A login method and terminal
A login method and terminal technology, applied in the electronic field, can solve problems such as the theft and tampering of authentication information, the inability to guarantee security, and the imperfect security authentication mechanism, so as to avoid theft and embezzlement, improve authentication security, and prevent illegal login.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
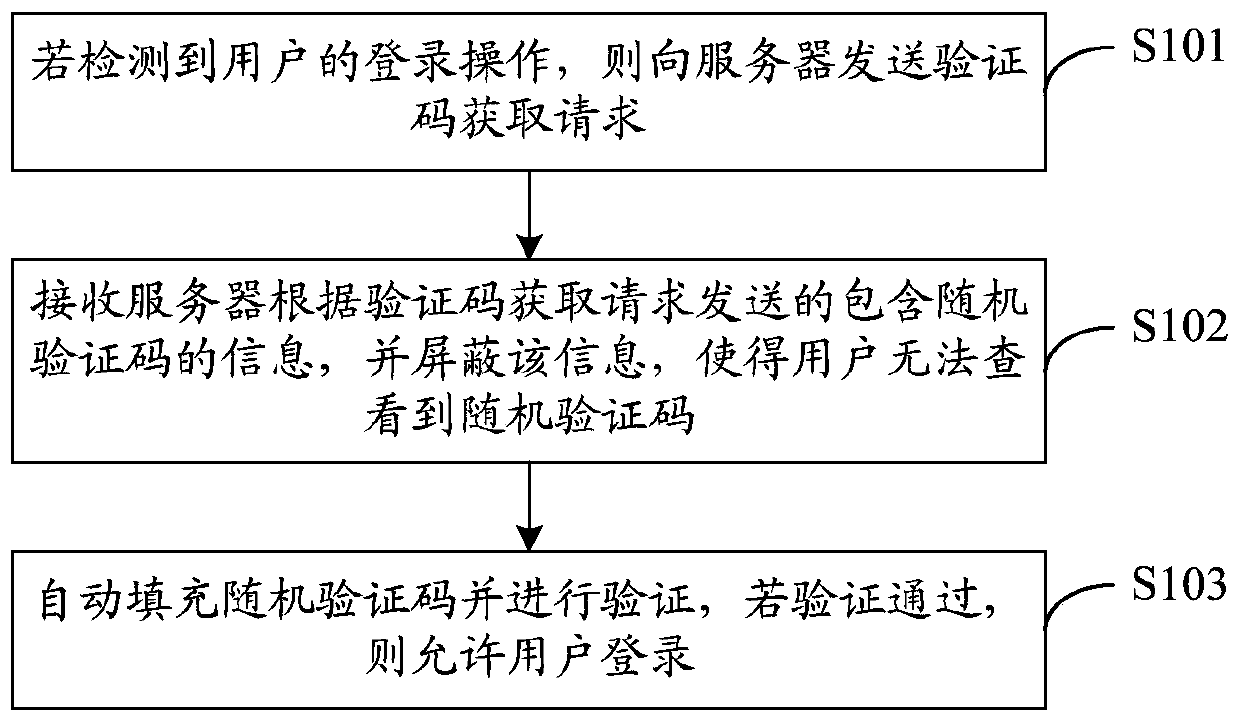
[0029] see figure 1 , figure 1 It is a schematic flow chart of a login method provided in Embodiment 1 of the present invention. The execution subject of this embodiment is a terminal, which may be a mobile phone or other smart terminals. figure 1 The illustrated login method may include the following steps:
[0030] S101. If a user's login operation is detected, a verification code acquisition request is sent to the server.
[0031] When a user logs in to an application software (Application, APP) on a terminal, it is often necessary to verify a communication number of a subscriber identification (Subscriber Identification Module, SIM) card, and the verification process is usually completed through a verification code.
[0032] Specifically, if the terminal detects that the user triggers a login operation, it sends a verification code acquisition request to the server.
[0033] The login operation triggered by the user may be the login operation of the private line encrypt...
