Patents
Literature
234 results about "Data masking" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data masking or data obfuscation is the process of hiding original data with modified content (characters or other data.)
Obfuscating network traffic from previously collected network traffic
ActiveUS8996728B2Multiple digital computer combinationsData switching networksTraffic capacityComputer network
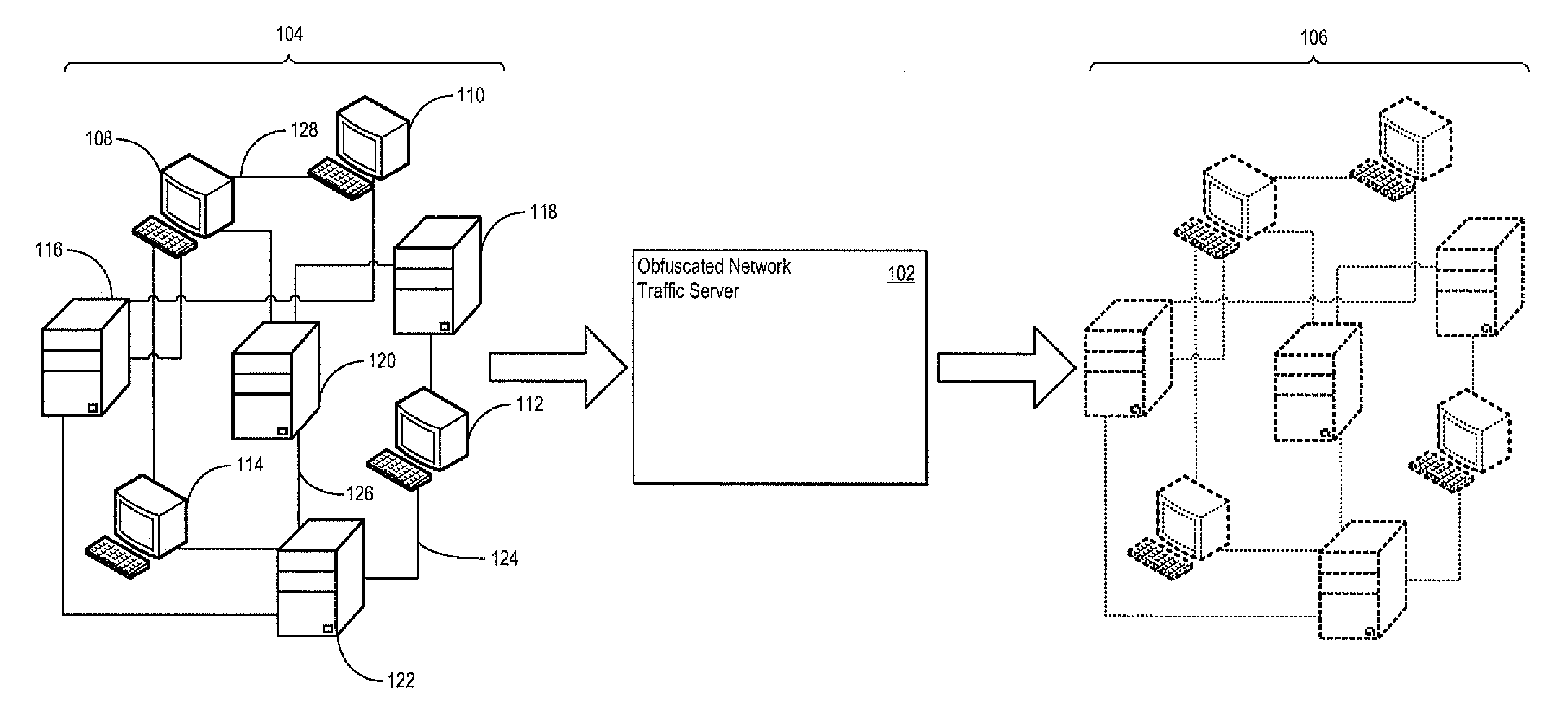
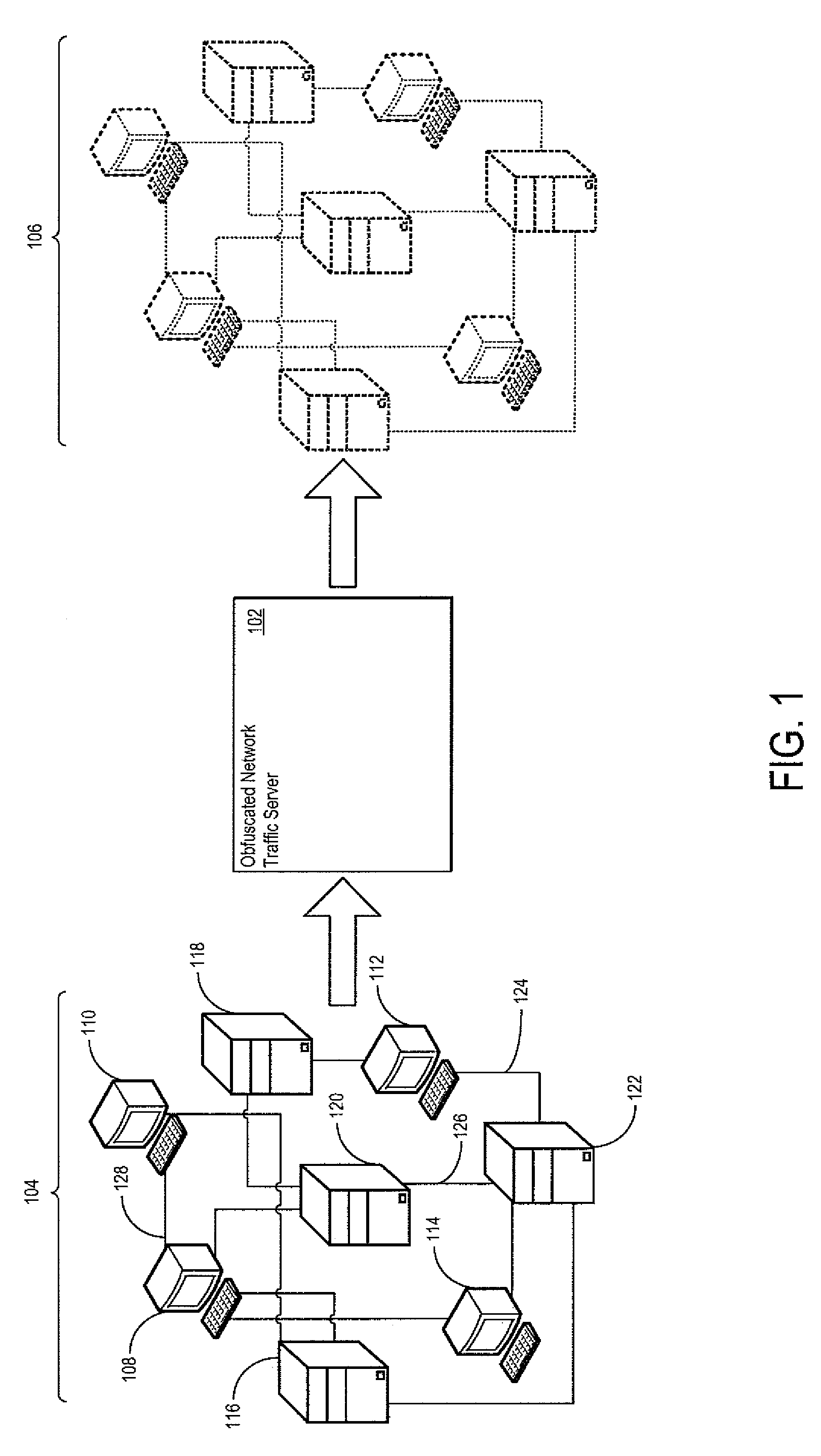
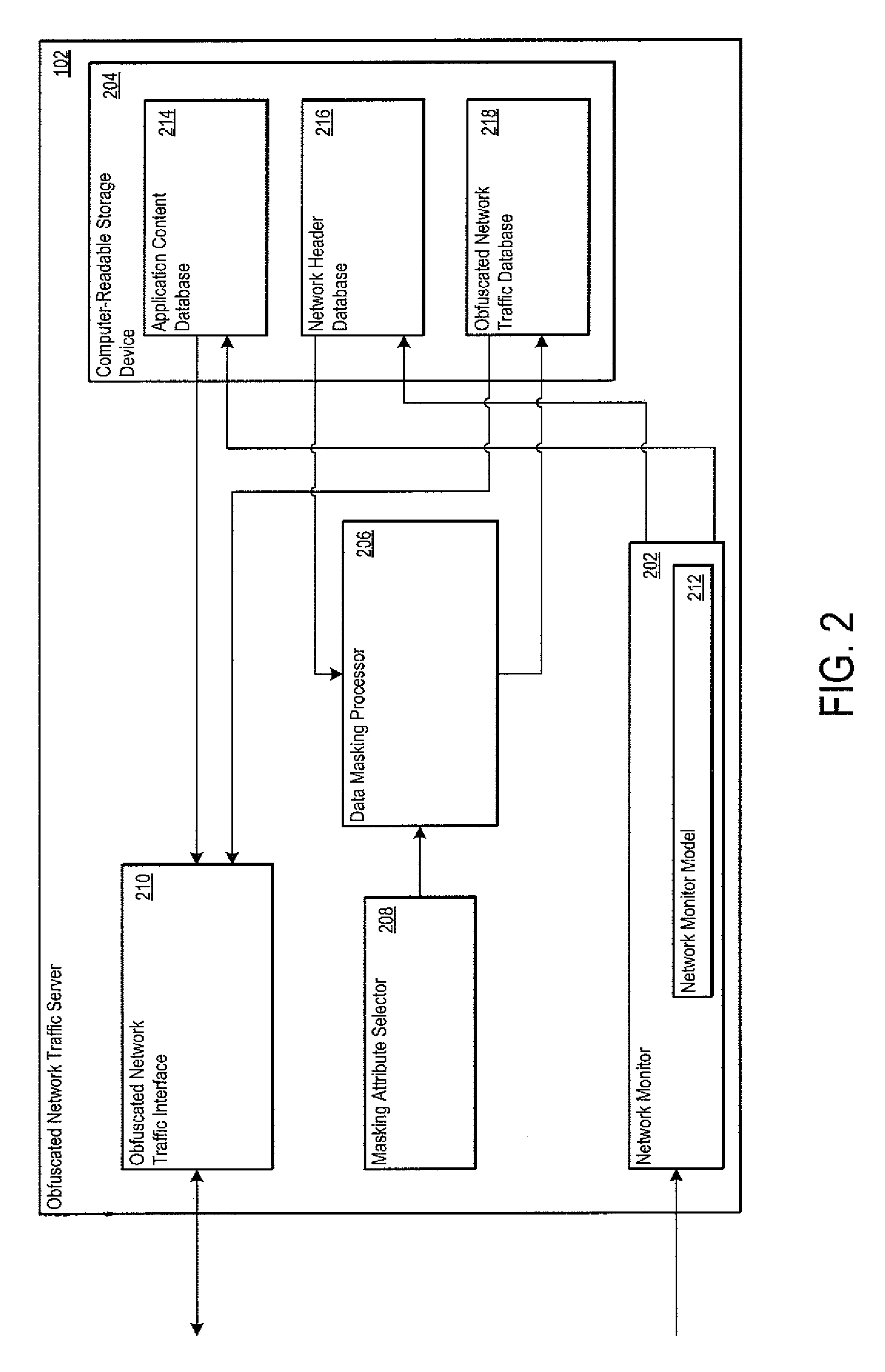
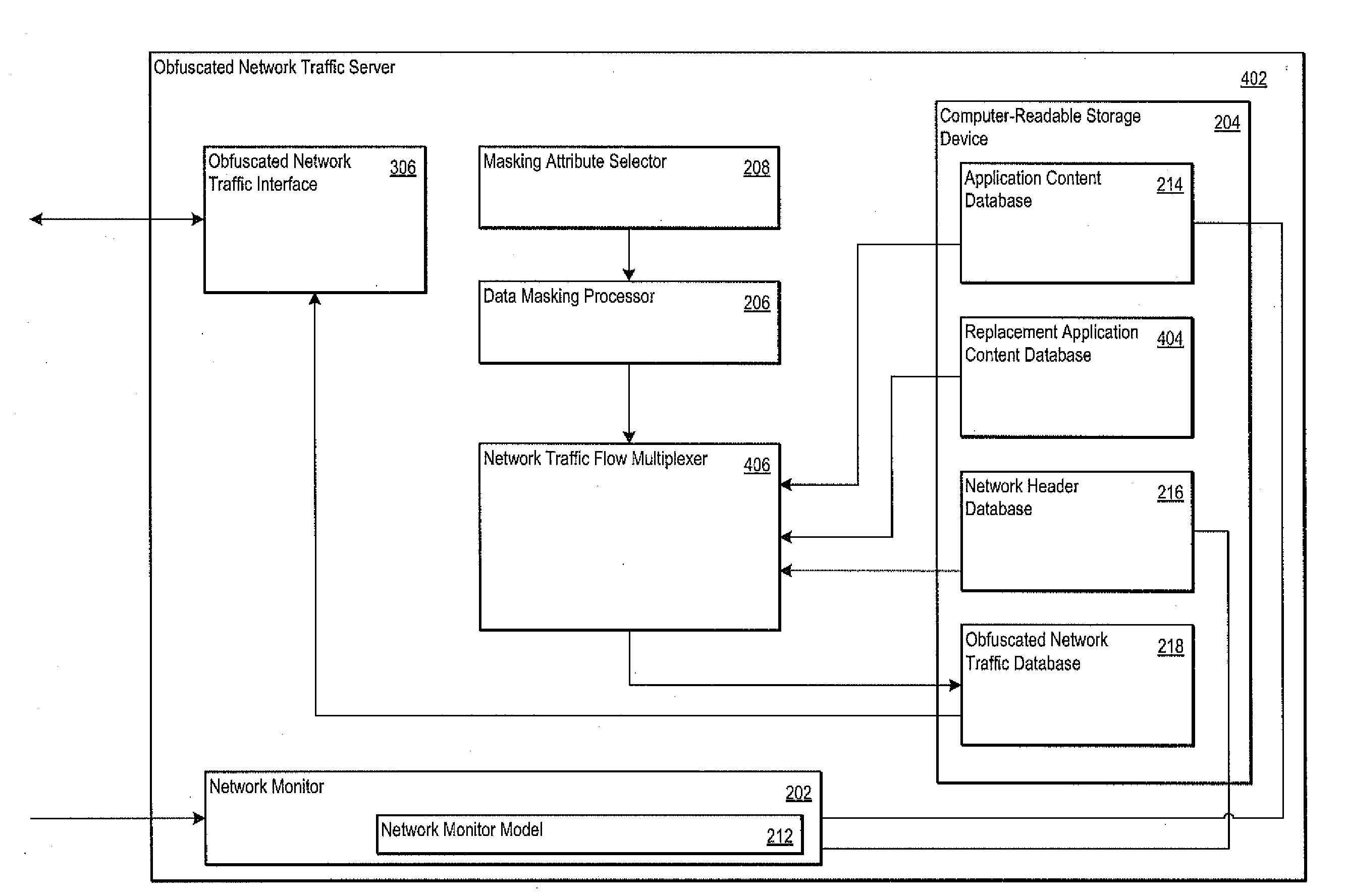
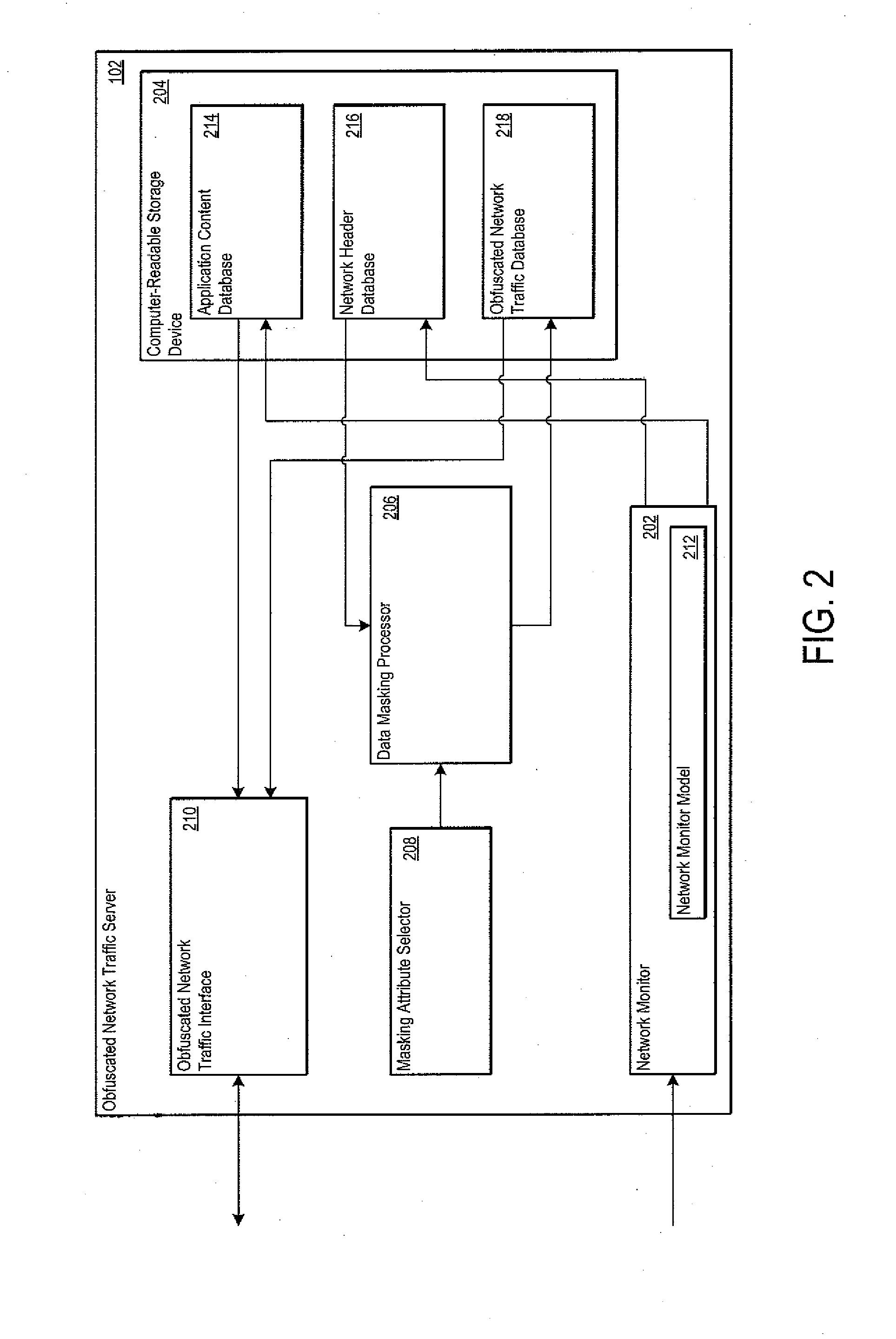
An obfuscated network traffic server is operative to generate obfuscated network traffic. The obfuscated network traffic server maintains the relationship between extracted application content and extracted network header content such that the obfuscated network traffic is indistinguishable from the monitored network traffic. The obfuscated network traffic server may include a network monitor operative to monitor network traffic and to extract application content and network header content from the monitored network traffic. The obfuscated network traffic server may also include a data masking processor operative to mask a portion of the separated application content and / or the separated network header content. The obfuscated network traffic server may further include a masking attribute selector operative to specify the attributes of the application content and / or the network header content that is to be masked.
Owner:TELCORDIA TECHNOLOGIES INC
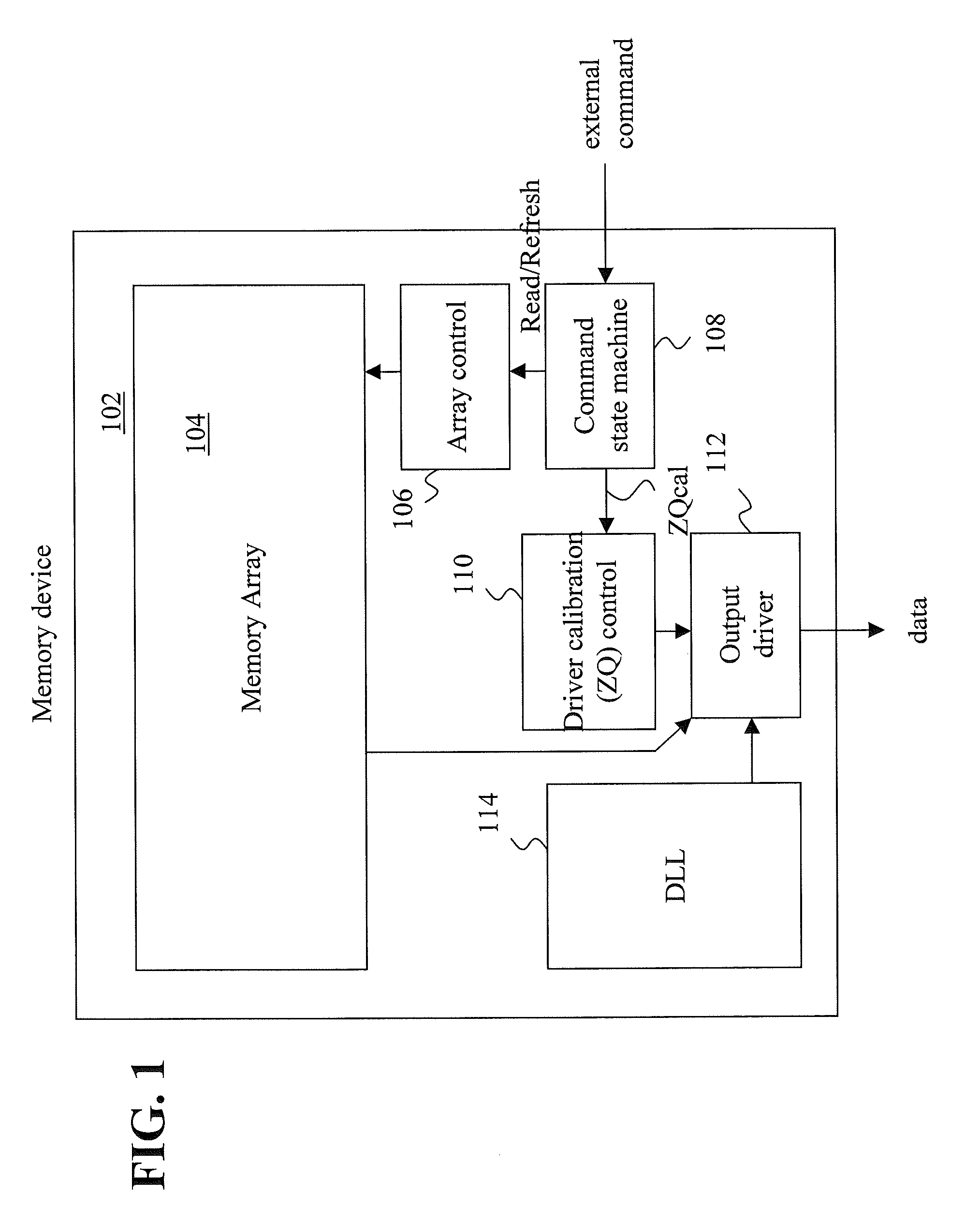
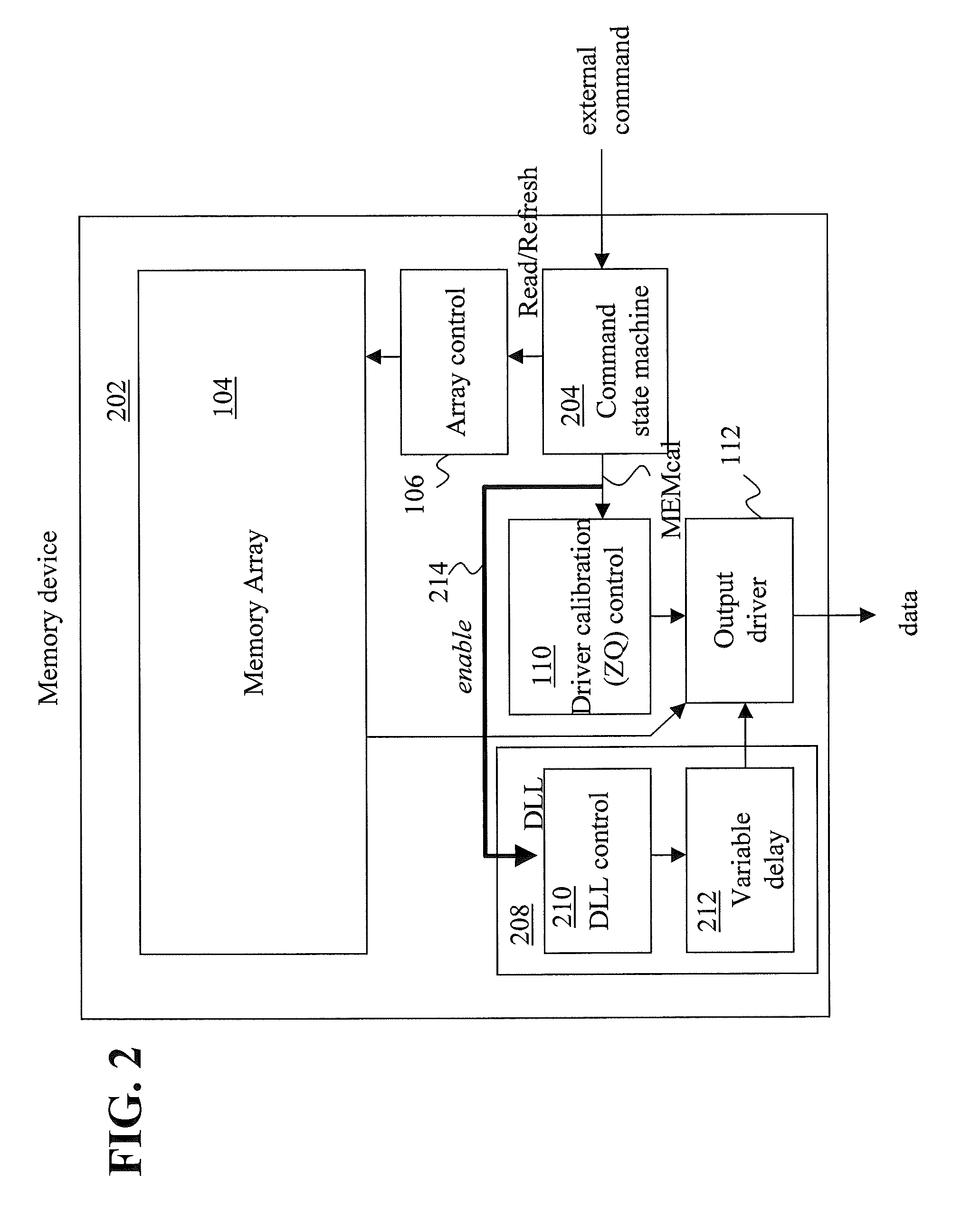
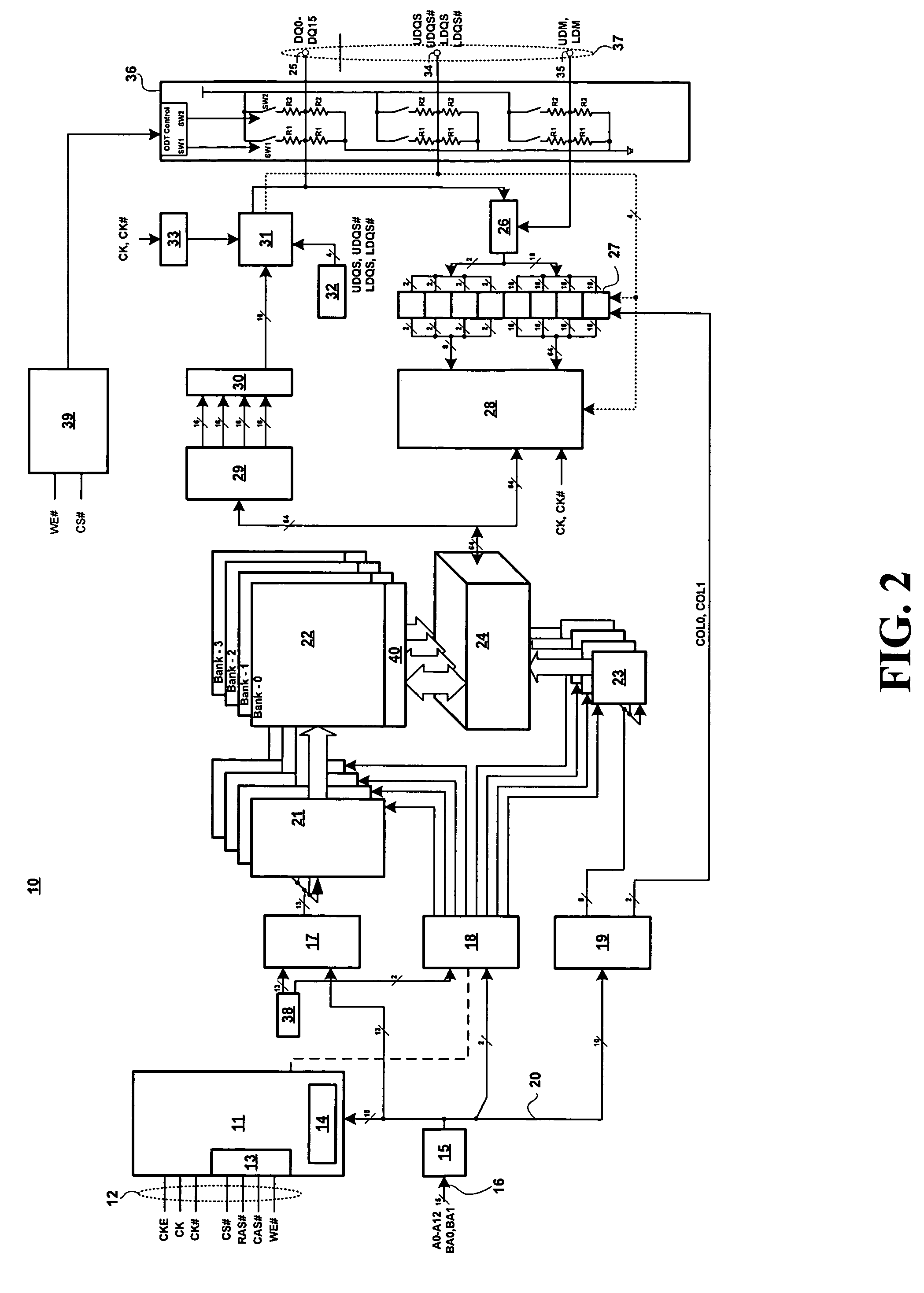
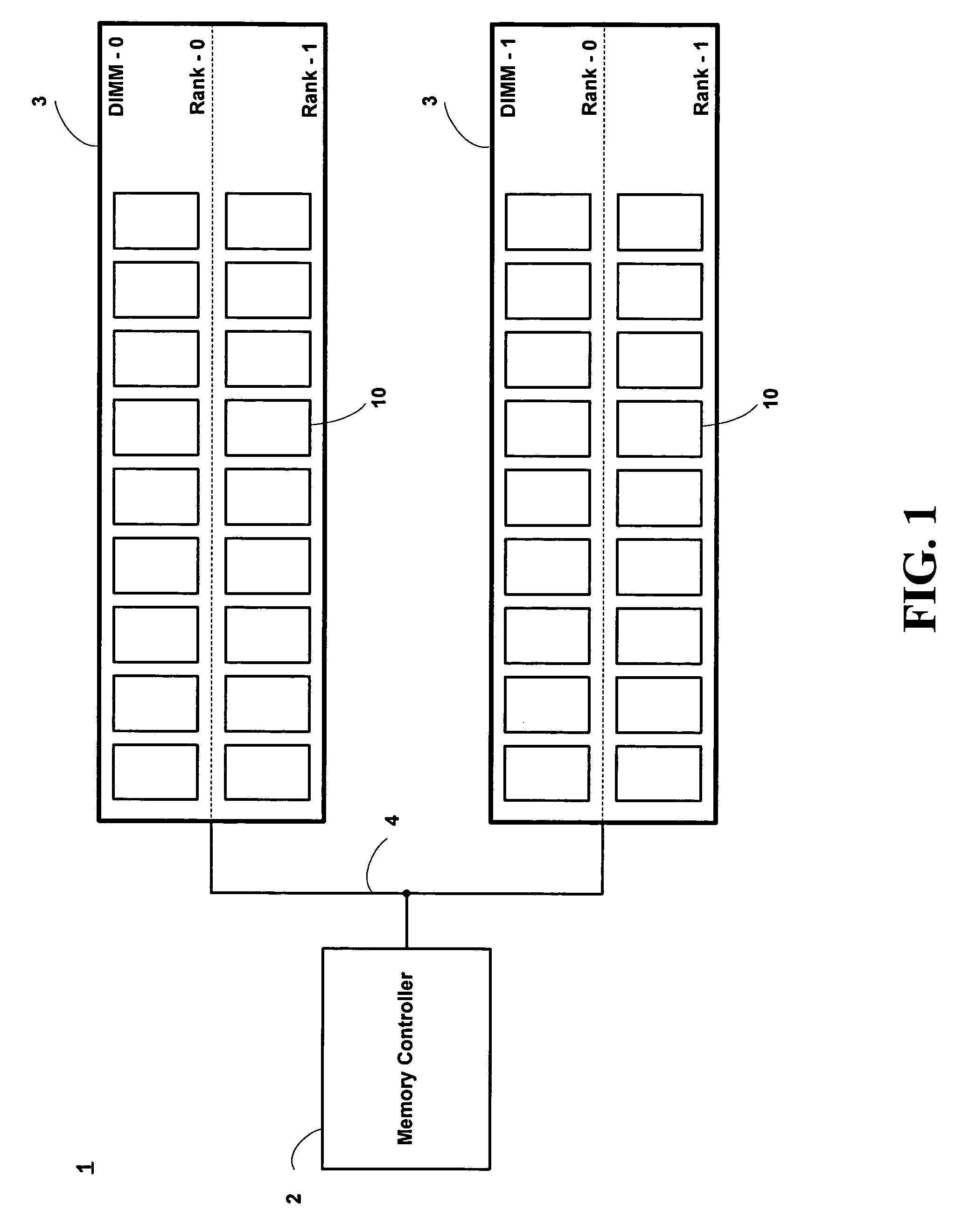
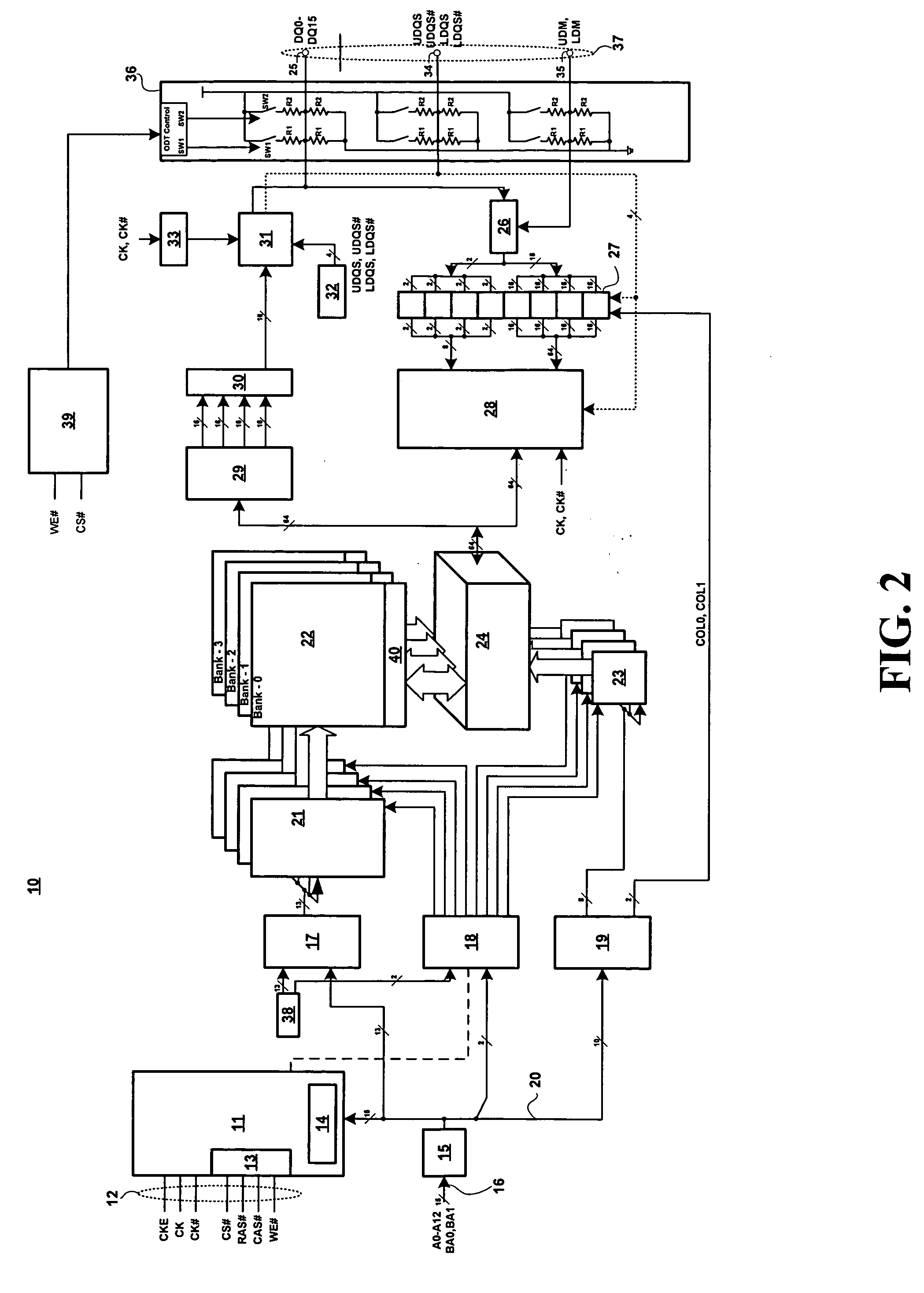
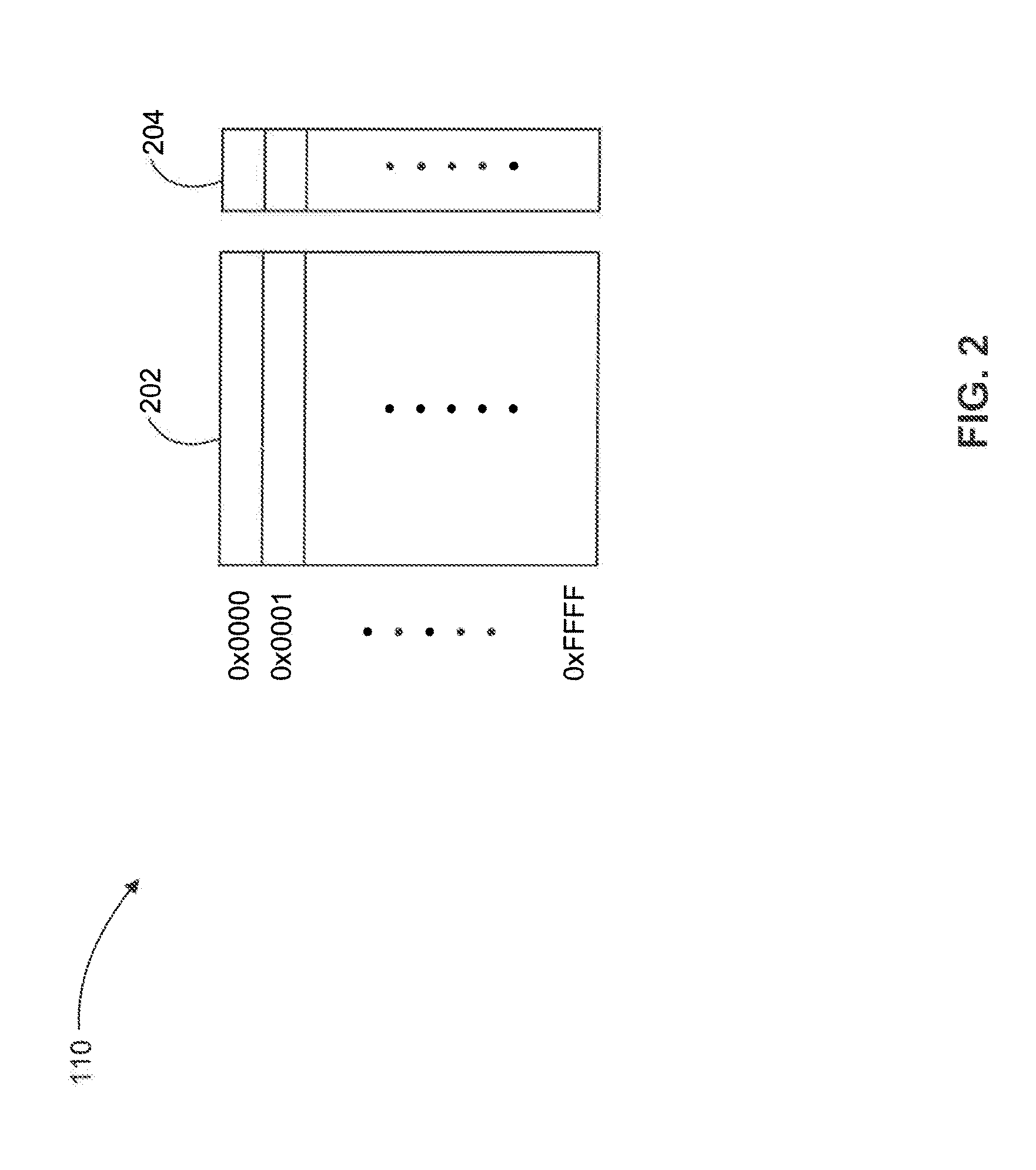
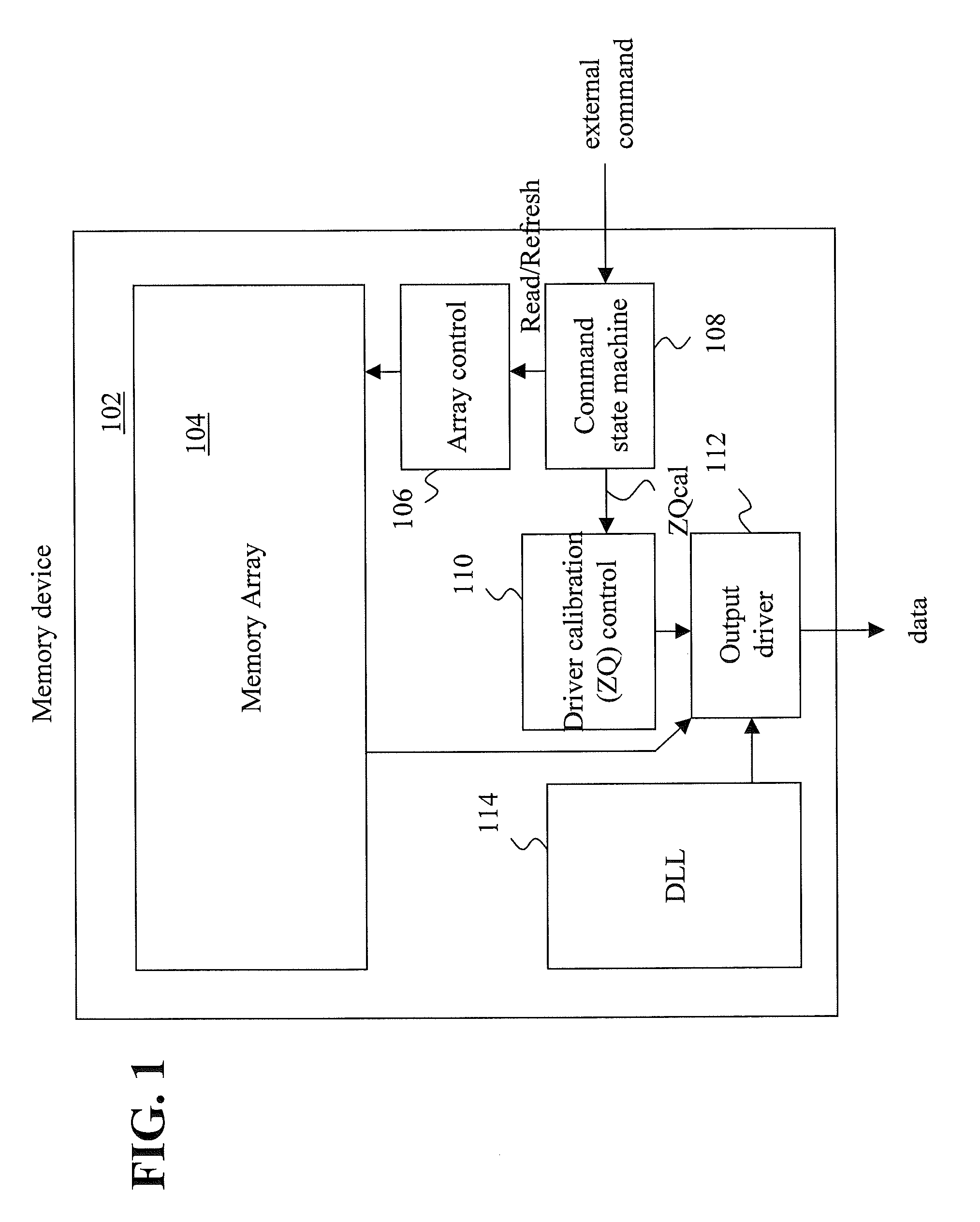
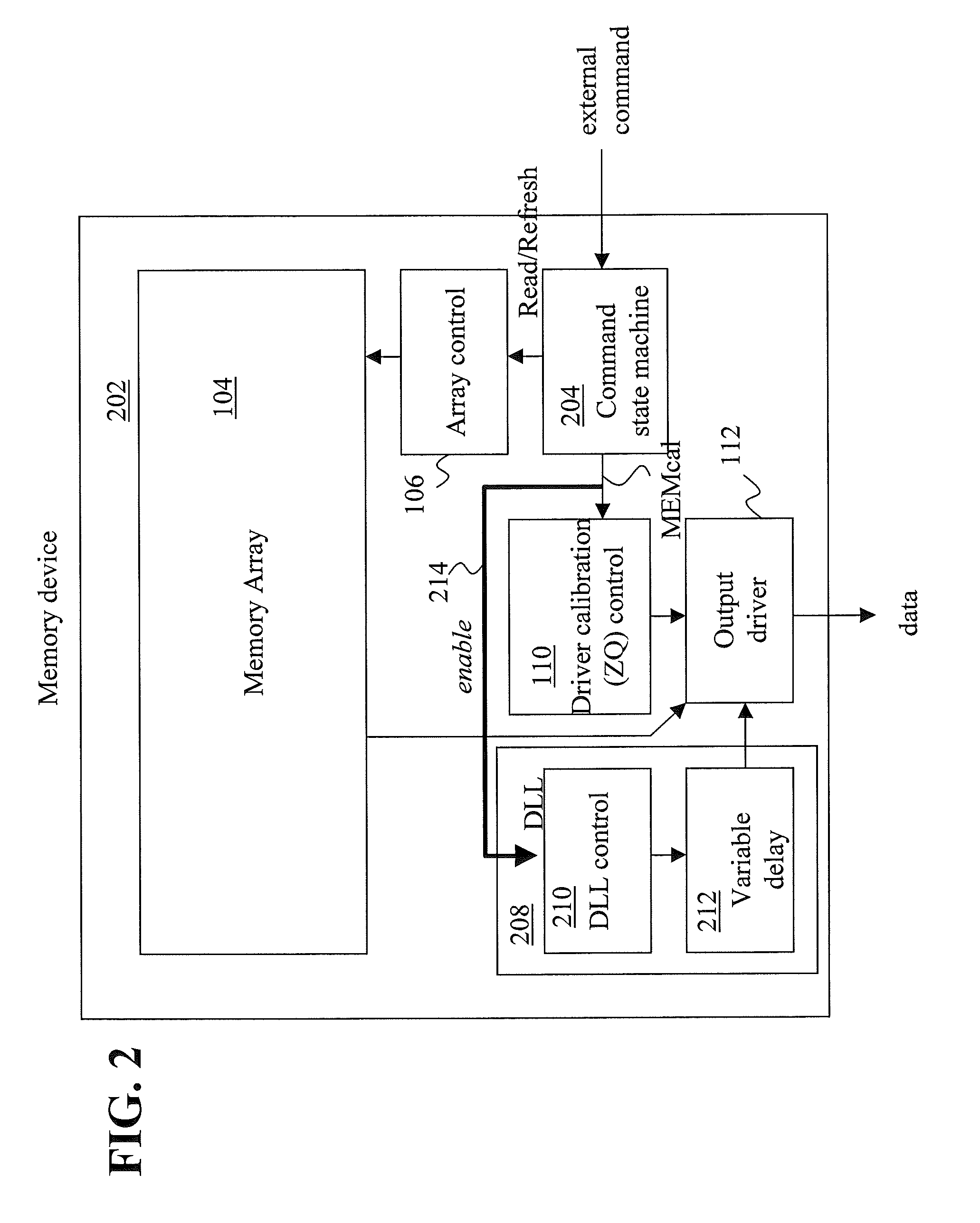
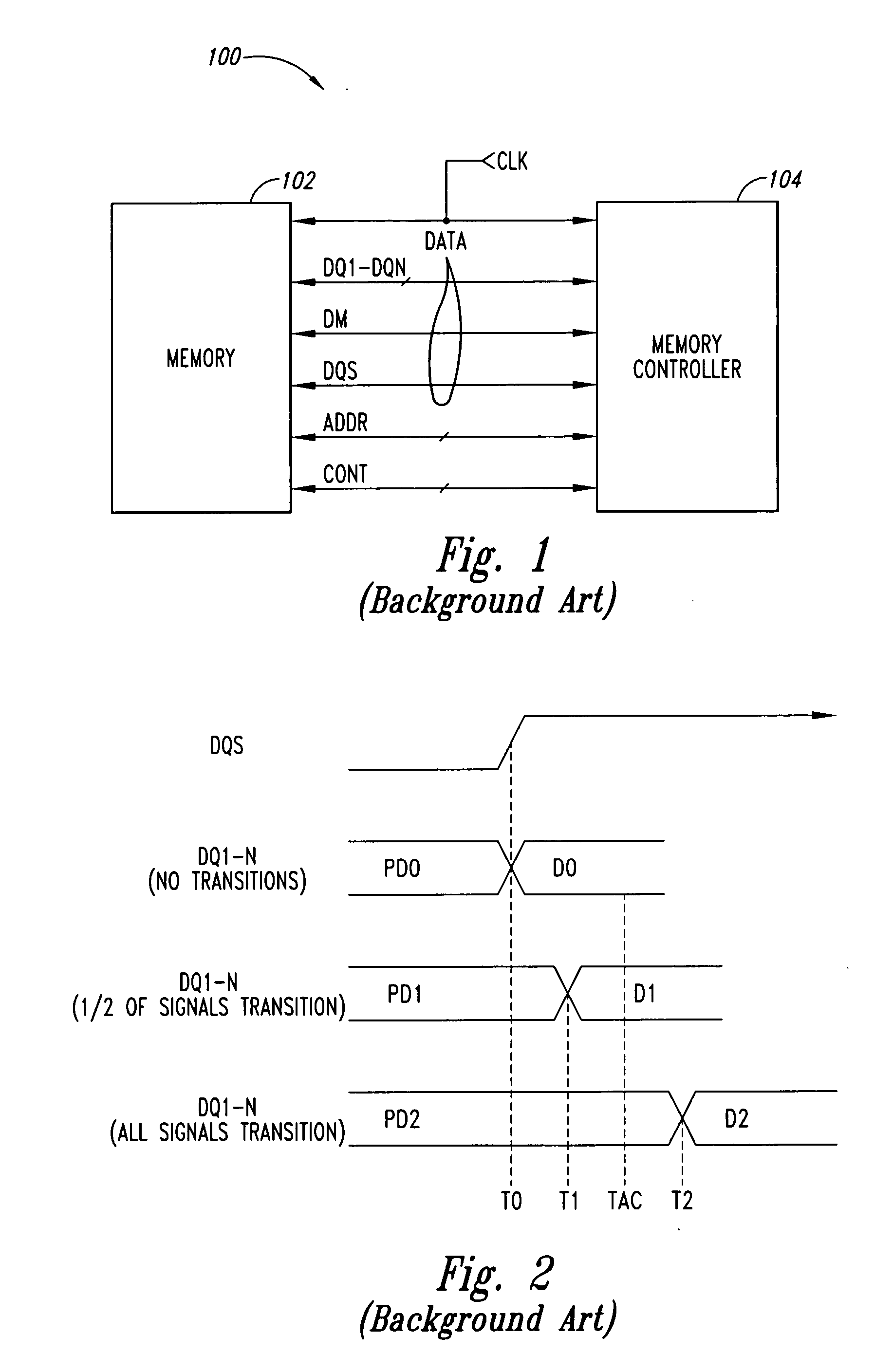
Advanced memory device having improved performance, reduced power and increased reliability
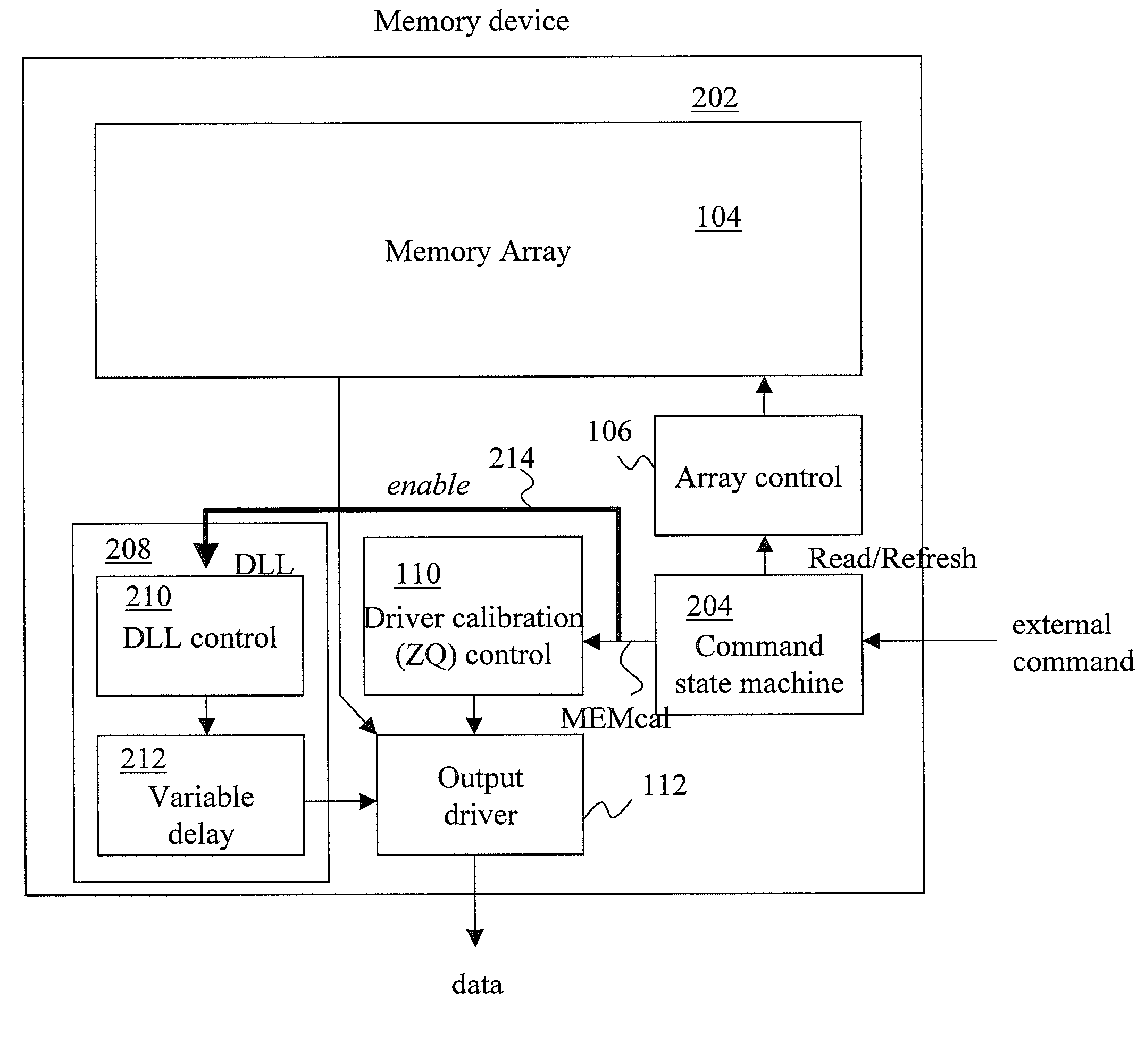
