Terminal function authorization method and device
A technology of terminals and functions, which is applied in the field of terminal function authorization methods and devices, and can solve problems such as cumbersome processes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
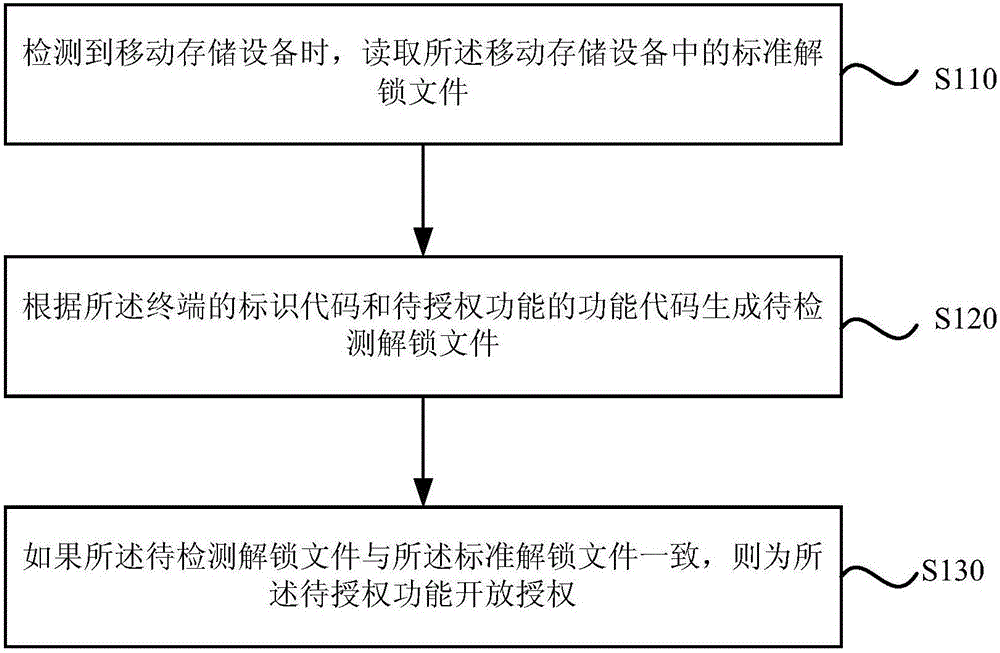
[0020] figure 1 It is a flowchart of a terminal function authorization method provided by Embodiment 1 of the present invention. This embodiment is applicable to various situations of terminal function authorization, and the method can be executed by the terminal function authorization device provided by the embodiment of the present invention. The device can be implemented in the form of software and / or hardware, and the device can be integrated into any device that provides terminal function authorization functions, such as a typical user terminal device, which can be a computer or a TV, such as figure 1 shown, including:
[0021] S110. When a mobile storage device is detected, read a standard unlock file in the mobile storage device.
[0022] Among them, the mobile storage device is a portable data storage device, which refers to a storage medium and has the function of reading and writing the medium itself, for example, it can be a U disk, a mobile hard disk, and various ...
