Human-machine recognition method and equipment
A human-machine identification and equipment technology, applied in the field of human-machine identification, can solve problems such as high cost, unrecognizable human-machine identification, and cumbersome SMS process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
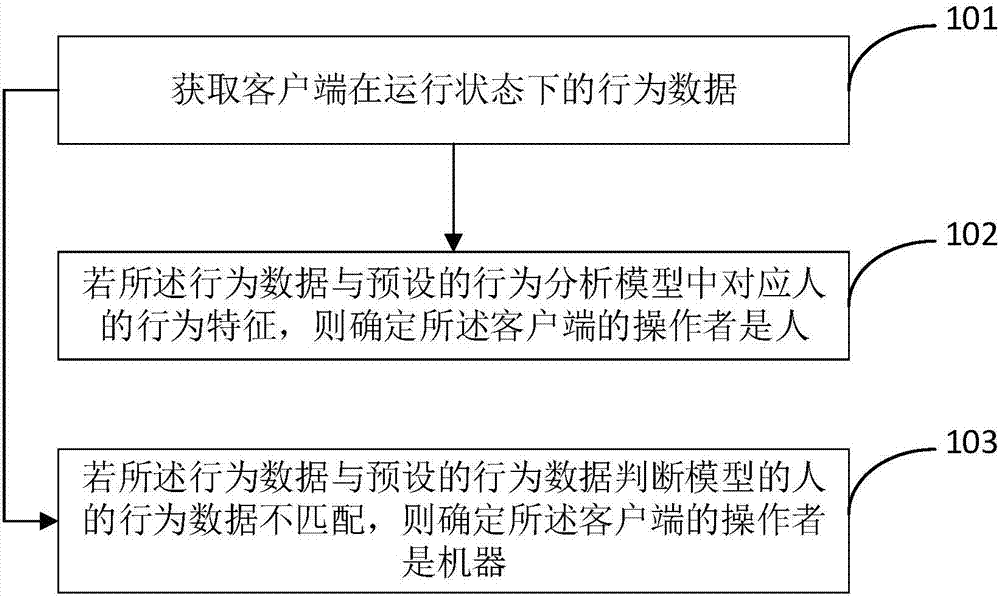
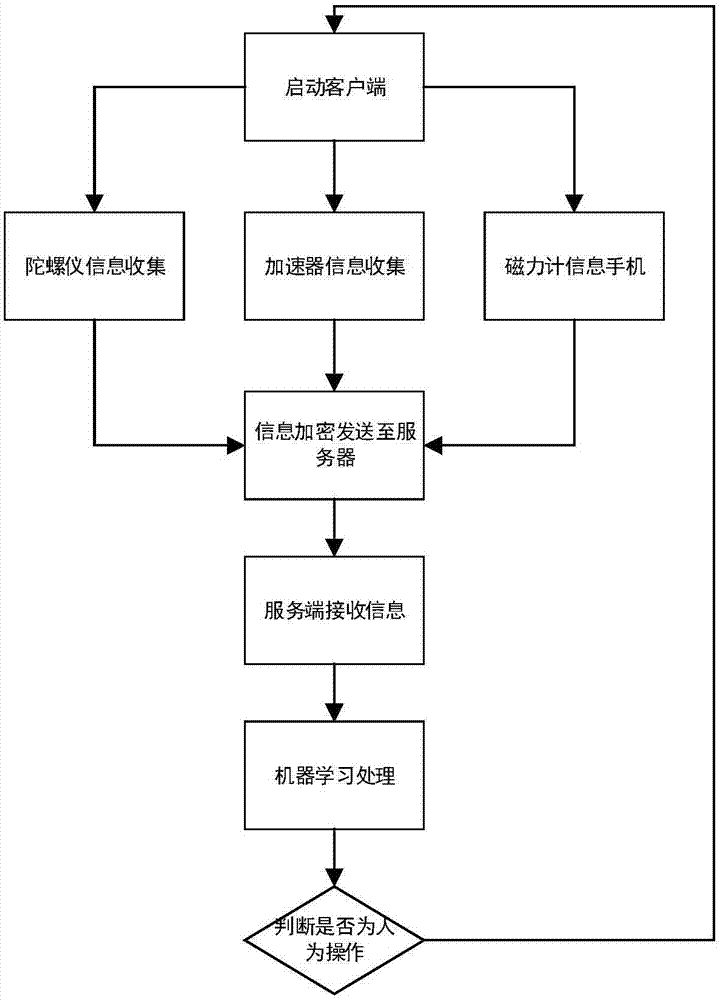
[0044] Embodiment 1 of the present invention discloses a method for human-machine identification, such as figure 1 as well as figure 2 Shown, including:
[0045] Step 101: Obtain behavior data of the client in a running state;
[0046] Wherein, the behavior data includes rotation data of the client, force data of the client, and orientation data of the client;
[0047] Specifically, in an actual embodiment, the client is a mobile client, that is, a mobile terminal, such as a mobile phone, a tablet computer, etc., the rotation data is monitored by a gyroscope, and the force data is Is obtained by monitoring by the accelerometer, and the orientation data is obtained by monitoring by the magnetometer positioning device.
[0048] However, current mobile terminals, such as mobile phones, because the gyroscopes, accelerometers, and magnetometer positioning devices mentioned above are already built into the mobile phones, they can directly obtain behavior data, without the need for addition...
Embodiment 2
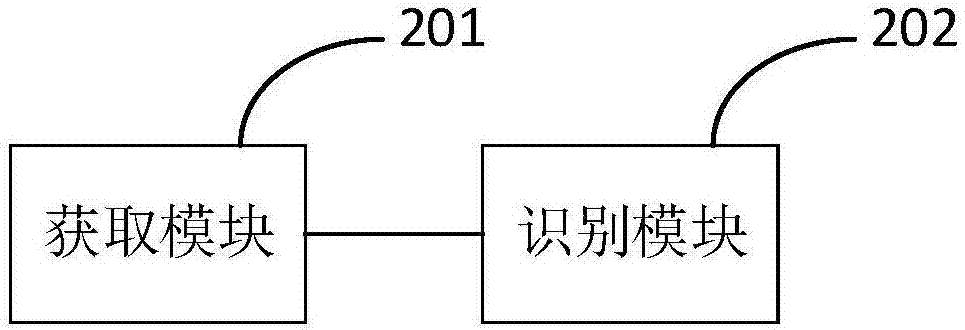
[0066] In order to further illustrate the present invention, Embodiment 2 of the present invention also discloses a human-machine identification device, such as image 3 Shown, including:
[0067] The obtaining module 201 is configured to obtain behavior data of the client in the running state; wherein the behavior data includes rotation data of the client, force data of the client, and orientation data of the client;
[0068] The recognition module 202 is configured to determine that the operator of the client is a human when the behavior data corresponds to the behavior characteristics of the corresponding person in the preset behavior analysis model; and when the behavior data and the preset behavior data judgment model When the behavior data of the person does not match, it is determined that the operator of the client is a machine.
[0069] In a specific embodiment, such as Figure 4 As shown, the equipment also includes:
[0070] The defense module 203 is configured to initiate ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com