An advanced memory having improved performance, reduced power and increased reliability. A memory device includes a memory array, a receiver for receiving a command and associated data, error control coding circuitry for performing error control checking on the received command, and data masking circuitry for preventing the associated data from being written to the memory array in response to the error control coding circuitry detecting an error in the received command. Another memory device includes a programmable preamble. Another memory device includes a fast exit self-refresh mode. Another memory device includes auto refresh function that is controlled by the characteristic device. Another memory device includes an auto refresh function that is controlled by a characteristic of the memory device.
Owner:GLOBALFOUNDRIES US INC
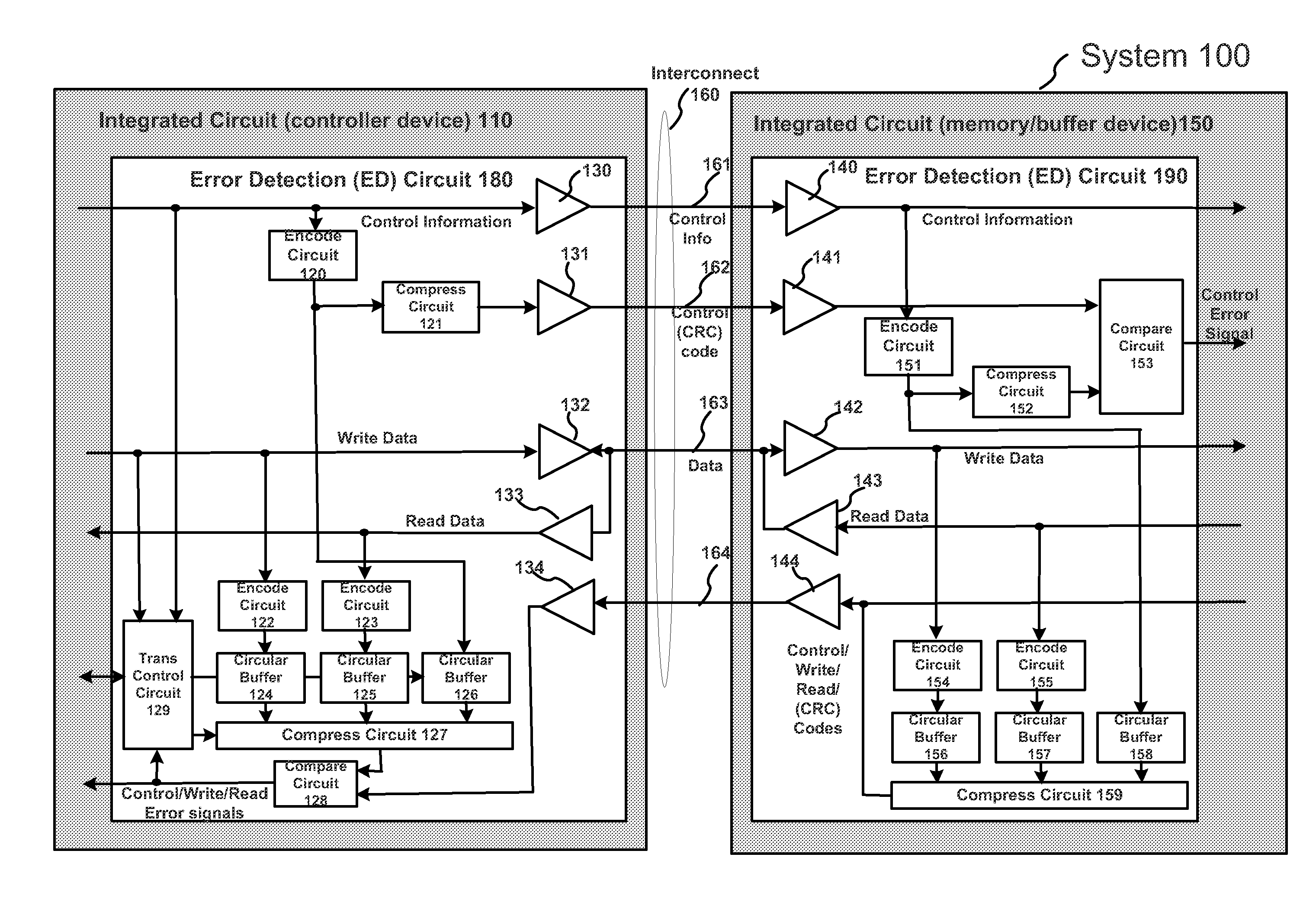
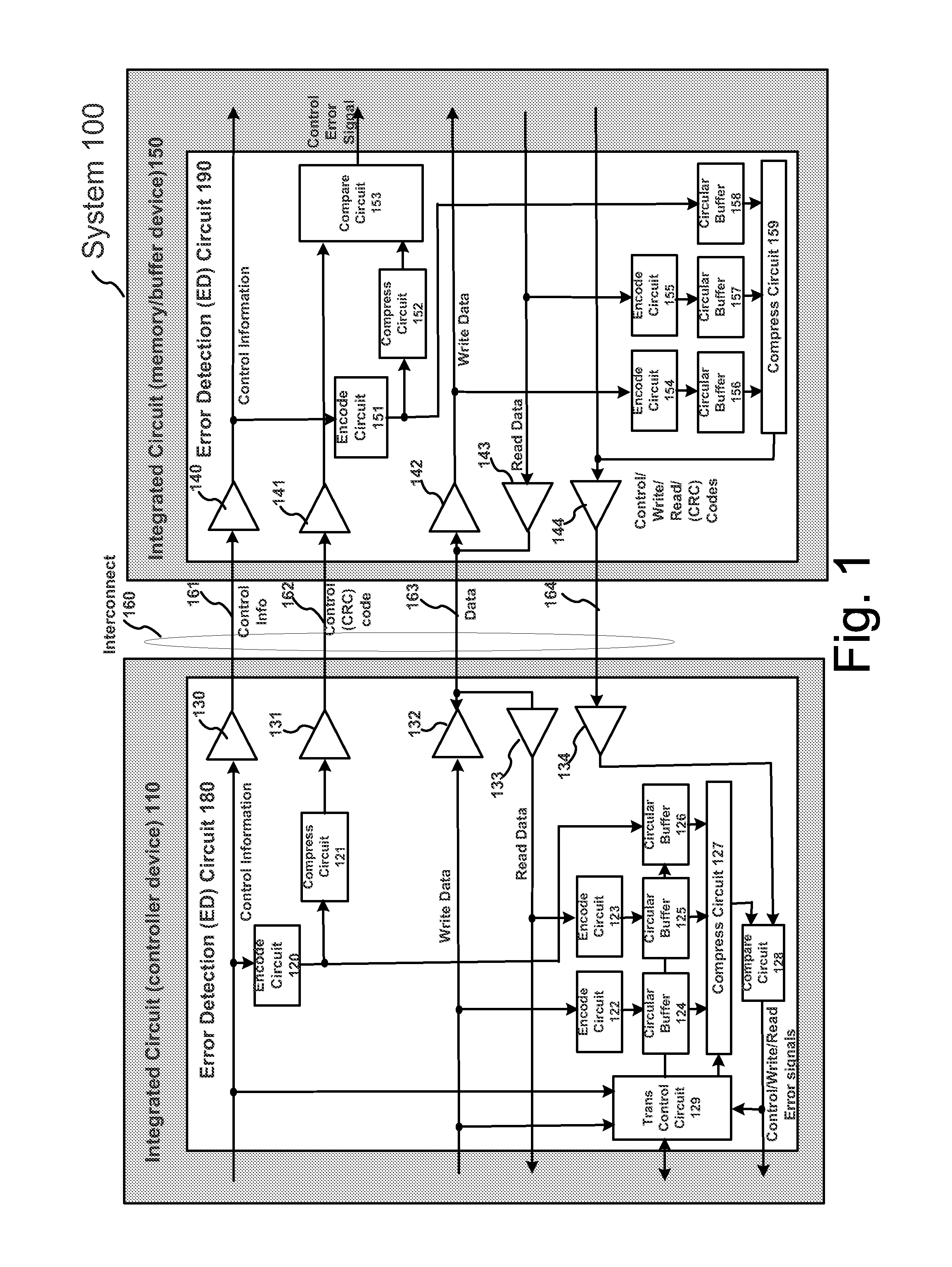
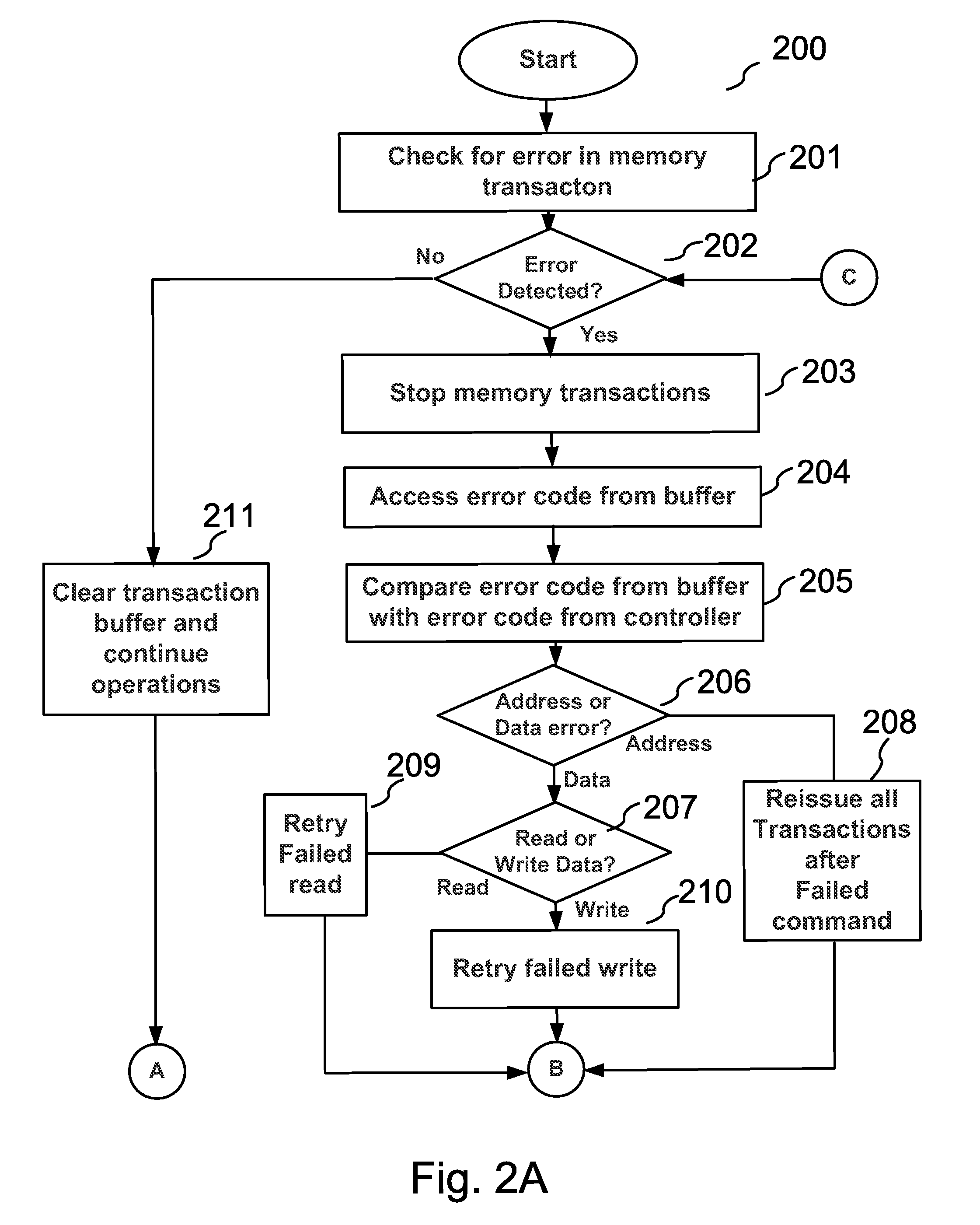
System To Detect And Identify Errors In Control Information, Read Data And/Or Write Data
An integrated circuit, such as an integrated circuit memory or buffer device, method and system, among other embodiments, generate a plurality of error codes, such as CRC codes, corresponding to control information, write data and read data transactions, respectively. The plurality of separately generated CRC codes is logged or stored in respective storage circuits, such as circular buffers. The stored plurality of CRC codes corresponding to each transaction then may be used to determine whether an error occurred during a particular transaction and thus whether a retry of the particular transaction is issued. The integrated circuit includes a compare circuit to compare a CRC code generated by the integrated circuit with a CRC code provided by a controller device. A CRC code corresponding to read data is transferred to a controller device using a data mask signal line that is not being used during a read transaction. The CRC code generated by the integrated circuit then may be compared to a CRC code generated by the controller device to determine whether an error occurred. The controller device generates and stores a plurality of CRC codes, corresponding to control information, write data and read data. The controller device then compares the CRC codes generated by the controller device with CRC codes generated and stored in the integrated circuit to determine whether an error has occurred during a particular transaction.
