Terminal permission control method and device
An access control and terminal technology, applied in the computer field, can solve the problems of occupying large resources and complex management process, and achieve the effect of saving resources and simplifying the control process.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
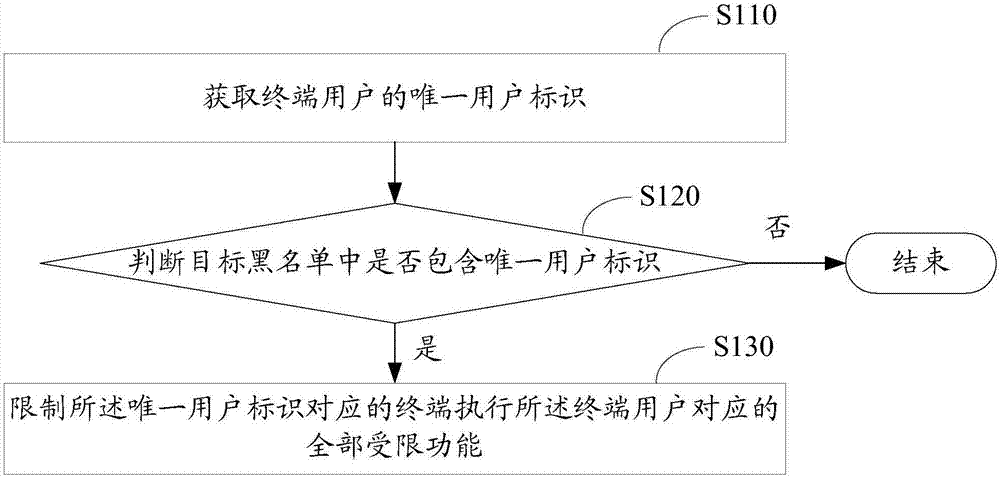
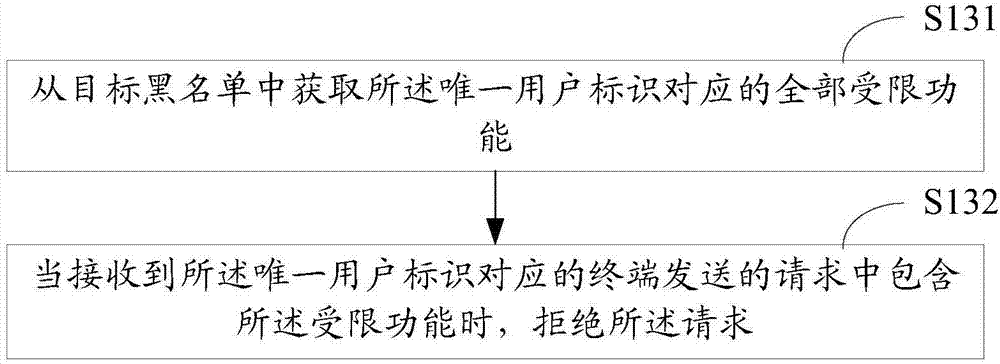
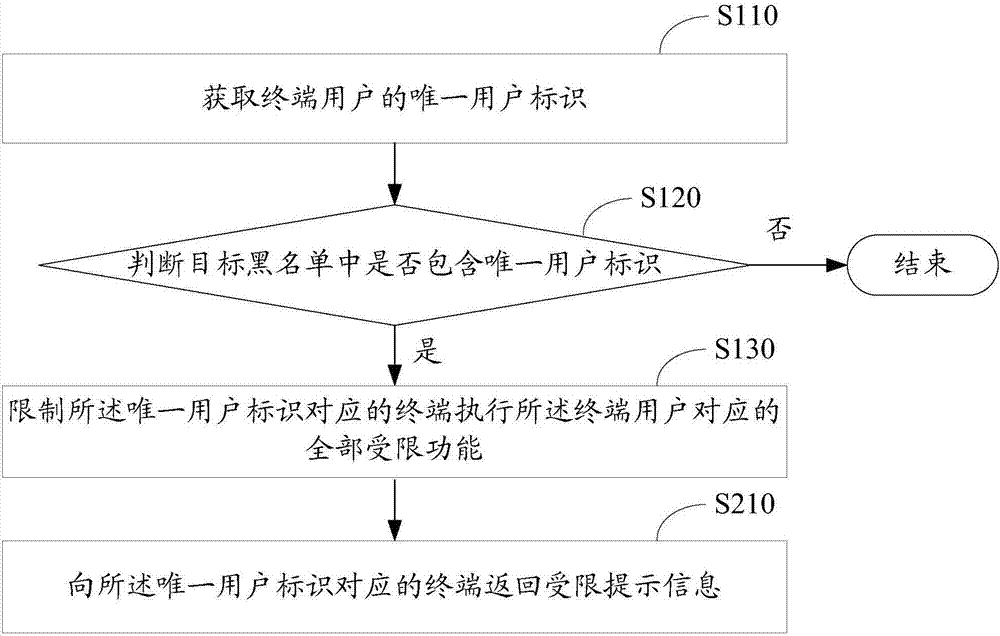
[0048] In the current terminal authority control method, a blacklist is created for different functional authorities in the same network application. For the same terminal user, it is necessary to check whether each blacklist contains the unique user identifier of the terminal user to determine the terminal user. Corresponding to all restricted functions, therefore, the current terminal authority control process is very complicated and takes up a lot of resources. This application provides a terminal authority control method, which combines the blacklists corresponding to all functional authorities into one blacklist, that is, the target blacklist; querying a target blacklist can complete the control of all restricted functions of the terminal user , there is no need to query multiple blacklists, so the control process is simplified and the resources required for the control process are saved.
[0049] In order to make the purpose, technical solutions and advantages of the emb...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com