Method, device and terminal for account authorization of application programs
An application program and account technology, applied in the Internet field, can solve problems such as information cannot be processed by users in the first time, information reception failure, user loss, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
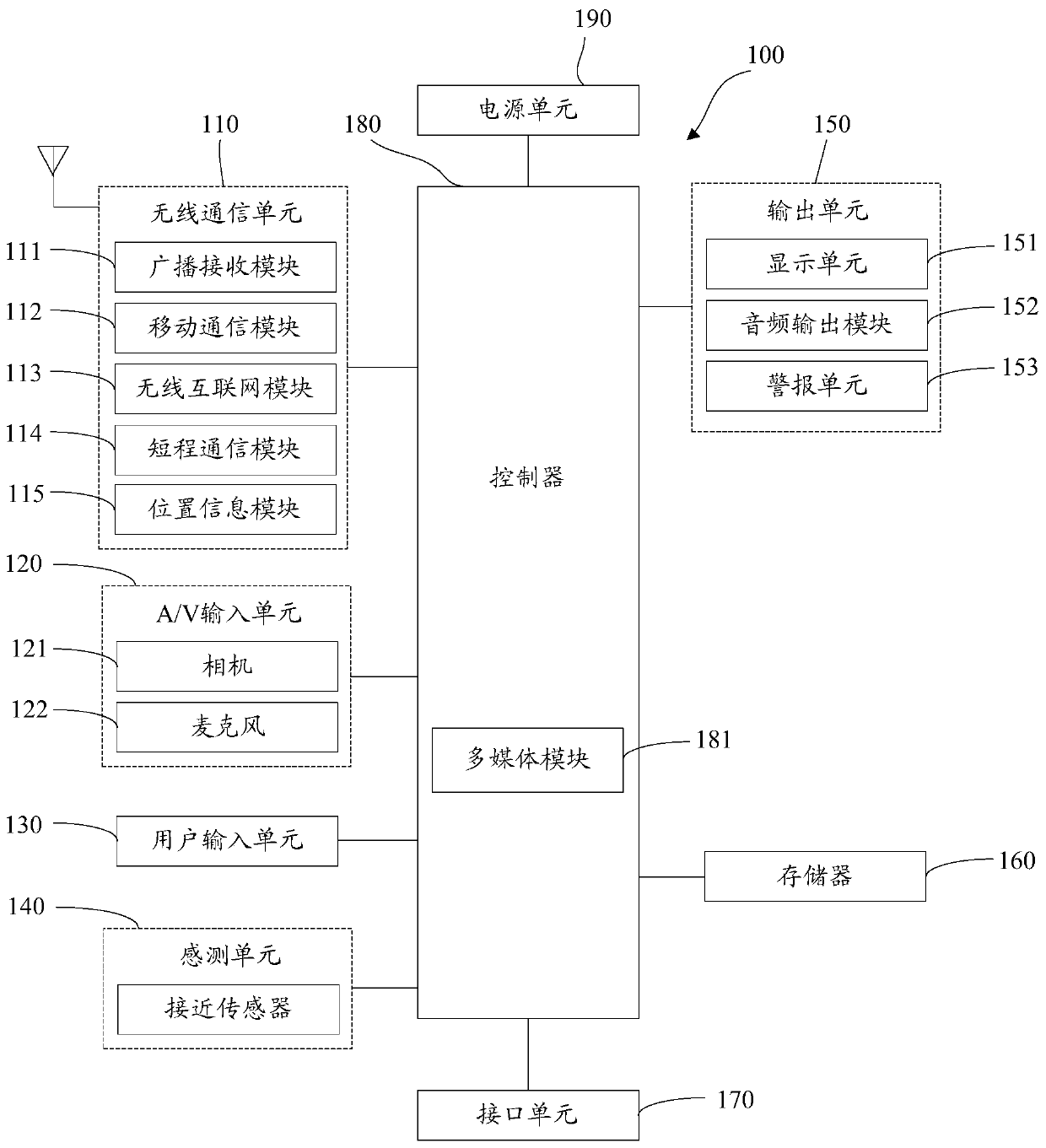
[0077] The first embodiment of the present invention proposes a method for account authorization of an application program, which can be applied to a terminal.
[0078] Here, the terminal described above may be a fixed terminal with a display screen, or a mobile terminal with a display screen.