Owner:RAMBUS INC
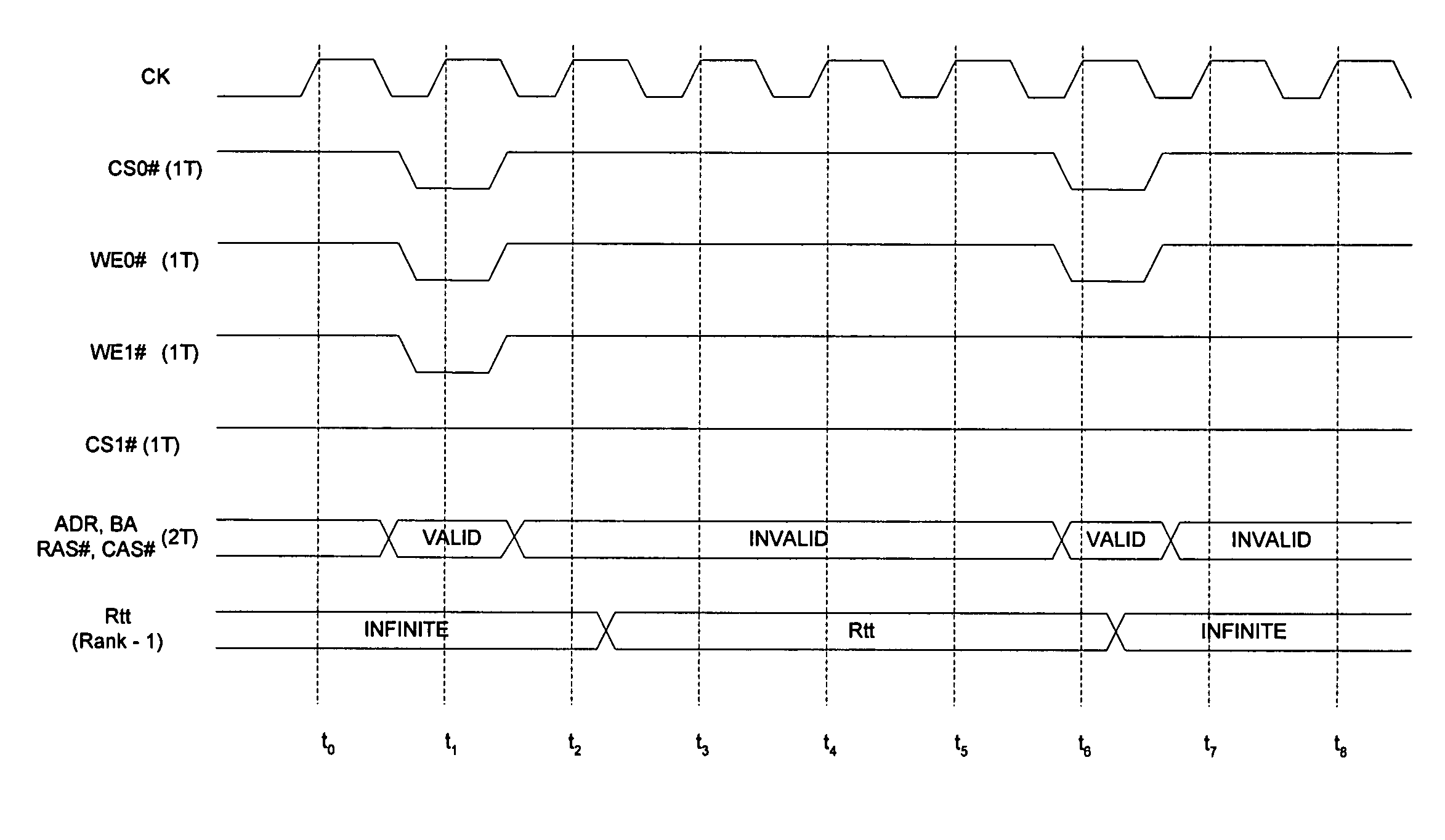
On-die termination snooping for 2T applications in a memory system implementing non-self-terminating ODT schemes
A method and apparatus for controlling the on-die termination of a memory system. The method comprises snooping a command bus in response to a first plurality of command signals clocked at 1T and enabling the on-die termination in response to a second plurality of command signals clocked at 2T and the first plurality of command signals. The apparatus may be a memory device comprising a memory array responsive to a plurality of command signals, a data bus having at least one of a data pad, a data strobe output pad, and an input data mask pad, an activation circuit responsive to certain of the plurality of command signals and operable to produce a control signal, and a termination circuit responsive to the control signal and operable to apply an effective resistance to at least one of the data pad, the data strobe output pad, and the input data mask pad.
Owner:MICRON TECH INC
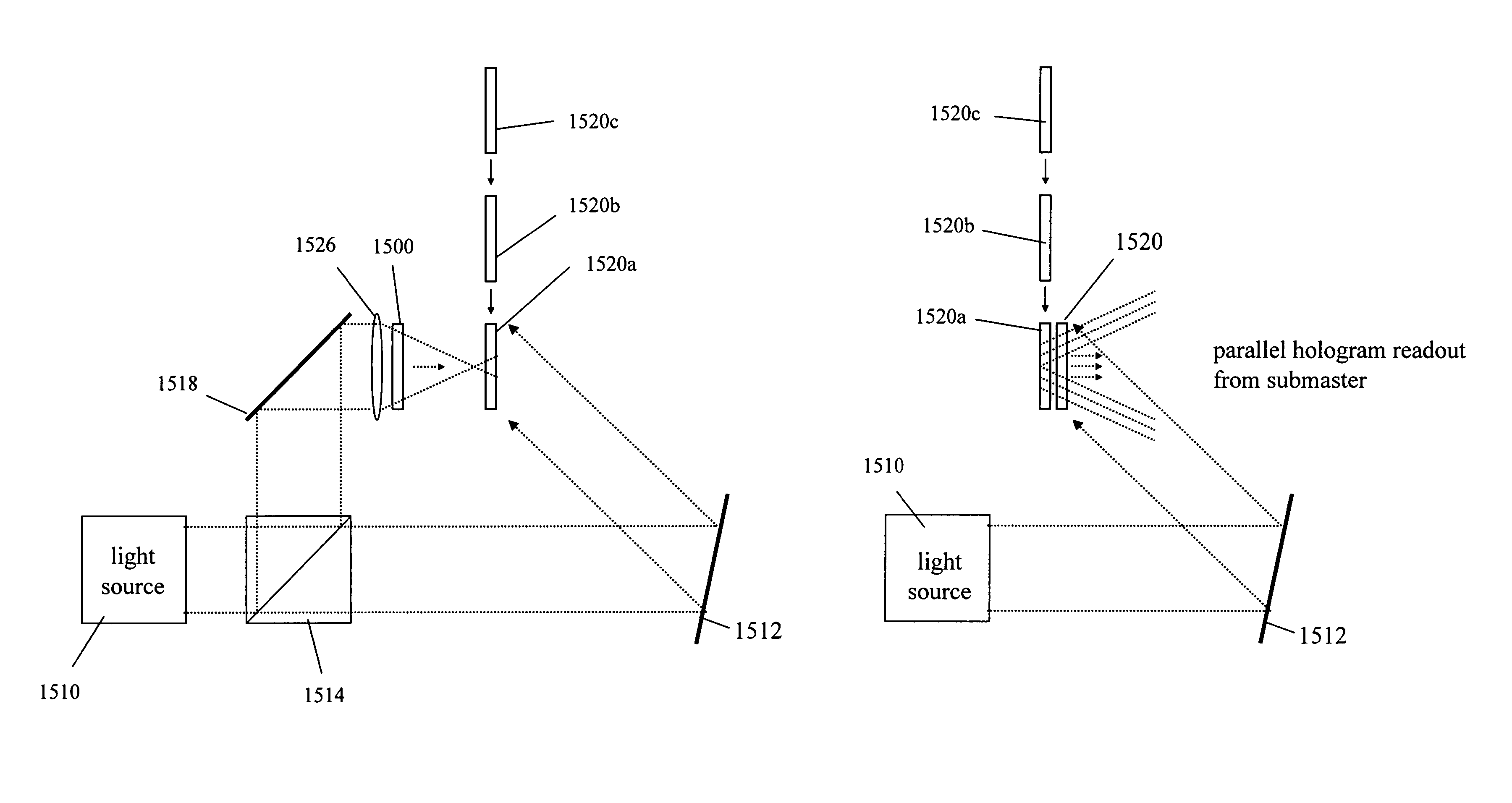
Methods and systems for recording to holographic storage media
InactiveUS8786923B2Increase storage capacityOptical re-recordingInformation arrangementHolographic storageInformation layer
According to one aspect and example, a method for recording holographic media and / or holographic master data masks includes recording at least a first hologram or information layer with a first holographic medium (e.g., a “submaster”) and recording at least a second information layer with a second holographic medium (e.g., a second “submaster”). The first information layer and the second information layer from the first and second holographic media are then sequentially reconstructed and stored with a single holographic master medium (e.g., a “master”). The holographic master may then be used to record the stored first and second information layers into additional holographic media, for example, into HROM devices or the like.
Owner:AKONIA HOLOGRAPHICS
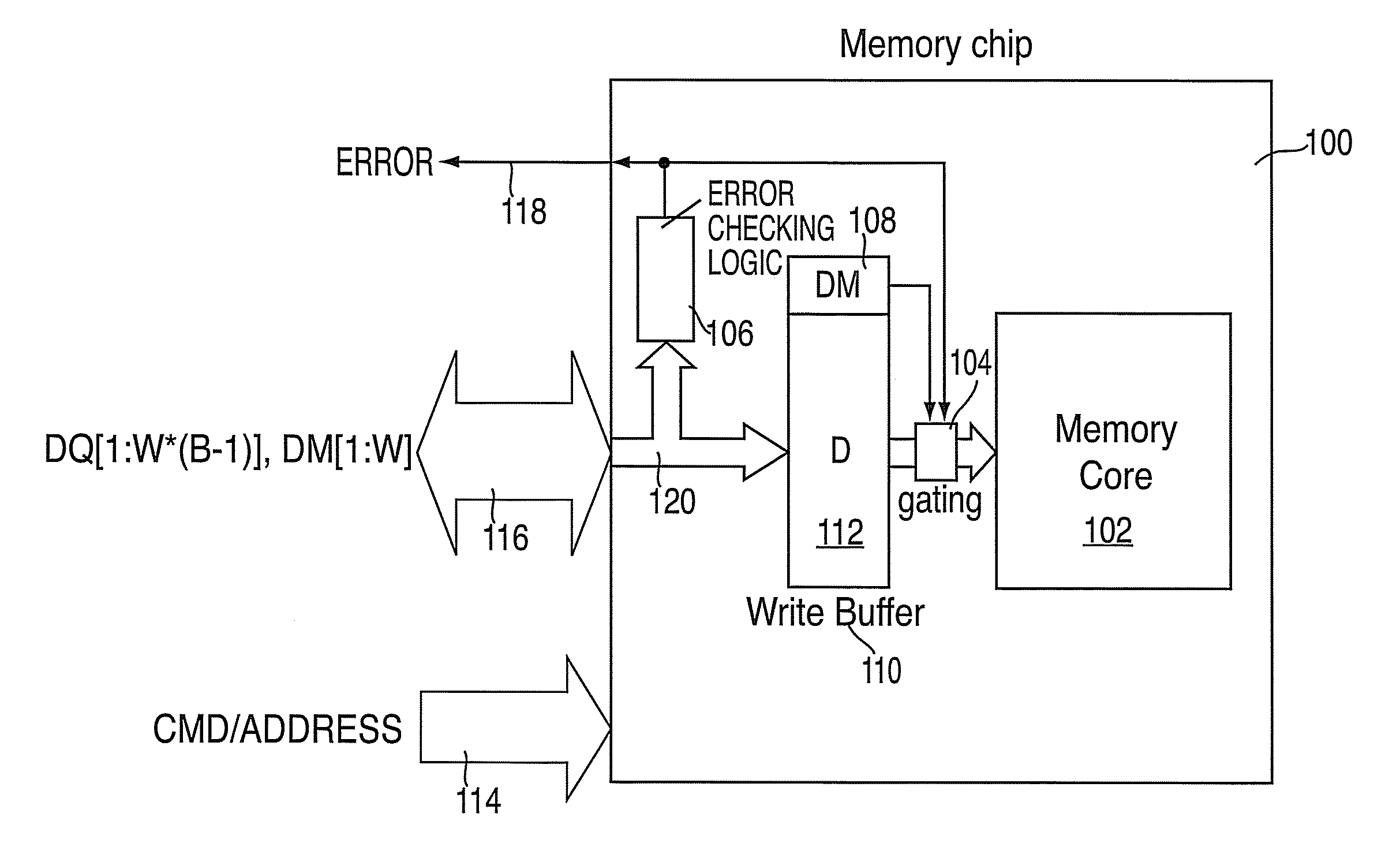
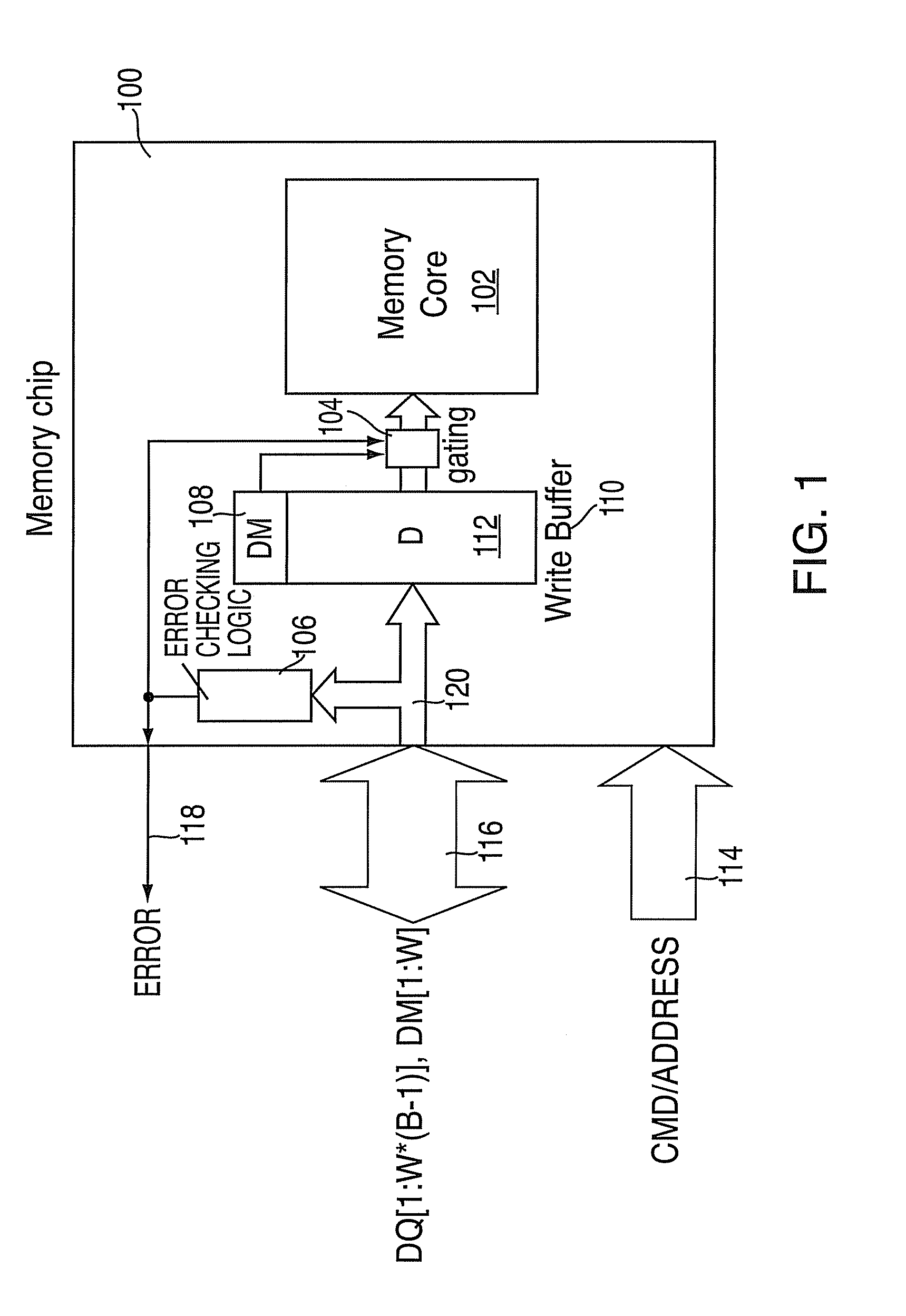
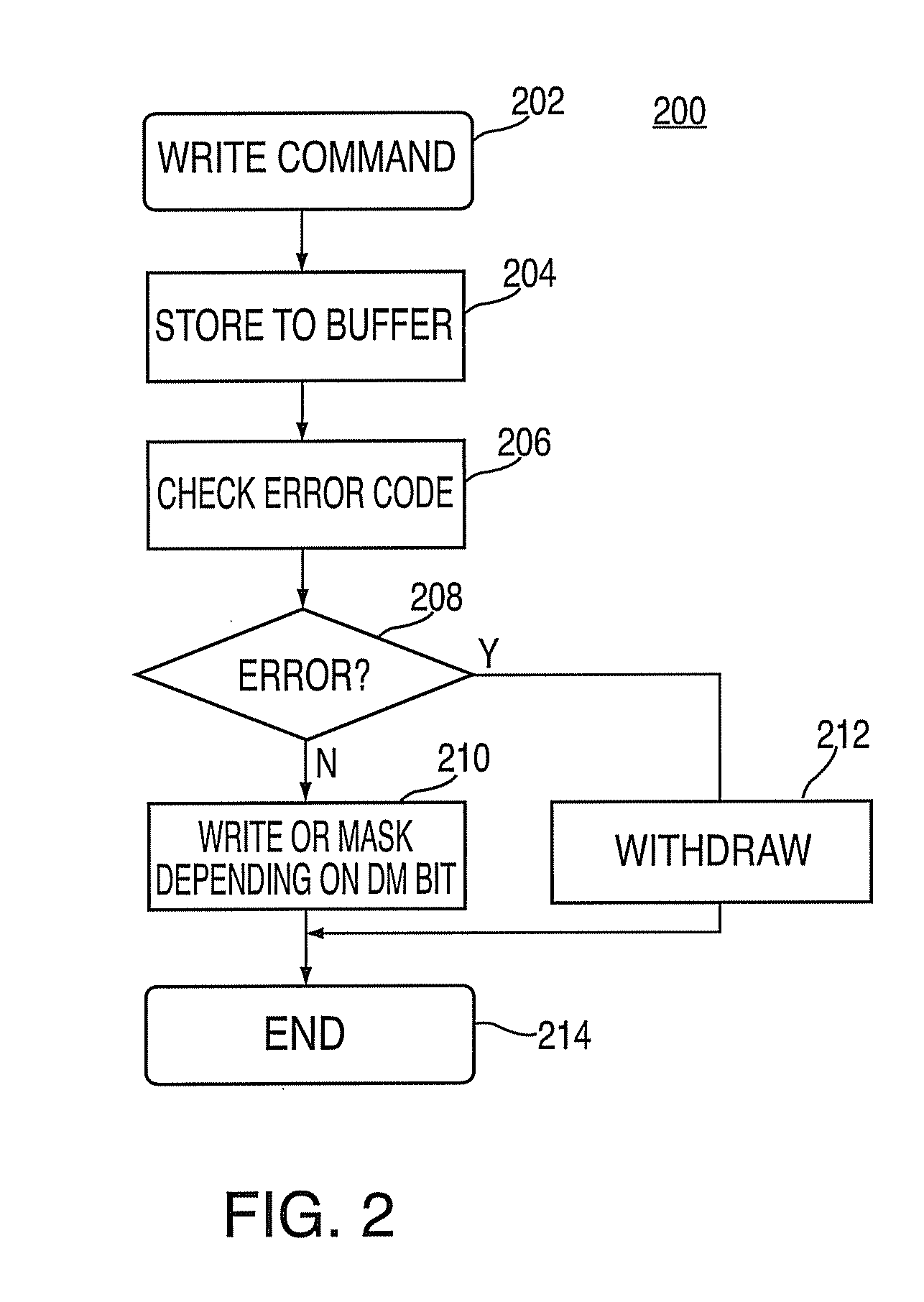
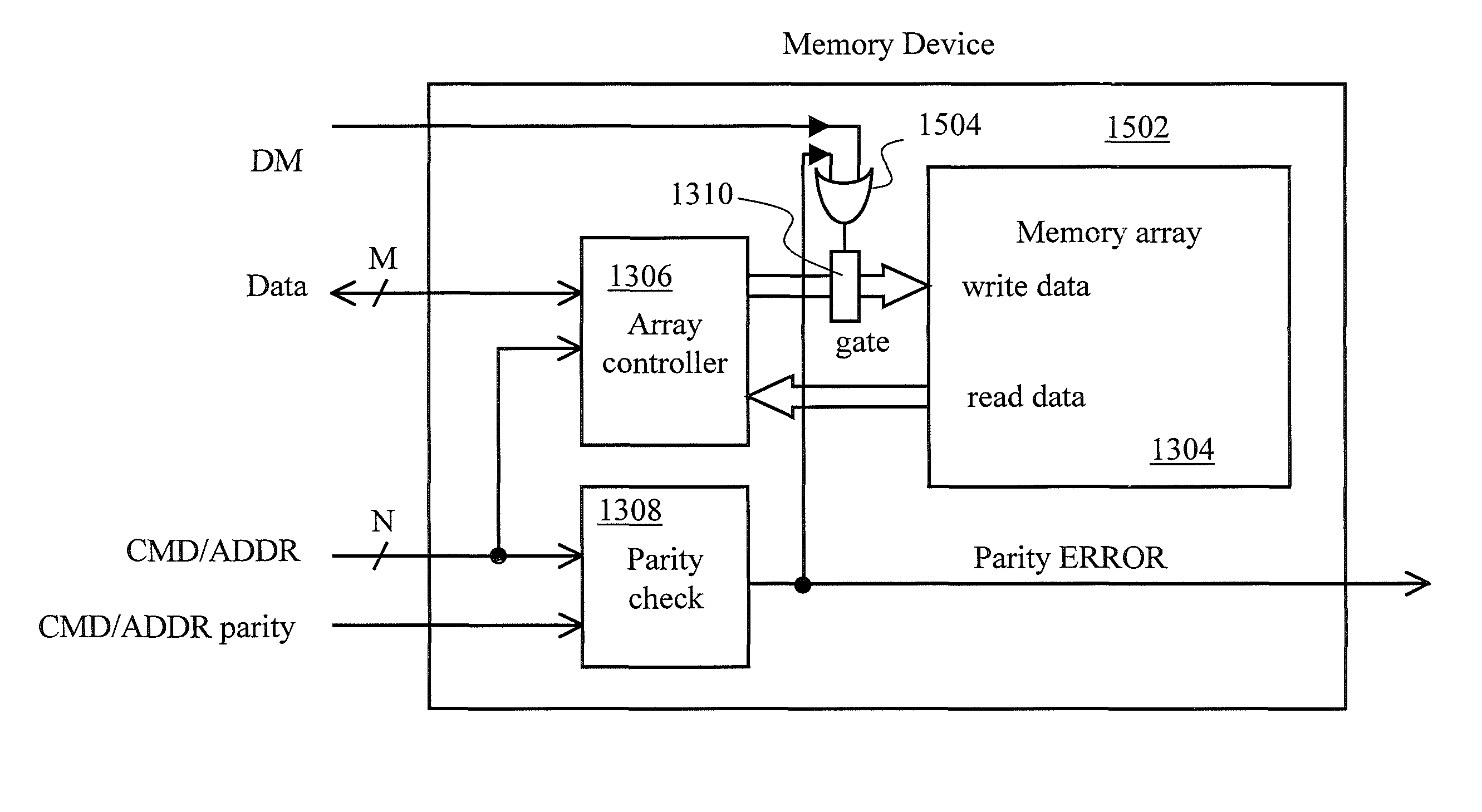
Apparatus, system and method for providing error protection for data-masking bits
An apparatus, system, and method for providing error protection for data-masking bits in a memory device of a memory system are provided. The memory device includes a memory core to store data, and a data interface to receive the data and data-masking bits associated with a write command. The memory device also includes a gating block to control writing the data to the memory core, where the writing of the data to the memory core is inhibited upon detecting an error with one or more of the data-masking bits.
