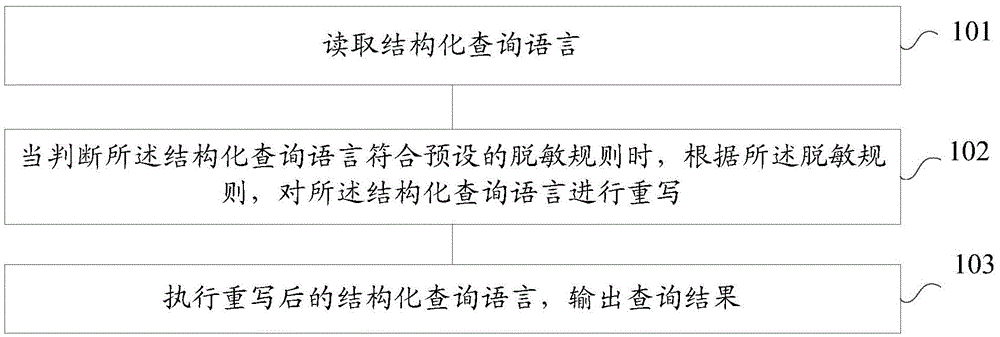
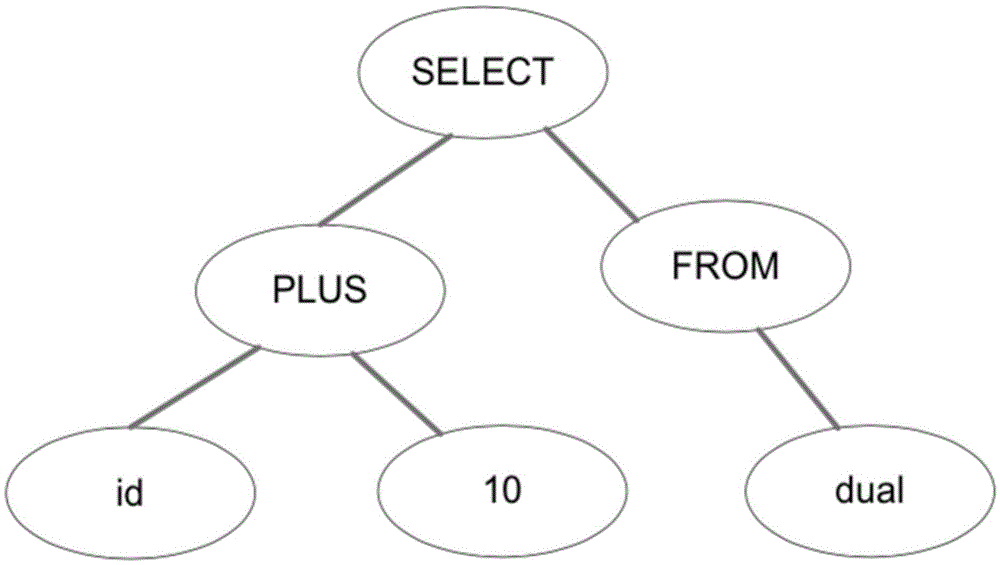
Method and system of data masking
A data desensitization and desensitization technology, which is applied in the data desensitization system and data desensitization field, can solve the problems of high storage and computing consumption and lack of flexibility in scheduling, so as to ensure security, save storage and computing consumption, The effect of improving data desensitization efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example
[0107] Example: long_hash(id)
[0108] crc32
[0109] Function description: use the CRC32 algorithm to encrypt the input, and the result is a long integer
[0110] Parameter: field name
[0111] Example: long_hash(id)
[0112] crc64
[0113] Function description: CRC64 algorithm encrypts the input, and the result is a long integer
[0114] Parameter: field name
[0115] Example: long_hash(id)
[0116] md5
[0117] Function description: The md5 algorithm encrypts the input, and the parameter string is a salt value (that is, the encryption interference value), which can improve the security of the encryption
[0118] Parameters: field name, salt
[0119] Example: md5(id,'md5_salt')
[0120] encrypt
[0121] Function description: encryption function, the parameter is the specified key (can be decrypted, please use it with caution)
[0122] Parameters: field name, encryption key
[0123] Example: encrypt(id,'encrypt_key')
[0124] d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com