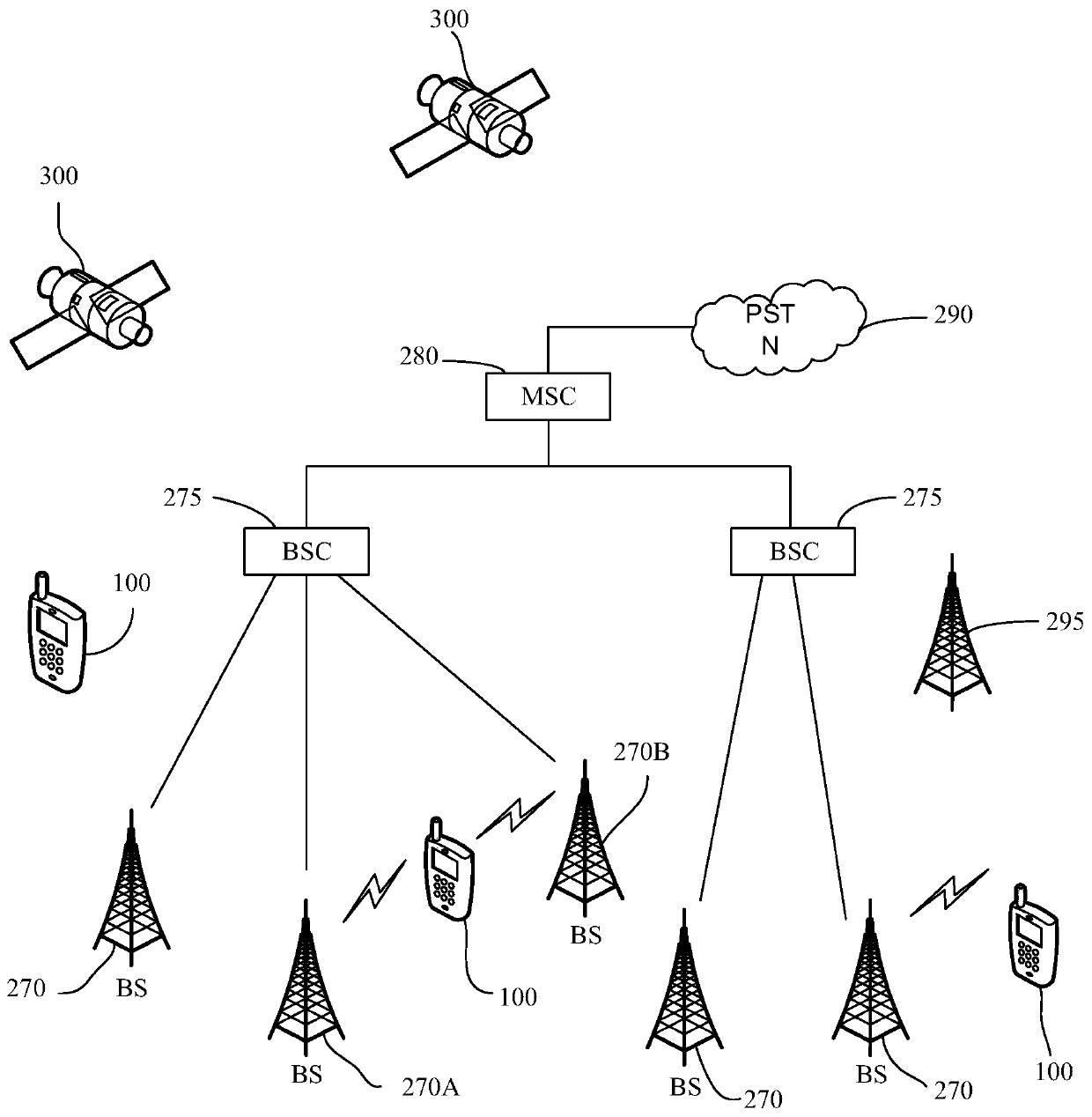
[0079] The above-mentioned fixed terminal may be a computer, etc., and the above-mentioned mobile terminal includes, but is not limited to, a mobile phone, a notebook computer, a camera, a PDA, a PAD, a PMP, a navigation device, and the like. The terminal may be connected to the Internet, wherein the connection may be through a mobile Internet network provided by an operator, or through a wireless access point for network connection.
[0080] Here, if the mobile terminal has an operating system, the operating system can be UNIX, Linux, Windows, Android (Android), Windows Phone and so on.
[0081] It should be noted that there is no limitation on the type, shape, size, etc. of the disp...
no. 2 example
[0106] Figure 6 The flow chart of the second embodiment of the method for authorizing the account of the application program of the present invention, as shown in Figure 6 As shown, the process includes:
[0107] Step 600: terminal A activates the account authorization function of application program A.
[0108] In the embodiment of the present invention, a corresponding account authorization function can be set for each application program in the terminal, so that more targeted account management can be realized. Whether to enable the account authorization function.
[0109] Step 601: Terminal A creates a list of account authorization objects, and i is initially set to 1.
[0110] In actual implementation, terminal A establishes an authorized object list corresponding to application A with friends who are allowed to receive the information of its own application A. The authorized object list includes N pieces of authorized object information, and N is an integer greater ...
no. 3 example
[0126] In order to better reflect the purpose of the present invention, further illustrations are made on the basis of the first embodiment of the present invention.
[0127] Figure 8 The flow chart of the third embodiment of the method for authorizing the account of the application program of the present invention, as shown in Figure 8 As shown, the process includes:
[0128] Step 800: Terminal A enables the account authorization function, and establishes a list of account authorization objects.
[0129] In the embodiment of the present invention, terminal A uses the same list of account authorization objects to perform account authorization operations for all applications. When the user creates the account authorization object list, the authorization objects selected are often several fixed friends. The authorization objects in the account authorization object list differ very little, so in order to avoid cumbersome authorization settings, you can set the authorization o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com