Owner:IBM CORP
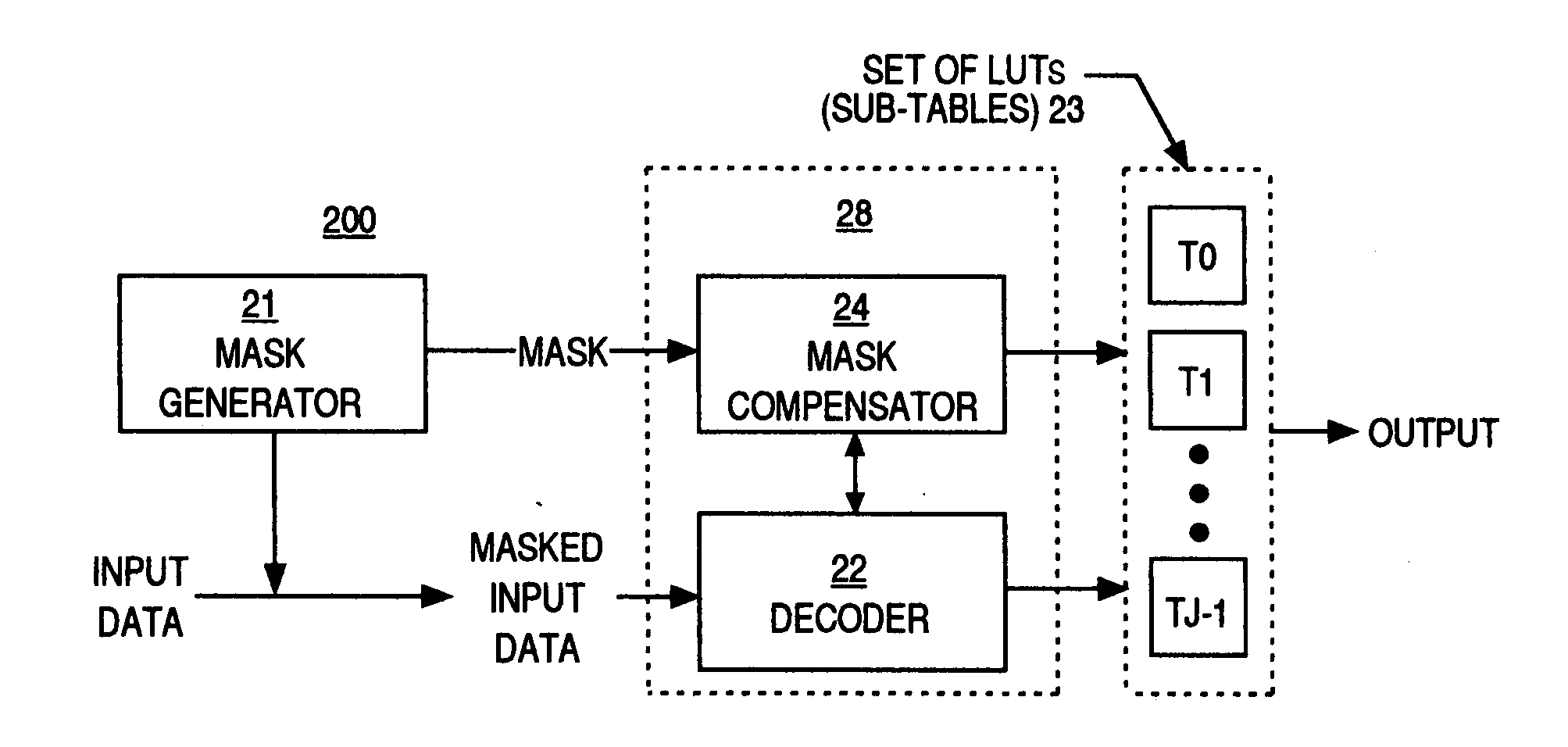
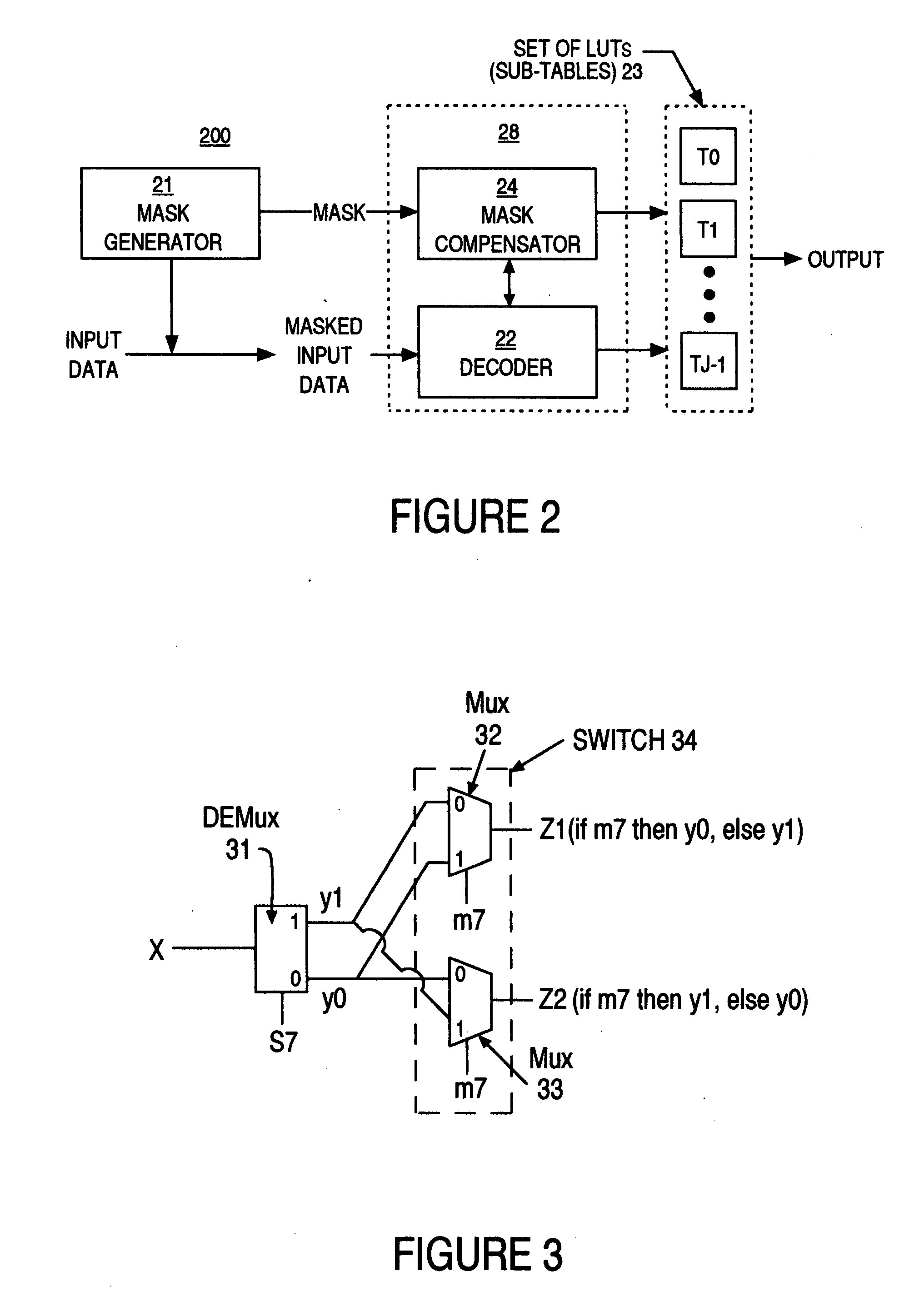
Selection of a lookup table with data masked with a combination of an additive and multiplicative mask
Processing of masked data using multiple lookup tables (LUTs), or sub-tables, is described. For each input value, an appropriate sub-table provides an output value that is the result of a non-linear transformation (e.g., byte substitution) applied to the input value. An additive mask can be applied to the input data. A transformation can be applied to the masked input data to transform the additive mask into a multiplicative-additive mask. Selected bits of the masked input data and the bits in the additive component of the multiplicative-additive mask can be used in combination to select one of the sub-tables. An entry in the selected sub-table, corresponding to a transformed version of the input data, can then be identified.
Owner:CYPRESS SEMICON CORP
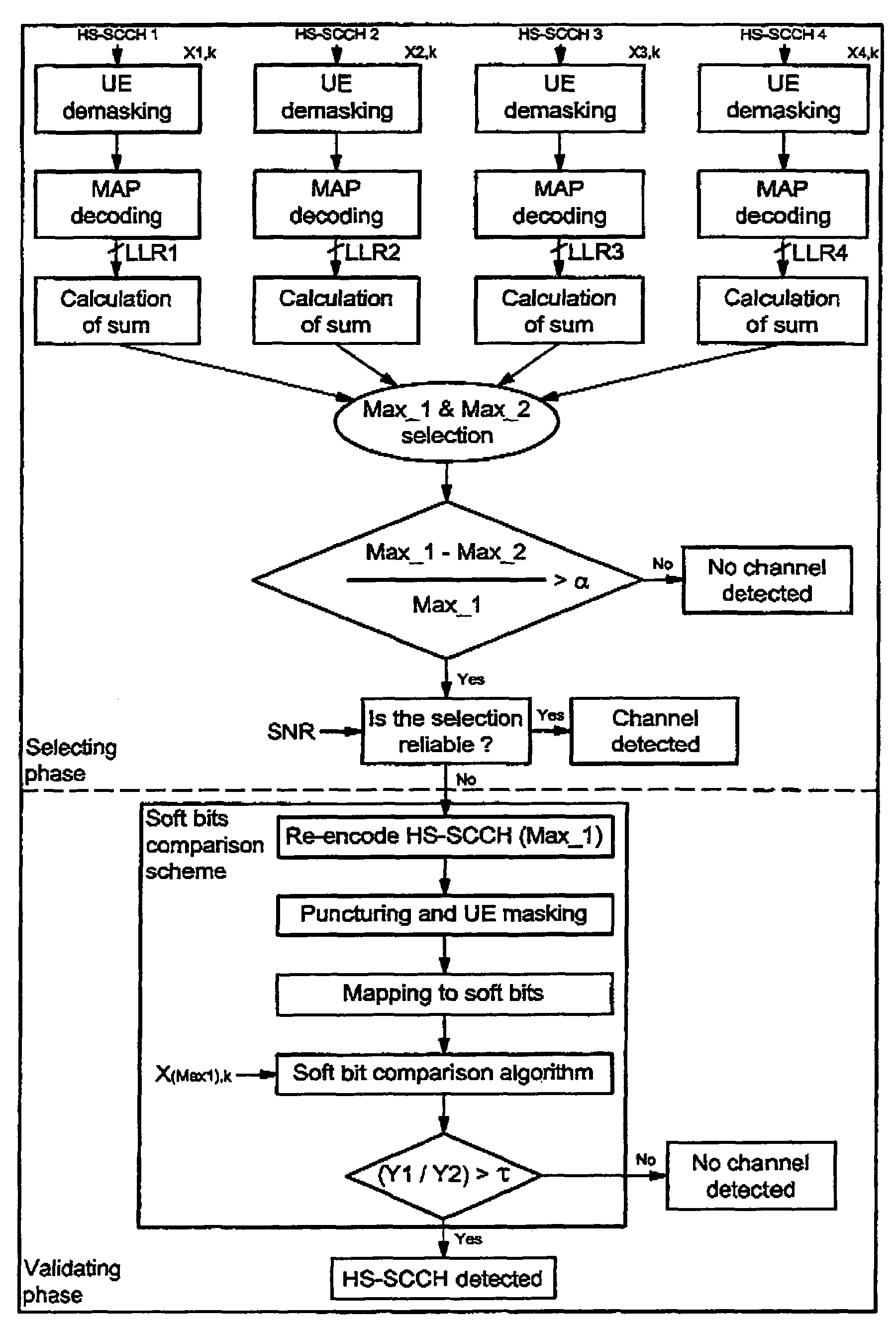
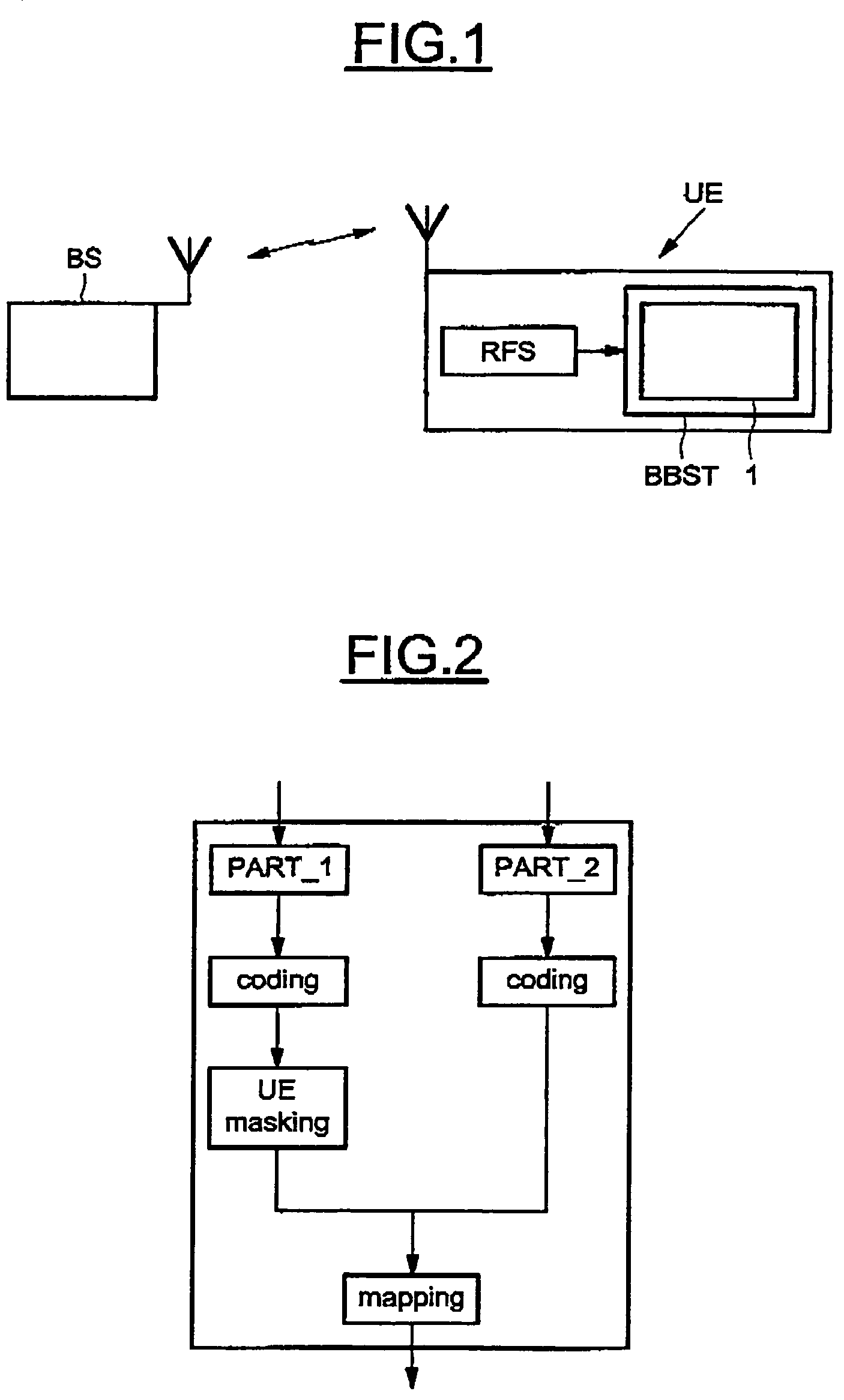
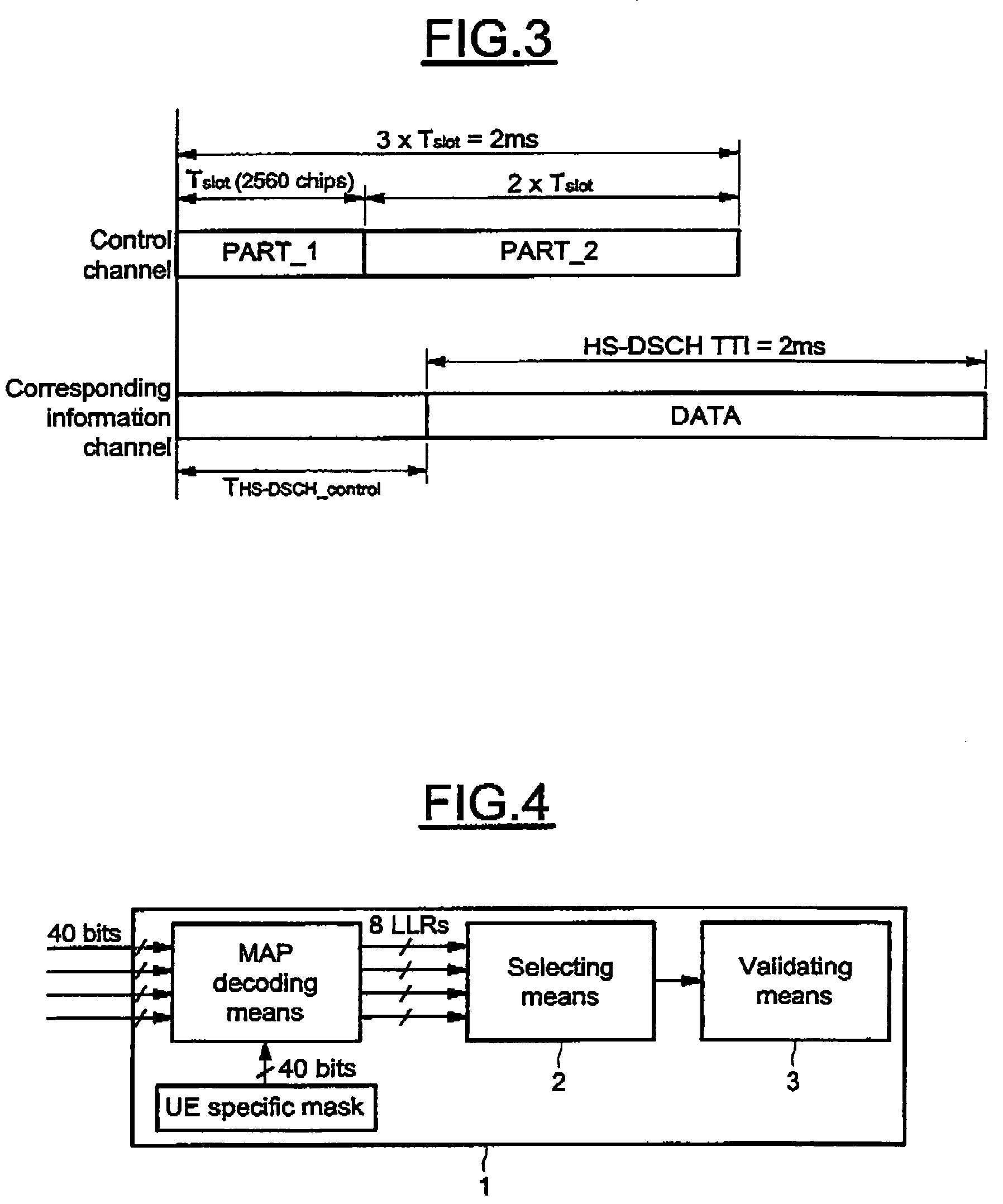
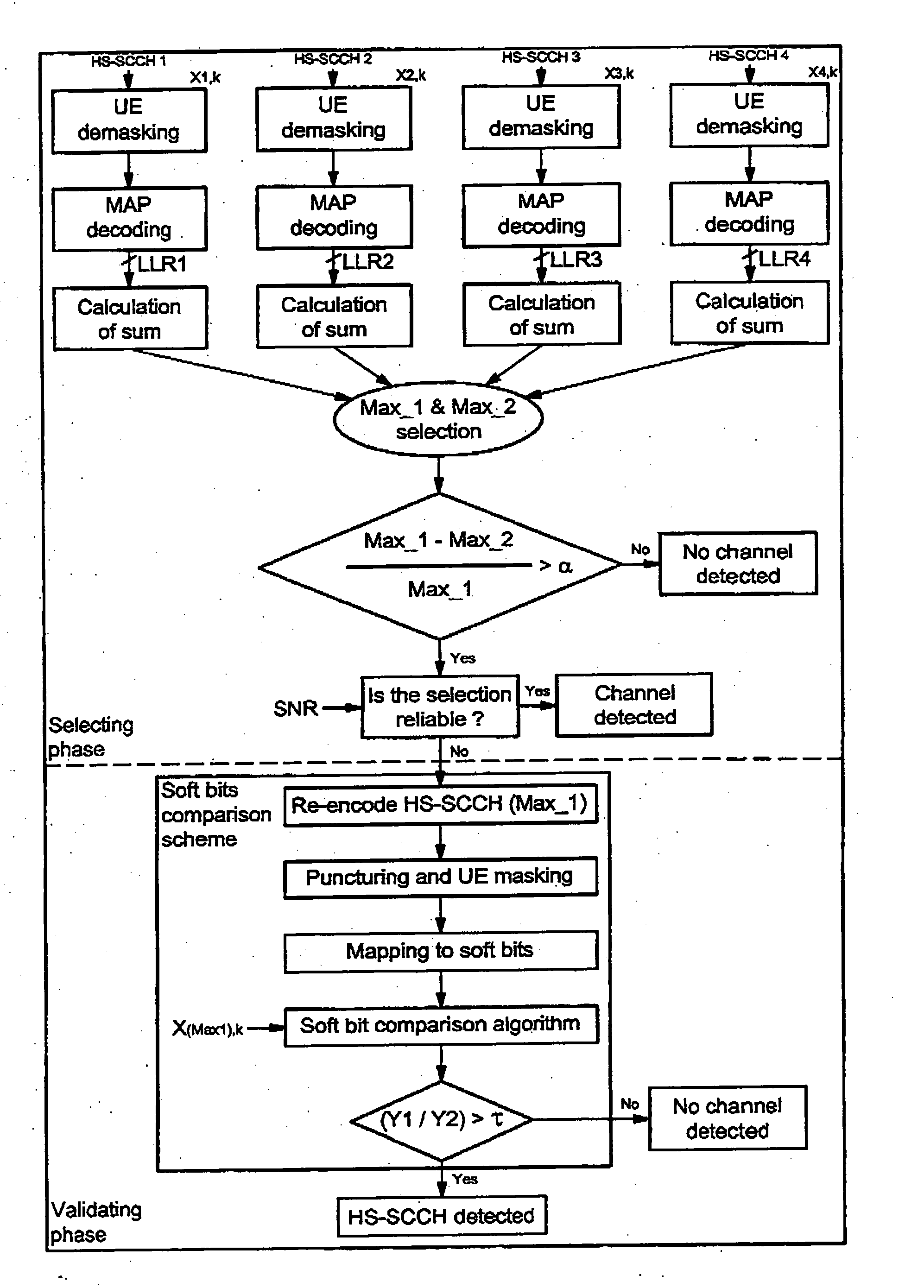
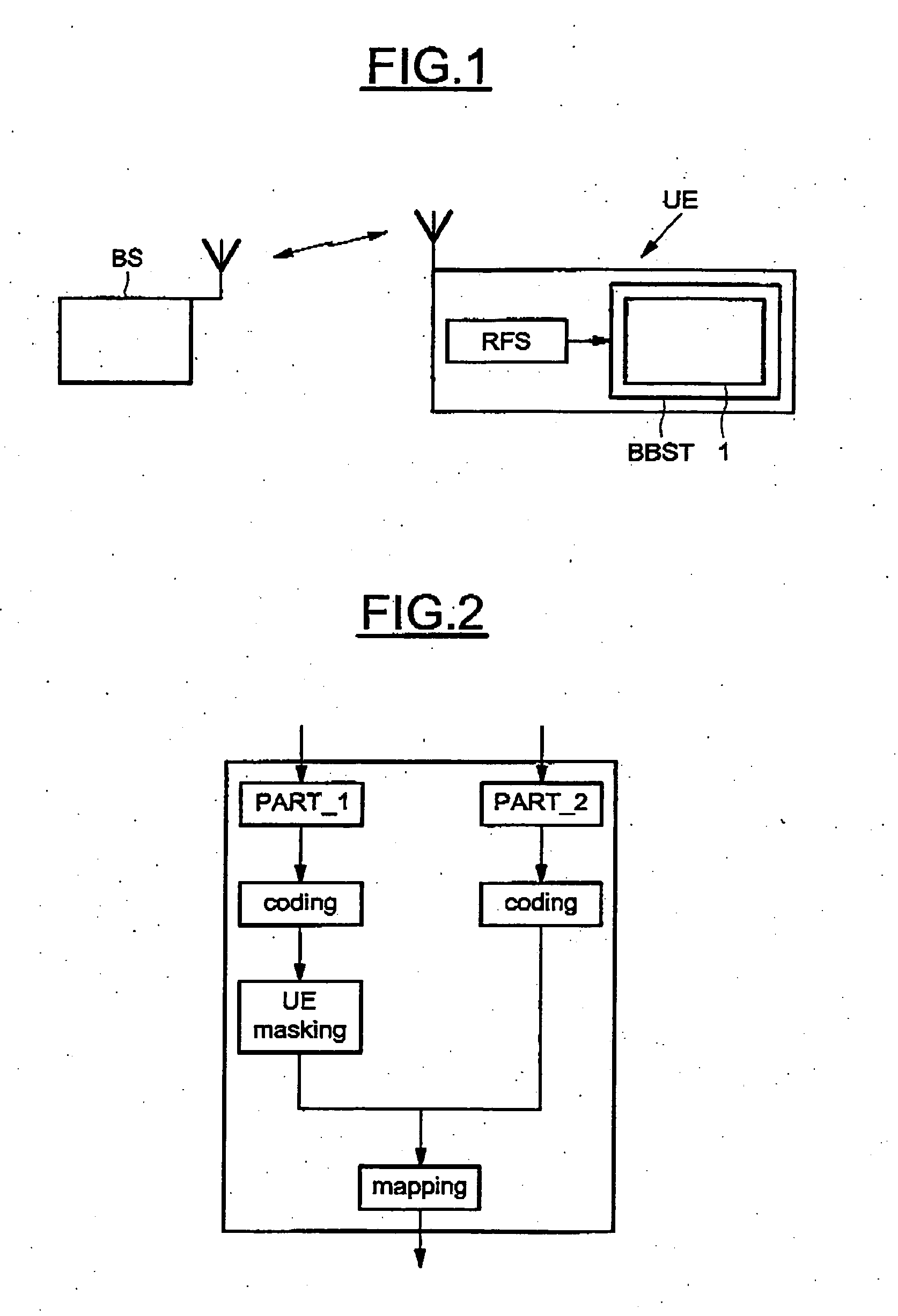
Method and system for blindly detecting a discontinuously transmitted shared channel, in particular blind high speed shared control channels detection
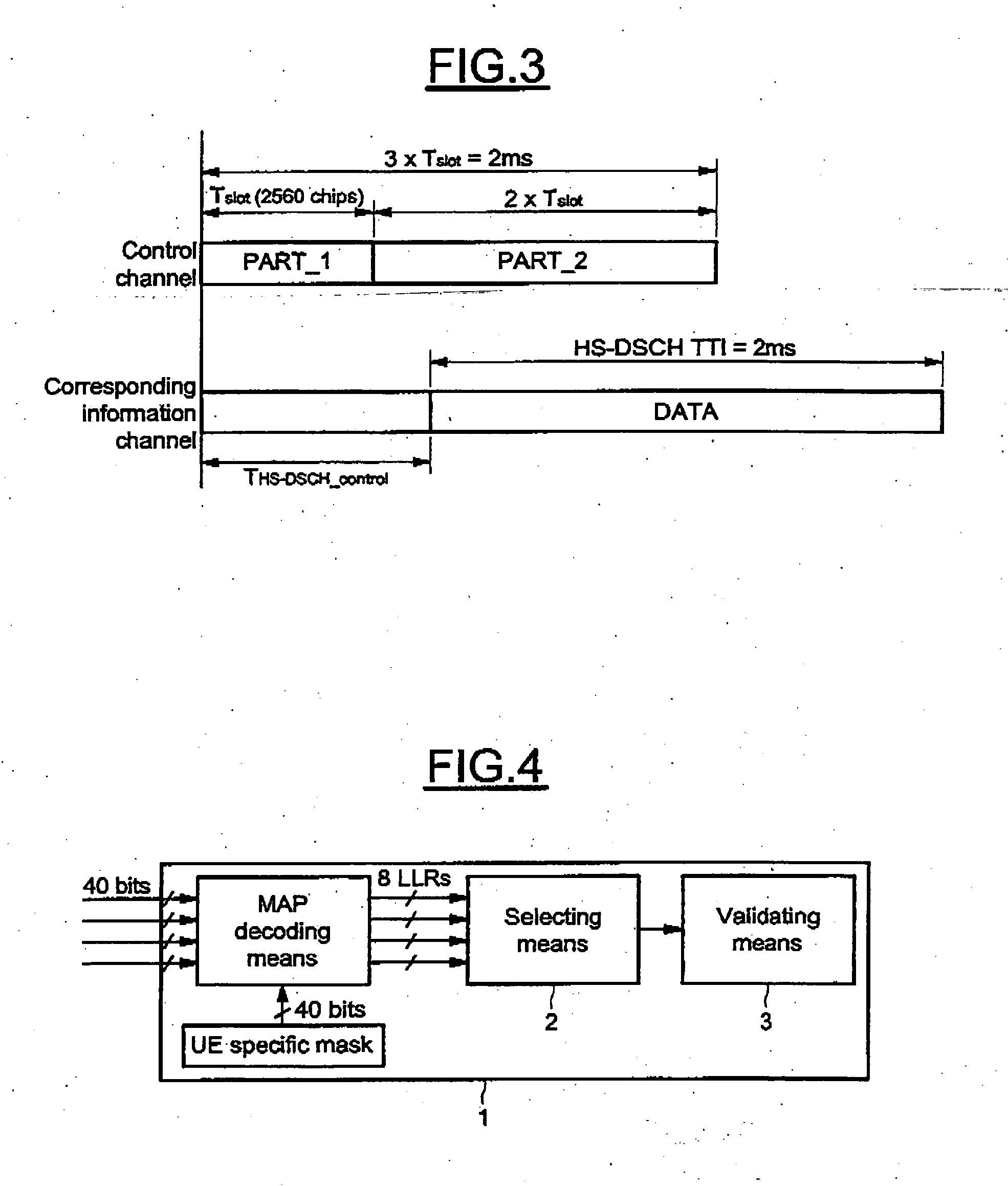
InactiveUS7688915B2Reduce loss rateReduce probabilityOther decoding techniquesCode conversionDigital dataControl channel
A method for detecting an eventual channel intended to a designated user equipment among n channels received by the designated user equipment during a given duration, each channel received during the duration carrying encoded data masked with an identifier associated to a user equipment. The method includes a selecting phase having a demasking step demasking the received masked encoded data of each channel with the identifier of the designated user equipment, a decoding step decoding the demasked encoded data of each channel to obtain a set of digital decoded data for each channel, a calculating step calculating, from each set of digital decoded data, a global information representative of a confidence in digital data received on the physical channel, and a detecting step detecting the channel from all the global information.
