Tunnel packet loss detection method and device, and network communication device
A packet loss detection and monitoring equipment technology, applied in the direction of network interconnection, data exchange network, data exchange through path configuration, etc., can solve the problem of low accuracy, and achieve convenient engineering maintenance, fast and accurate tunnel packet loss detection Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
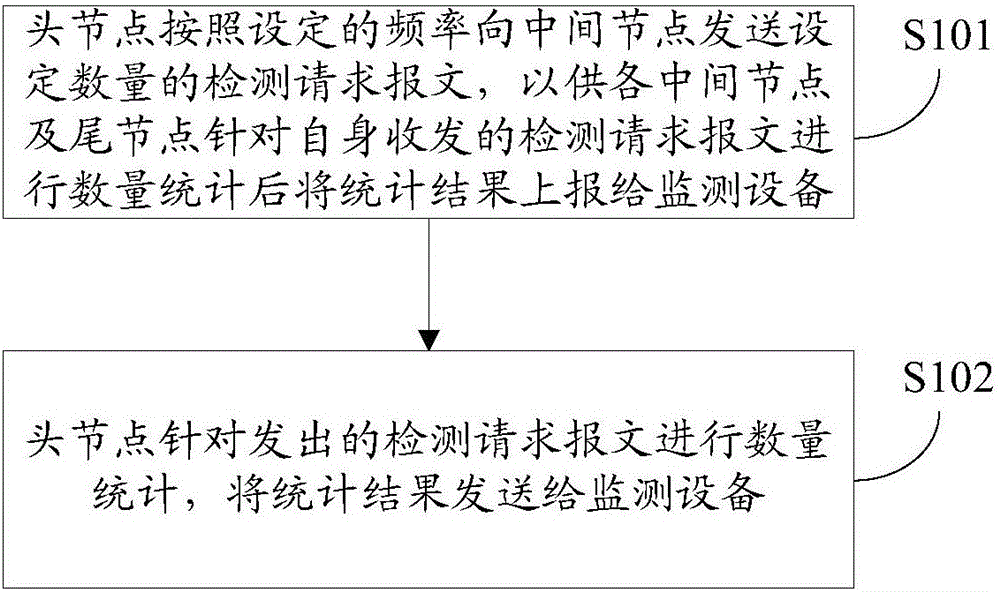
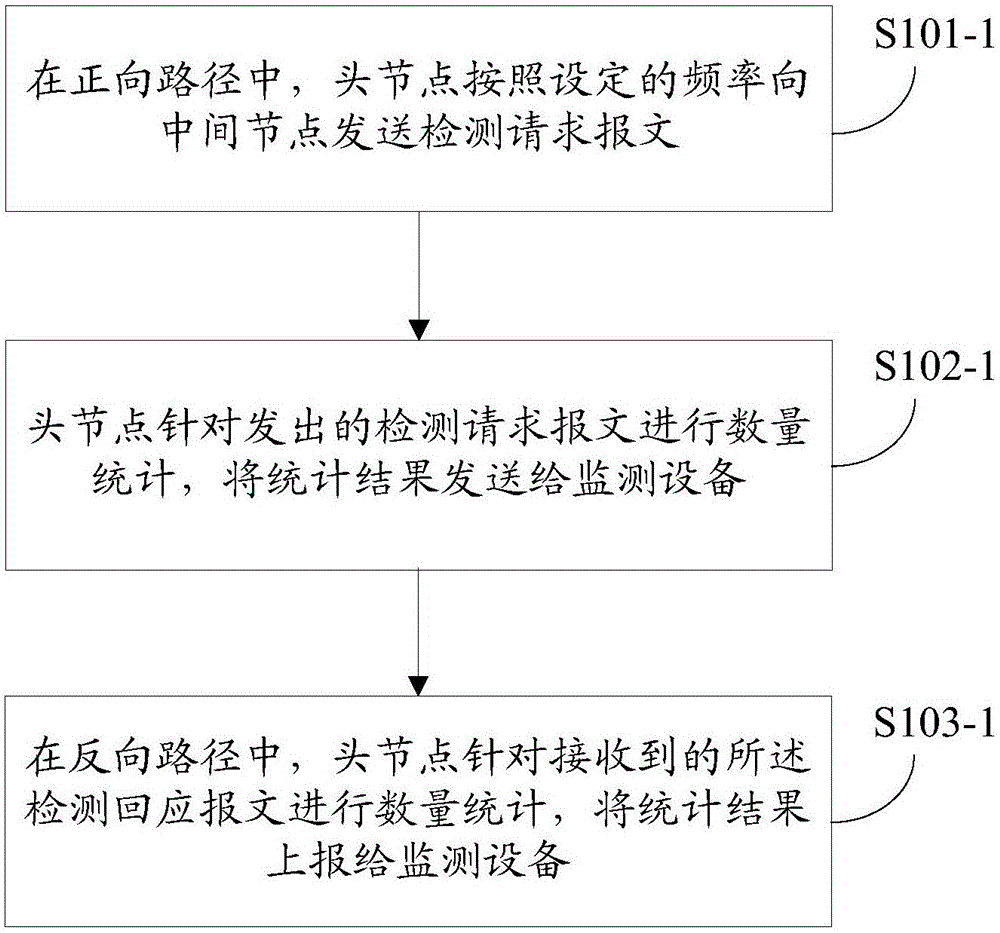
[0053] In the first embodiment of the present invention, a tunnel packet loss detection method is composed of a head node, several intermediate nodes and a tail node to form a tunnel, such as figure 1 As shown, the process performed by the head node includes the following specific steps:
[0054] Step S101, the head node sends a set number of detection request messages to the intermediate nodes according to the set frequency, so that each intermediate node and tail node can count the number of detection request messages sent and received by itself, and then report the statistical results to the monitoring device ; The frequency of the setting is greater than the sending frequency of the Ping message adopted when checking the network connectivity and network speed but must be the upper limit with the transmission bandwidth of the tunnel, and the transmission bandwidth of the tunnel is usually defaulted to the communication device network side The transmission bandwidth of the p...
