Virus killing method and virus killing device for local area network
A virus detection and local area network technology, applied in the Internet field, can solve the problem of low virus detection and killing rate, and achieve the effect of rapid response, improving virus detection and killing rate, and rapid feedback
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
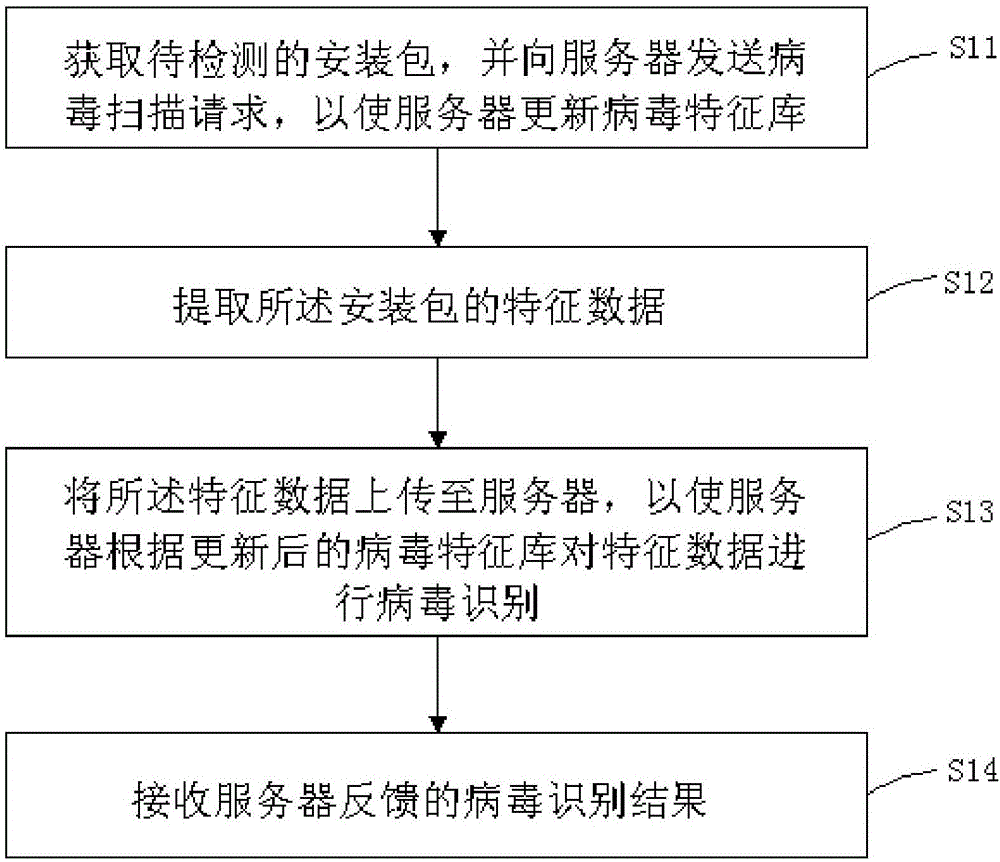
[0056] see figure 1 , the present invention provides a kind of virus checking and killing method for local area network, comprising:
[0057] S11. Obtain the installation package to be detected, and send a virus scanning request to the server, so that the server updates the virus signature database;
[0058] S12. Extracting feature data of the installation package;
[0059] S13. Upload the characteristic data to the server, so that the server can identify the virus on the characteristic data according to the updated virus characteristic database;
[0060] S14. Receive the virus identification result fed back by the server.
[0061] The installation package also includes a signature file;
[0062] The feature identification data of the extraction of the installation package specifically includes:
[0063] Identify the installation package;
[0064] A hash algorithm is used to calculate the hash value of the signature file as the feature identification data of the installat...
