A kind of unlocking code processing method, door lock and front server
A technology for unlocking passwords and processing methods, which is applied in the direction of instruments, time registers, and individual input/output registers, etc., and can solve the problems of easy leakage of unlocking passwords, hidden dangers of personal and property safety of tourists staying in the room, leakage of unlocking passwords, etc. problems, to achieve the effect of reducing the leakage of unlocking passwords, ensuring personal and property safety, and reducing daily costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0071] This embodiment provides a method for processing an unlock password, and the execution subject of this embodiment is a door lock. The door lock can generate an unlock password valid in the current password generation period in each password generation period through the unlock password processing method provided in this embodiment.
[0072] see Figure 4 The shown flow chart of a method for processing an unlock password provided by this embodiment includes the following steps:
[0073] Step 400, the door lock acquires current time information.
[0074] Wherein, the above-mentioned door lock obtains current time information from a clock module preset in the processor.
[0075] The above-mentioned clock module is used to generate current time information, so that the door lock can obtain the current time information in real time.
[0076] Step 402: When it is determined according to the obtained time information that the time since the last generation of the unlock pas...
Embodiment 2
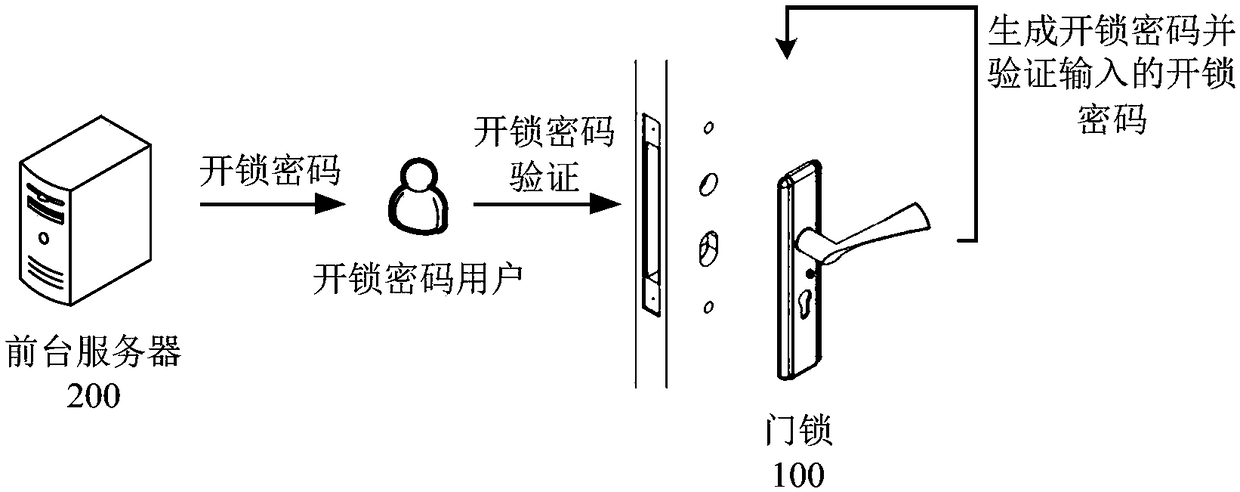
[0115] In related technologies, after the front-end server that communicates with the door lock in real time generates the unlock code of the room, it will send the generated unlock code to the door lock of the room that the visitor is about to stay in, and the front-end server will send the generated unlock code to the corresponding door lock. During the lock process, if the unlock password is monitored by criminals, it will also cause the leakage of the unlock password, so that the room unlock password generated by the front server that communicates with the door lock in real time cannot protect the tourists staying in the room. Personal and property safety plays a protective role.
