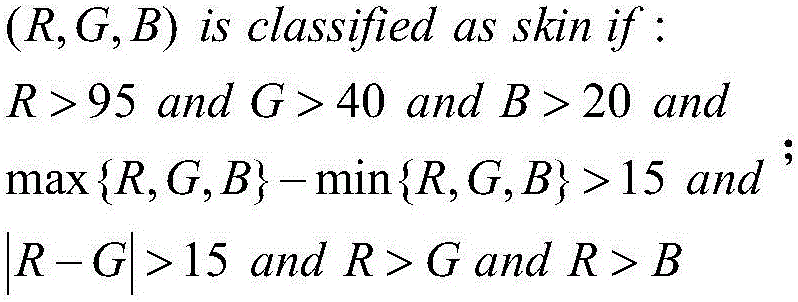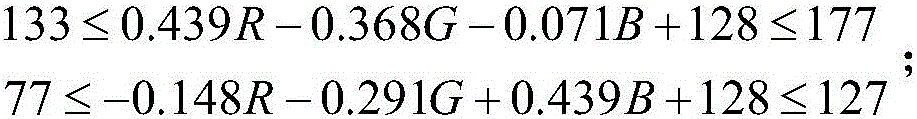Mobile terminal sensitive information identification method
A mobile terminal, information identification technology, applied in the field of information security identification, can solve problems such as national and unit construction losses, and achieve the effect of improving the face recognition rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] The present invention is further described below in conjunction with embodiment.
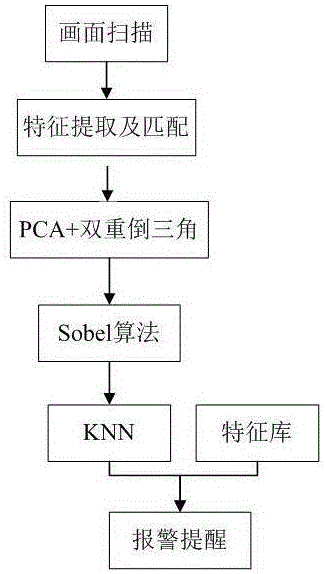
[0051] like figure 1 As shown, a mobile terminal "sensitive" information identification method is divided into two stages of screen scanning and feature extraction and matching, including the following steps:
[0052] 1) The screen scanning stage is to convert the dynamic screen of the mobile terminal into a static picture:
[0053] Screen scanning takes 16×16 as a unit, scans the current screen every 30s, and initially extracts screen features. When two or more sensitive information features appear on the screen, screenshots are taken to the terminal memory, and stored in the memory to realize dynamic screens. conversion to static images;
[0054] 2) The feature extraction and matching stage is to analyze the picture and find out whether it is "sensitive" information. The feature extraction and matching stage is composed of inverted double triangle double discrimination algorithm, PCA fa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com