Determining model protection level on-device based on malware detection in similar devices
A computing device, type of technology, applied in computer security devices, platform integrity maintenance, instrumentation, etc., capable of solving complex, identifying and correcting power utilization levels affecting the long-term and continuous performance of mobile devices, and affecting the long-term and continuous performance of mobile devices. performance and power utilization levels
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] Various embodiments will be described in detail with reference to the accompanying drawings. Wherever possible, the same reference numbers will be used throughout the drawings to refer to the same or like parts. References made to particular examples and implementations are for illustrative purposes, and are not intended to limit the scope of the invention or the claims.
[0025] The word "exemplary" is used herein to mean "serving as an example, instance, or illustration." Any implementation described herein as "exemplary" should not necessarily be construed as preferred or advantageous over other implementations.
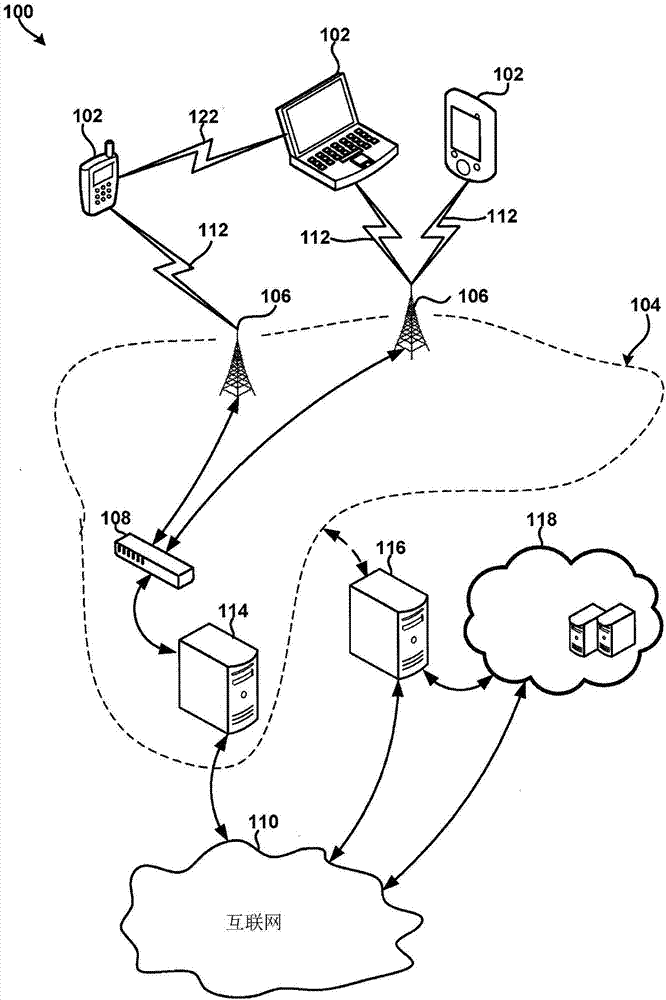
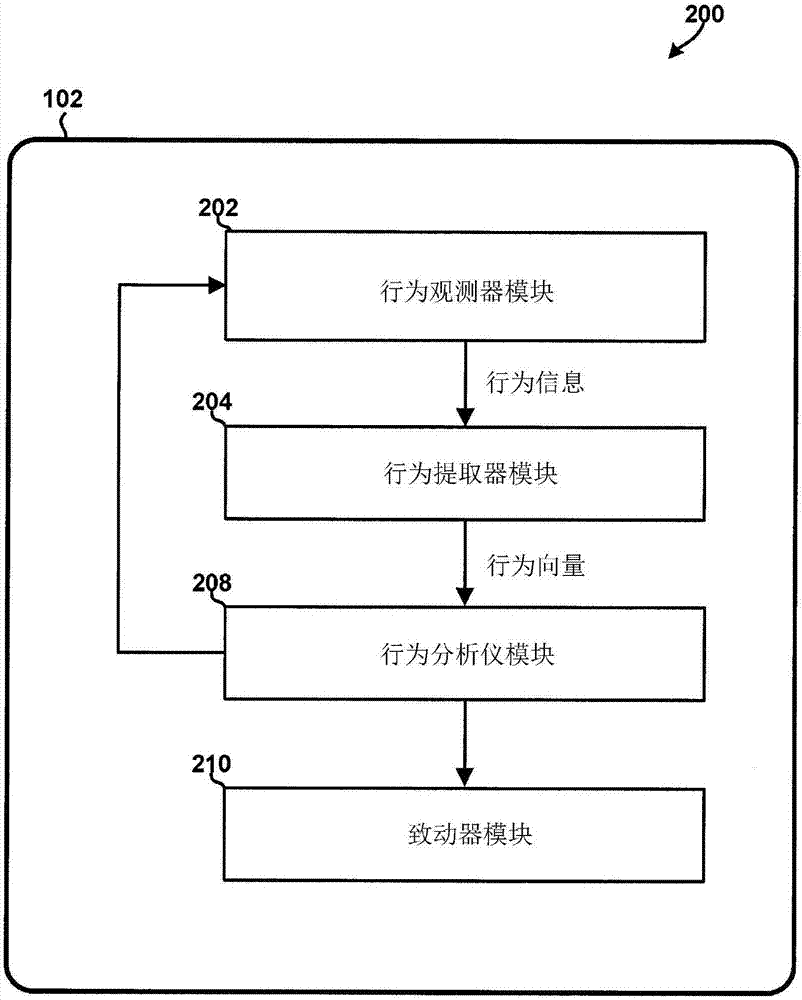
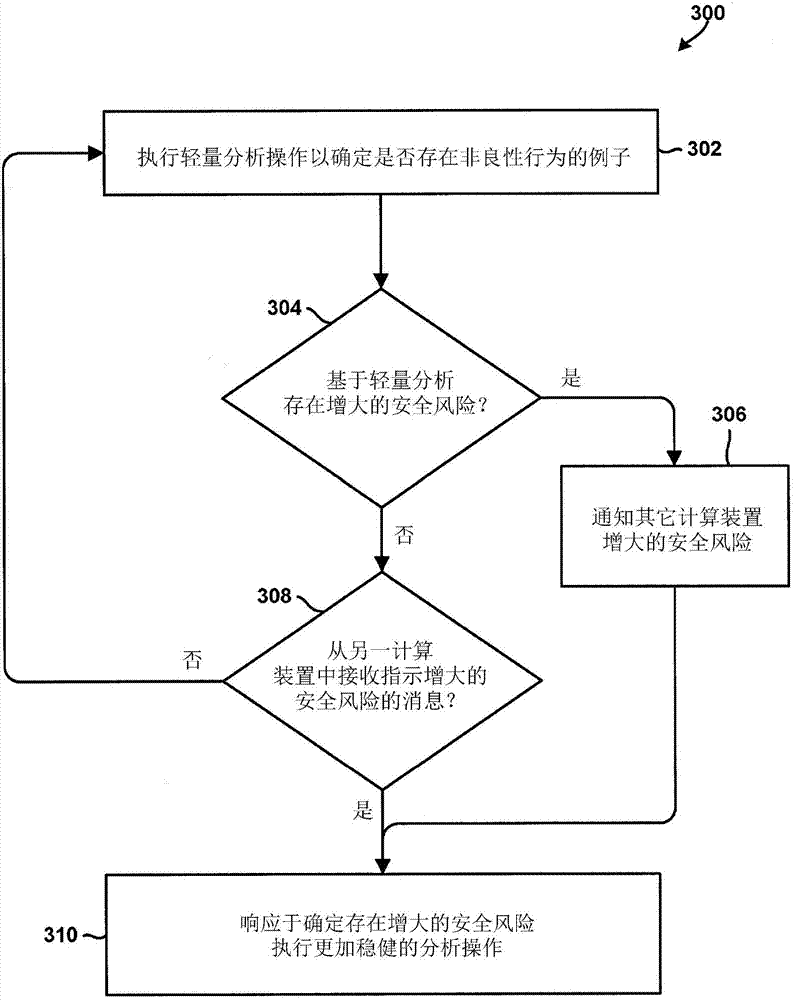
[0026] In summary, various embodiments include effectively identifying, classifying, modeling, preventing and / or correcting conditions that typically degrade computing device performance, power utilization levels, network usage levels, security and / or privacy over time Methods and acts and computing devices configured to implement the methods. The comput...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com