; It can also prevent the company's computers from directly accessing untrusted computers and prevent the company's computers from being poisoned.
[0021] A network access admission control method provided by an embodiment of the present invention will be described in detail below with reference to the accompanying drawings.
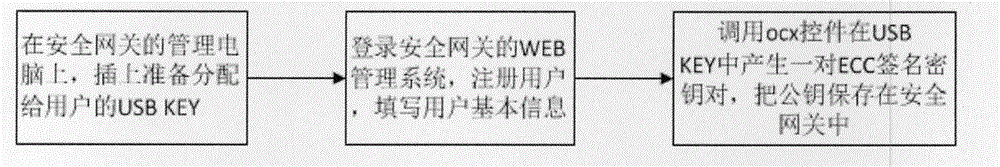
[0022] Such as figure 1 , 2 , 3, 4, and 5, a method for controlling network access admission provided by an embodiment of the present invention is characterized in that it includes the following steps:
[0023] S1: Log in to the WEB management system of the security gateway, register detailed information for each computer in the company, and assign a US...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com