Owner:SNO WAY INT +1
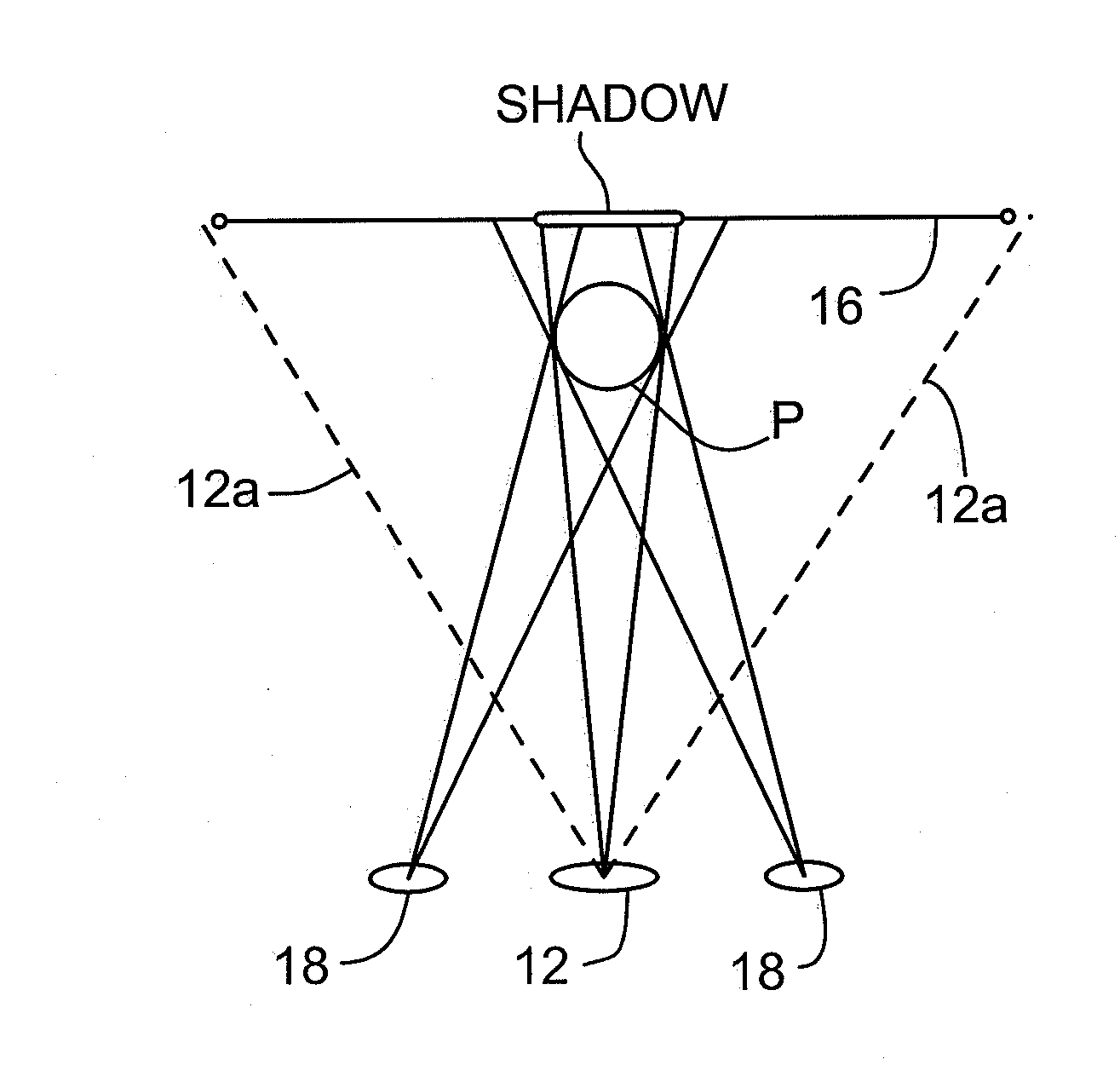
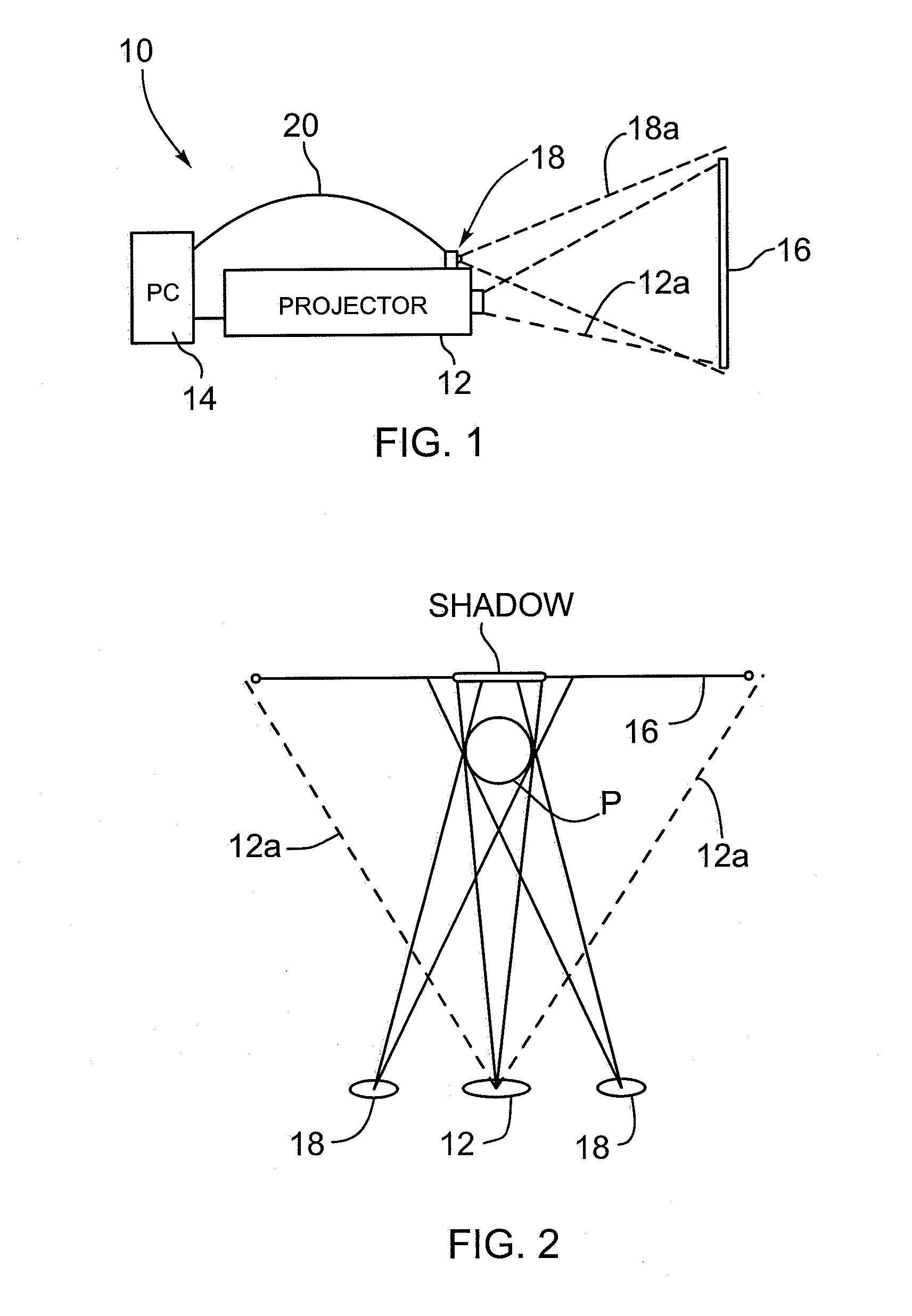
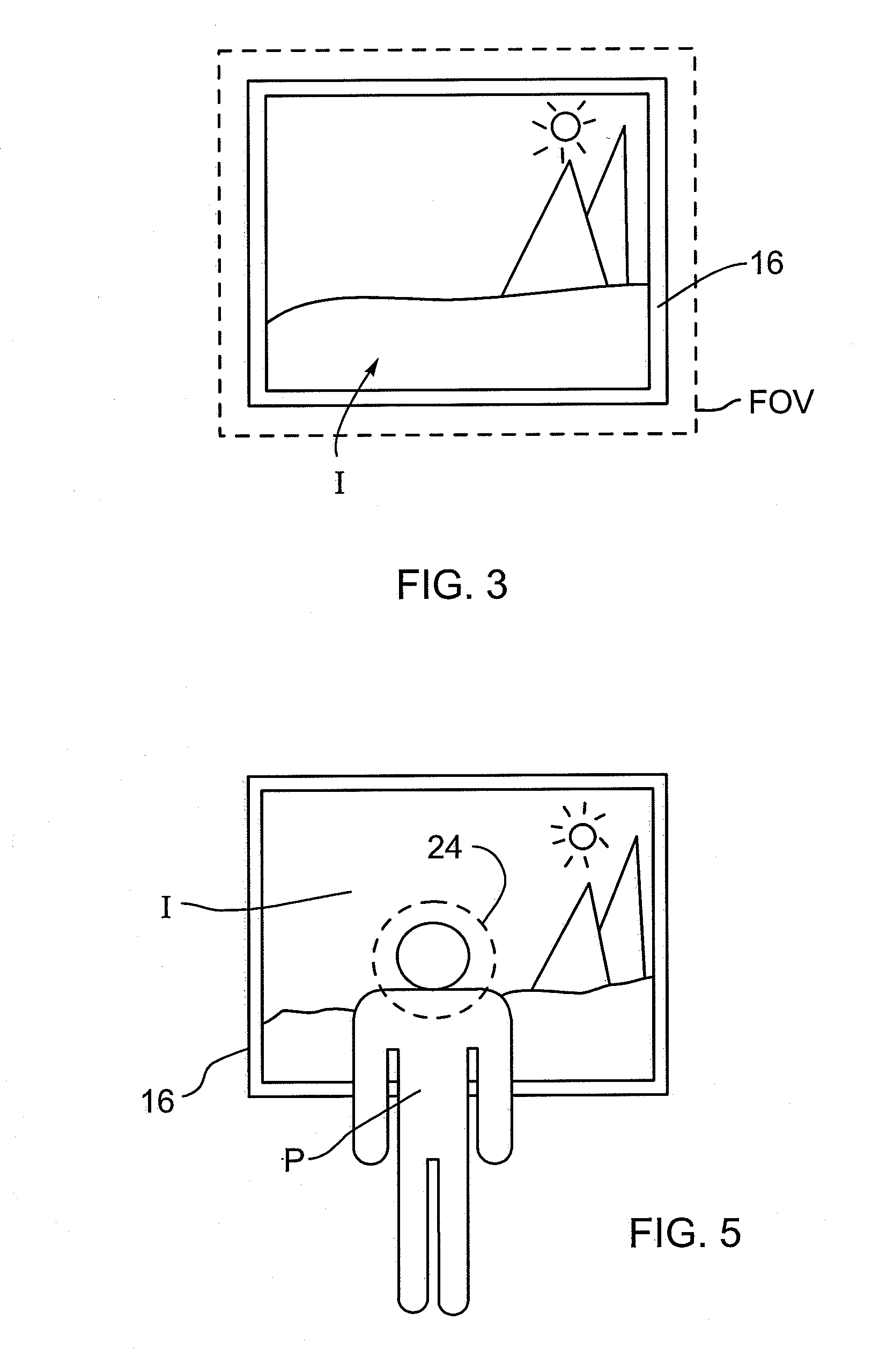
Method and apparatus for inhibiting a subject's eyes from being exposed to projected light
Owner:SEIKO EPSON CORP
On-die termination snooping for 2T applications in a dynamic random access memory device
ActiveUS20050268059A1Digital data processing detailsMemory systemsElectrical resistance and conductanceControl signal
A method and apparatus for controlling the on-die termination of a memory system. The method comprises snooping a command bus in response to a first plurality of command signals clocked at 1T and enabling the on-die termination in response to a second plurality of command signals clocked at 2T and the first plurality of command signals. The apparatus may be memory device comprising a memory array responsive to a plurality of command signals, a data bus having at least one of a data pad, a data strobe output pad, and an input data mask pad, an activation circuit responsive to certain of the plurality of command signals and operable to produce a control signal, and an termination circuit responsive to the control signal and operable to apply an effective resistance to at least one of the data pad, the data strobe output pad, and the input data mask pad.
Owner:MICRON TECH INC
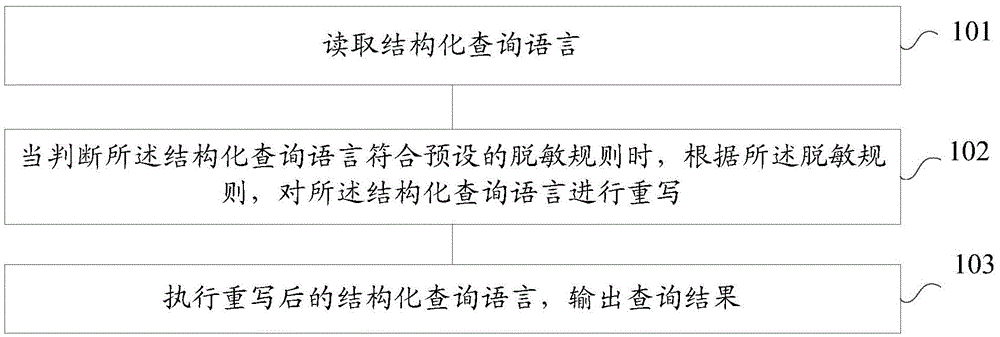
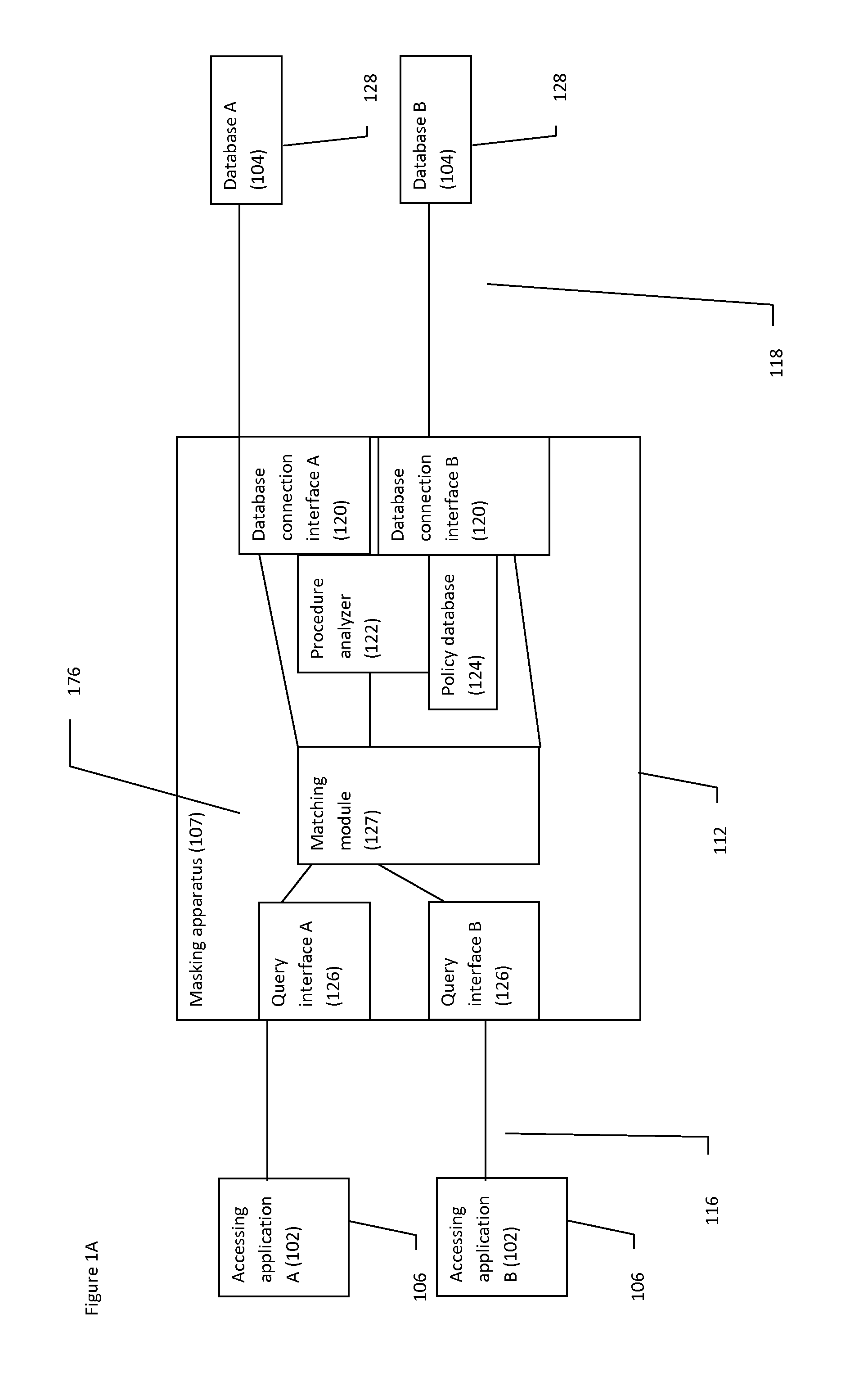
Method and system of data masking
ActiveCN106778288AAchieve desensitizationEnsure safetyDigital data protectionSpecial data processing applicationsDynamic dataQuery language
The embodiment of the invention provides a method and system of data masking. The method of data masking comprises the steps of reading a structuralized query language; when it is judged that the structuralized query language is in accordance with a preset masking rule, rewriting the structuralized query language according to the masking rule; executing the rewritten structuralized query language, and outputting a query result. According to the method and system of data masking, dynamic data masking can be achieved, a masked query result can be flexibly output, and the safety of the data can be guaranteed.
Owner:ALIBABA (CHINA) CO LTD
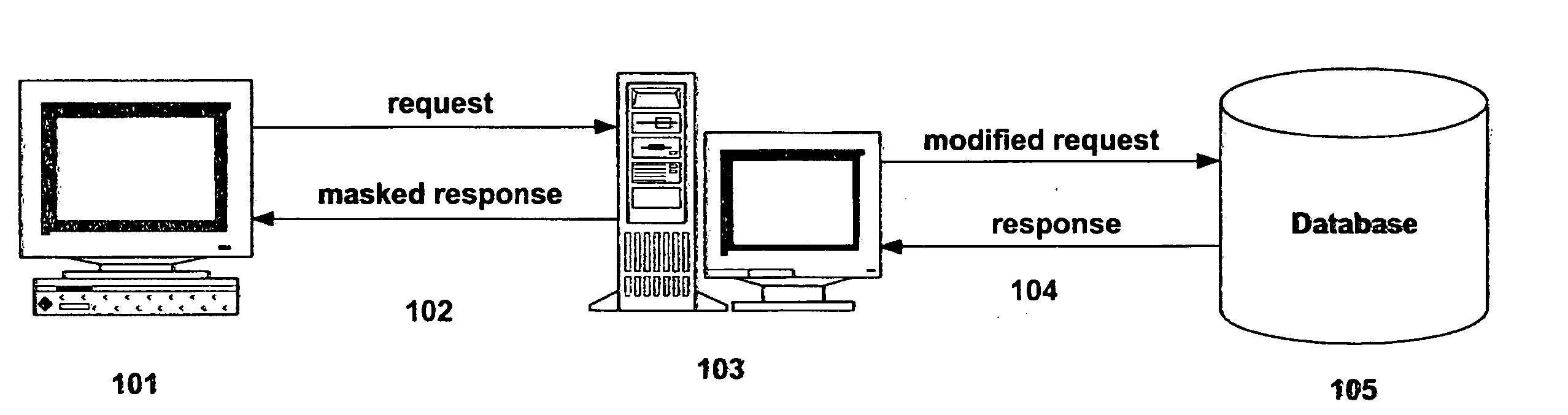
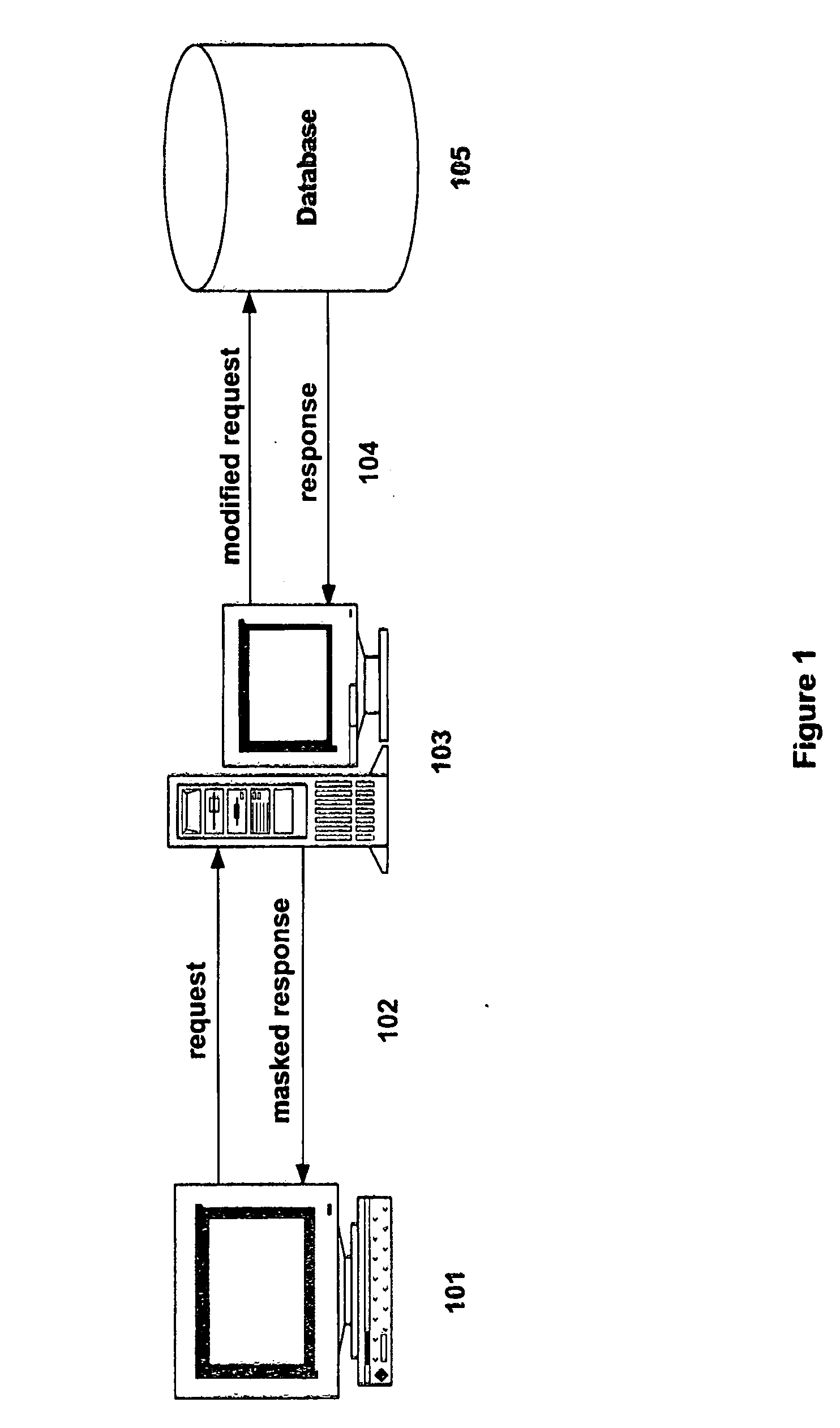
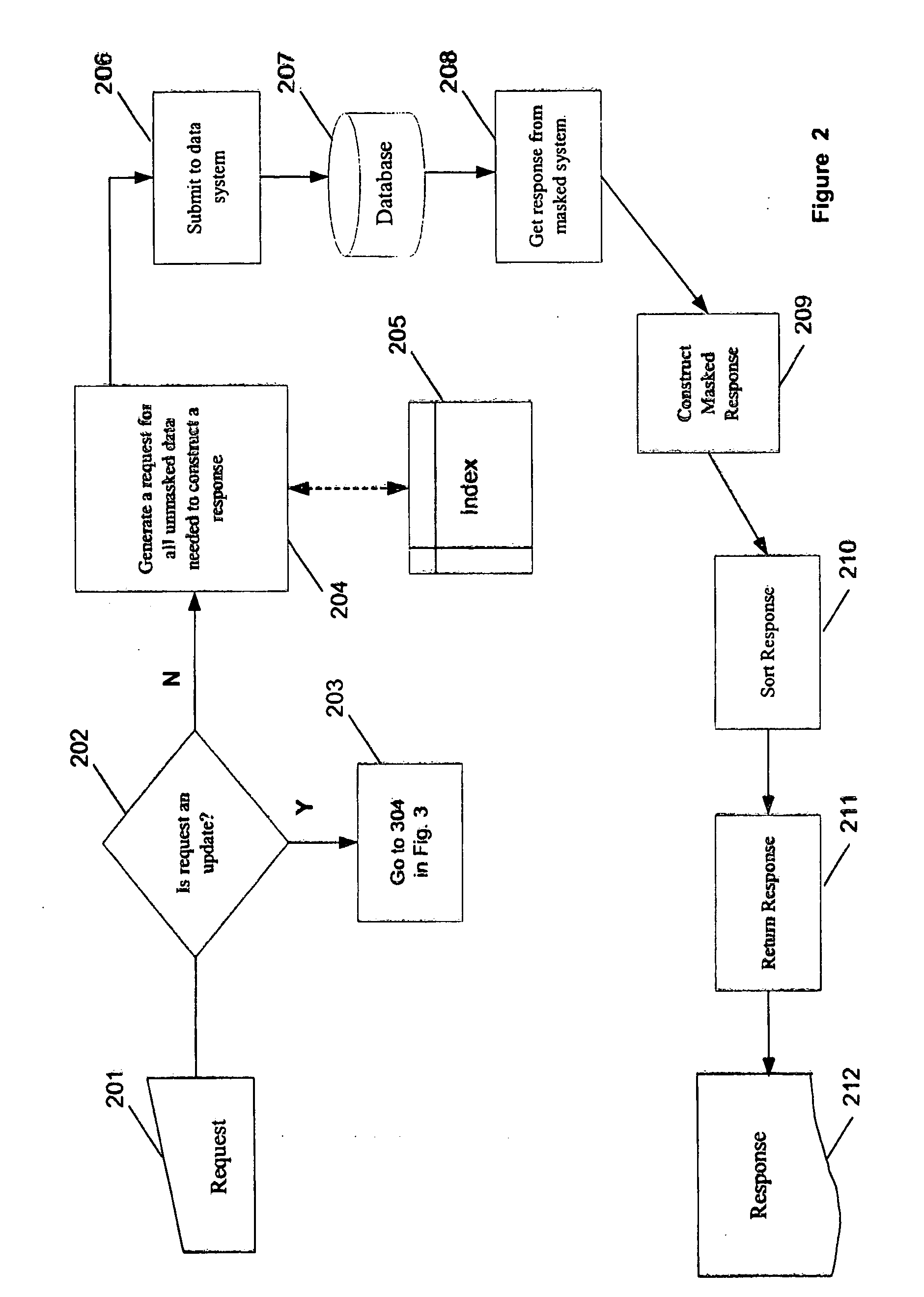
System and method for dynamic data masking
InactiveUS20060074897A1Reduce effortShorten the timeDigital data information retrievalSpecial data processing applicationsConfidentialityDynamic data
A system and method for dynamically masking data. The system and method receive and identify masked data in a data request, generate a request to receive the corresponding unmasked data, provide the request for unmasked data to a database, receive an unmasked response from the database, mask the response, and return the masked response. The system and method do not alter the database to mask the data it contains and maintain the confidentiality of the sensitive data. Additionally, the system and method receive updates for masked data, generate a corresponding update for unmasked data and apply the unmasked update to the database. The masked and unmasked data updated are held in a data map, and used to remask updated data in response to requests for masked data.
Owner:JPMORGAN CHASE BANK NA
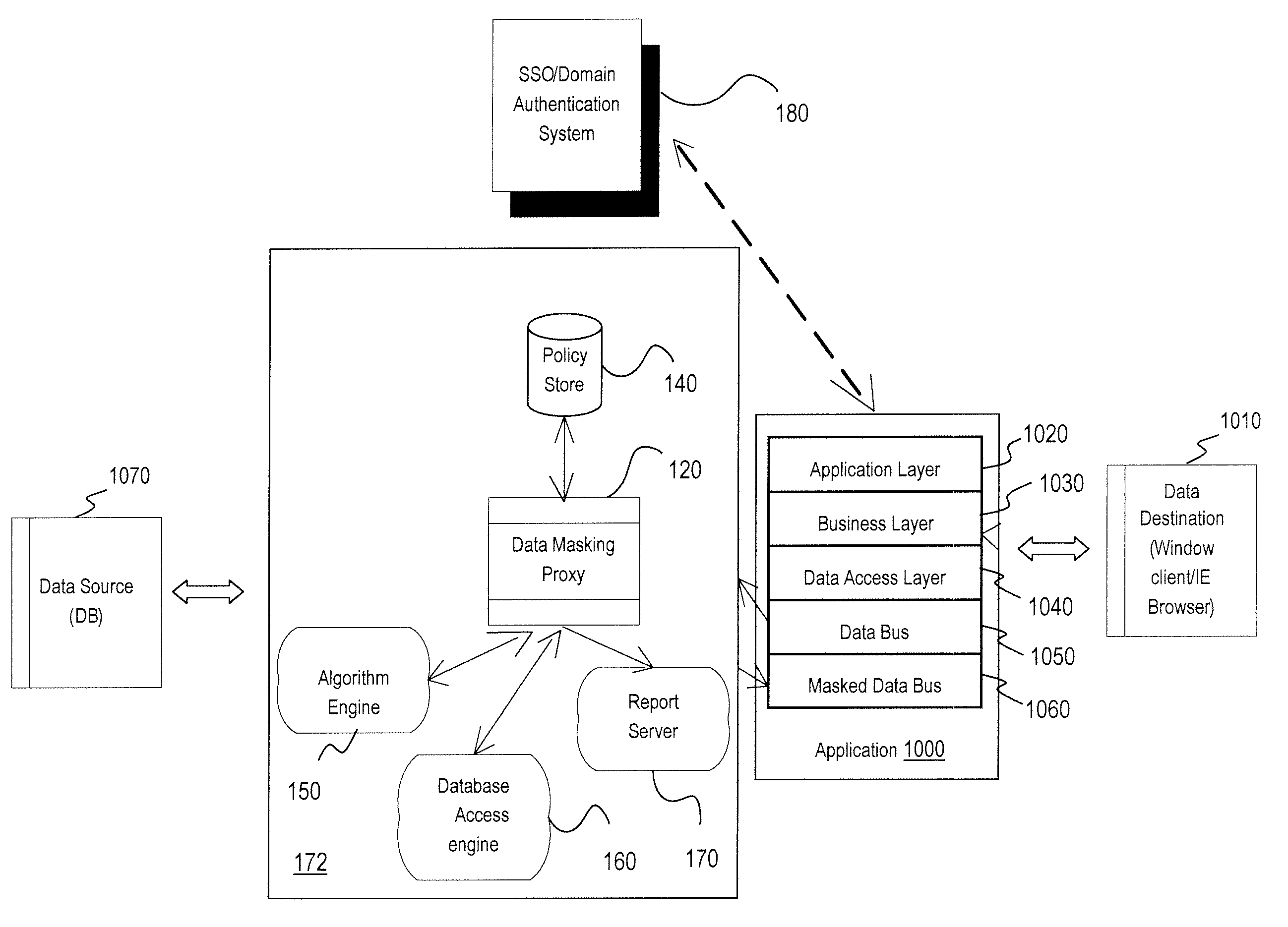
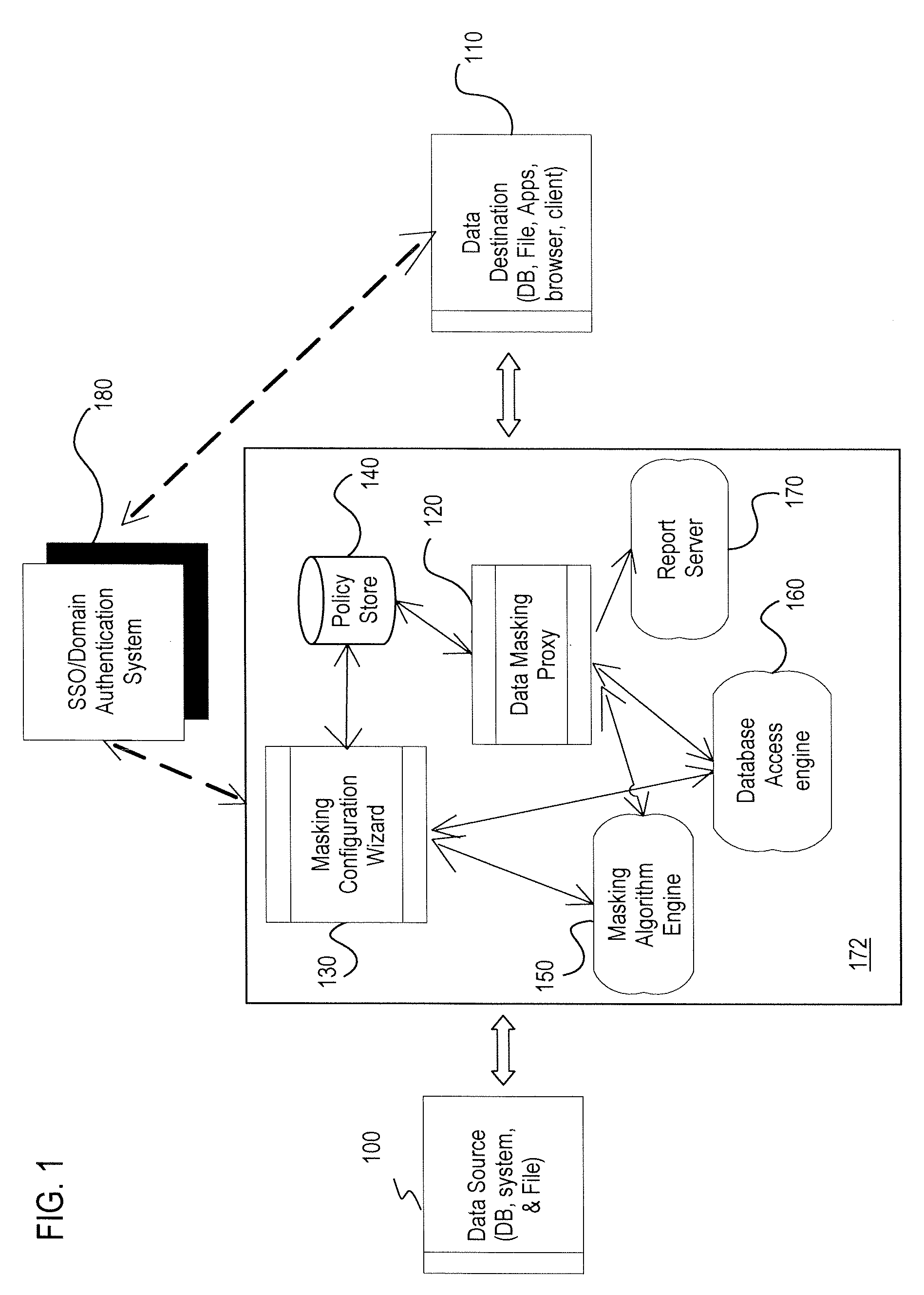
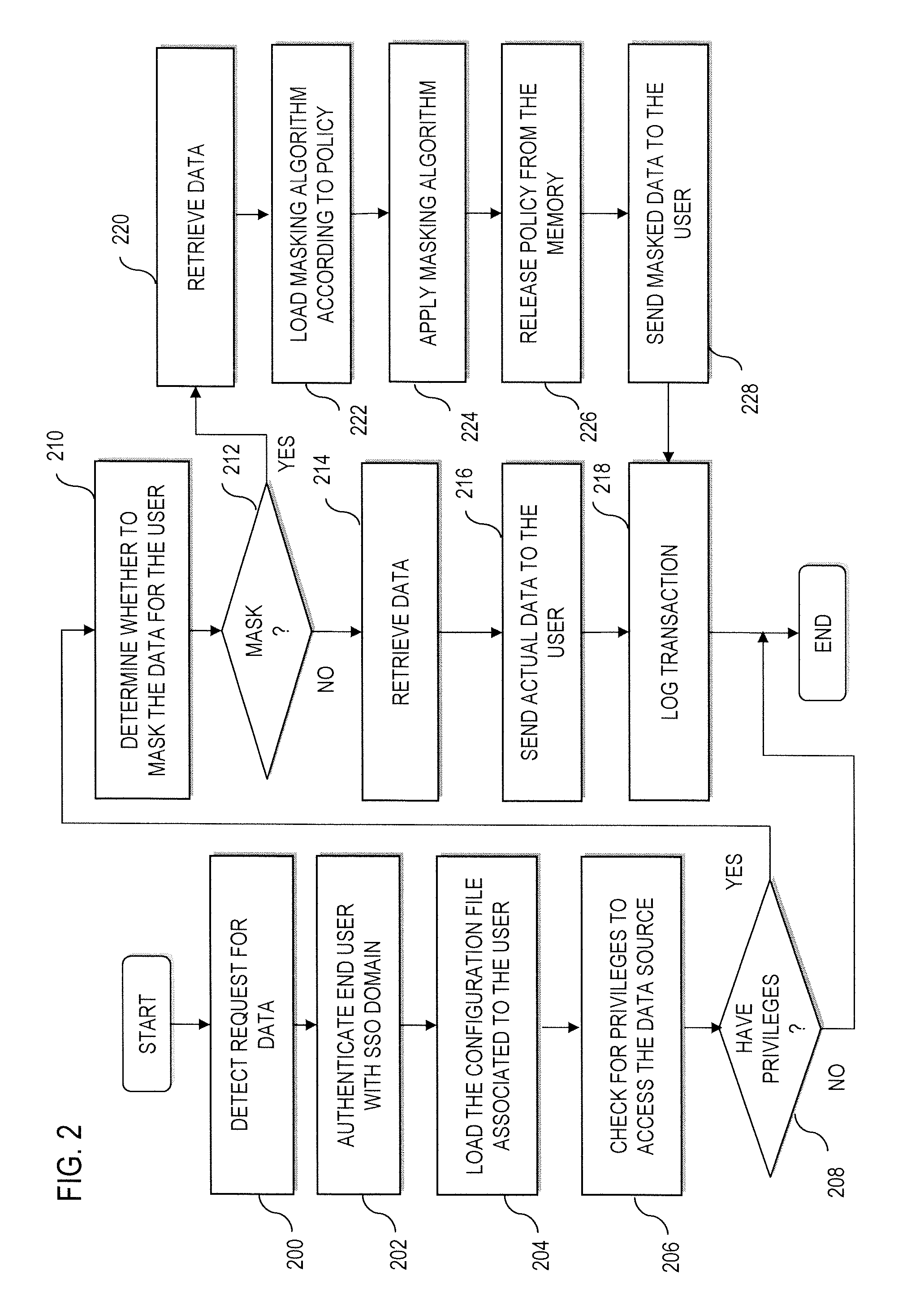
Method and apparatus for providing a data masking portal
ActiveUS20090049511A1Digital data processing detailsUser identity/authority verificationPersonalizationApplication software
An approach is provided for de-personalizing data. A request is received from an application for retrieval of data. An end user associated with the request is authenticated. A determination is made whether to mask the data based on the request and the authentication. In response to the determination, a masking algorithm is selected to apply to the data and to output mask data.