no. 2 example
[0065] The second embodiment of the present invention is a tunnel packet loss detection method. The method of this embodiment and the method of the first embodiment all belong to the same technical idea. The difference is that this embodiment describes the present invention from the perspective of an intermediate node. Technical solutions.
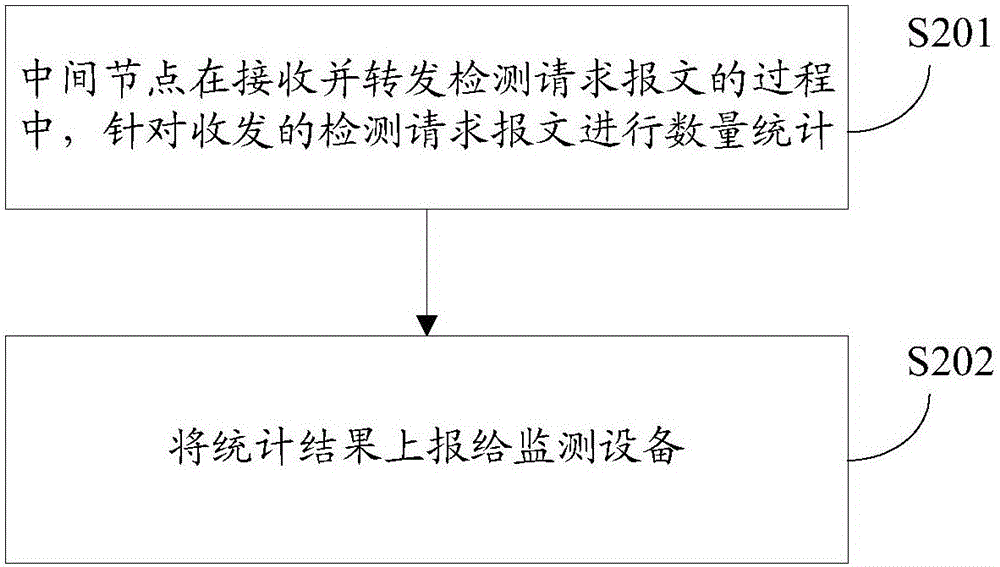
[0066] The tunnel packet loss detection method of this embodiment consists of a head node, several intermediate nodes and a tail node to form a tunnel, such as image 3 As shown, the process executed by the intermediate node includes:
[0067] Step S201 , during the process of receiving and forwarding the detection request message, the intermediate node counts the number of detection request messages sent and received. The frequency at which the detection request message is sent from the head node of the tunnel conforms to the set frequency, and the set frequency is greater than the sending frequency of the Ping message used when checking...
no. 3 example
[0077] The third embodiment of the present invention is a tunnel packet loss detection method. The method of this embodiment and the method of the first embodiment all belong to the same technical idea. The difference is that this embodiment describes the present invention from the perspective of the tail node. Technical solutions.
[0078] The tunnel packet loss detection method of this embodiment consists of a head node, several intermediate nodes and a tail node to form a tunnel, and the process performed by the tail node includes:
[0079] Step S301, counting the number of received detection request messages, and reporting the statistical results to the monitoring device; the frequency of the detection request messages sent from the head node of the tunnel conforms to the set frequency, and the set frequency It is greater than the sending frequency of the Ping message used in network connectivity and network speed checks, but the upper limit must be the transmission bandwi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com