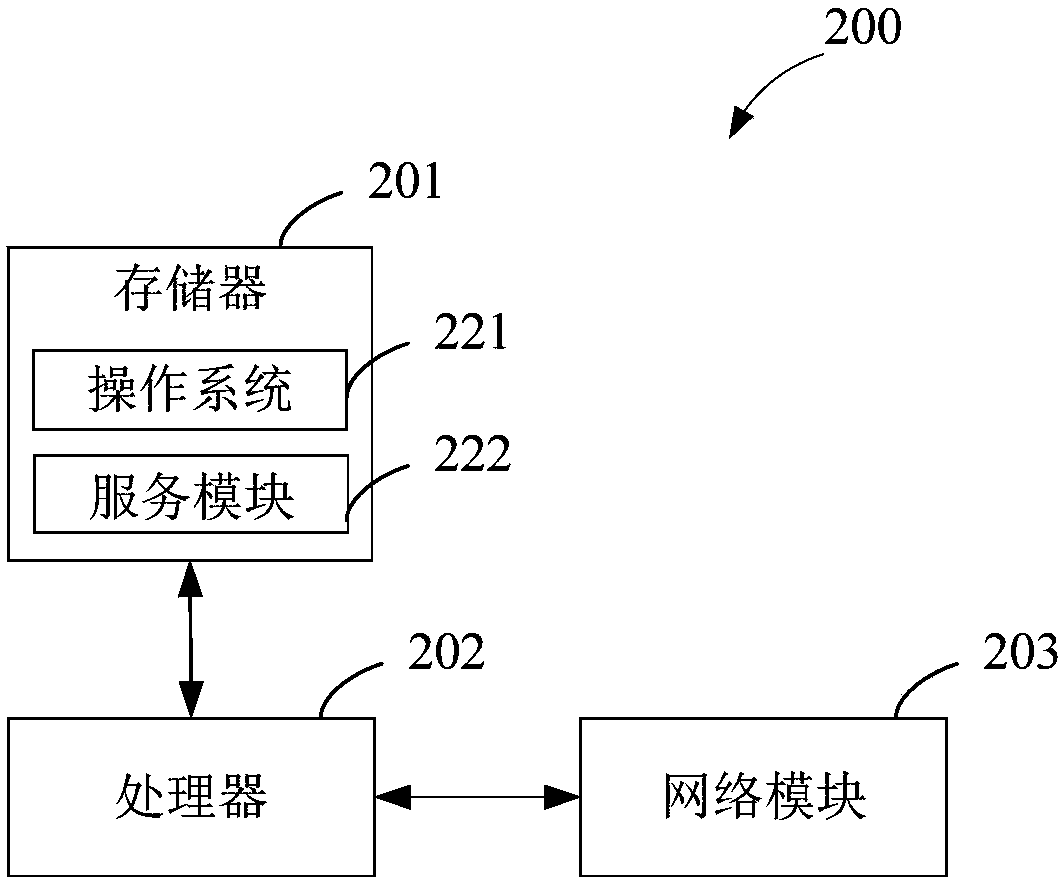
[0116] In order to solve the above problems, this embodiment provides a method for processing unlock passwords. The execution subject of this embodiment is the front-end server. Sent to the unlock password user.
[0117] see Figure 5 , which shows a flow chart of a method for processing an un...
Embodiment 3
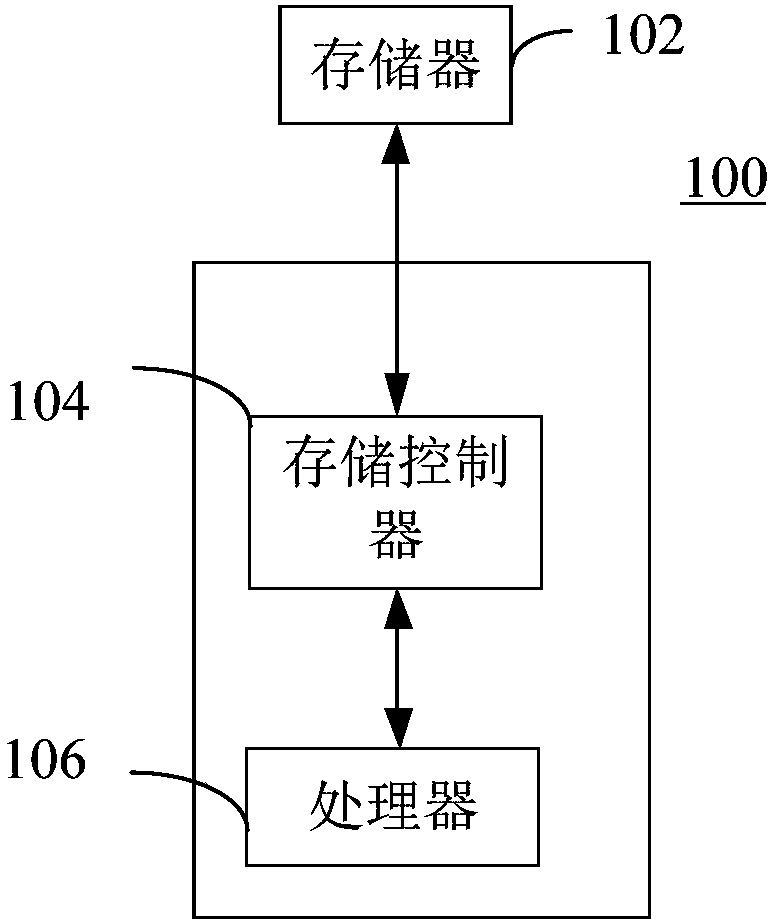
[0141] This embodiment provides a door lock, which is used to implement the unlocking password processing method described in Embodiment 1 above.
[0142] see Figure 6 , a door lock provided in this embodiment shown, including:
[0143] A time information acquisition module 600, configured to acquire current time information;
[0144] The password generation module 602 is configured to encrypt the password generation information of the current password generation period to obtain the current password generation period when it is determined according to the acquired time information that the time since the last generation of the unlock password reaches the preset password generation period valid unlock code.
[0145] To sum up, the door lock provided by this embodiment automatically generates an effective unlock password in the current password generation cycle in each password generation cycle, which is different from the unlock code in the prior art door lock, which is a f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com