Owner:VERIZON PATENT & LICENSING INC
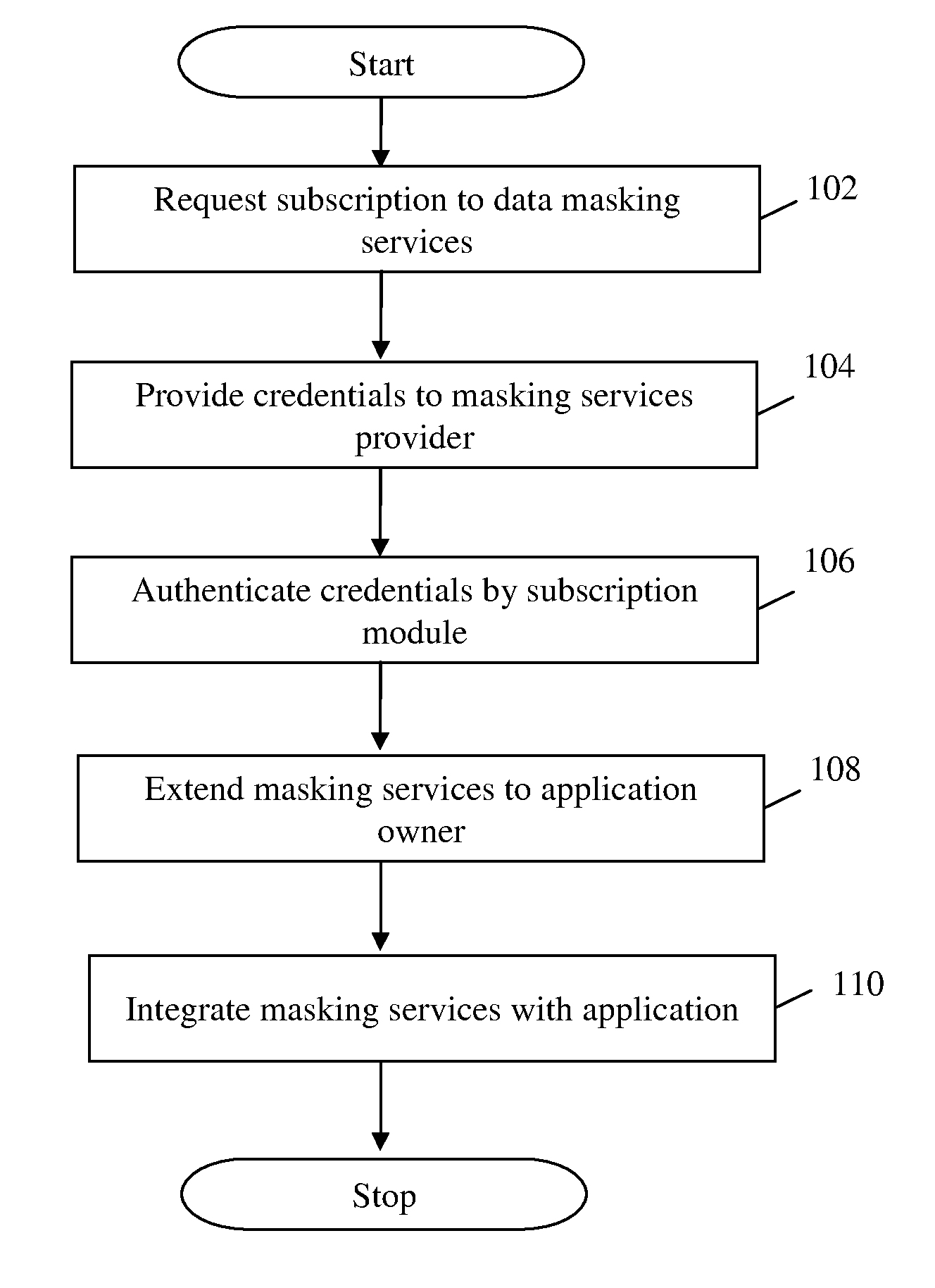
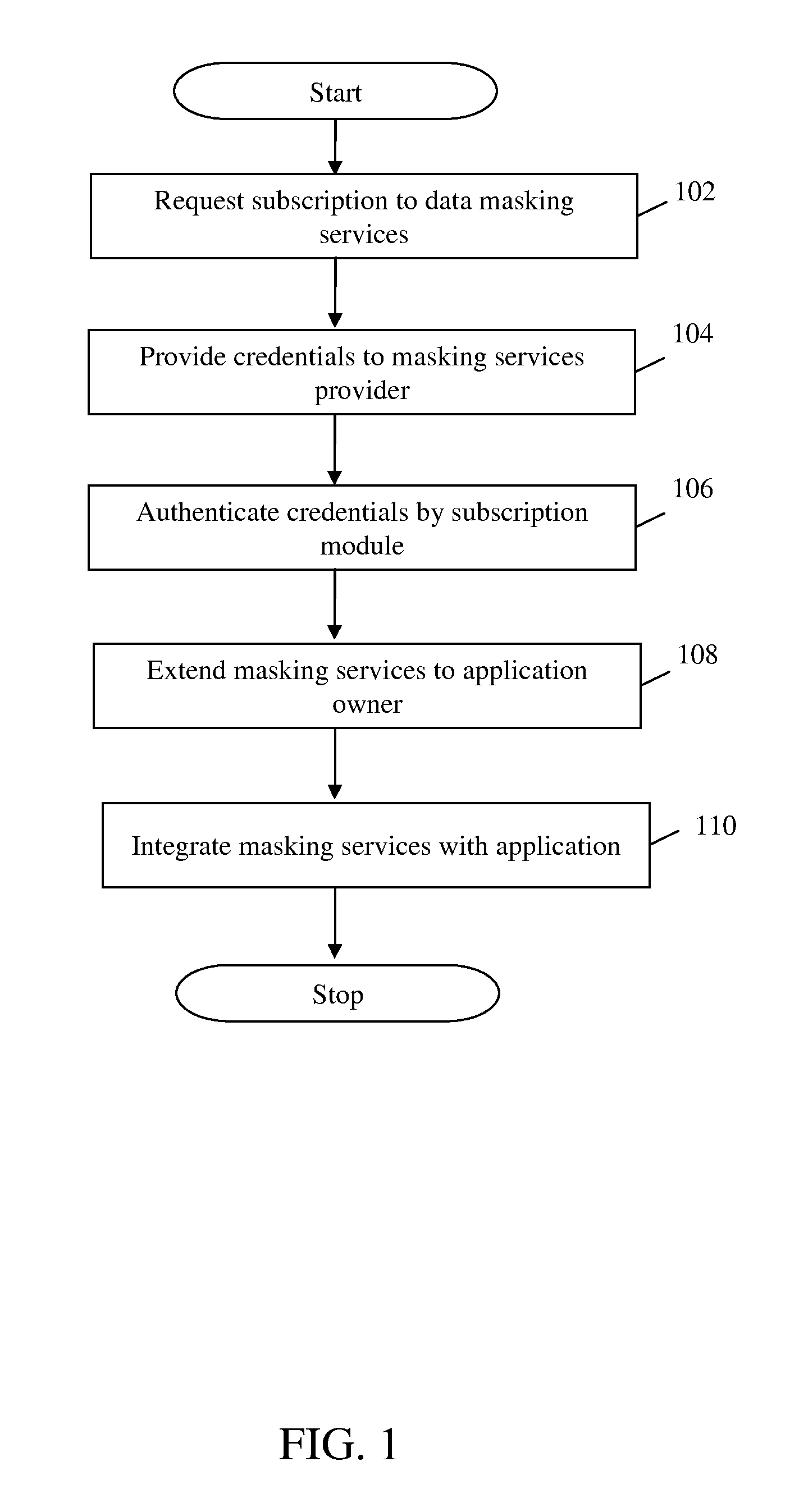
Method and system for providing masking services
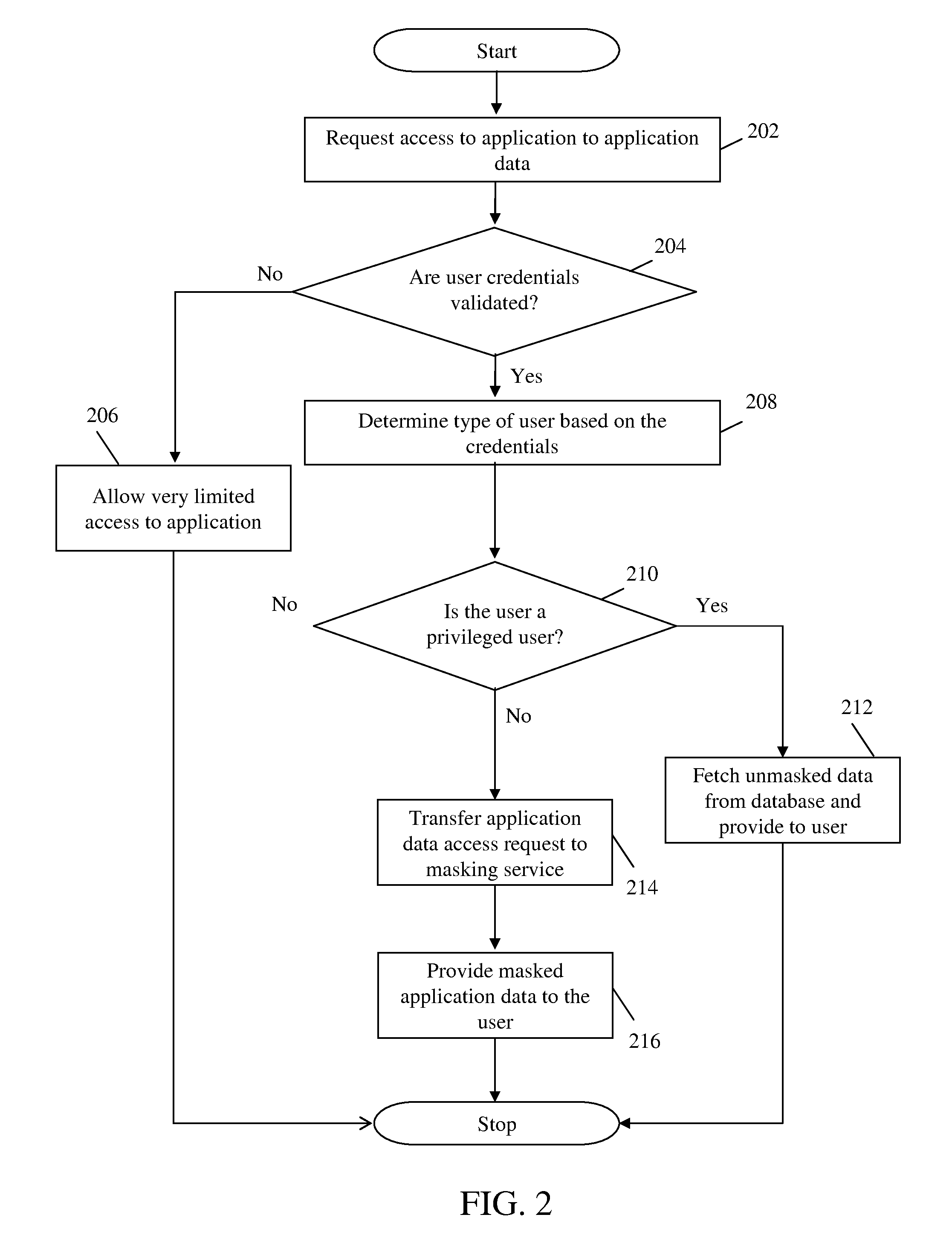
ActiveUS20110321120A1Facilitate subscriptionFacilitates configuration of one or more masking rulesDigital data authenticationTransmissionData accessData masking
A system and method for presenting on-demand masking of data as a software service in a distributed environment is provided. An application hosted on a computing device receives request for access to application data from a user. Credentials of the user are first validated in order to determine whether the user is authorized to access the requested application data. For an authorized user, a category of the user is determined to ascertain whether the user is privileged to obtain full access. In case the user is a privileged user, unmasked application data is fetched from a database utility and provided to the user. In case the user is not a privileged user, application data access request is transferred to a data masking service. Application data is fetched from database utility, masked based on pre-defined masking rules and provided to the user.
Owner:INFOSYS LTD
Memory bus polarity indicator system and method for reducing the affects of simultaneous switching outputs (SSO) on memory bus timing
A method and system transfer read data from a memory device having a data bus and a data masking pin adapted to receive a masking signal during write operations of the memory device. The method includes placing a sequence of read data words on the data bus and applying a data bus inversion signal on the data masking pin, the data bus inversion signal indicating whether the data contained each read data word has been inverted. Another method and system transfer data over a data bus. The method includes generating a sequence of data words, at least one data word including data bus inversion data. The sequence of data words is applied on the data bus and is thereafter stored. The data bus inversion data is applied to invert or not invert the data contained in the stored data words.
Owner:MICRON TECH INC
Obfuscating Network Traffic from Previously Collected Network Traffic
ActiveUS20120084464A1Multiple digital computer combinationsTransmissionTraffic capacityComputer network
An obfuscated network traffic server is operative to generate obfuscated network traffic. The obfuscated network traffic server maintains the relationship between extracted application content and extracted network header content such that the obfuscated network traffic is indistinguishable from the monitored network traffic. The obfuscated network traffic server may include a network monitor operative to monitor network traffic and to extract application content and network header content from the monitored network traffic. The obfuscated network traffic server may also include a data masking processor operative to mask a portion of the separated application content and / or the separated network header content. The obfuscated network traffic server may further include a masking attribute selector operative to specify the attributes of the application content and / or the network header content that is to be masked.
Owner:TELCORDIA TECHNOLOGIES INC
System and method for bitwise readout holographic ROM
InactiveUS6825960B2Mechanical record carriersRecord information storageHolographic storageLight beam
According to one aspect a method for manufacturing a holographic storage medium includes providing one or more data masks with data to be recorded, illuminating the one or more data masks onto the medium with a plane wave object beam from a laser light source operating at a record wavelength, propagating a reference beam at an incident angle to the medium to record the one or more data masks on the medium, and altering the incident angle of the reference beam for each of the one or more data masks, wherein each of the one or more data masks recorded on said medium can be read bit by bit using a laser light source operating in a readout range of wavelengths different from the record wavelength.
Owner:AKONIA HOLOGRAPHICS
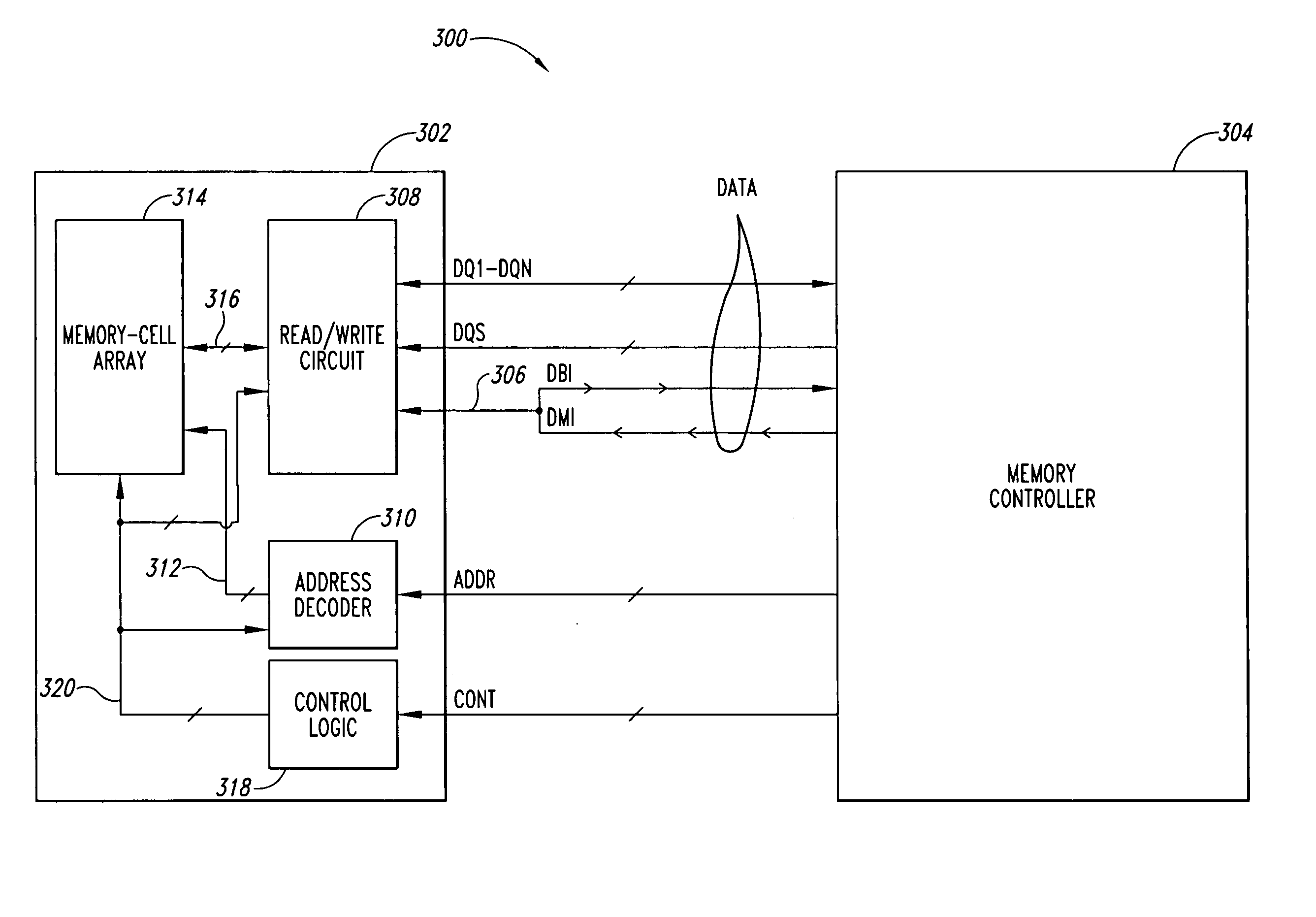
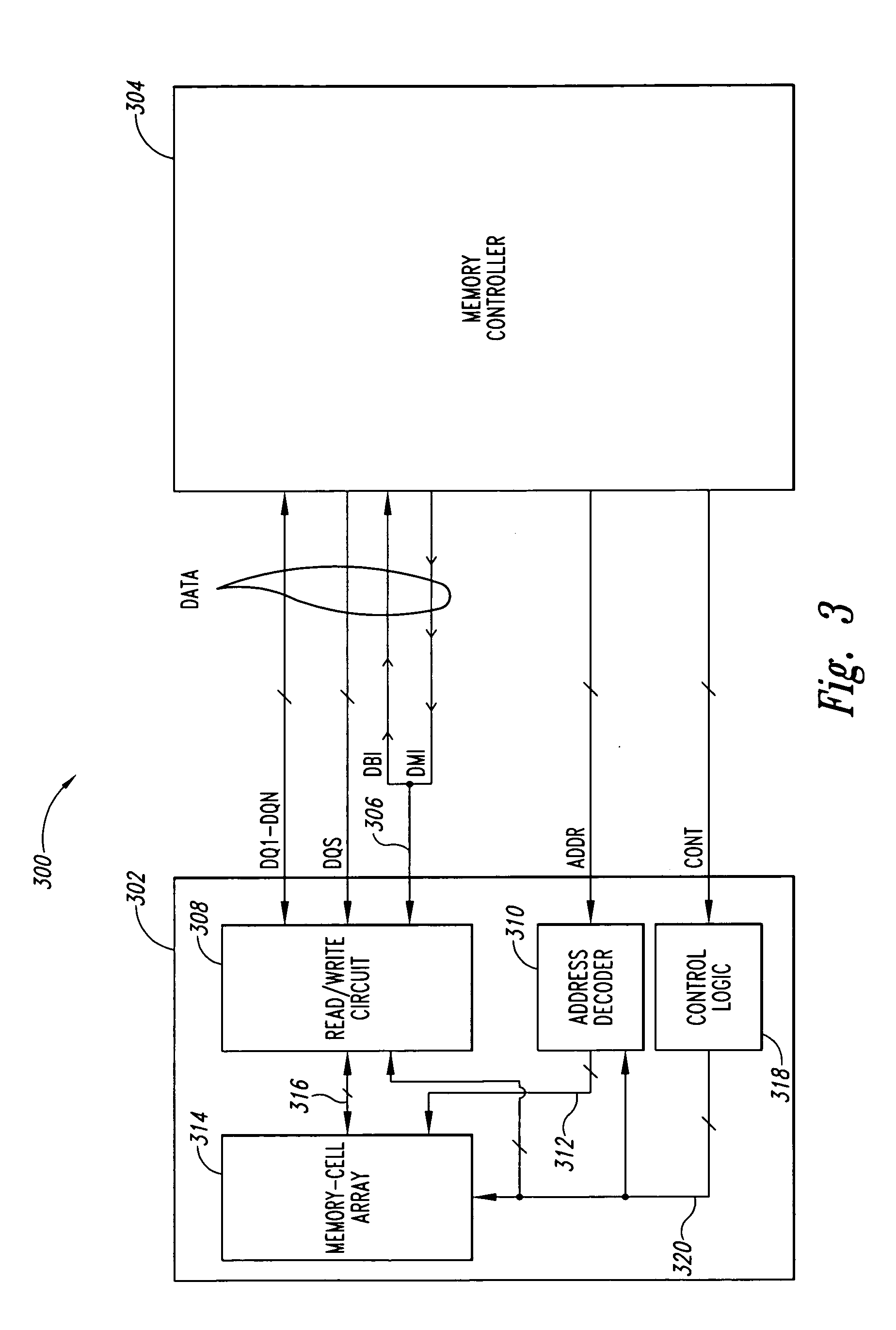
Memory Interface Supporting Both ECC and Per-Byte Data Masking
A memory and a method of storing data in a memory are provided. The memory comprises a memory block comprising data bits and additional bits. The memory includes logic which, when receiving a first command, writes data into the data bits of the memory block, wherein the data is masked according to a first input. The logic, in response to a second command, writes data into the data bits of the memory block and writes a second input into the additional bits of the memory block.
Owner:ADVANCED MICRO DEVICES INC
Advanced memory device having improved performance, reduced power and increased reliability
An advanced memory having improved performance, reduced power and increased reliability. A memory device includes a memory array, a receiver for receiving a command and associated data, error control coding circuitry for performing error control checking on the received command, and data masking circuitry for preventing the associated data from being written to the memory array in response to the error control coding circuitry detecting an error in the received command. Another memory device includes a programmable preamble. Another memory device includes a fast exit self-refresh mode. Another memory device includes auto refresh function that is controlled by the characteristic device. Another memory device includes an auto refresh function that is controlled by a characteristic of the memory device.
Owner:GLOBALFOUNDRIES US INC
Method and system for logical data masking
ActiveUS20110270837A1Digital data processing detailsComputer security arrangementsDigital dataCluster algorithm
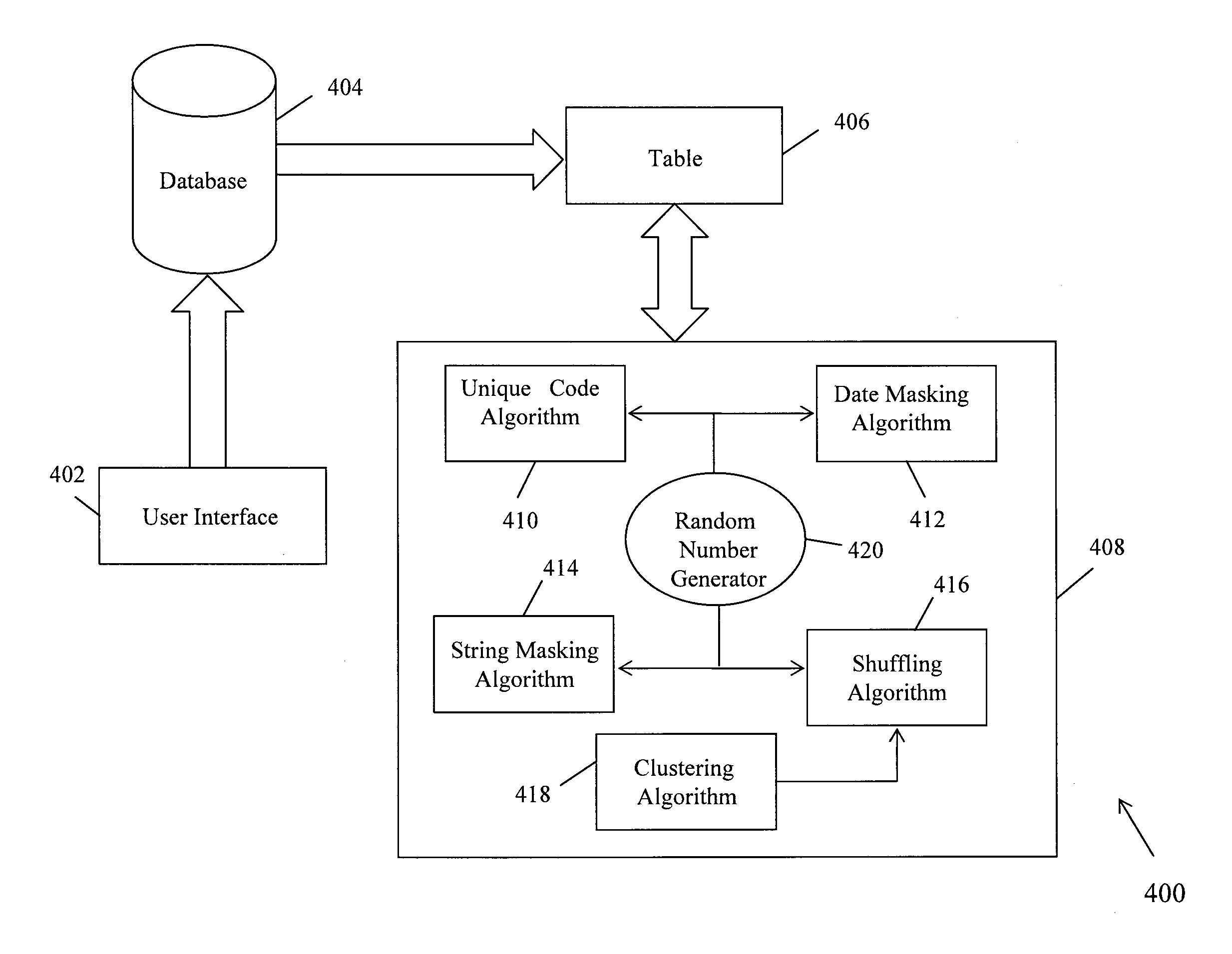
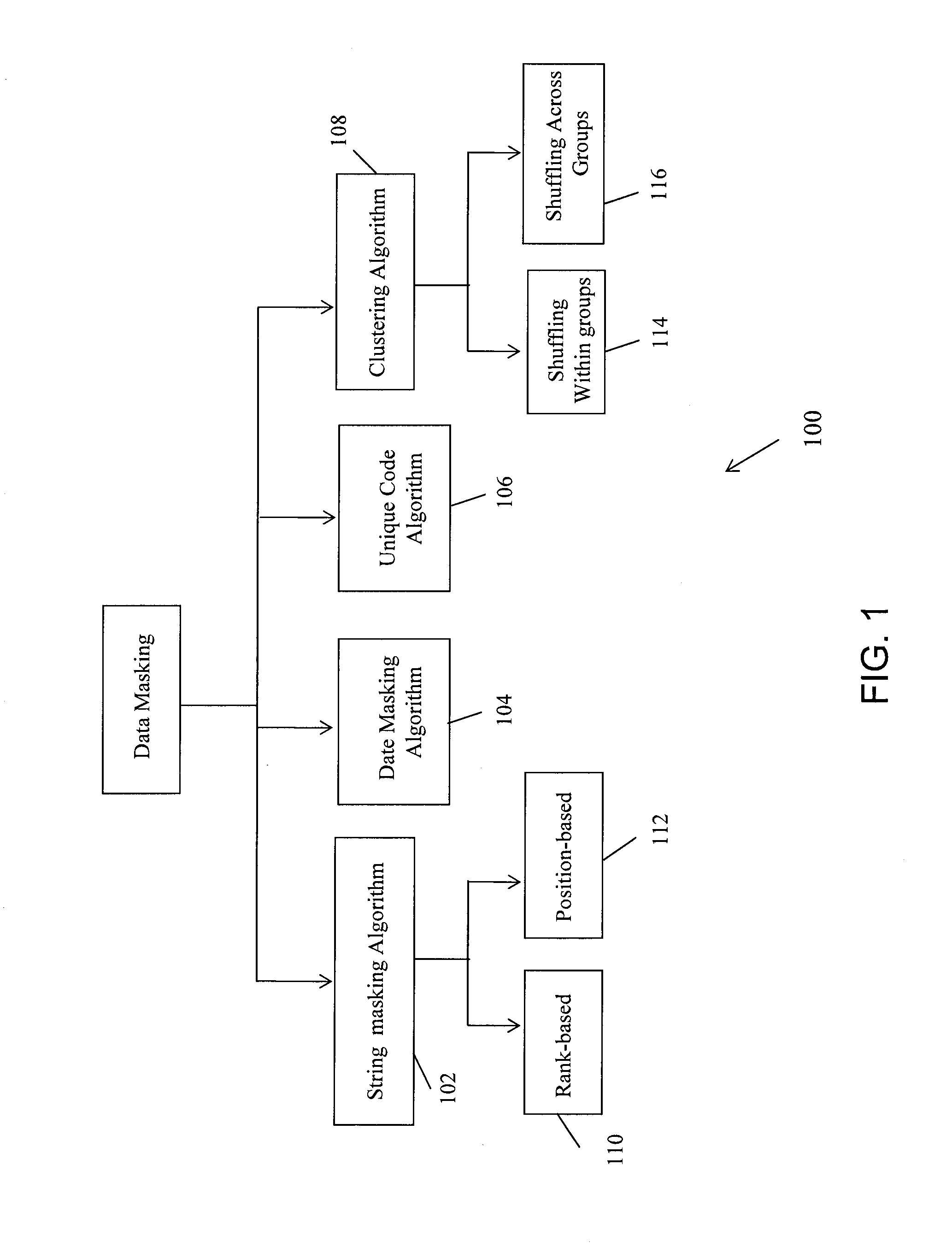
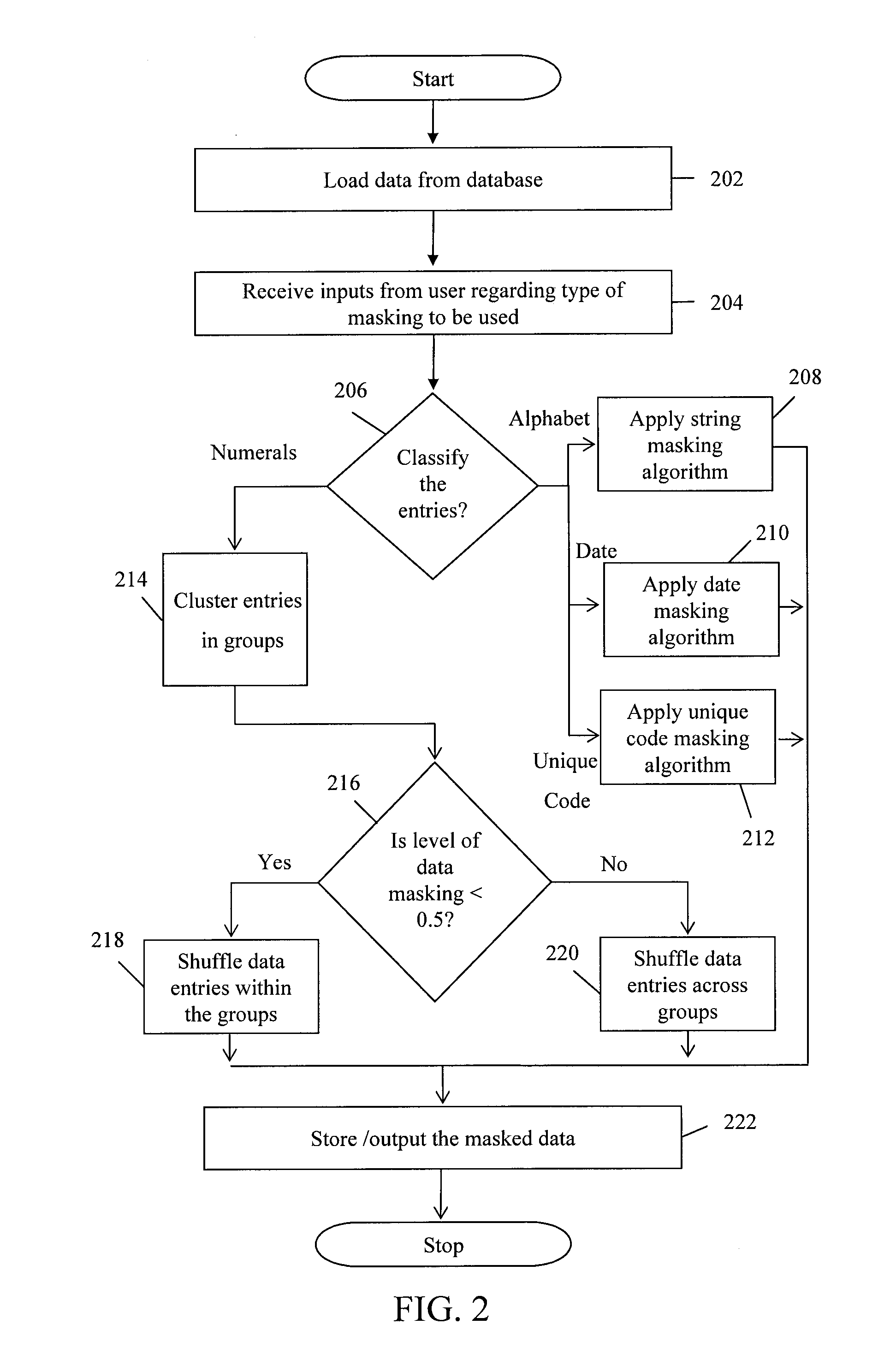
A system and method for logically masking data by implementing masking algorithms is provided. The method includes receiving one or more inputs from user regarding type of data masking to be implemented depending on type of data entry. Data entries include alphabetical data, data comprising unique codes, data comprising dates and numerical data. Based on inputs received, the data entries are classified and appropriate masking algorithms are executed. For masking numerical data entries, the data entries are first grouped using clustering algorithms and are then shuffled using shuffling algorithms. For low level of data masking selected by a user, numerical data entries are shuffled within groups and for high level of data masking selected by a user, numerical data entries are shuffled across groups.