Embodiment 2
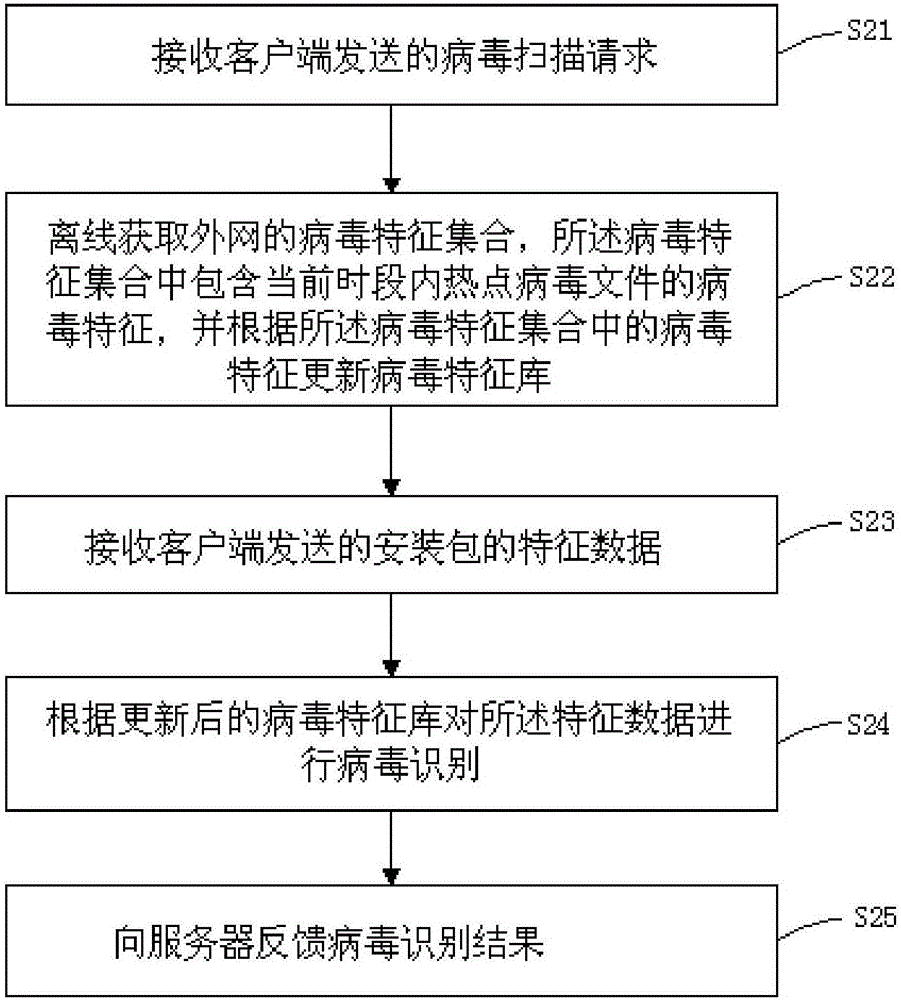
[0066] see figure 2 , the present invention also provides another virus checking and killing method for local area network, comprising:
[0067] S21. Receive a virus scanning request sent by the client;
[0068]S22. Obtain the virus signature set of the external network offline, the virus signature set includes the virus signatures of hot virus files in the current period, and update the virus signature library according to the virus signatures in the virus signature set;
[0069] S23. Receive the characteristic data of the installation package sent by the client;
[0070] S24. Perform virus identification on the feature data according to the updated virus feature database;
[0071] S25. Feedback the virus identification result to the server.
[0072] Specifically, updating the virus signature library according to the virus signatures in the virus signature set includes:
[0073] Empty the virus signatures in the virus signature database, and write the virus signatures in...
Embodiment 3
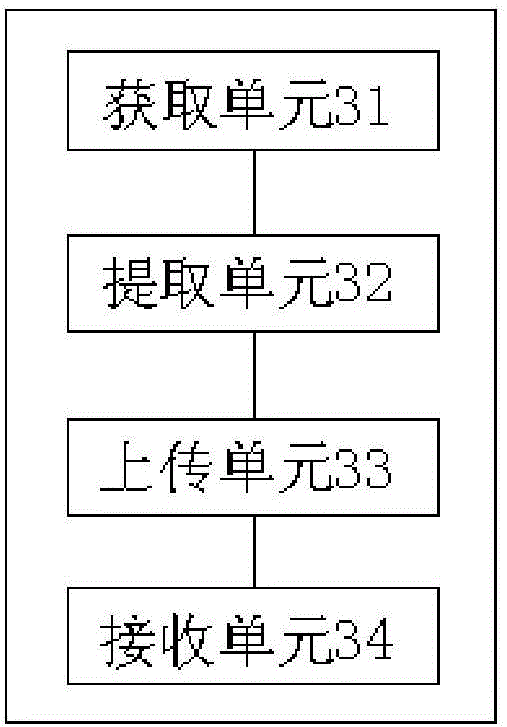
[0078] see image 3 , the present invention also provides a virus scanning and killing device for a local area network, which is used to implement the method described in the first embodiment above, and the device includes:
[0079] An acquisition unit 31, configured to acquire the installation package to be detected, and send a virus scanning request to the server, so that the server updates the virus signature database;
[0080] An extracting unit 32, configured to extract feature data of the installation package;
[0081] An uploading unit 33, configured to upload the feature data to the server, so that the server performs virus identification on the feature data according to the updated virus feature database;
[0082] The receiving unit 34 is configured to receive the virus identification result fed back by the server.
[0083] Specifically, the installation package also includes a signature file;
[0084] The extraction unit is specifically used for:
[0085] Identif...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com