A security reinforcement method for transmitting key information in a packet transport network
A packet transmission network, a key transmission technology, applied in the field of communication, can solve the problems of increasing the difficulty of information interception and hidden dangers of leaking secrets, and achieve the effects of reducing the possibility of being deciphered, smooth upgrading, and easy implementation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention will be described in detail below in conjunction with the accompanying drawings and embodiments.
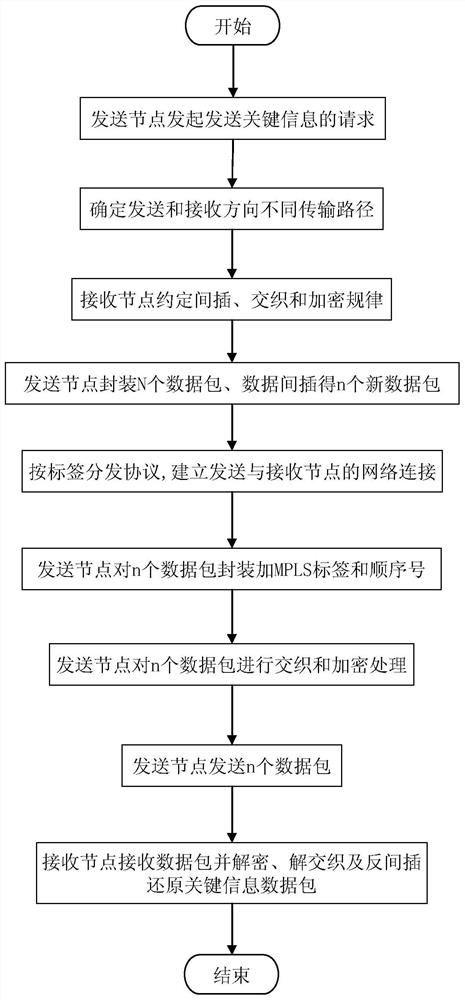
[0036] The flow of this embodiment of the security hardening method for transmitting key information in the packet transport network is as follows figure 1 As shown, the main steps are as follows:
[0037] Step 1. Determine the transmission path for sending and receiving information
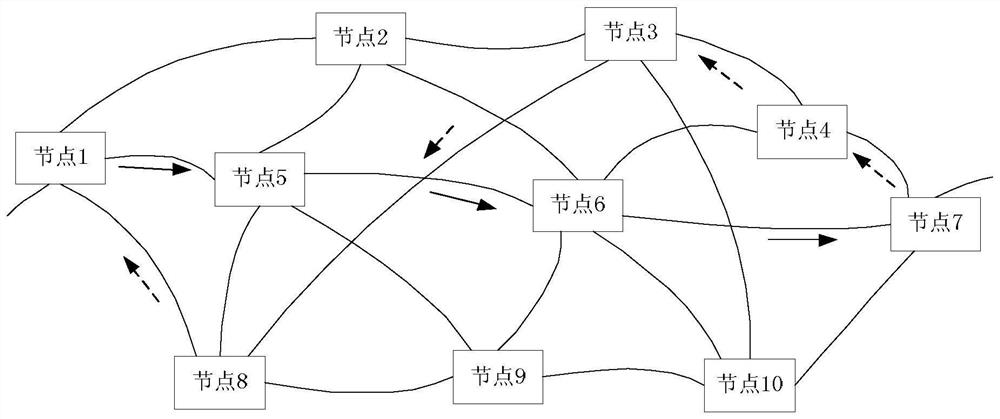
[0038] When the MPLS-TP-based packet transport network PTN network node transmits key information, the sending node initiates a request for key information transmission, and the sending node and the receiving node respectively determine their respective sending direction and receiving direction network path, and the sending direction and The network paths in the receiving direction are different.
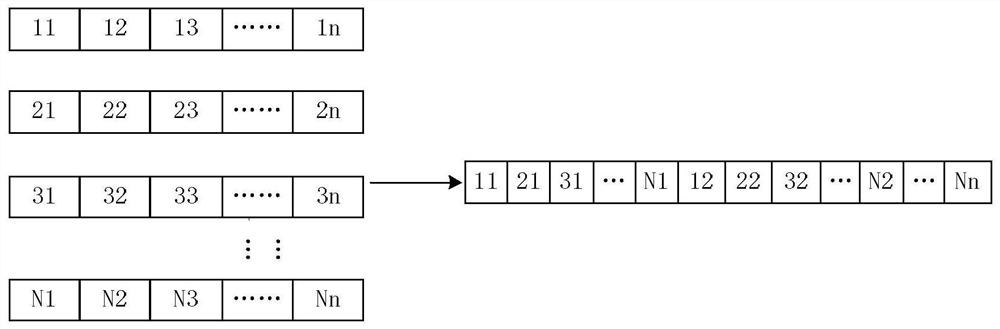
[0039] According to the calculation of the equivalent cost multi-path (ECMP) between the two, the set of available routes for information transmission between the sending no...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com