Embodiment 2
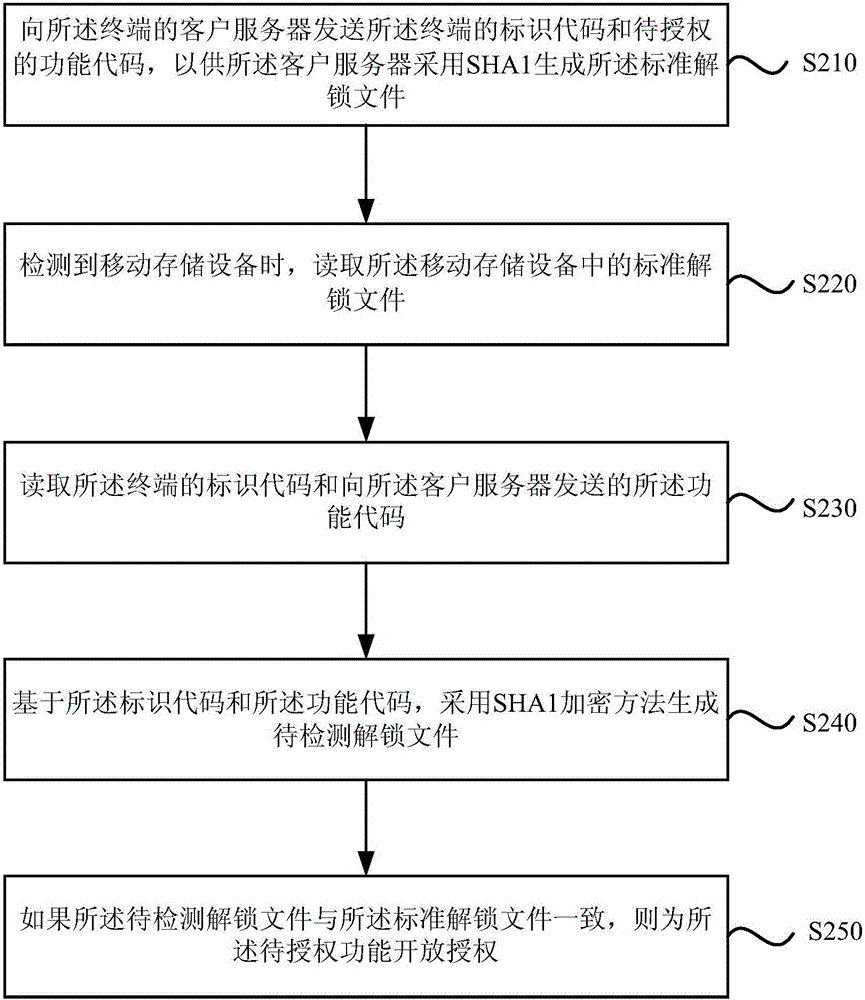
[0032] figure 2 It is a flow chart of a terminal function authorization method provided by Embodiment 2 of the present invention. On the basis of the above embodiments, this embodiment further includes: sending the identification code of the terminal and the authorization code to be authorized to the client server of the terminal. A function code for the client server to use SHA1 to generate the standard unlock file; and an optimized processing method for generating the unlock file to be detected according to the identification code of the terminal and the function code of the function to be authorized is provided, specifically Yes: reading the identification code of the terminal and the function code sent to the client server; based on the identification code and the function code, using the SHA1 encryption method to generate an unlock file to be detected.
[0033] Correspondingly, the method of this embodiment includes:
[0034] S210. Send the identification code of the te...
Embodiment 3
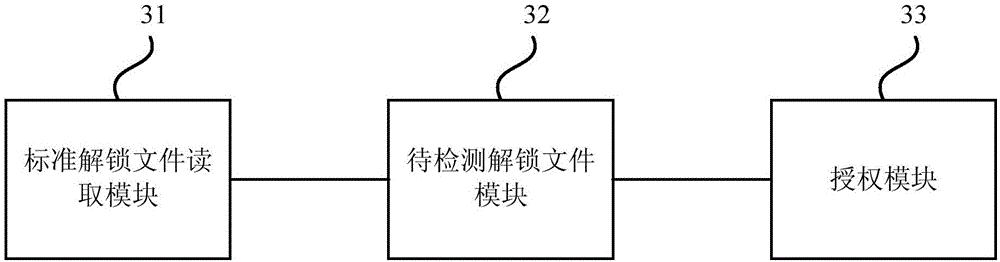
[0046] image 3 It is a schematic structural diagram of a terminal function authorization device provided in Embodiment 3 of the present invention. This embodiment is applicable to various terminal function authorization situations, and the method can be executed by the terminal function authorization device provided in the embodiment of the present invention. The device can be implemented in the form of software and / or hardware, and the device can be integrated into any device that provides terminal function authorization functions, such as a typical user terminal device, which can be a computer or a TV, such as figure 1 As shown, it specifically includes: a standard unlock file reading module 31 , a pending unlock file module 32 and an authorization module 33 .
[0047] A standard unlock file reading module 31, configured to read the standard unlock file in the mobile storage device when a mobile storage device is detected;
[0048] The unlocking file module 32 to be detect...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com