Random-verification-code parallel generation method based on low order iterative method and linear chaotic heredity
A generation method and iterative method technology, applied in the direction of secure communication, transmission system, and digital data authentication through chaotic signals, to achieve the effect of simple implementation, resistance to brute force cracking, and fast operation speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0155] Embodiments of the present invention will be further described in detail below in conjunction with the accompanying drawings and examples. The following examples are used to illustrate the present invention, but should not be used to limit the scope of the present invention.
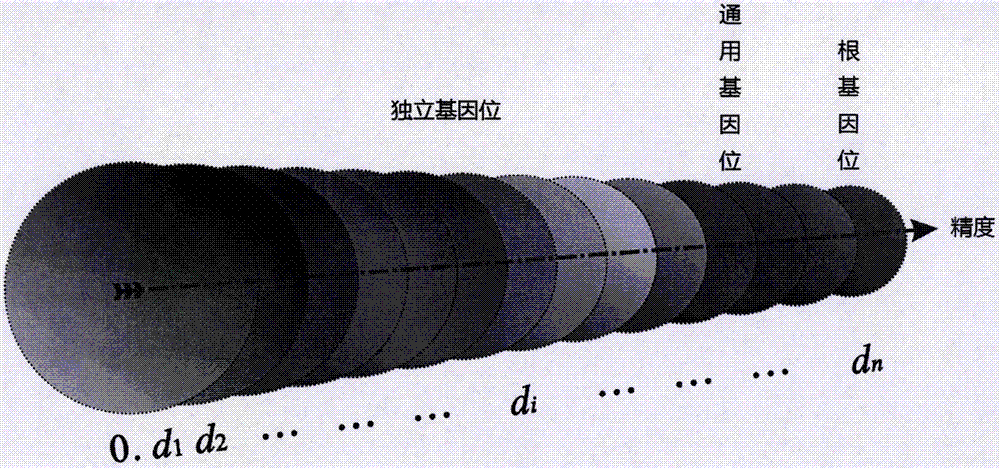
[0156] Example 1: Assume that the number of processes of the multi-core computer system is set to 4, and the low-bit precision pn is set to 6.
[0157] Assume that MPI_Send and MPI_Recv are MPI functions used for message sending and message receiving in the program.
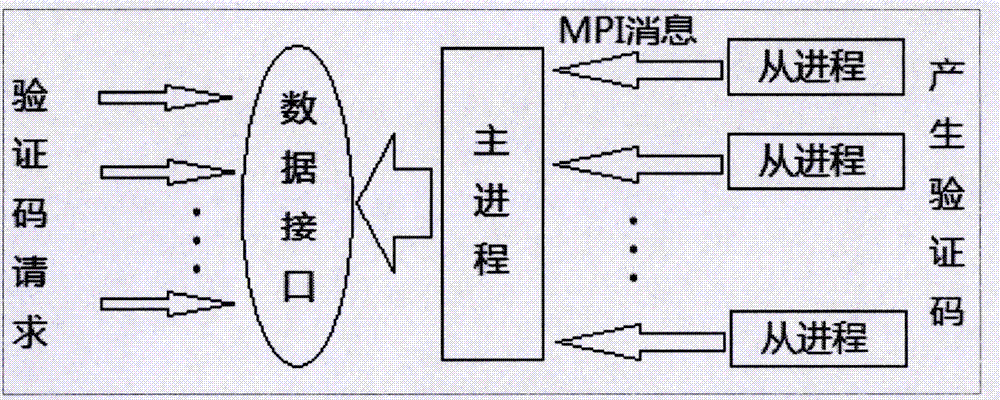
[0158] The parallel program starts executing.
[0159] After the MPI environment is initialized; MyID=0 in the parallel system is the main process, and the serial numbers of MyID are 1, 2, and 3 are the slave processes.
[0160] Obtain the total number of system MPI processes ranksize=4.
[0161] The master process MPI_Send passes parameters to the slave process, assuming that the given parameter is x[0]=0.92, k=0.3457 in the slav...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com