Owner:INFOSYS LTD
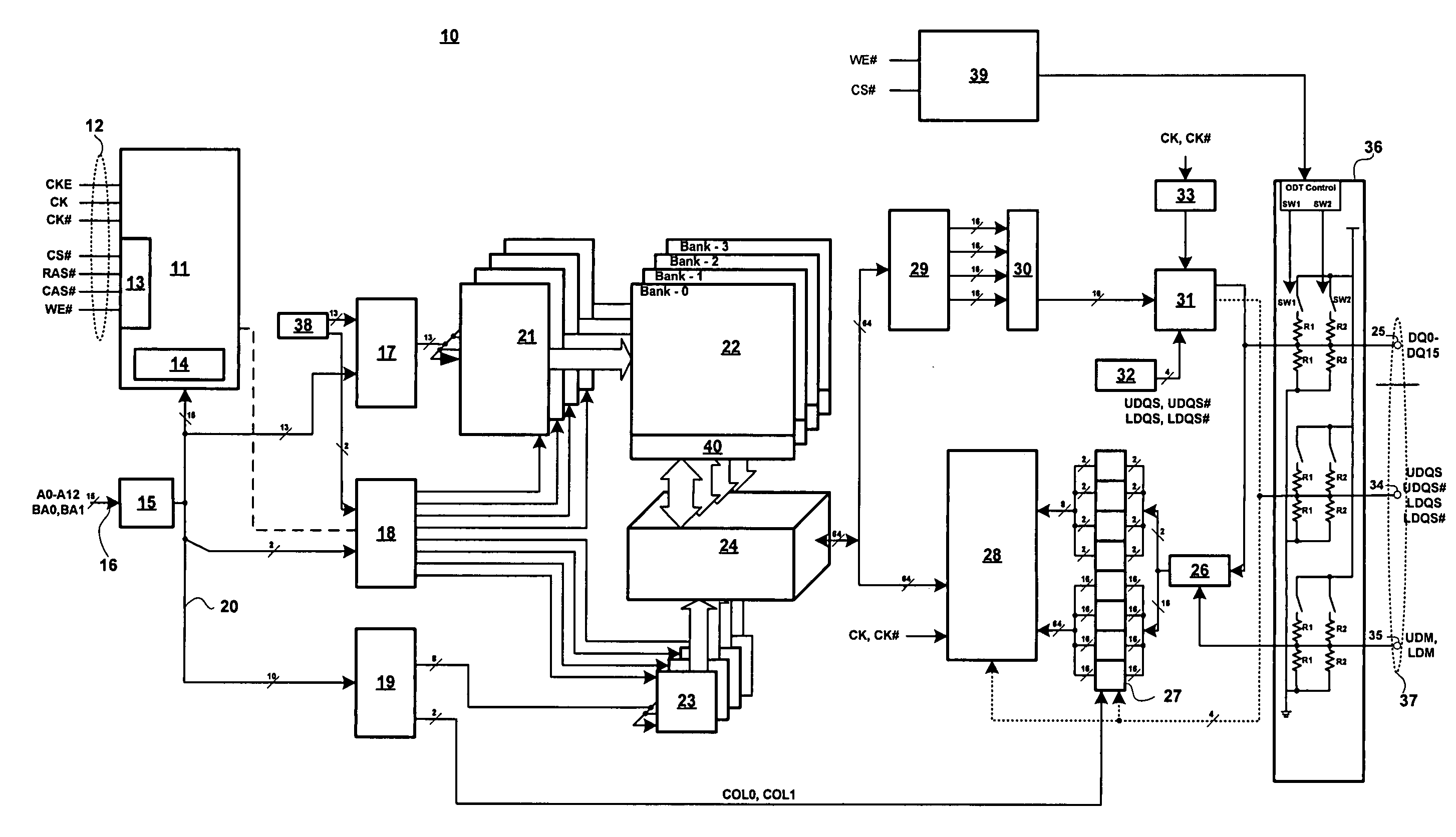
Memory chip and apparatus for testing a memory chip
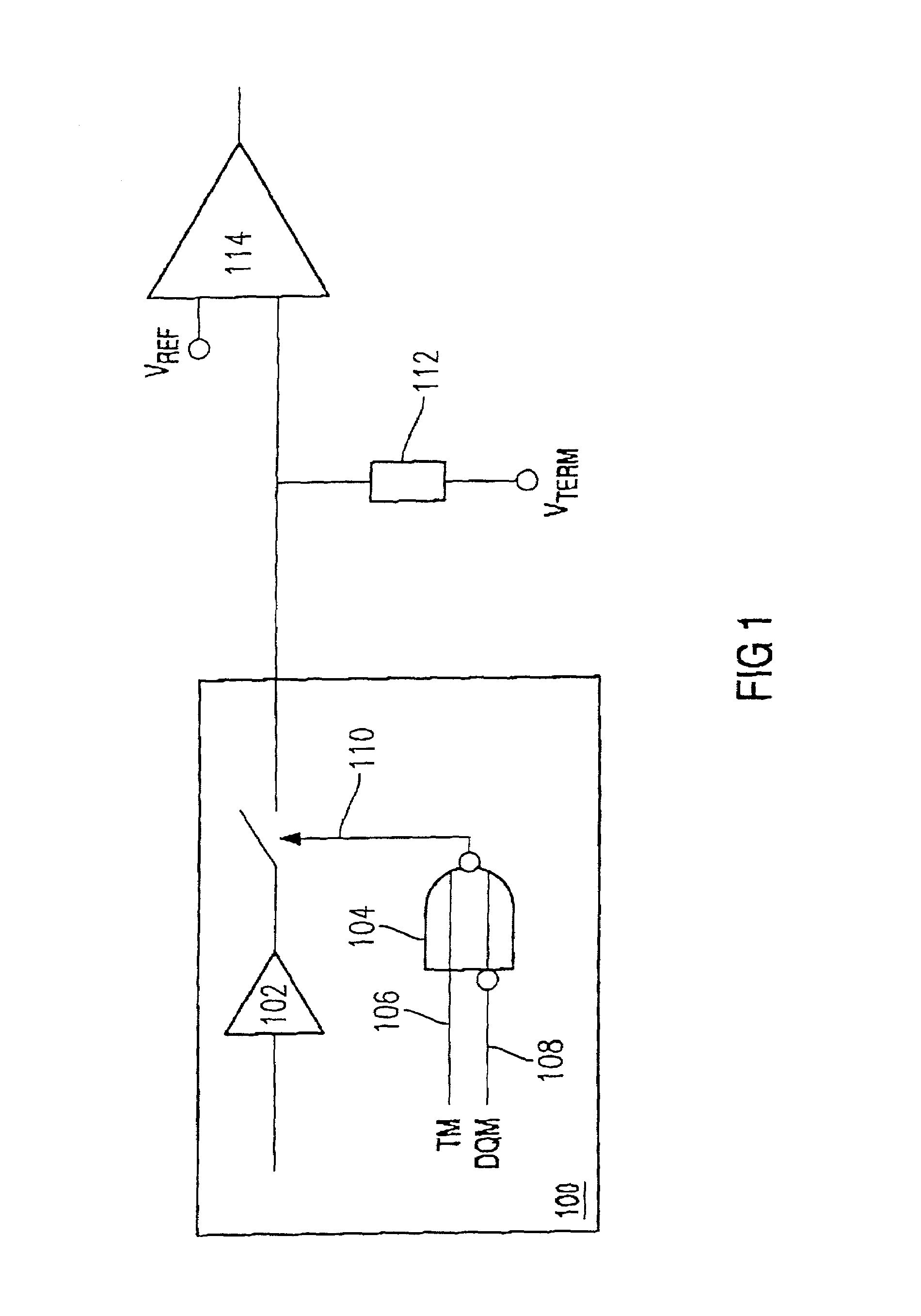
ActiveUS6961882B2Little complexity without adversely affecting the performance of the memory chipsDigital storageMemory chipComputer hardware
The present invention provides a memory chip (100) which can be operated in a normal mode and in a test mode (TM) and which has a device (102) for outputting data from the memory chip (100) and a device (104) for enabling the device (102) for outputting data when the test mode (TM) has been activated. The device (104) for enabling the device (102) for outputting data has a device for masking data so that only particular portions of the data are output when a data masking state (DQM) has been activated.
Owner:POLARIS INNOVATIONS
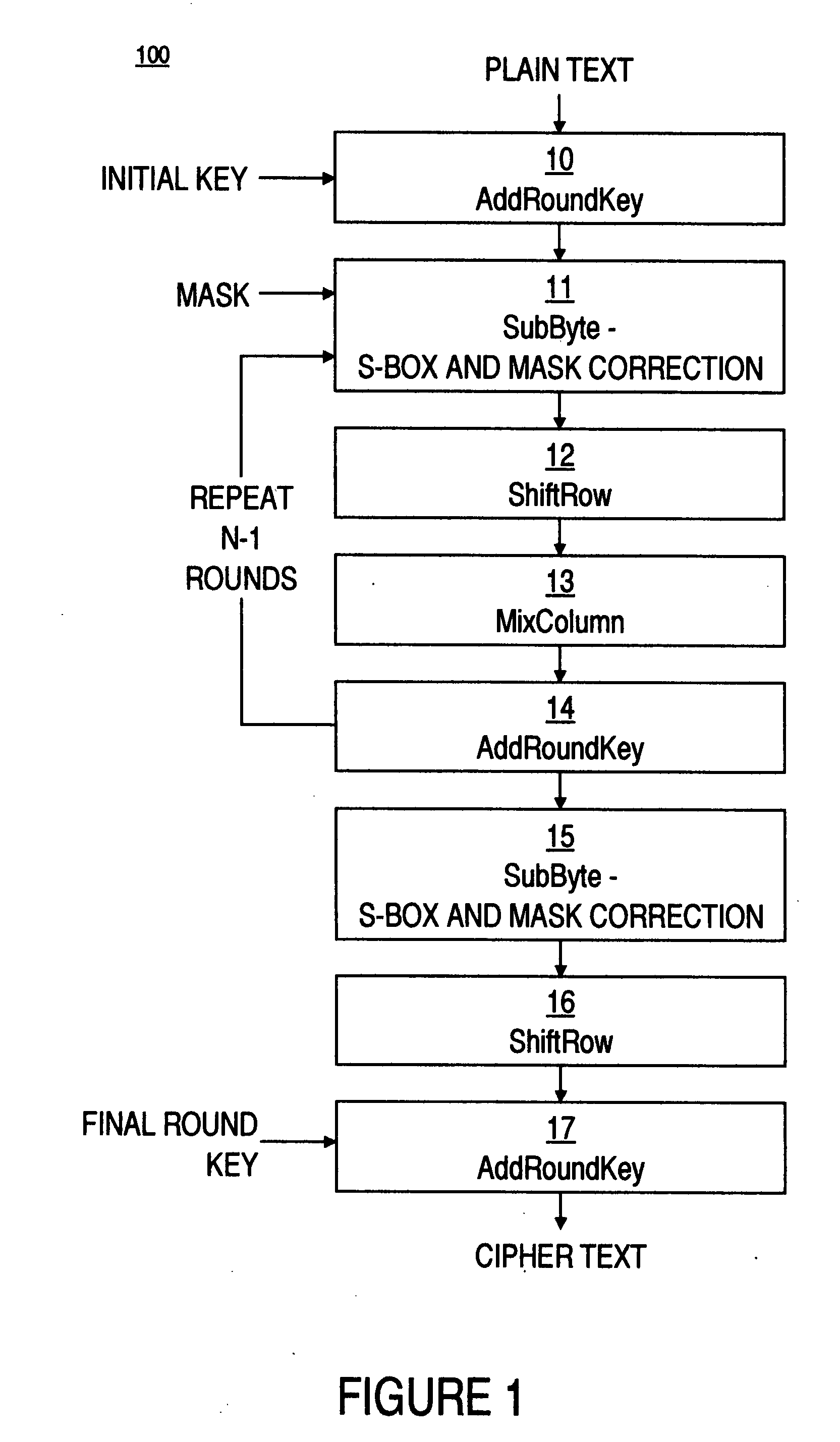
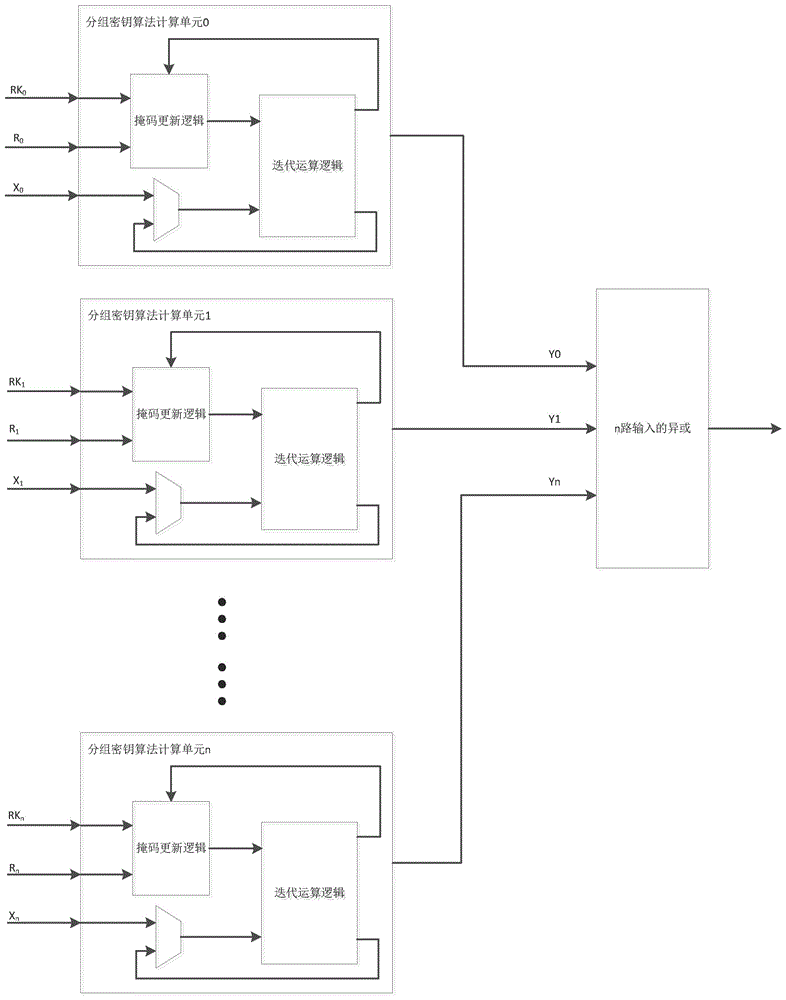
Mask S box, packet key calculation unit, apparatus and corresponding construction method
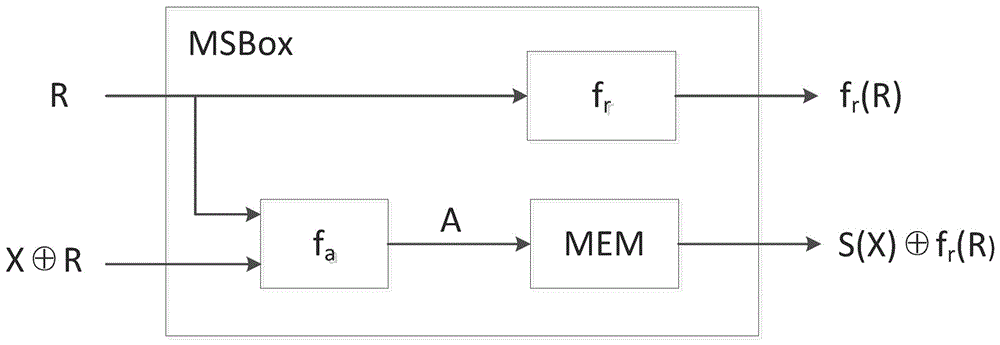
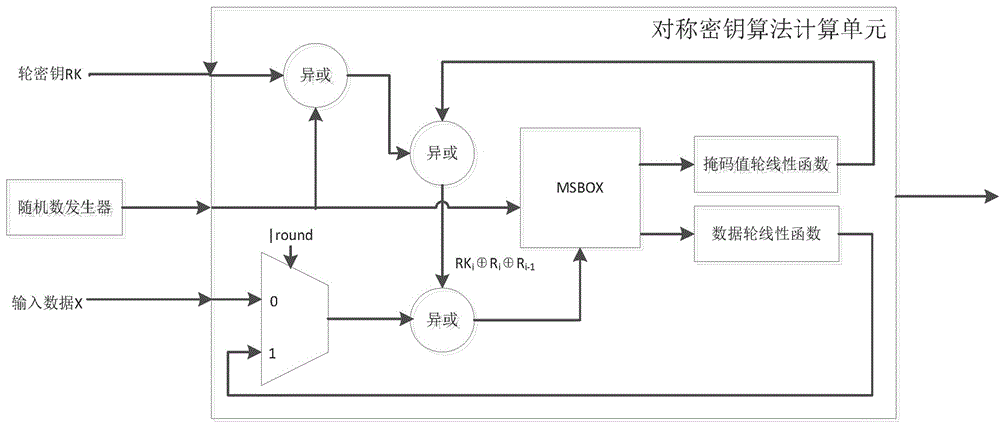
ActiveCN106788974AHigh reusabilityIncreased complexityEncryption apparatus with shift registers/memoriesDigital data processing detailsS-boxComputer module
The present invention discloses a mask S box, a packet key calculation unit, an apparatus and corresponding construction method. The mask S box comprises an input module, an address mapping processing module, and an output module. The input module receives and uses a random number and input data masked by the random number as two inputs of the mask S box. The address mapping processing module performs one-to-one mapping on the two inputs and corresponding storage addresses in a memory of the mask S box. The output module performs linear processing on the random number by using a linear equation so as to obtain and uses the random number after linear conversion as one output of the mask S box. The storage address is obtained after the random number undergone linear conversion masks the output of the original S box, and is used as another output of the mask S box. The mask S box is safe, and further, the mask S box is easy to implement, is low in power consumption and small in area, and is optimized and expanded to realize the anti-high order DPA encryption device.
Owner:SHENZHEN STATE MICRO TECH CO LTD
Methods and systems for recording to holographic storage media
InactiveUS20050254108A1Increase storage capacityOptical re-recordingInformation arrangementInformation layerHolographic storage
According to one aspect and example, a method for recording holographic media and / or holographic master data masks includes recording at least a first hologram or information layer with a first holographic medium (e.g., a “submaster”) and recording at least a second information layer with a second holographic medium (e.g., a second “submaster”). The first information layer and the second information layer from the first and second holographic media are then sequentially reconstructed and stored with a single holographic master medium (e.g., a “master”). The holographic master may then be used to record the stored first and second information layers into additional holographic media, for example, into HROM devices or the like.
Owner:AKONIA HOLOGRAPHICS
Error correction method of memory
ActiveCN103187104AReduce the possibility of errorError detection/correctionSingle error correctionExternal dataCorrection method
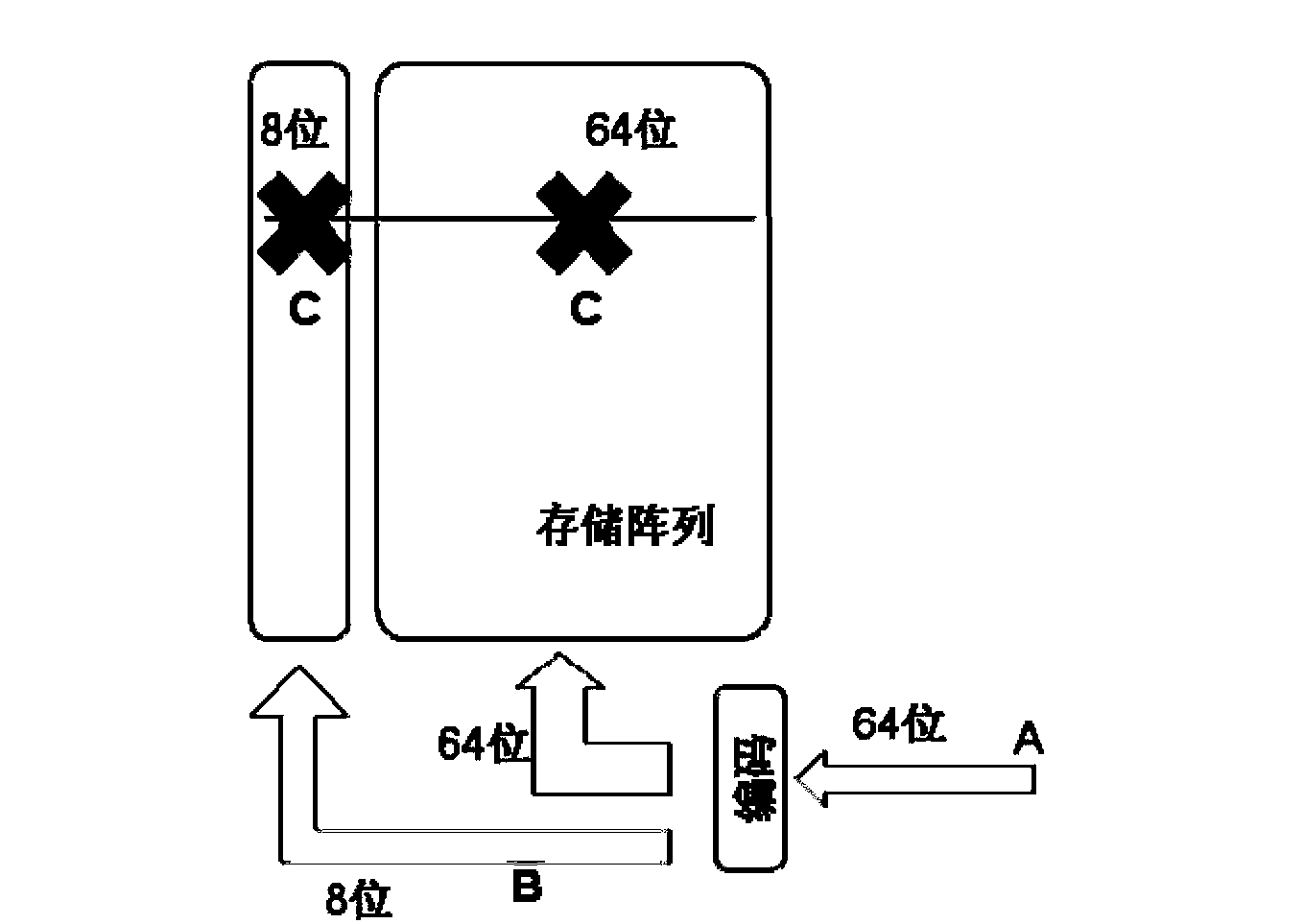
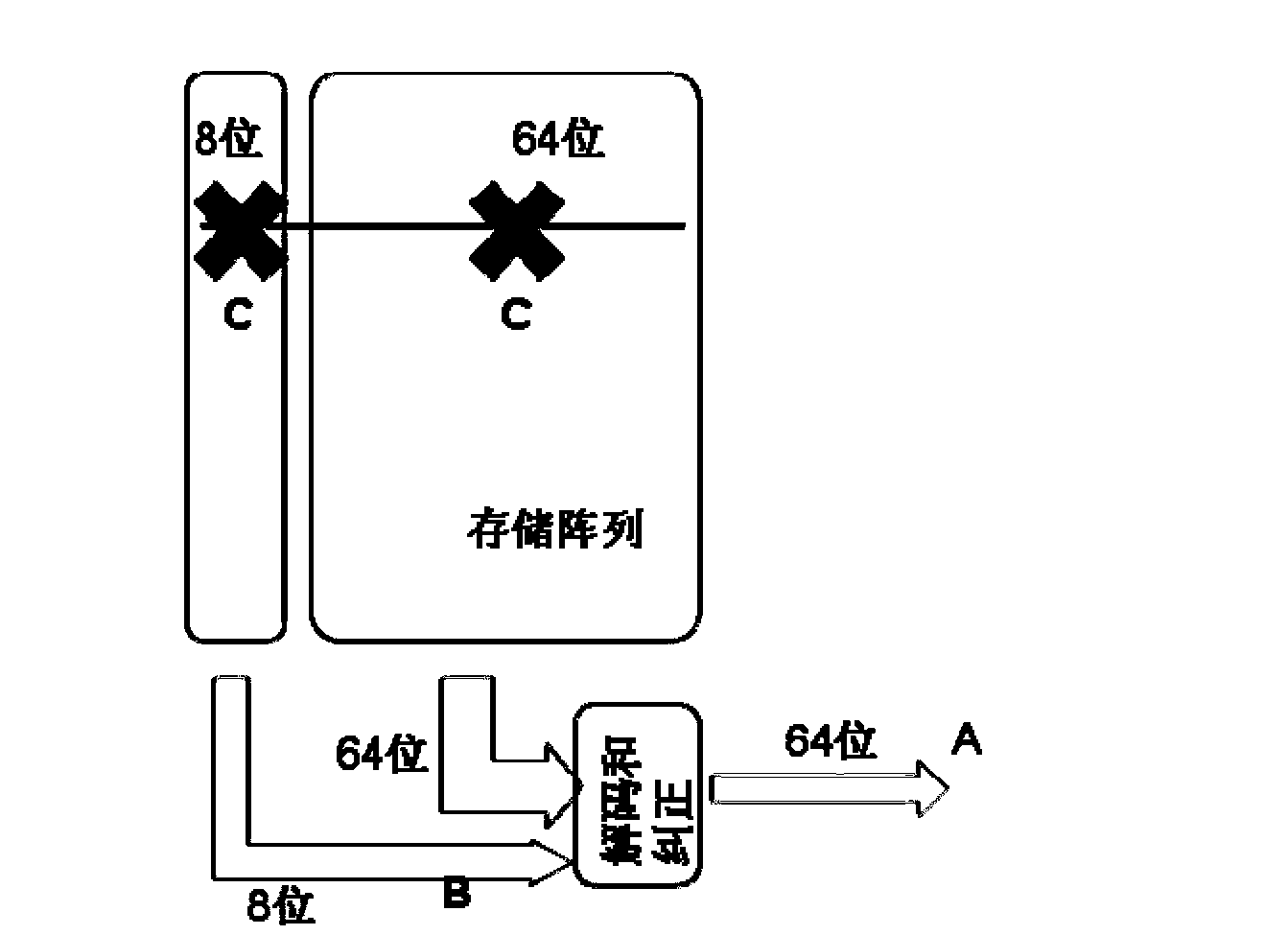
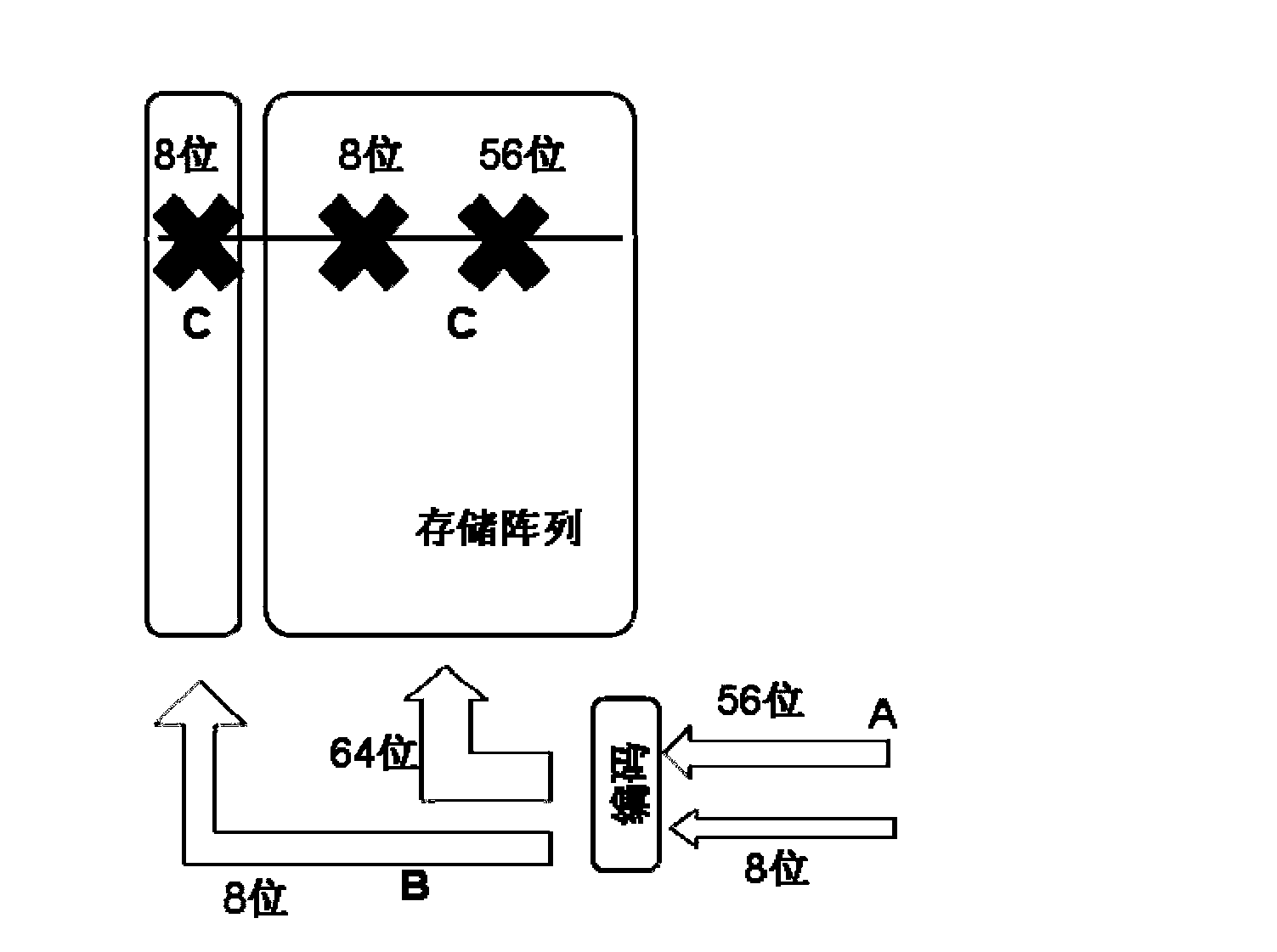
The invention provides an error correction method of a memory and solves the problem that a conventional ECC (error correction code) encoding process cannot be smoothly performed to achieving encoding and a parity bit cannot be generated due to existing of a data mask, or a storage array area is required to be increased in order to generate the parity bit. The error correction method of the memory comprises the following steps: (1) external data are read in, the parity bit is generated according to a set rule, a characteristic bit is generated simultaneously, and the external data, the characteristic bit and the parity bit are stored in the memory; and (2) the external data, the characteristic bit and the parity bit in the memory are read out, if characteristic bit characterizes that the data mask (DM) exists, the parity bit is invalid, and decoding and error correction are not performed when the data are read out, and if characteristic bit characterizes that the DM dose not exists, the parity bit is valid, and decoding and error correction are performed by utilizing the parity bit when the data are read out. The error correction method of the memory can reduce the possibility for a DRAM (dynamic random access memory) to make errors, even for a system using the DM.
