Identity verification method and apparatus
An identity verification and identity attribute technology, applied in the field of information identification, can solve problems such as inability to match users, inability to verify user identity, etc., to achieve the effect of expanding usage scenarios
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
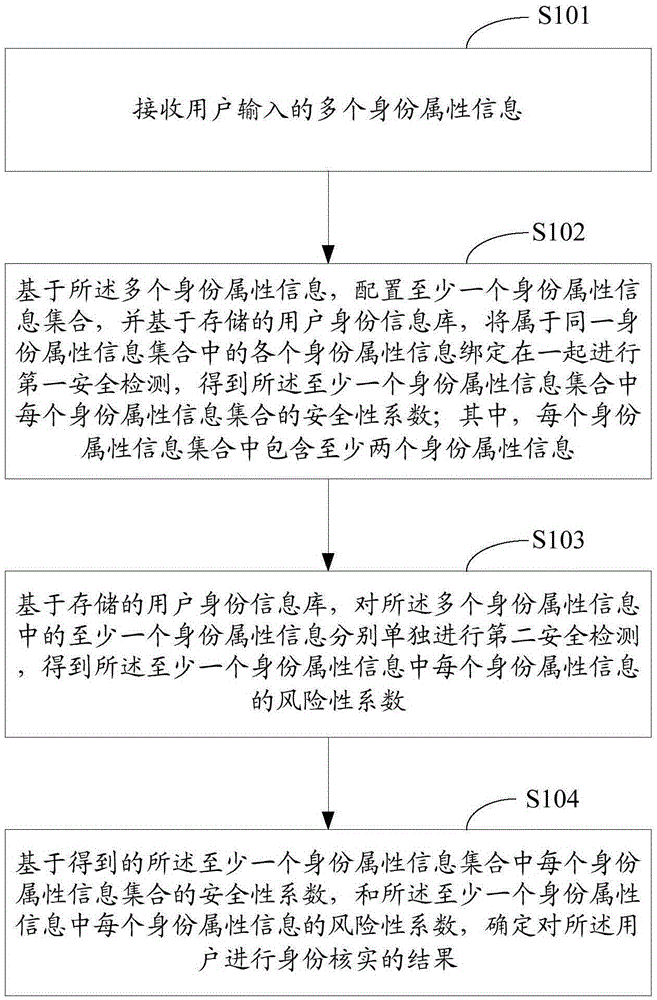
[0052] like figure 1 As shown, the flow chart of the identity verification method provided in Embodiment 1 of the present application includes the following steps:
[0053] S101: Receive multiple pieces of identity attribute information input by a user.
[0054] Here, the plurality of identity attribute information input by the user may include: ID card number, name, mobile phone number, address, email address, address, and the like.
[0055] S102: Based on the plurality of identity attribute information, configure at least one identity attribute information set, and based on the stored user identity information database, bind together each identity attribute information belonging to the same identity attribute information set to perform the first security detection , to obtain the safety factor of each identity attribute information set in the at least one identity attribute information set; wherein, each identity attribute information set contains at least two identity attr...
Embodiment 2
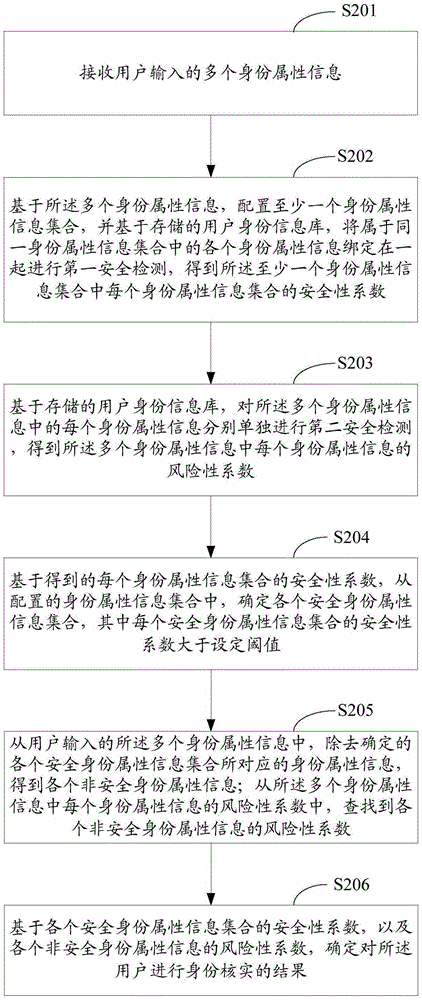
[0063] like figure 2 As shown, the flow chart of the identity verification method provided in Embodiment 2 of the present application includes the following steps:
[0064] S201: Receive multiple pieces of identity attribute information input by a user.
[0065] S202: Based on the plurality of identity attribute information, configure at least one identity attribute information set, and based on the stored user identity information database, bind together the identity attribute information belonging to the same identity attribute information set to perform the first security detection , to obtain the safety factor of each identity attribute information set in the at least one identity attribute information set; wherein, each identity attribute information set contains at least two identity attribute information.
[0066] S203: Based on the stored user identity information database, perform a second security check on each identity attribute information in the plurality of ide...
Embodiment 3
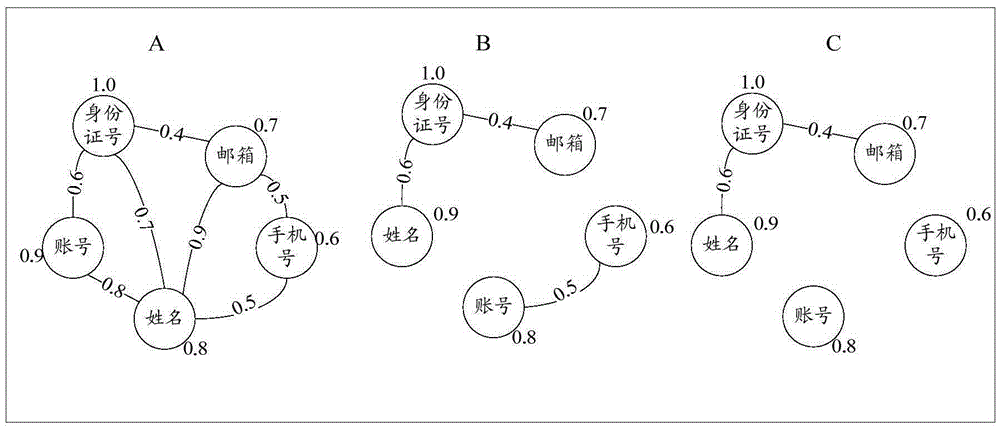
[0084] like Figure 4 As shown, the flow chart of the identity verification method provided in Embodiment 3 of the present application includes the following steps:
[0085] S401: Receive multiple pieces of identity attribute information input by a user.
[0086] S402: Based on the plurality of identity attribute information, configure at least one identity attribute information set, and based on the stored user identity information database, bind together the identity attribute information belonging to the same identity attribute information set to perform the first security detection , to obtain the safety factor of each identity attribute information set in the at least one identity attribute information set; wherein, each identity attribute information set contains at least two identity attribute information.
[0087] S403: Based on the obtained safety factor of each identity attribute information set, determine each security identity attribute information set from the co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com