Vulnerability Automatic Classification Method Supporting Vulnerability Correlation Mining
A technology of automatic classification and correlation, applied in the field of information security, which can solve the problems of non-mutual exclusion between classes, vague concepts, and no specific characteristics clearly pointed out.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0078] The technical solution of the present invention will be described in detail below in conjunction with the drawings and embodiments.
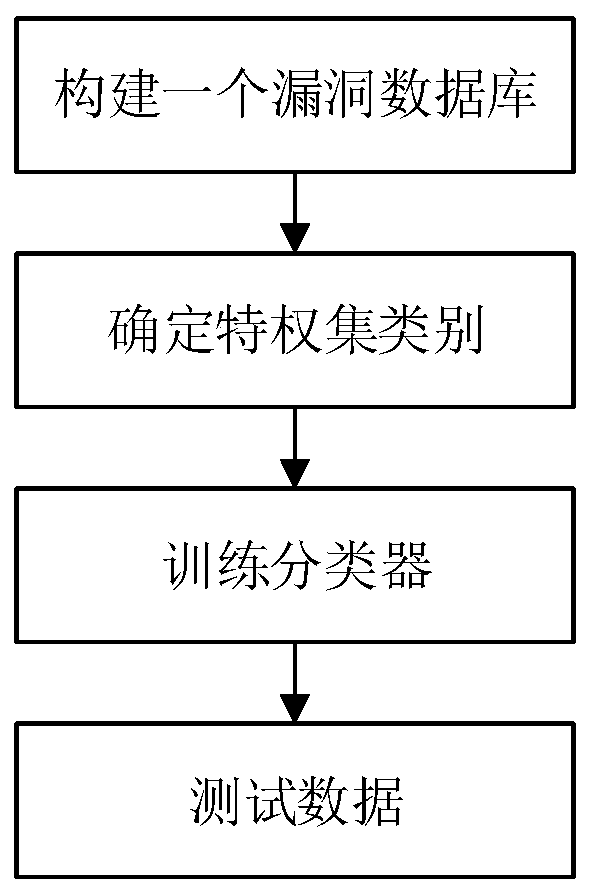
[0079] Using the vulnerability automatic classification method that supports vulnerability association mining proposed by the present invention to classify vulnerabilities and obtain the operation process of the association relationship between vulnerabilities is as follows: figure 1 As shown, the specific steps are:
[0080] Step 1: Build a vulnerability database, download the 2010-2016 vulnerability data from the National Vulnerability Database (NVD), select the vulnerability data under Linux and filter the fields and import it into the local database.
[0081] The fields of the local vulnerability database are shown in Table 1.
[0082] Table 1 Vulnerability database field table
[0083]
[0084]
[0085] Step 2: Determine the privilege set category.
[0086] The categories of privilege sets include: system administrator privilege set, common sy...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com