Owner:XI AN UNIIC SEMICON CO LTD
Memory bus polarity indicator system and method for reducing the affects of simultaneous switching outputs (SSO) on memory bus timing
A method and system transfer read data from a memory device having a data bus and a data masking pin adapted to receive a masking signal during write operations of the memory device. The method includes placing a sequence of read data words on the data bus and applying a data bus inversion signal on the data masking pin, the data bus inversion signal indicating whether the data contained each read data word has been inverted. Another method and system transfer data over a data bus. The method includes generating a sequence of data words, at least one data word including data bus inversion data. The sequence of data words is applied on the data bus and is thereafter stored. The data bus inversion data is applied to invert or not invert the data contained in the stored data words.
Owner:MICRON TECH INC
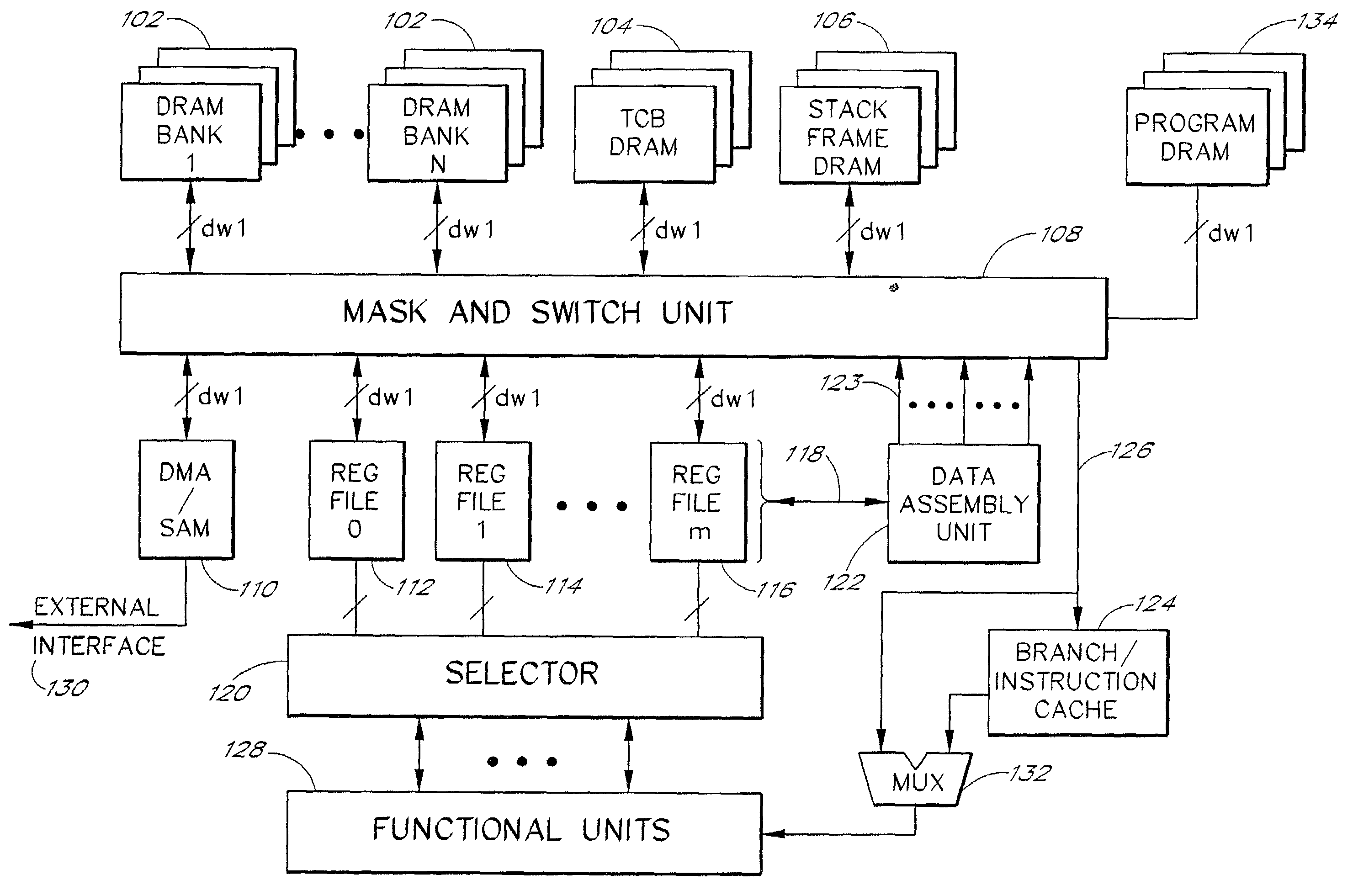
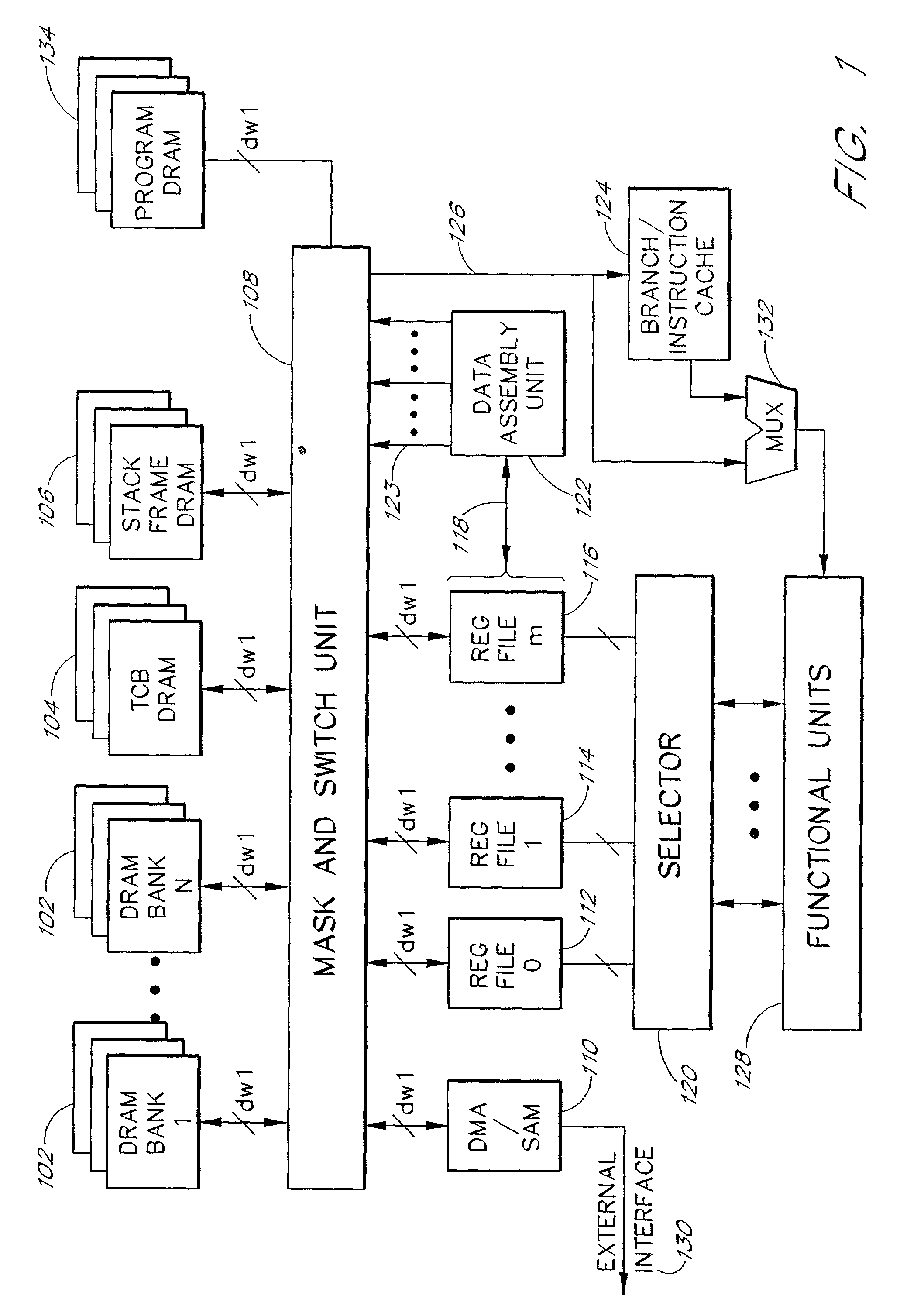
Methods for intelligent caching in an embedded DRAM-DSP architecture
InactiveUS7146489B2Reduce and eliminate wait timeReduce delaysMemory architecture accessing/allocationRegister arrangementsDsp architectureProcessor register
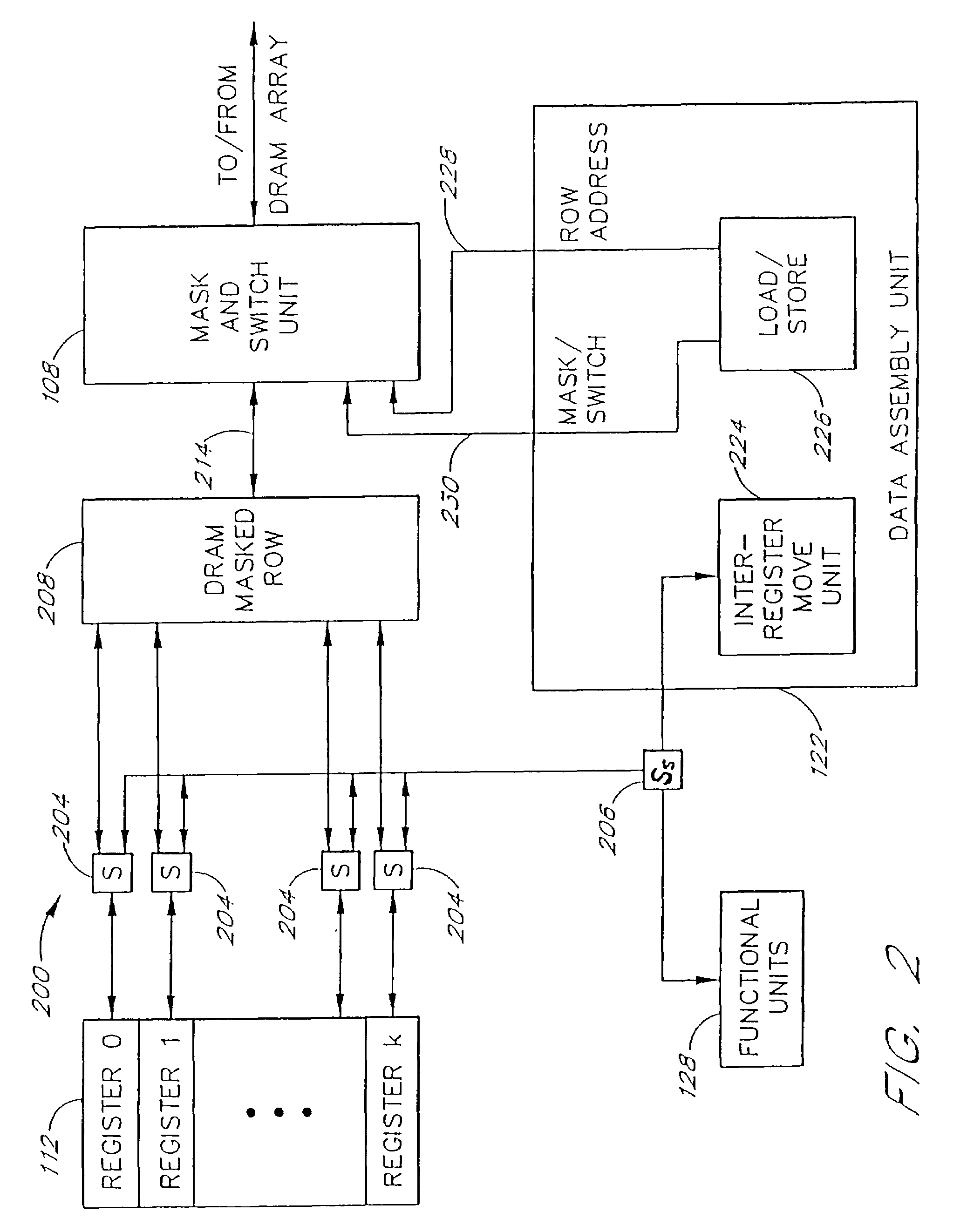
An efficient embedded-DRAM processor architecture and associated methods. In one exemplary embodiment, the architecture includes a DRAM array, a set of register files, set of functional units, and a data assembly unit. The data assembly unit includes a set of row-address registers and is responsive to commands to activate and deactivate DRAM rows and to control the movement of data throughout the system. A pipelined data assembly approach allowing the functional units to perform register-to-register operations, and allowing the data assembly unit to perform all load / store operations using wide data busses. Data masking and switching hardware allows individual data words or groups of words to be transferred between the registers and memory. Other aspects of the invention include a memory and logic structure and an associated method to extract data blocks from memory to accelerate, for example, operations related to image compression and decompression.
Owner:ROUND ROCK RES LLC
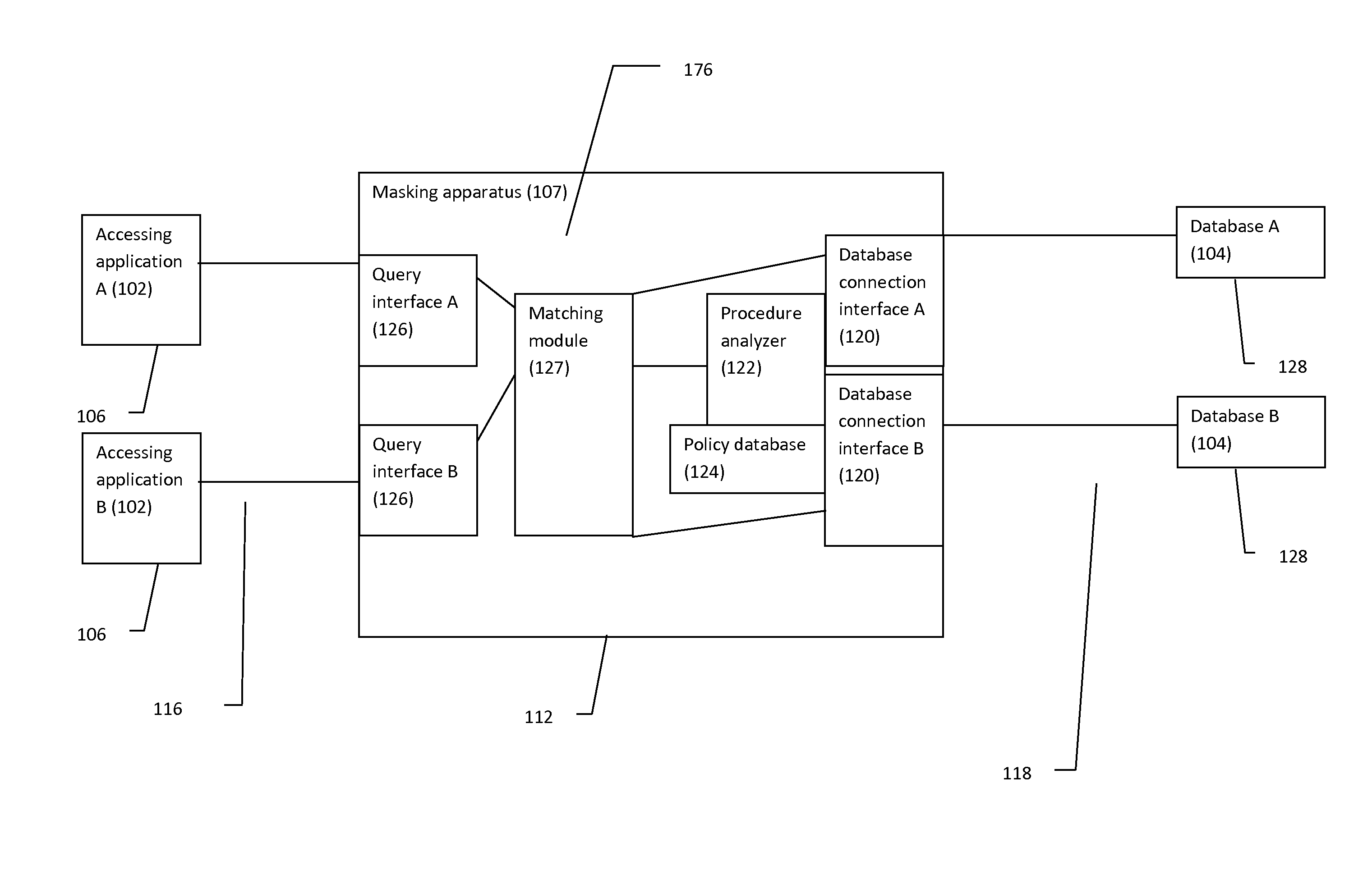
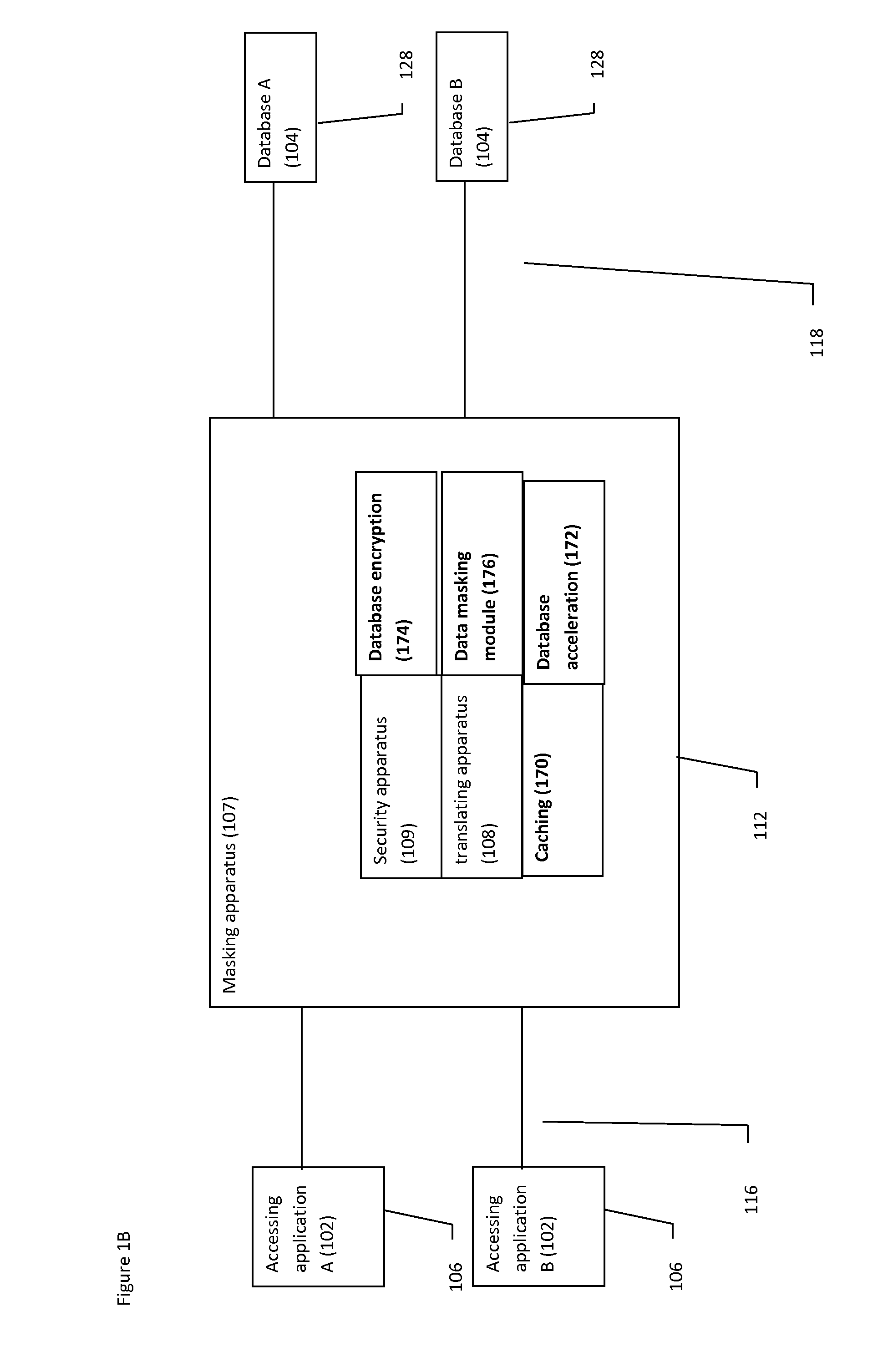
Consistent data masking
InactiveUS20150113659A1Database management systemsDigital data processing detailsData maskingDatabase
According to one embodiment of the present invention, a system masks data objects across a plurality of different data resources. The system comprises a processor configured to include a plurality of service providers to mask the data objects, wherein each service provider corresponds to a different type of data masking for the data objects. An interface provides access to the plurality of service providers from different data-consumers to mask the data objects according to the corresponding types of data masking, wherein resulting masked data maintains relational integrity across the different data resources. Embodiments of the present invention further include a method and computer program product for masking data objects across a plurality of different data resources in substantially the same manners described above.
Owner:GLOBALFOUNDRIES INC
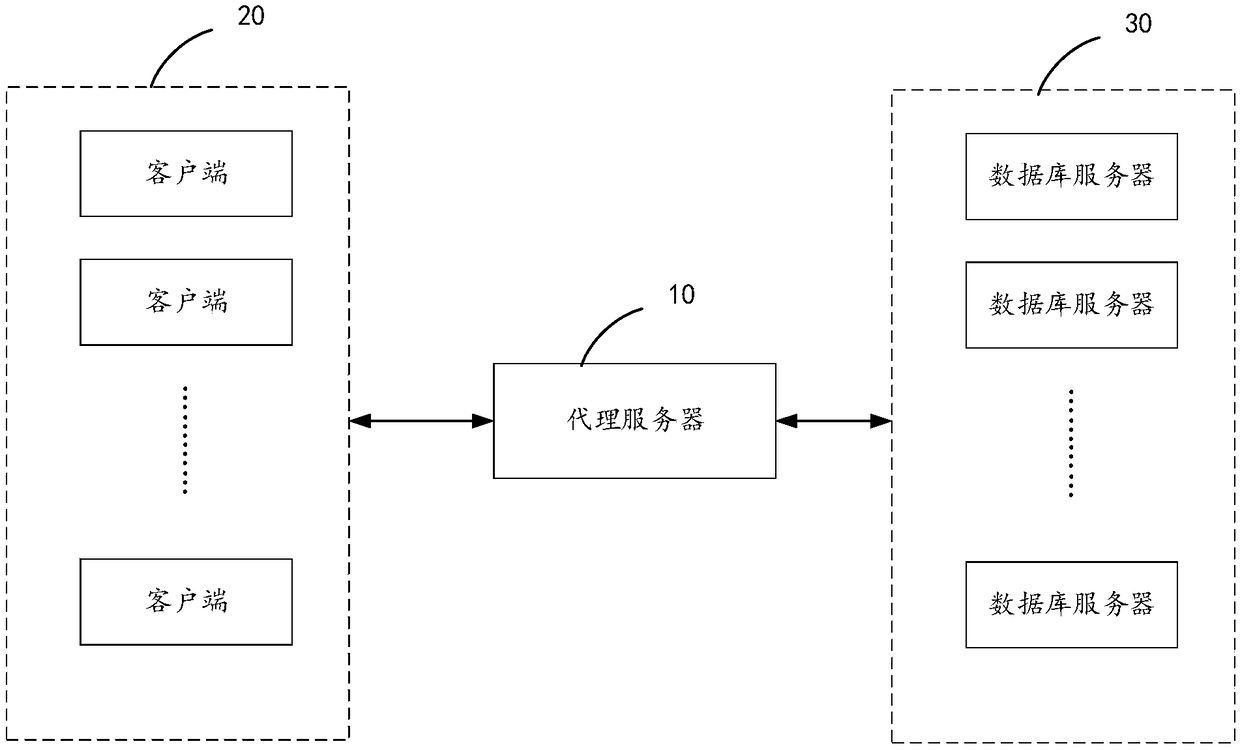
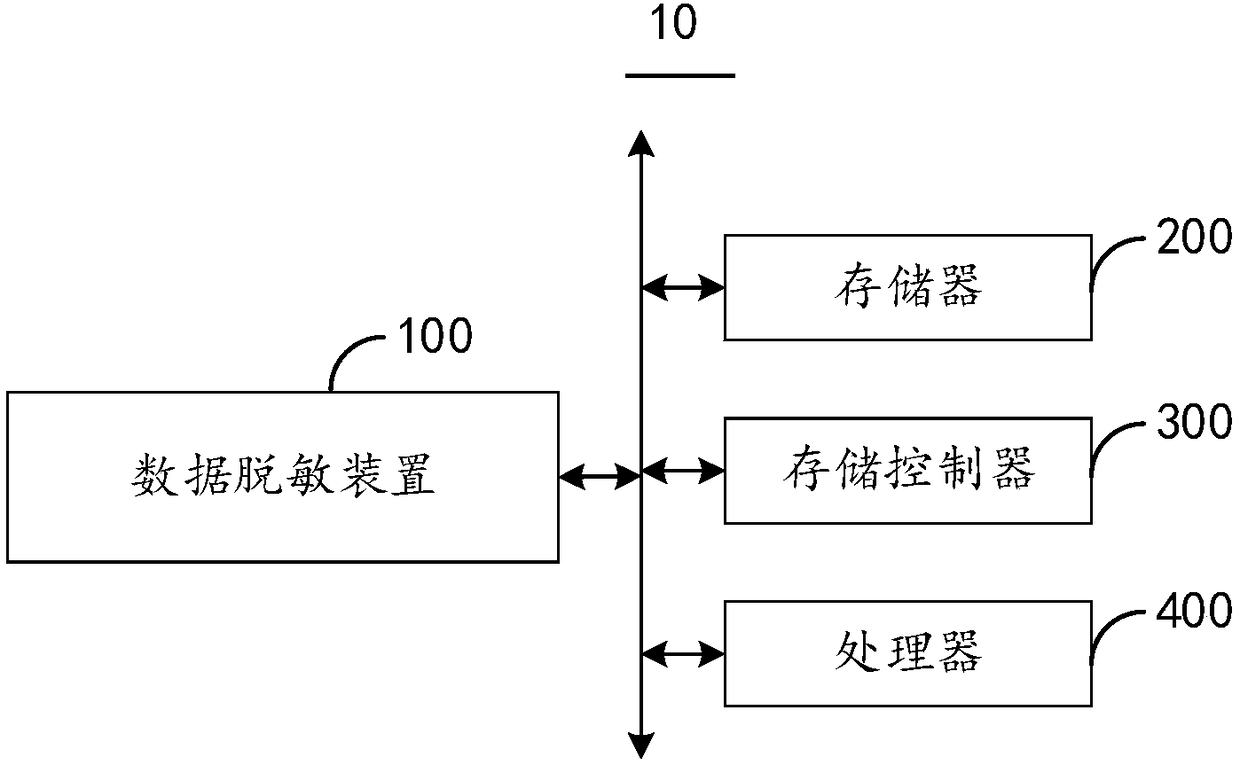
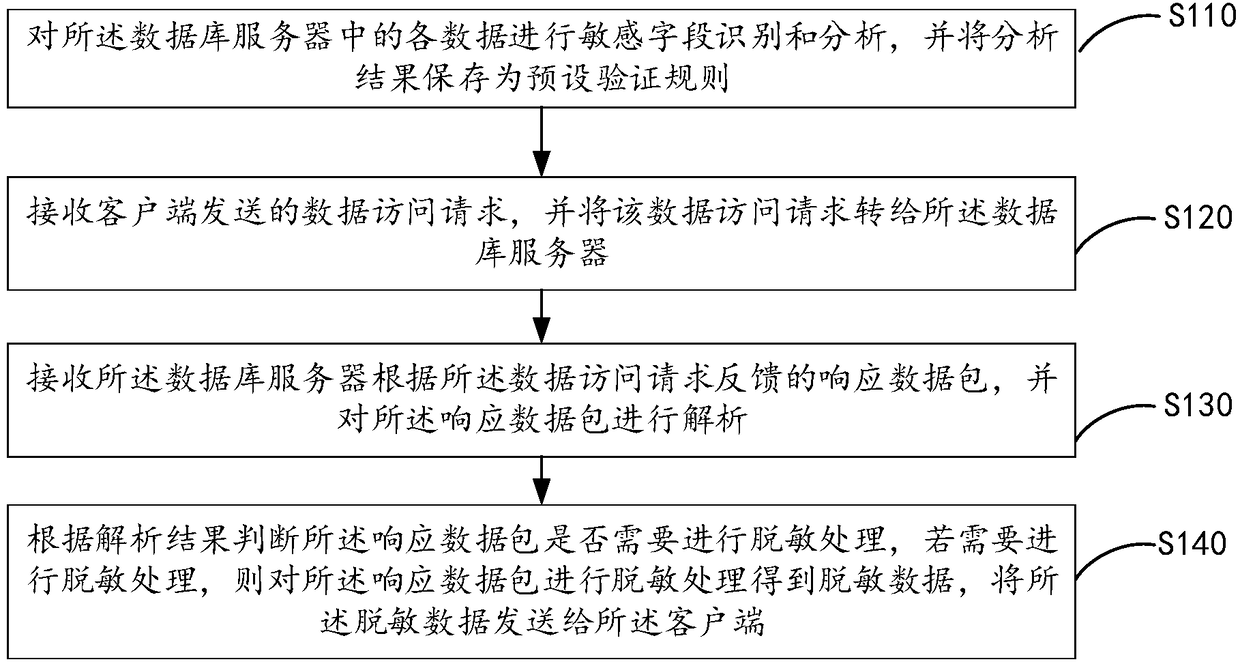
Data masking method and device
The embodiment of the invention provides a data masking method and device. The data masking method comprises the steps of receiving a data access request sent by a client, and forwarding the data access request to a database server; receiving a response data packet fed back by the database server according to the data access request, and parsing the response data packet; judging whether or not theresponse data packet needs to be desensitized according to a parsing result, if yes, desensitizing the response data packet to obtain desensitization data, and sending the desensitization data to theclient. By means of the embodiment, the data access risk can be effectively reduced, and the data security is improved.
Owner:BEIJING WISEWEB TECH
Dynamic data masking system and method
A system and method for providing dynamic data asking for databases through a data masking apparatus.
Owner:GREEN SQL
Method and system for blindly detecting a discontinuously transmitted shared channel, in particular blind high speed shared control channels detection
InactiveUS20050286654A1Reduce loss rateReduce probabilityOther decoding techniquesCode conversionDigital dataControl channel
A method for detecting an eventual channel intended to a designated user equipment among n channels received by the designated user equipment during a given duration, each channel received during the duration carrying encoded data masked with an identifier associated to a user equipment. The method includes a selecting phase having a demasking step demasking the received masked encoded data of each channel with the identifier of the designated user equipment, a decoding step decoding the demasked encoded data of each channel to obtain a set of digital decoded data for each channel, a calculating step calculating, from each set of digital decoded data, a global information representative of a confidence in digital data received on the physical channel, and a detecting step detecting the channel from all the global information.
Owner:SNO WAY INT +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com