Embodiment 2
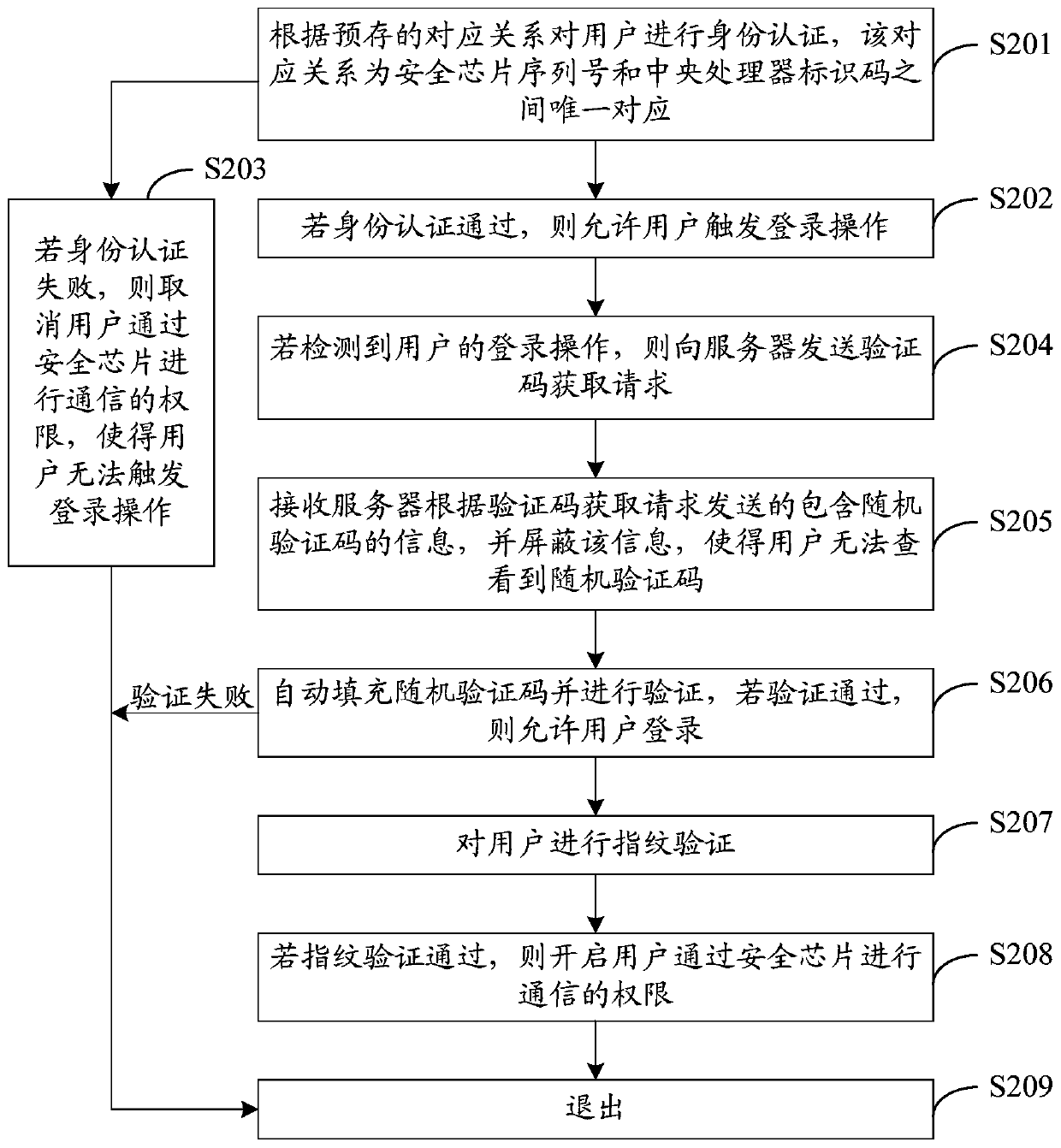
[0044] see figure 2 , figure 2 It is a schematic flow chart of a login method provided by Embodiment 2 of the present invention. The execution subject of this embodiment is a terminal, which may be a mobile phone or other smart terminals. figure 2 The illustrated login method may include the following steps:
[0045] S201. Perform identity authentication on the user according to a pre-stored correspondence, the correspondence being a unique correspondence between the serial number of the security chip and the identification code of the central processing unit.
[0046] Specifically, before the user triggers the login operation of the APP, the terminal with the security chip will authenticate the user according to the pre-stored corresponding relationship. This verification process can be completed when the terminal is turned on, or when the user registers the APP. The completion may also be completed at other times before the login operation on the APP is triggered, and t...
Embodiment 3
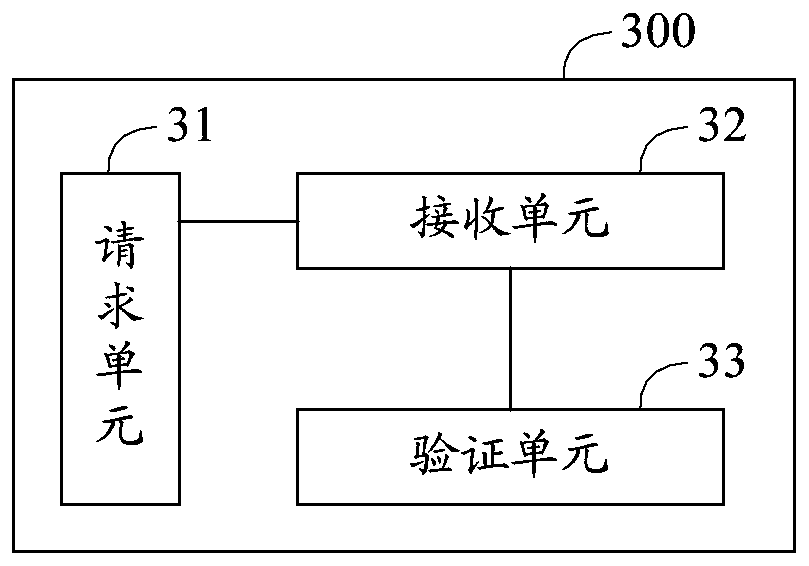
[0081] see image 3 , image 3 It is a schematic block diagram of a terminal provided by Embodiment 3 of the present invention. For ease of description, only parts related to the embodiments of the present invention are shown. image 3 The example terminal 300 may be the execution subject of the login method provided in the first embodiment. image 3 The exemplary terminal 300 mainly includes: a requesting unit 31 , a receiving unit 32 and a verification unit 33 . The details of each unit are as follows:
[0082] The request unit 31 is configured to send a verification code acquisition request to the server if a user's login operation is detected;
[0083] The receiving unit 32 is configured to receive the information containing the random verification code sent by the server according to the verification code acquisition request, and shield the information so that the user cannot view the random verification code;
[0084]The verification unit 33 is configured to automat...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap